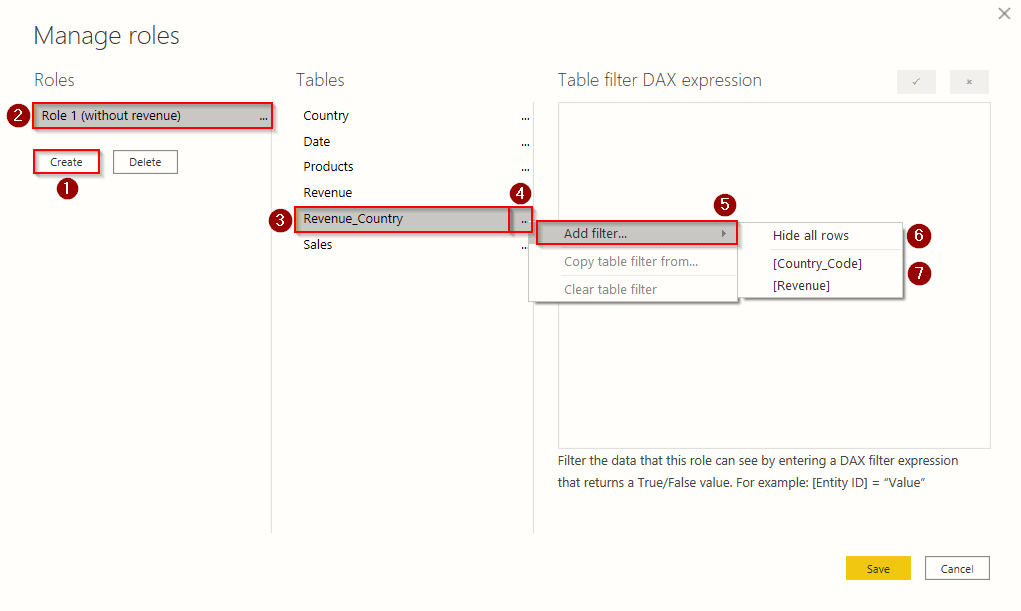
Power Bi Security Documentation . Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. By implementing rls, you can.
from k21academy.com
By implementing rls, you can. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user.
Data Security in Power BI How to Implement and Configure
Power Bi Security Documentation Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. By implementing rls, you can. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal.
From data-flair.training
Power BI Security What is Dynamic RowLevel Security DataFlair Power Bi Security Documentation Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. By implementing rls, you can. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every. Power Bi Security Documentation.
From www.pk-anexcelexpert.com
Static and Dynamic Row Level Security in Power BI PK An Excel Expert Power Bi Security Documentation Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. By implementing rls, you can. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of. Power Bi Security Documentation.
From o365.vn
How to visualise security and threat information in Microsoft Power BI Power Bi Security Documentation Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. By implementing rls, you. Power Bi Security Documentation.
From www.powerbisentinel.com
Power BI Documentation Power BI Sentinel writes it for you! Power Bi Security Documentation Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. By implementing rls, you can. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of. Power Bi Security Documentation.
From www.loginworks.com
How to implement RLS security with Filters in Power BI? Power Bi Security Documentation Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. By implementing rls, you can. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of. Power Bi Security Documentation.
From www.softude.com
24 Essential Practices to Ensure Power BI Security Power Bi Security Documentation To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. By implementing rls, you can. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security. Power Bi Security Documentation.
From skypointcloud.com
How Do We Improve Power BI Security? SkyPoint Cloud Power Bi Security Documentation To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. By implementing rls, you can. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security. Power Bi Security Documentation.
From www.biconnector.com
Power BI Row Level Security RLS Setup Stepbystep guide Power Bi Security Documentation Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. By implementing rls, you can. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of. Power Bi Security Documentation.
From learn.microsoft.com
Laporan resmi keamanan Power BI Power BI Microsoft Learn Power Bi Security Documentation By implementing rls, you can. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every. Power Bi Security Documentation.
From www.cloudfronts.com
Fig 2 CEO Dashboard Power Bi Security Documentation Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. By implementing rls, you. Power Bi Security Documentation.
From www.excelmojo.com
Power BI Security How to Create RowLevel Security? Power Bi Security Documentation Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. By implementing rls, you can. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security. Power Bi Security Documentation.
