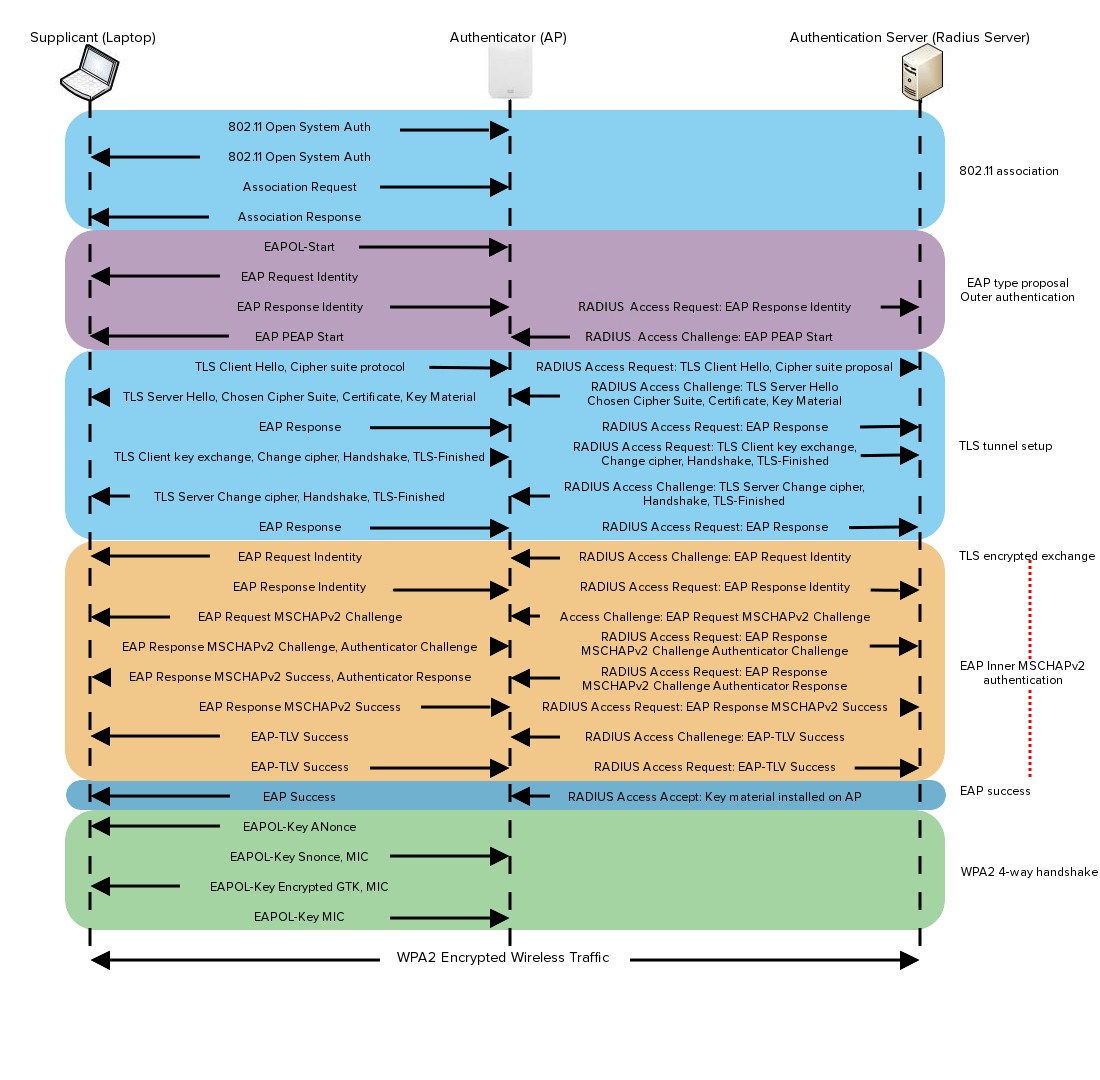
Radius Vs Eap . Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In this article, we’ll cover a baseline of authentication protocols: In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. We’ll cover what the protocol is, give a detailed. In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual authentication/authorization.
from documentation.meraki.com
We’ll cover what the protocol is, give a detailed. Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual authentication/authorization. In this article, we’ll cover a baseline of authentication protocols:
Configuring RADIUS Authentication with WPA2Enterprise Cisco Meraki
Radius Vs Eap Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In this article, we’ll cover a baseline of authentication protocols: In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual authentication/authorization. Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. We’ll cover what the protocol is, give a detailed.
