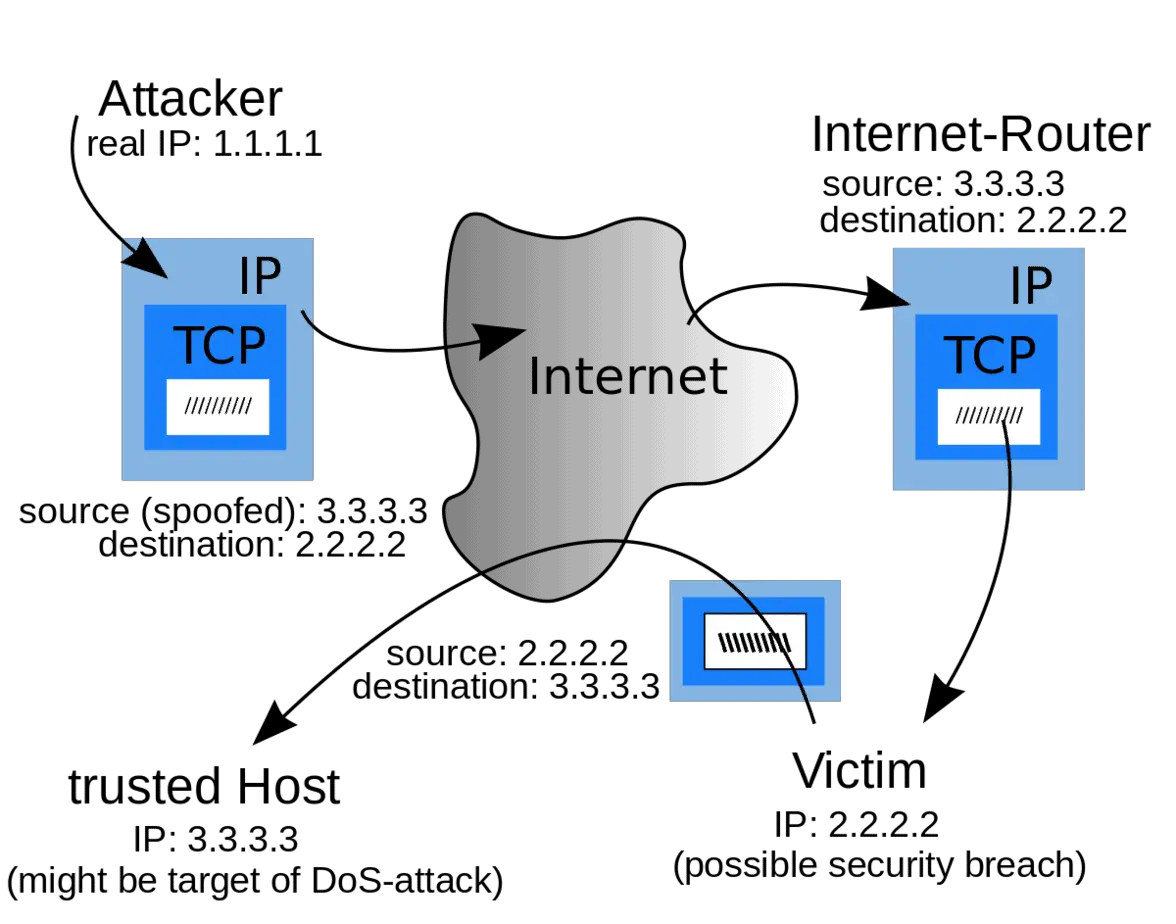
Local Network Ip Spoofing . Learn about the types, examples, and methods of ip. Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to. Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Ip spoofing is a technique used by hackers to gain unauthorized access to computers by sending messages with fake ip addresses. Ip spoofing is a method in which tcp/ip or udp/ip data packets are sent with a fake sender address. You created a packet with fake ip address and a fake mac address (associated with the fake ip), so that you both spoofed the packet source and.
from networkencyclopedia.com
You created a packet with fake ip address and a fake mac address (associated with the fake ip), so that you both spoofed the packet source and. Ip spoofing is a technique used by hackers to gain unauthorized access to computers by sending messages with fake ip addresses. Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Learn about the types, examples, and methods of ip. Ip spoofing is a method in which tcp/ip or udp/ip data packets are sent with a fake sender address. Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to.
