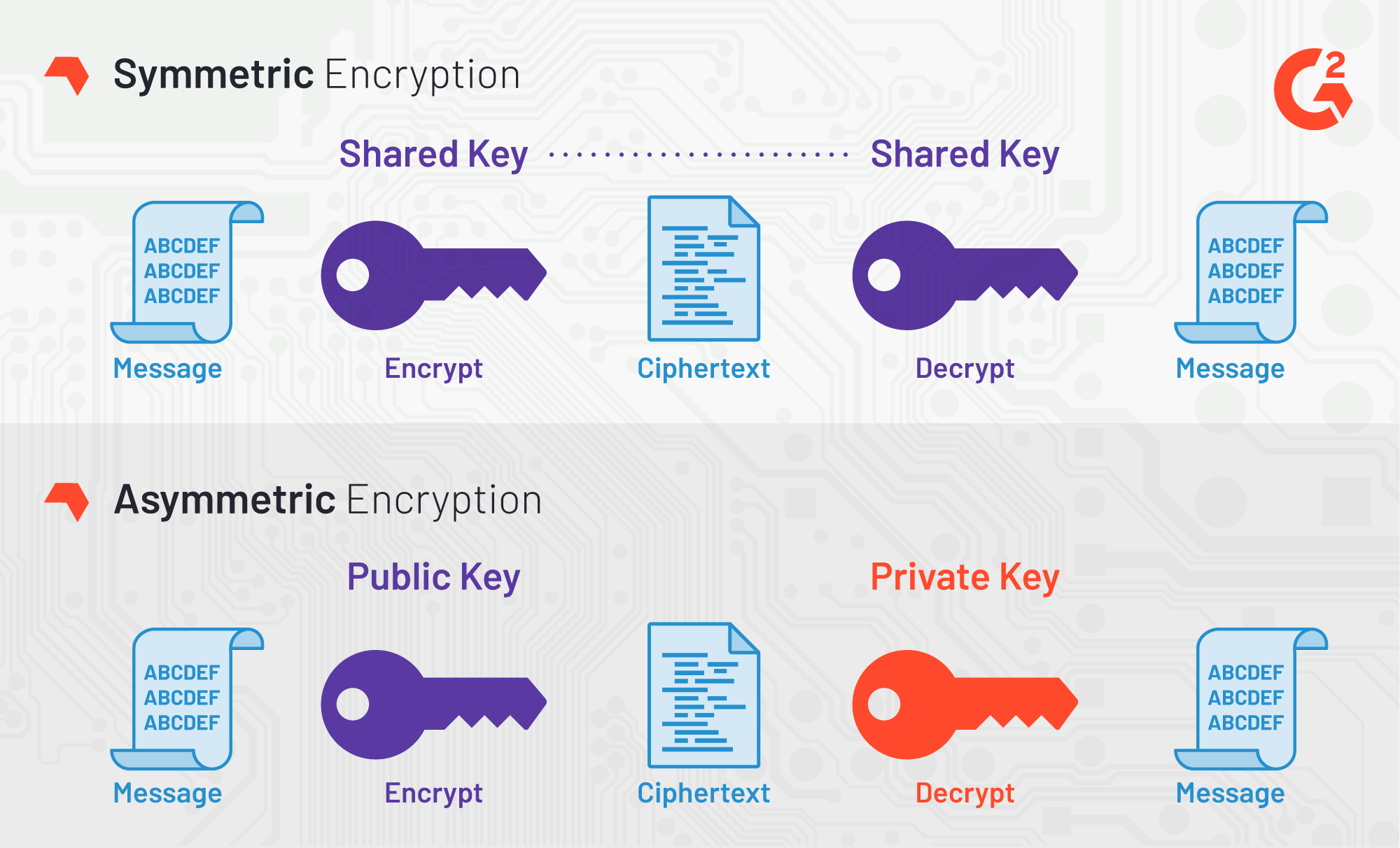
Examples Of Encryption In Transit . Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and buying an item from an online retailer, and ensure the privacy of messages such as emails and texts. Sending an email over the internet. in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. a short overview of the various data encryption methods available today: encryption at rest refers to the encryption applied to the stored data. here are a few examples of a file in transit: best practices for data in transit encryption. Two employees exchanging files over a corporate network. google works actively with the industry to help bring encryption in transit to everyone, everywhere. Implement virtual private networks (vpns): Encryption may be implemented at the source, where data is generated. Common encryption technologies and tools.
from learn.g2.com
best practices for data in transit encryption. a short overview of the various data encryption methods available today: here are a few examples of a file in transit: Sending an email over the internet. Common encryption technologies and tools. Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and buying an item from an online retailer, and ensure the privacy of messages such as emails and texts. google works actively with the industry to help bring encryption in transit to everyone, everywhere. Two employees exchanging files over a corporate network. Encryption may be implemented at the source, where data is generated. in addition to protecting customer data at rest, microsoft uses encryption technologies to protect.