From www.slideserve.com
PPT RADIUS PowerPoint Presentation, free download ID7023684 Radius Vs Eap Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. Instead of configuring numerous separate networking. Radius Vs Eap.
From www.securew2.com
What's the Difference between RADIUS, TLS, and EAPTLS? Radius Vs Eap Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. In this article, we’ll cover a baseline of authentication protocols:. Radius Vs Eap.
From studylib.net
Understanding EAPMD5 Authentication with RADIUS Radius Vs Eap In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. In this article, we’ll cover a baseline of authentication protocols: We’ll cover what the protocol is, give a detailed. Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized. Radius Vs Eap.
From best-route.blogspot.com
Best Route IEEE 802.1X, EAP and RADIUS. Whats all this and how they Radius Vs Eap In this article, we’ll cover a baseline of authentication protocols: In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi.. Radius Vs Eap.
From cybr.com
Authentication Protocols (802.1X, EAP/PEAP, EAPFAST/TLS/TTLS, and Radius Vs Eap In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual authentication/authorization. In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. In this article, we’ll cover a baseline of. Radius Vs Eap.
From www.researchgate.net
WPA2/EAPTLS with RADIUS Download Scientific Diagram Radius Vs Eap In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual authentication/authorization. Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In radius authentication, when a user attempts to access a. Radius Vs Eap.
From www.slideserve.com
PPT Protokół RADIUS i jego zastosowania PowerPoint Presentation, free Radius Vs Eap Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. We’ll cover what the protocol is, give a detailed. In conclusion, radius. Radius Vs Eap.
From www.portnox.com
Monitoring 802.1X EAP What You Need to Know Portnox Radius Vs Eap We’ll cover what the protocol is, give a detailed. In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual authentication/authorization. Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. In radius authentication, when a. Radius Vs Eap.
From www.cisco.com
External RADIUS Server EAP Authentication with 5760/3850 WLC Radius Vs Eap Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual authentication/authorization. In this article, we’ll cover a baseline of authentication protocols:. Radius Vs Eap.
From www.slideserve.com
PPT Protokół RADIUS i jego zastosowania PowerPoint Presentation, free Radius Vs Eap Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. In radius authentication, when a user attempts to access a network, the. Radius Vs Eap.
From www.slideserve.com
PPT 801.11 WiFi Sécurité PowerPoint Presentation, free download ID Radius Vs Eap In this article, we’ll cover a baseline of authentication protocols: In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi.. Radius Vs Eap.
From www.securew2.com
What's the Difference between RADIUS, TLS, and EAPTLS? Radius Vs Eap In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. In this article, we’ll cover a baseline of authentication protocols: In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the. Radius Vs Eap.
From www.cloudradius.com
How 802.1X Network Authentication Works InDepth Guide Cloud RADIUS Radius Vs Eap Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. We’ll cover what the protocol is, give a detailed. In this article, we’ll cover a baseline of authentication protocols: In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be. Radius Vs Eap.
From cybr.com
Authentication Protocols (802.1X, EAP/PEAP, EAPFAST/TLS/TTLS, and Radius Vs Eap In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. Instead of configuring numerous separate networking. Radius Vs Eap.
From techhub.hpe.com
EAP over RADIUS Radius Vs Eap In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual authentication/authorization. We’ll cover what the protocol is, give a detailed. Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In. Radius Vs Eap.
From documentation.meraki.com
RADIUS WPA2Enterprise With EAPTLS Using Microsoft NPS Cisco Meraki Radius Vs Eap Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In this article, we’ll cover a baseline of authentication protocols: Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. In conclusion,. Radius Vs Eap.
From github.com
GitHub TanNang/EAPRadiusV2ray (Still in developing) EAP Radius Vs Eap Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. In this article, we’ll cover a. Radius Vs Eap.
From learn.microsoft.com
Use EAPTLS Azure Sphere Microsoft Learn Radius Vs Eap In this article, we’ll cover a baseline of authentication protocols: In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual authentication/authorization. We’ll cover what the protocol is, give a detailed. Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding. Radius Vs Eap.