From fyowyiqya.blob.core.windows.net
Power Bi Security Considerations at Lucy Allison blog Power Bi Security Documentation By implementing rls, you can. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security. Power Bi Security Documentation.
From www.ilink-digital.com
Microsoft Power BI Security 6 Best Practices iLink Digital Power Bi Security Documentation Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. By implementing rls, you can. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every. Power Bi Security Documentation.
From www.dtonomy.com
Create Power BI Reporting for CrowdStrike AIDriven Security Operations Power Bi Security Documentation Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. By implementing rls, you. Power Bi Security Documentation.
From powerbiconsulting.com
Row Level Security in Power BI Setup & Importance Power Bi Security Documentation By implementing rls, you can. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of. Power Bi Security Documentation.
From onlineappsdba.com
Data Security in Power BI How to Implement and Configure Power Bi Security Documentation Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. By implementing rls, you. Power Bi Security Documentation.
From www.biconnector.com
Power BI Row Level Security RLS Setup Stepbystep guide Power Bi Security Documentation To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. By implementing rls, you can. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every. Power Bi Security Documentation.
From www.liongard.com
Create ataglance security dashboards with Power BI Liongard Power Bi Security Documentation By implementing rls, you can. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of. Power Bi Security Documentation.
From skypointcloud.com
How Do We Improve Power BI Security? SkyPoint Cloud Power Bi Security Documentation To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. By implementing rls, you can. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security. Power Bi Security Documentation.
From www.youtube.com
Power BI Security Combined Column Level Security & Row Level Security Power Bi Security Documentation By implementing rls, you can. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security. Power Bi Security Documentation.
From docs.gavagai.io
PowerBI Gavagai Explorer Documentation Power Bi Security Documentation Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. By implementing rls, you can. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of. Power Bi Security Documentation.
From k21academy.com
Data Security in Power BI How to Implement and Configure Power Bi Security Documentation Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. By implementing rls, you can. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security. Power Bi Security Documentation.
From yodalearning.com
Power BI Architecture A Ultimate Guide on Power BI Security & BI Power Bi Security Documentation Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. By implementing rls, you can. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security. Power Bi Security Documentation.
From www.liongard.com
Create ataglance security dashboards with Power BI Liongard Power Bi Security Documentation Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. By implementing rls, you can. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every. Power Bi Security Documentation.
From www.liongard.com
Create ataglance security dashboards with Power BI Liongard Power Bi Security Documentation Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. By implementing rls, you can. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security. Power Bi Security Documentation.
From learn.microsoft.com
Power BI security white paper Power BI Microsoft Learn Power Bi Security Documentation To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. By implementing rls, you can. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every. Power Bi Security Documentation.
From www.journeyteam.com
9 Power BI Security Best Practices Power Bi Security Documentation To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. By implementing rls, you. Power Bi Security Documentation.
From dxosydcqp.blob.core.windows.net
Power Bi Security Management at Lee Causey blog Power Bi Security Documentation Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. By implementing rls, you. Power Bi Security Documentation.
From dxosydcqp.blob.core.windows.net
Power Bi Security Management at Lee Causey blog Power Bi Security Documentation By implementing rls, you can. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security. Power Bi Security Documentation.
From www.sqlcircuit.com
SQLCircuit Power BI Security Model Power Bi Security Documentation Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. By implementing rls, you. Power Bi Security Documentation.
From cescvwpi.blob.core.windows.net
Power Bi Dataflow Security at Brian Oshea blog Power Bi Security Documentation To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. By implementing rls, you can. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every. Power Bi Security Documentation.
From learn.microsoft.com
Notas del producto sobre la seguridad de Power BI Power BI Power Bi Security Documentation To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. By implementing rls, you can. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every. Power Bi Security Documentation.
From www.pinterest.com
Power BI Security Roles Learn How to Secure Your Data Power Bi Security Documentation Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. By implementing rls, you. Power Bi Security Documentation.
From bigintsolutions.com
BI Architecture Power BI Security and Architecture advise Power Bi Security Documentation By implementing rls, you can. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of monitoring,. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every. Power Bi Security Documentation.
From www.youtube.com
Security in Power BI Quick Overview YouTube Power Bi Security Documentation By implementing rls, you can. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Data protection capabilities in power bi build on microsoft's strengths in security and enable customers to empower every user. To give power bi and security admins better visibility over sensitive data consumption, for the purpose of. Power Bi Security Documentation.