What Does Encryption Mean and Why Is It Important?
Examples Of Encryption In Transit Common encryption technologies and tools. Implement virtual private networks (vpns): in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. Sending an email over the internet. Common encryption technologies and tools. a short overview of the various data encryption methods available today: best practices for data in transit encryption. Encryption may be implemented at the source, where data is generated. Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and buying an item from an online retailer, and ensure the privacy of messages such as emails and texts. encryption at rest refers to the encryption applied to the stored data. here are a few examples of a file in transit: Two employees exchanging files over a corporate network. google works actively with the industry to help bring encryption in transit to everyone, everywhere.
From netlibsecurity.com
Data at Rest vs Data in Transit Examples Of Encryption In Transit Sending an email over the internet. Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and buying an item from an online retailer, and ensure the privacy of messages such as emails and texts. here are a few examples of a file in transit: Encryption may be. Examples Of Encryption In Transit.
From ready.io
Endtoend Encryption (E2EE), Explained Ready Examples Of Encryption In Transit in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. Two employees exchanging files over a corporate network. here are a few examples of a file in transit: google works actively with the industry to help bring encryption in transit to everyone, everywhere. Encryption is used to secure devices such as smartphones and. Examples Of Encryption In Transit.
From j471n.in
Data Encryption Securing Data at Rest and in Transit with Encryption Examples Of Encryption In Transit Sending an email over the internet. encryption at rest refers to the encryption applied to the stored data. a short overview of the various data encryption methods available today: Common encryption technologies and tools. Encryption may be implemented at the source, where data is generated. Implement virtual private networks (vpns): here are a few examples of a. Examples Of Encryption In Transit.
From www.splunk.com
Encryption Explained At Rest, In Transit & EndToEnd Encryption Splunk Examples Of Encryption In Transit Two employees exchanging files over a corporate network. Encryption may be implemented at the source, where data is generated. a short overview of the various data encryption methods available today: Common encryption technologies and tools. here are a few examples of a file in transit: google works actively with the industry to help bring encryption in transit. Examples Of Encryption In Transit.
From www.youtube.com
What is Encryption In Transit? A Layman's Explanation YouTube Examples Of Encryption In Transit a short overview of the various data encryption methods available today: Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and buying an item from an online retailer, and ensure the privacy of messages such as emails and texts. encryption at rest refers to the encryption. Examples Of Encryption In Transit.
From www.youtube.com
DATA Encryption at Rest and in Transit AWS S3 YouTube Examples Of Encryption In Transit Common encryption technologies and tools. Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and buying an item from an online retailer, and ensure the privacy of messages such as emails and texts. encryption at rest refers to the encryption applied to the stored data. here. Examples Of Encryption In Transit.
From au.news.yahoo.com
A Beginner's Guide to Encryption Examples Of Encryption In Transit encryption at rest refers to the encryption applied to the stored data. in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. a short overview of the various data encryption methods available today: best practices for data in transit encryption. Common encryption technologies and tools. Sending an email over the internet. . Examples Of Encryption In Transit.
From pushbuildtestdeploy.com
Encryption in Transit and Rest Push Build Test Deploy Examples Of Encryption In Transit google works actively with the industry to help bring encryption in transit to everyone, everywhere. Sending an email over the internet. Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and buying an item from an online retailer, and ensure the privacy of messages such as emails. Examples Of Encryption In Transit.
From blog.documatic.com
Data Encryption Securing Data at Rest and in Transit with Encryption Examples Of Encryption In Transit Two employees exchanging files over a corporate network. encryption at rest refers to the encryption applied to the stored data. here are a few examples of a file in transit: Sending an email over the internet. Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and. Examples Of Encryption In Transit.
From securityboulevard.com
SaaS Data Encryption Data at Rest vs Data inTransit Security Boulevard Examples Of Encryption In Transit best practices for data in transit encryption. google works actively with the industry to help bring encryption in transit to everyone, everywhere. a short overview of the various data encryption methods available today: Common encryption technologies and tools. Encryption may be implemented at the source, where data is generated. encryption at rest refers to the encryption. Examples Of Encryption In Transit.