What is an IP Spoofing Attack? NETWORK ENCYCLOPEDIA
Local Network Ip Spoofing Ip spoofing is a technique used by hackers to gain unauthorized access to computers by sending messages with fake ip addresses. You created a packet with fake ip address and a fake mac address (associated with the fake ip), so that you both spoofed the packet source and. Ip spoofing is a method in which tcp/ip or udp/ip data packets are sent with a fake sender address. Learn about the types, examples, and methods of ip. Ip spoofing is a technique used by hackers to gain unauthorized access to computers by sending messages with fake ip addresses. Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to.
From www.pubconcierge.com
What is IP Spoofing? How it Works and 6 Steps to Prevent it Local Network Ip Spoofing Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Learn about the types, examples, and methods of ip. You created a packet with fake ip address and a fake mac address (associated with the fake ip), so that you both spoofed the packet source. Local Network Ip Spoofing.
From theruntime.com
17 Most Common IP Spoofing Tools in 2024 The Run Time Local Network Ip Spoofing Ip spoofing is a technique used by hackers to gain unauthorized access to computers by sending messages with fake ip addresses. Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source. Local Network Ip Spoofing.
From www.thesecuritybuddy.com
What is ARP spoofing? The Security Buddy Local Network Ip Spoofing Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Ip spoofing is a technique used by hackers to gain unauthorized access to computers by sending messages with fake ip addresses. You created a packet with fake ip address and a fake mac address (associated. Local Network Ip Spoofing.
From www.collidu.com
IP Spoofing PowerPoint and Google Slides Template PPT Slides Local Network Ip Spoofing Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to. Learn about the types, examples, and methods of ip. Ip spoofing is a method. Local Network Ip Spoofing.
From www.youtube.com
Ip spoofing in network security YouTube Local Network Ip Spoofing Ip spoofing is a method in which tcp/ip or udp/ip data packets are sent with a fake sender address. Learn about the types, examples, and methods of ip. Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Internet protocol (ip) spoofing is a type. Local Network Ip Spoofing.
From www.vrogue.co
How Ip Spoofing Works What Is Ip Spoofing And How To vrogue.co Local Network Ip Spoofing You created a packet with fake ip address and a fake mac address (associated with the fake ip), so that you both spoofed the packet source and. Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to. Ip spoofing, also known as ip address. Local Network Ip Spoofing.
From nordvpn.com
Wat is IP spoofing en hoe kun je het voorkomen? NordVPN Local Network Ip Spoofing Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to. Ip spoofing is a networking attack that involves falsifying. Local Network Ip Spoofing.
From people.scs.carleton.ca
IP Address Spoofing Local Network Ip Spoofing You created a packet with fake ip address and a fake mac address (associated with the fake ip), so that you both spoofed the packet source and. Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Learn about the types, examples, and methods of. Local Network Ip Spoofing.
From topdev.vn
Tìm hiểu thêm về HTTP/3 và so sánh với HTTP2 TopDev Local Network Ip Spoofing Ip spoofing is a technique used by hackers to gain unauthorized access to computers by sending messages with fake ip addresses. Ip spoofing is a method in which tcp/ip or udp/ip data packets are sent with a fake sender address. Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks.. Local Network Ip Spoofing.
From www.youtube.com
What is IP Spoofing? YouTube Local Network Ip Spoofing Ip spoofing is a technique used by hackers to gain unauthorized access to computers by sending messages with fake ip addresses. Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. Learn about the types, examples, and methods of ip. Ip spoofing, also known as ip address spoofing, is a. Local Network Ip Spoofing.
