X Server Unauthenticated Access . If the x client/server facility is not used, disable tcp connections to the x server entirely as the ports identified with this. If the x client/server facility is not used, disable tcp connections to the x server. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. Try following solutions to fix it. Restrict access to this port by using the 'xhost' command. Let us see how to fix this error on linux. It is possible for an attacker to authenticate to the exchange server and gain access to the active directory environment and download. Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. Restrict access to this port by. This error can be caused by various factors. The remote x11 server accepts connection from. An attacker can exploit this flaw to obtain the username and password of a user on the remote host.
from www.cve.news
It is possible for an attacker to authenticate to the exchange server and gain access to the active directory environment and download. If the x client/server facility is not used, disable tcp connections to the x server. Restrict access to this port by. Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. The remote x11 server accepts connection from. Let us see how to fix this error on linux. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. Restrict access to this port by using the 'xhost' command. If the x client/server facility is not used, disable tcp connections to the x server entirely as the ports identified with this. An attacker can exploit this flaw to obtain the username and password of a user on the remote host.
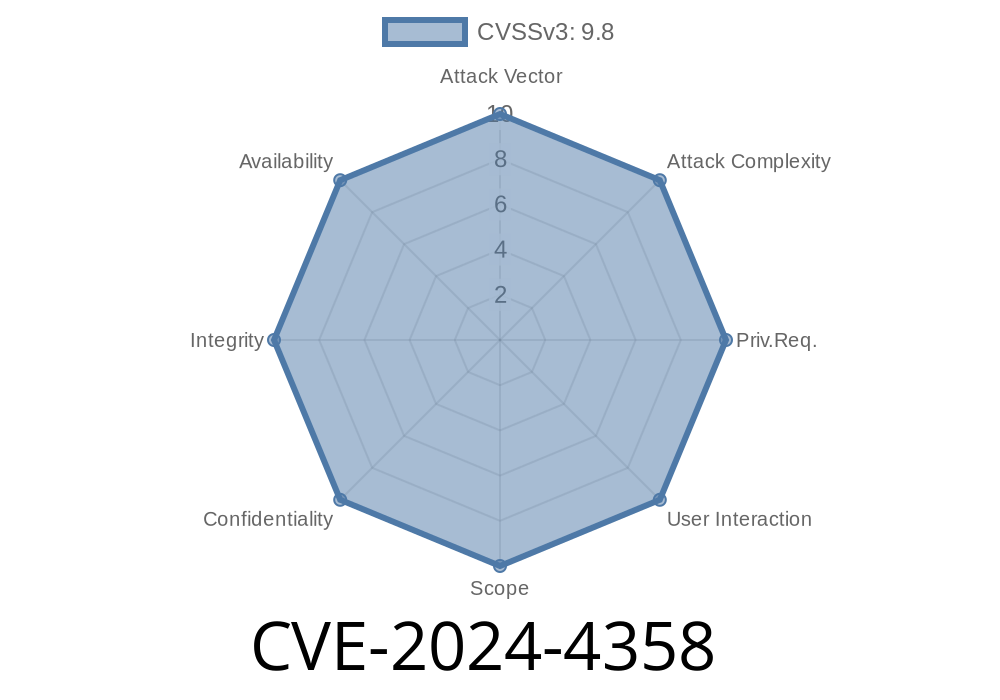
CVE20244358 Unauthenticated Access to Restricted Telerik Report
X Server Unauthenticated Access This error can be caused by various factors. This error can be caused by various factors. Restrict access to this port by. Let us see how to fix this error on linux. An attacker can exploit this flaw to obtain the username and password of a user on the remote host. Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. If the x client/server facility is not used, disable tcp connections to the x server entirely as the ports identified with this. Try following solutions to fix it. The remote x11 server accepts connection from. Restrict access to this port by using the 'xhost' command. It is possible for an attacker to authenticate to the exchange server and gain access to the active directory environment and download. If the x client/server facility is not used, disable tcp connections to the x server.