From www.slideserve.com
PPT Data Encryption in Transit PowerPoint Presentation, free download Examples Of Encryption In Transit a short overview of the various data encryption methods available today: Two employees exchanging files over a corporate network. Common encryption technologies and tools. google works actively with the industry to help bring encryption in transit to everyone, everywhere. Sending an email over the internet. here are a few examples of a file in transit: Implement virtual. Examples Of Encryption In Transit.
From www.sealpath.com
The Three States of Data Guide Description and How to Secure them Examples Of Encryption In Transit encryption at rest refers to the encryption applied to the stored data. google works actively with the industry to help bring encryption in transit to everyone, everywhere. Common encryption technologies and tools. Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and buying an item from. Examples Of Encryption In Transit.
From marini.systems
Data In Transit Encryption (DITE) Examples Of Encryption In Transit Encryption may be implemented at the source, where data is generated. a short overview of the various data encryption methods available today: encryption at rest refers to the encryption applied to the stored data. Implement virtual private networks (vpns): google works actively with the industry to help bring encryption in transit to everyone, everywhere. here are. Examples Of Encryption In Transit.
From stonefly.com
Data Encryption Essential For Data Storage StoneFly Examples Of Encryption In Transit Sending an email over the internet. Common encryption technologies and tools. google works actively with the industry to help bring encryption in transit to everyone, everywhere. Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and buying an item from an online retailer, and ensure the privacy. Examples Of Encryption In Transit.
From www.youtube.com
Encryption in Transit pt2 Certificates and Encryption YouTube Examples Of Encryption In Transit google works actively with the industry to help bring encryption in transit to everyone, everywhere. Sending an email over the internet. encryption at rest refers to the encryption applied to the stored data. Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and buying an item. Examples Of Encryption In Transit.
From us.norton.com
What is encryption? How it works + types of encryption Norton Examples Of Encryption In Transit a short overview of the various data encryption methods available today: Two employees exchanging files over a corporate network. in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. google works actively with the industry to help bring encryption in transit to everyone, everywhere. Common encryption technologies and tools. encryption at rest. Examples Of Encryption In Transit.
From www.slideteam.net
Overview Of Encryption For Securing Data In Transit Encryption Examples Of Encryption In Transit in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. encryption at rest refers to the encryption applied to the stored data. Two employees exchanging files over a corporate network. here are a few examples of a file in transit: Implement virtual private networks (vpns): Common encryption technologies and tools. Encryption is used. Examples Of Encryption In Transit.
From martin.kleppmann.com
The Investigatory Powers Bill would increase cybercrime — Martin Examples Of Encryption In Transit encryption at rest refers to the encryption applied to the stored data. a short overview of the various data encryption methods available today: Common encryption technologies and tools. Two employees exchanging files over a corporate network. Encryption may be implemented at the source, where data is generated. in addition to protecting customer data at rest, microsoft uses. Examples Of Encryption In Transit.
From brightlineit.com
Data Encryption in Transit What Your Business Needs to Know Examples Of Encryption In Transit google works actively with the industry to help bring encryption in transit to everyone, everywhere. Two employees exchanging files over a corporate network. best practices for data in transit encryption. in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. Encryption may be implemented at the source, where data is generated. encryption. Examples Of Encryption In Transit.
From www.vrogue.co
Kpitsimpl Encryption In Transit Encryption At Rest vrogue.co Examples Of Encryption In Transit google works actively with the industry to help bring encryption in transit to everyone, everywhere. a short overview of the various data encryption methods available today: Sending an email over the internet. Common encryption technologies and tools. Encryption may be implemented at the source, where data is generated. Implement virtual private networks (vpns): Encryption is used to secure. Examples Of Encryption In Transit.
From www.titanfile.com
Securing Data in Transit With Encryption The Ultimate Guide TitanFile Examples Of Encryption In Transit a short overview of the various data encryption methods available today: google works actively with the industry to help bring encryption in transit to everyone, everywhere. Implement virtual private networks (vpns): in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. Sending an email over the internet. Encryption is used to secure devices. Examples Of Encryption In Transit.
From www.slideserve.com
PPT Encryption Protecting Your Data While in Transit PowerPoint Examples Of Encryption In Transit Implement virtual private networks (vpns): here are a few examples of a file in transit: Sending an email over the internet. Two employees exchanging files over a corporate network. best practices for data in transit encryption. Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and. Examples Of Encryption In Transit.