From www.youtube.com
Dns Spoofing on local network.avi YouTube Local Network Ip Spoofing Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. Ip spoofing is a method in which tcp/ip or udp/ip data packets are sent with a fake sender address. Learn about the types, examples, and methods of ip. Internet protocol (ip) spoofing is a type of malicious attack where the. Local Network Ip Spoofing.
From networkhutline.com
What is IP Spoofing? How To Prevent It? Network Hutline Local Network Ip Spoofing Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Learn about the types, examples, and methods of ip. Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to.. Local Network Ip Spoofing.
From gridinsoft.com
IP spoofing What is IP Spoofing Attack? Gridinsoft Blogs Local Network Ip Spoofing Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to. Learn about the types, examples, and methods of ip.. Local Network Ip Spoofing.
From www.vrogue.co
What Is Spoofing Attack How Does Spoofing Work Sangfo vrogue.co Local Network Ip Spoofing Ip spoofing is a technique used by hackers to gain unauthorized access to computers by sending messages with fake ip addresses. Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to. Learn about the types, examples, and methods of ip. Ip spoofing, also known. Local Network Ip Spoofing.
From www.valimail.com
Phishing vs. Spoofing What’s the Difference? Valimail Local Network Ip Spoofing Ip spoofing is a method in which tcp/ip or udp/ip data packets are sent with a fake sender address. Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Learn about the types, examples, and methods of ip. Ip spoofing is a networking attack that. Local Network Ip Spoofing.
From www.comparitech.com
ARP poisoning/spoofing How to detect & prevent it Comparitech Local Network Ip Spoofing Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Learn about the types, examples, and methods of ip. Ip spoofing is a method in which tcp/ip or udp/ip data packets are sent with a fake sender address. Internet protocol (ip) spoofing is a type. Local Network Ip Spoofing.
From www.slideshare.net
Ip spoofing ppt Local Network Ip Spoofing Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to. You created a packet with fake ip address and a fake mac address (associated. Local Network Ip Spoofing.
From witestlab.poly.edu
Redirect traffic to a wrong or fake site with DNS spoofing on a LAN Local Network Ip Spoofing You created a packet with fake ip address and a fake mac address (associated with the fake ip), so that you both spoofed the packet source and. Ip spoofing is a technique used by hackers to gain unauthorized access to computers by sending messages with fake ip addresses. Learn about the types, examples, and methods of ip. Ip spoofing, also. Local Network Ip Spoofing.
From fossbytes.com
What Is IP Spoofing And Denial Of Service (DOS) Attack? Local Network Ip Spoofing Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to. Ip spoofing is a technique used by hackers to gain unauthorized access to computers by sending messages with fake ip addresses. Ip spoofing is a networking attack that involves falsifying the source ip address. Local Network Ip Spoofing.
From www.scribd.com
Ip Spoofing Ppt Ip Address Routing Local Network Ip Spoofing You created a packet with fake ip address and a fake mac address (associated with the fake ip), so that you both spoofed the packet source and. Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Ip spoofing is a method in which tcp/ip. Local Network Ip Spoofing.
From theruntime.com
What is Spoofing in Computer & How to Prevent It? The Run Time Local Network Ip Spoofing Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. Learn about the types, examples, and methods of ip. Internet protocol (ip) spoofing is a. Local Network Ip Spoofing.
From avinetworks.com
What is IP Spoofing? Avi Networks Local Network Ip Spoofing Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to. Learn about the types, examples, and methods of ip. Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header.. Local Network Ip Spoofing.
From nordvpn.com
Qu'estce que l'IP spoofing ? NordVPN Local Network Ip Spoofing You created a packet with fake ip address and a fake mac address (associated with the fake ip), so that you both spoofed the packet source and. Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to. Ip spoofing is a method in which. Local Network Ip Spoofing.