From support.banyansecurity.io
How Do I Access an SSH Server via MobaXterm? Banyan Security X Server Unauthenticated Access Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. Try following solutions to fix it. This error can be caused by various factors. If the x client/server facility is not used, disable tcp connections to the x server entirely as the ports identified with this. It is possible for an attacker to authenticate to. X Server Unauthenticated Access.
From www.youtube.com
(Solved) You Can't Access This Shared Folder Because Your Organization X Server Unauthenticated Access Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. It is possible for an attacker to authenticate to the exchange server and gain access to the active directory environment and download. An attacker can exploit this flaw to obtain the username and password of a user on the remote host. Let us see how. X Server Unauthenticated Access.
From cert.bournemouth.ac.uk
regreSSHion Remote Unauthenticated Code Execution Vulnerability in X Server Unauthenticated Access If the x client/server facility is not used, disable tcp connections to the x server. Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. Restrict access to this port by. An attacker can exploit. X Server Unauthenticated Access.
From www.youtube.com
ISA Server 2006 SP1 Allow unauthenticated users (non domain users X Server Unauthenticated Access The remote x11 server accepts connection from. Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. Try following solutions to fix it. Let us see how to fix this error on linux. An attacker can exploit this flaw to obtain the username and password of a user on the remote host. If the x. X Server Unauthenticated Access.
From www.petenetlive.com
Cisco Firewall (ASA/PIX) Granting Access to an FTP Server X Server Unauthenticated Access Try following solutions to fix it. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. The remote x11 server accepts connection from. If the x client/server facility is not used, disable tcp connections to the x server. Restrict access to this port by. Creating untrusted clients is cumbersome since. X Server Unauthenticated Access.
From petri.com
Enable Unauthenticated Access to a Windows File Share Petri IT X Server Unauthenticated Access The remote x11 server accepts connection from. Try following solutions to fix it. If the x client/server facility is not used, disable tcp connections to the x server. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. It is possible for an attacker to authenticate to the exchange server. X Server Unauthenticated Access.
From itekblog.com
SSH X11 Forwarding Display using MobaXterm on Windows ITek Blog X Server Unauthenticated Access Restrict access to this port by. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. Try following solutions to fix it. The remote x11 server accepts connection from. Let us see how to fix this error on linux. If the x client/server facility is not used, disable tcp connections. X Server Unauthenticated Access.
From www.youtube.com
Access Your FTP Server from anywhere on the Access Computer X Server Unauthenticated Access If the x client/server facility is not used, disable tcp connections to the x server. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. If the x client/server facility is not used, disable tcp connections to the x server entirely as the ports identified with this. An attacker can. X Server Unauthenticated Access.
From www.raffaelechiatto.com
Soluzione All'errore Di Accesso Ad Una Share You Can't Access This X Server Unauthenticated Access The remote x11 server accepts connection from. Try following solutions to fix it. If the x client/server facility is not used, disable tcp connections to the x server. If the x client/server facility is not used, disable tcp connections to the x server entirely as the ports identified with this. This error can be caused by various factors. An attacker. X Server Unauthenticated Access.
From keiyu.xyz
XサーバーとACCESSをODBC経由で接続をする その2 KEIYU企画 X Server Unauthenticated Access This error can be caused by various factors. Let us see how to fix this error on linux. An attacker can exploit this flaw to obtain the username and password of a user on the remote host. If the x client/server facility is not used, disable tcp connections to the x server entirely as the ports identified with this. Try. X Server Unauthenticated Access.
From dev.classmethod.jp
S3 の サーバーアクセスログを有効したがログが記録されないときの対処方法 DevelopersIO X Server Unauthenticated Access It is possible for an attacker to authenticate to the exchange server and gain access to the active directory environment and download. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. If the x client/server facility is not used, disable tcp connections to the x server entirely as the. X Server Unauthenticated Access.
From www.youtube.com
Ricoh Scan to SFTP Server,FileZilla Server,Scan to ftp,sftp server X Server Unauthenticated Access If the x client/server facility is not used, disable tcp connections to the x server. If the x client/server facility is not used, disable tcp connections to the x server entirely as the ports identified with this. The remote x11 server accepts connection from. Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. Restrict. X Server Unauthenticated Access.