From www.slideserve.com
PPT RADIUS PowerPoint Presentation, free download ID1227176 Radius Vs Eap Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual authentication/authorization. We’ll cover what the protocol is, give a detailed. In. Radius Vs Eap.
From networkwizkid.com
Capturing EAPOL and RADIUS Using Wireshark Radius Vs Eap Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. In this article, we’ll cover a baseline of authentication protocols: In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials.. Radius Vs Eap.
From www.cloudradius.com
Setting Up EAPTLS WPA2Enterprise with Cisco Wireless LAN Controller Radius Vs Eap In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual authentication/authorization. In this article, we’ll cover a baseline of. Radius Vs Eap.
From www.expertnetworkconsultant.com
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Radius Vs Eap In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual authentication/authorization. We’ll cover what the protocol is, give a detailed. Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. In radius authentication, when a. Radius Vs Eap.
From help.ui.com
Intro to Networking AAA, 802.1X, EAP & RADIUS Ubiquiti Help Center Radius Vs Eap Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In this article, we’ll cover a baseline of authentication protocols: In conclusion,. Radius Vs Eap.
From documentation.meraki.com
Configuring RADIUS Authentication with WPA2Enterprise Cisco Meraki Radius Vs Eap Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual authentication/authorization. We’ll cover what the protocol is, give a detailed. Instead. Radius Vs Eap.
From www.cloudradius.com
How 802.1X Network Authentication Works InDepth Guide Cloud RADIUS Radius Vs Eap We’ll cover what the protocol is, give a detailed. Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In this article, we’ll cover a baseline of authentication protocols: Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for. Radius Vs Eap.
From www.cloudradius.com
Configure EAPTLS Authentication Cloud RADIUS Radius Vs Eap Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In this article, we’ll cover a baseline of authentication protocols: We’ll cover what the protocol is, give a detailed. Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for. Radius Vs Eap.
From www.youtube.com
Securing RADIUS with EAPTLS (Wired WPA2 Enterprise) [Windows Server Radius Vs Eap In this article, we’ll cover a baseline of authentication protocols: We’ll cover what the protocol is, give a detailed. Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to. Radius Vs Eap.
From www.pinterest.com
WiFi Authentication with Foxpass RADIUS Wifi, Wireless networking Radius Vs Eap In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual authentication/authorization. Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. We’ll cover what the protocol is, give a detailed. Instead. Radius Vs Eap.
From www.wirelessnewbies.com
802.1x Authentication Radius Vs Eap In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. We’ll cover what the protocol is, give a detailed. In conclusion, radius can be seen as a transport and control (for the nas) protocol, and eap can be seen as the actual. Radius Vs Eap.
From www.securew2.com
What is EAPTLS? Radius Vs Eap In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. In this article, we’ll cover a baseline of authentication protocols: Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi.. Radius Vs Eap.
From ipcisco.com
802.1x Authentication What is 802.1x Port Based Access Control Radius Vs Eap Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. Because the supplicant and authentication server technically use separate protocols. Radius Vs Eap.
From igm.univ-mlv.fr
Exposé 802.1x Radius Vs Eap In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. In conclusion, radius can be seen. Radius Vs Eap.
From www.youtube.com
YouTube Radius Vs Eap We’ll cover what the protocol is, give a detailed. In this article, we’ll cover a baseline of authentication protocols: Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the authenticator as a. Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for. Radius Vs Eap.
From www.yumpu.com
Présentation de RADIUS, EAP et FreeRADIUS 3ème partie Radius Vs Eap Instead of configuring numerous separate networking and infrastructure devices, radius is a centralized mechanism for faster onboarding of new devices to wifi. In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. We’ll cover what the protocol is, give a detailed. Because. Radius Vs Eap.
From www.cisco.com
EAPFAST Authentication with Wireless LAN Controllers and External Radius Vs Eap We’ll cover what the protocol is, give a detailed. In radius authentication, when a user attempts to access a network, the radius client sends an authentication request to the radius server, which then verifies the user's credentials. Because the supplicant and authentication server technically use separate protocols for 802.1x authentication (eap and radius, respectively), it can help to consider the. Radius Vs Eap.