From www.pinterest.com
What is IP spoofing and how it works? Ddos attack, Ip address Local Network Ip Spoofing Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Ip spoofing is a method in which tcp/ip or udp/ip data packets are sent with a fake sender address. Learn about the types, examples, and methods of ip. Ip spoofing is a networking attack that. Local Network Ip Spoofing.
From networkencyclopedia.com
What is an IP Spoofing Attack? NETWORK ENCYCLOPEDIA Local Network Ip Spoofing Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. Ip spoofing is a method in which tcp/ip or udp/ip data packets are sent with a fake sender address. Learn about the types, examples, and methods of ip. You created a packet with fake ip address and a fake mac. Local Network Ip Spoofing.
From www.researchgate.net
(PDF) Detecting and Preventing IP Spoofing and Local Area Network Local Network Ip Spoofing Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. You created a packet with fake ip address and a fake mac address (associated with. Local Network Ip Spoofing.
From www.pinterest.com
ARP spoofing and IP spoofing both rely on the attack being connected to Local Network Ip Spoofing You created a packet with fake ip address and a fake mac address (associated with the fake ip), so that you both spoofed the packet source and. Ip spoofing is a method in which tcp/ip or udp/ip data packets are sent with a fake sender address. Ip spoofing is a technique used by hackers to gain unauthorized access to computers. Local Network Ip Spoofing.
From www.ipxo.com
What Is IP Spoofing, and How To Protect Yourself Against It IPXO Local Network Ip Spoofing Learn about the types, examples, and methods of ip. Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. Ip spoofing is a technique used by hackers to gain unauthorized access to computers by sending messages with fake ip addresses. Internet protocol (ip) spoofing is a type of malicious attack. Local Network Ip Spoofing.
From www.cyberyodha.org
What is spoofing? Local Network Ip Spoofing You created a packet with fake ip address and a fake mac address (associated with the fake ip), so that you both spoofed the packet source and. Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Internet protocol (ip) spoofing is a type of. Local Network Ip Spoofing.
From www.geekboots.com
What is IP spoofing? Geekboots Story Local Network Ip Spoofing Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. Ip spoofing is a method in which tcp/ip or udp/ip data packets are sent with a fake sender address. Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets. Local Network Ip Spoofing.
From www.appknox.com
Preventing & Identifying ARP Poisoning or Spoofing Attacks Local Network Ip Spoofing Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. You created a packet with fake ip address and a fake mac address (associated with the fake ip), so that you both spoofed the packet source and. Ip spoofing is a method in which tcp/ip or udp/ip data packets are. Local Network Ip Spoofing.
From www.mdpi.com
Computers Free FullText IP Spoofing In and Out of the Public Cloud Local Network Ip Spoofing Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets to make it difficult to. Ip spoofing is a method in which tcp/ip or udp/ip data packets are sent with a fake sender address. You created a packet with fake ip address and a fake mac address (associated with. Local Network Ip Spoofing.
From bkhost.vn
IP spoofing là gì? Cách phát hiện và ngăn chặn BKHOST Local Network Ip Spoofing You created a packet with fake ip address and a fake mac address (associated with the fake ip), so that you both spoofed the packet source and. Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. Ip spoofing is a technique used by hackers to gain unauthorized access to. Local Network Ip Spoofing.
From www.pinterest.com
IP Spoofing (IP Address Spoofing) Diagram Session hijacking, Ip Local Network Ip Spoofing Ip spoofing is a networking attack that involves falsifying the source ip address of packets to deceive hosts or networks. Ip spoofing is a method in which tcp/ip or udp/ip data packets are sent with a fake sender address. Internet protocol (ip) spoofing is a type of malicious attack where the threat actor hides the true source of ip packets. Local Network Ip Spoofing.
From www.thesecuritybuddy.com
How does IP spoofing work? The Security Buddy Local Network Ip Spoofing You created a packet with fake ip address and a fake mac address (associated with the fake ip), so that you both spoofed the packet source and. Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header. Ip spoofing is a networking attack that involves. Local Network Ip Spoofing.