From forum.chirpstack.io
Unauthenticated error="rpc error code = Unauthenticated desc X Server Unauthenticated Access In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. This error can be caused by various factors. Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. Let us see how to fix this error on linux. If the x client/server facility is not. X Server Unauthenticated Access.
From www.cve.news
CVE20244358 Unauthenticated Access to Restricted Telerik Report X Server Unauthenticated Access Restrict access to this port by. If the x client/server facility is not used, disable tcp connections to the x server entirely as the ports identified with this. Let us see how to fix this error on linux. The remote x11 server accepts connection from. An attacker can exploit this flaw to obtain the username and password of a user. X Server Unauthenticated Access.
From keiyu.xyz
XサーバーとACCESSをODBC経由で接続をする その2 KEIYU企画 X Server Unauthenticated Access This error can be caused by various factors. Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. Restrict access to this port by using the 'xhost' command. If the x client/server facility is not used, disable tcp connections to the x server entirely as the ports identified with this. It is possible for an. X Server Unauthenticated Access.
From www.thehackerwire.com
CVE202436991 Critical Windows Splunk Vulnerability Allows X Server Unauthenticated Access Try following solutions to fix it. Let us see how to fix this error on linux. An attacker can exploit this flaw to obtain the username and password of a user on the remote host. If the x client/server facility is not used, disable tcp connections to the x server. Restrict access to this port by. The remote x11 server. X Server Unauthenticated Access.
From trevorsaudi.medium.com
RCE on Unauthenticated Redis server by Trevor saudi Medium X Server Unauthenticated Access Let us see how to fix this error on linux. An attacker can exploit this flaw to obtain the username and password of a user on the remote host. This error can be caused by various factors. Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. Restrict access to this port by. Restrict access. X Server Unauthenticated Access.
From support-eu.wd.com
My Cloud OS 5 & Home Share Access Failure Organization Policies X Server Unauthenticated Access Let us see how to fix this error on linux. Try following solutions to fix it. This error can be caused by various factors. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. An. X Server Unauthenticated Access.
From www.youtube.com
FTP Server Not Working How to Fix FTP Server Problem windows 11 X Server Unauthenticated Access An attacker can exploit this flaw to obtain the username and password of a user on the remote host. Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. Restrict access to this port by. Try following solutions to fix it. This error can be caused by various factors. In this article, we are going. X Server Unauthenticated Access.
From www.raffaelechiatto.com
Soluzione All'errore Di Accesso Ad Una Share You Can't Access This X Server Unauthenticated Access An attacker can exploit this flaw to obtain the username and password of a user on the remote host. If the x client/server facility is not used, disable tcp connections to the x server entirely as the ports identified with this. Try following solutions to fix it. This error can be caused by various factors. In this article, we are. X Server Unauthenticated Access.
From www.kapilarya.com
FIX You Can't Access This Shared Folder Because Your Organization's X Server Unauthenticated Access In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. It is possible for an attacker to authenticate to the exchange server and gain access to the active directory environment and download. The remote x11 server accepts connection from. This error can be caused by various factors. Let us see. X Server Unauthenticated Access.
From curity.io
SPA using the Token Handler Pattern Curity Identity Server X Server Unauthenticated Access If the x client/server facility is not used, disable tcp connections to the x server. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. Restrict access to this port by using the 'xhost' command. The remote x11 server accepts connection from. It is possible for an attacker to authenticate. X Server Unauthenticated Access.
From trevorsaudi.medium.com
RCE on Unauthenticated Redis server by Trevor saudi Medium X Server Unauthenticated Access If the x client/server facility is not used, disable tcp connections to the x server. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. The remote x11 server accepts connection from. An attacker can exploit this flaw to obtain the username and password of a user on the remote. X Server Unauthenticated Access.
From assist.plus.konicaminolta.asia
Error organization's security policies block unauthenticated guess X Server Unauthenticated Access Restrict access to this port by. Restrict access to this port by using the 'xhost' command. Try following solutions to fix it. This error can be caused by various factors. It is possible for an attacker to authenticate to the exchange server and gain access to the active directory environment and download. In this article, we are going to see. X Server Unauthenticated Access.