From www.youtube.com
What does encryption of dataintransit and data at rest mean? YouTube Examples Of Encryption In Transit Common encryption technologies and tools. Two employees exchanging files over a corporate network. in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. here are a few examples of a file in transit: encryption at rest refers to the encryption applied to the stored data. Implement virtual private networks (vpns): Encryption may be. Examples Of Encryption In Transit.
From fitsmallbusiness.com
Encryption Atrest & Intransit Explained Benefits & Examples Examples Of Encryption In Transit here are a few examples of a file in transit: a short overview of the various data encryption methods available today: Two employees exchanging files over a corporate network. google works actively with the industry to help bring encryption in transit to everyone, everywhere. Sending an email over the internet. in addition to protecting customer data. Examples Of Encryption In Transit.
From www.redswitches.com
Data At Rest Encryption 6 Best Practices For Data Security Examples Of Encryption In Transit in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. best practices for data in transit encryption. here are a few examples of a file in transit: Encryption may be implemented at the source, where data is generated. Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions. Examples Of Encryption In Transit.
From securityboulevard.com
Symmetric Encryption Algorithms Live Long & Encrypt Security Boulevard Examples Of Encryption In Transit a short overview of the various data encryption methods available today: in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and buying an item from an online retailer, and ensure the privacy. Examples Of Encryption In Transit.
From theunlockr.com
What is Encryption? (& How it Works to Protect Your Data) Examples Of Encryption In Transit encryption at rest refers to the encryption applied to the stored data. Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and buying an item from an online retailer, and ensure the privacy of messages such as emails and texts. google works actively with the industry. Examples Of Encryption In Transit.
From us.norton.com
What is encryption? How it works + types of encryption Norton Examples Of Encryption In Transit Common encryption technologies and tools. a short overview of the various data encryption methods available today: encryption at rest refers to the encryption applied to the stored data. Two employees exchanging files over a corporate network. in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. best practices for data in transit. Examples Of Encryption In Transit.
From sectigostore.com
What Is Asymmetric Encryption & How Does It Work? InfoSec Insights Examples Of Encryption In Transit Common encryption technologies and tools. Two employees exchanging files over a corporate network. Sending an email over the internet. encryption at rest refers to the encryption applied to the stored data. best practices for data in transit encryption. a short overview of the various data encryption methods available today: google works actively with the industry to. Examples Of Encryption In Transit.
From www.securenetconsulting.co.uk
Data in Transit Encryption Examples Of Encryption In Transit Encryption is used to secure devices such as smartphones and personal computers, protect financial transactions such as making a bank deposit and buying an item from an online retailer, and ensure the privacy of messages such as emails and texts. best practices for data in transit encryption. Encryption may be implemented at the source, where data is generated. . Examples Of Encryption In Transit.
From www.youtube.com
The Definitive Guide to Understanding AtRest and InTransit Encryption Examples Of Encryption In Transit Implement virtual private networks (vpns): in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. Encryption may be implemented at the source, where data is generated. encryption at rest refers to the encryption applied to the stored data. here are a few examples of a file in transit: a short overview of. Examples Of Encryption In Transit.
From learn.g2.com
What Does Encryption Mean and Why Is It Important? Examples Of Encryption In Transit in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. google works actively with the industry to help bring encryption in transit to everyone, everywhere. Implement virtual private networks (vpns): here are a few examples of a file in transit: Sending an email over the internet. a short overview of the various. Examples Of Encryption In Transit.
From phoenixnap.com
Data in Transit Encryption Explained phoenixNAP Blog Examples Of Encryption In Transit encryption at rest refers to the encryption applied to the stored data. Common encryption technologies and tools. google works actively with the industry to help bring encryption in transit to everyone, everywhere. best practices for data in transit encryption. Implement virtual private networks (vpns): Encryption is used to secure devices such as smartphones and personal computers, protect. Examples Of Encryption In Transit.
From docs.aws.amazon.com
AWS DataSync encryption in transit AWS DataSync Examples Of Encryption In Transit a short overview of the various data encryption methods available today: Two employees exchanging files over a corporate network. Sending an email over the internet. google works actively with the industry to help bring encryption in transit to everyone, everywhere. in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. best practices. Examples Of Encryption In Transit.
From flo.net
Encryption How to protect data in transit Flō Networks Examples Of Encryption In Transit a short overview of the various data encryption methods available today: Implement virtual private networks (vpns): google works actively with the industry to help bring encryption in transit to everyone, everywhere. in addition to protecting customer data at rest, microsoft uses encryption technologies to protect. Two employees exchanging files over a corporate network. Common encryption technologies and. Examples Of Encryption In Transit.