From moremeng.in.th
เปลี่ยนการตั้งค่า Scan to FTP ของเครื่อง RICOH IM C2000 • MoreMeng.in.th X Server Unauthenticated Access It is possible for an attacker to authenticate to the exchange server and gain access to the active directory environment and download. If the x client/server facility is not used, disable tcp connections to the x server entirely as the ports identified with this. Restrict access to this port by. If the x client/server facility is not used, disable tcp. X Server Unauthenticated Access.
From trevorsaudi.medium.com
RCE on Unauthenticated Redis server by Trevor saudi Medium X Server Unauthenticated Access In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. This error can be caused by various factors. Restrict access to this port by. Restrict access to this port by using the 'xhost' command. If the x client/server facility is not used, disable tcp connections to the x server. It. X Server Unauthenticated Access.
From www.raffaelechiatto.com
Soluzione All'errore Di Accesso Ad Una Share You Can't Access This X Server Unauthenticated Access If the x client/server facility is not used, disable tcp connections to the x server entirely as the ports identified with this. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. It is possible for an attacker to authenticate to the exchange server and gain access to the active. X Server Unauthenticated Access.
From blog.qualys.com
regreSSHion Remote Unauthenticated Code Execution Vulnerability in X Server Unauthenticated Access The remote x11 server accepts connection from. Try following solutions to fix it. If the x client/server facility is not used, disable tcp connections to the x server. It is possible for an attacker to authenticate to the exchange server and gain access to the active directory environment and download. Restrict access to this port by. If the x client/server. X Server Unauthenticated Access.
From www.youtube.com
you cant access this shared folder because your organization's security X Server Unauthenticated Access If the x client/server facility is not used, disable tcp connections to the x server. Restrict access to this port by using the 'xhost' command. Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with.. X Server Unauthenticated Access.
From help.ui.com
Intro to Networking AAA, 802.1X, EAP & RADIUS Ubiquiti Help Center X Server Unauthenticated Access If the x client/server facility is not used, disable tcp connections to the x server. Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. An attacker can exploit this flaw to obtain the username and password of a user on the remote host. The remote x11 server accepts connection from. It is possible for. X Server Unauthenticated Access.
From forum.bubble.io
API Connector OAuth Service Unauthenticated even with Generated Access X Server Unauthenticated Access It is possible for an attacker to authenticate to the exchange server and gain access to the active directory environment and download. Creating untrusted clients is cumbersome since cookie authentications must be generated using a protocol request. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. This error can. X Server Unauthenticated Access.
From forum.bubble.io
API Connector OAuth Service Unauthenticated even with Generated Access X Server Unauthenticated Access An attacker can exploit this flaw to obtain the username and password of a user on the remote host. This error can be caused by various factors. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. It is possible for an attacker to authenticate to the exchange server and. X Server Unauthenticated Access.
From www.horizon3.ai
Are Your Clusters Configured Properly? Horizon3.ai X Server Unauthenticated Access If the x client/server facility is not used, disable tcp connections to the x server entirely as the ports identified with this. If the x client/server facility is not used, disable tcp connections to the x server. This error can be caused by various factors. It is possible for an attacker to authenticate to the exchange server and gain access. X Server Unauthenticated Access.
From www.nedapsecurity.com
802.1X Brings Extra Security to Your AEOS System Nedap X Server Unauthenticated Access Restrict access to this port by using the 'xhost' command. This error can be caused by various factors. Try following solutions to fix it. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. It is possible for an attacker to authenticate to the exchange server and gain access to. X Server Unauthenticated Access.
From community.sophos.com
unauthenticated users can use LINE Message Discussions Sophos X Server Unauthenticated Access Restrict access to this port by using the 'xhost' command. This error can be caused by various factors. In this article, we are going to see how to exploit the x11server unauthenticated access vulnerability which is associated with. Try following solutions to fix it. If the x client/server facility is not used, disable tcp connections to the x server entirely. X Server Unauthenticated Access.