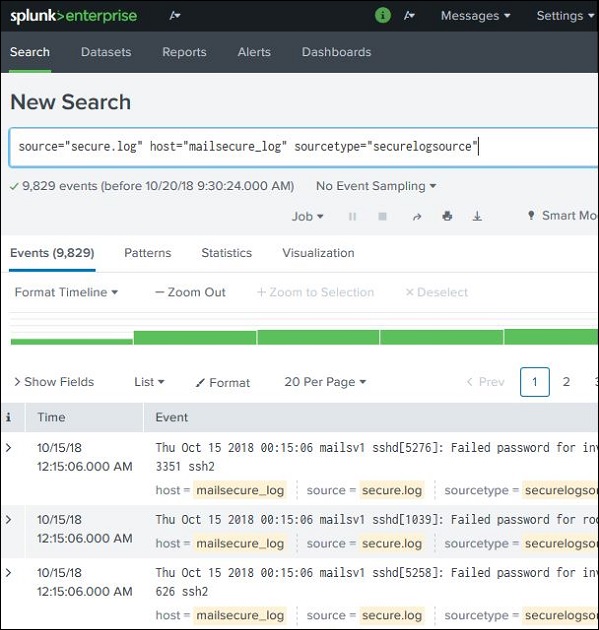
Splunk Search Query Group By Field . | transaction user | table user, src, dest, logontype |. And if you don't want events with no dest, you should add dest=* to your search query. You can assign one or more tags to any field/value combination,. A tag is a knowledge object that enables you to search for events that contain particular field values. Once you have your results, click the export button found above the results table on the splunk interface. For example, we receive events from three different hosts: So, here's one way you can mask the reallocation with a display location by checking to see if the reallocation is the same. Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. For the stats command, fields that you specify in the by clause group the results based on those fields. Search criteria | extract fields if necessary | stats or timechart Perform your search and apply your group by in splunk.
from www.tutorialspoint.com
Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. For the stats command, fields that you specify in the by clause group the results based on those fields. A tag is a knowledge object that enables you to search for events that contain particular field values. Once you have your results, click the export button found above the results table on the splunk interface. Perform your search and apply your group by in splunk. So, here's one way you can mask the reallocation with a display location by checking to see if the reallocation is the same. For example, we receive events from three different hosts: You can assign one or more tags to any field/value combination,. | transaction user | table user, src, dest, logontype |. Search criteria | extract fields if necessary | stats or timechart
Splunk Basic Search
Splunk Search Query Group By Field A tag is a knowledge object that enables you to search for events that contain particular field values. You can assign one or more tags to any field/value combination,. Search criteria | extract fields if necessary | stats or timechart So, here's one way you can mask the reallocation with a display location by checking to see if the reallocation is the same. | transaction user | table user, src, dest, logontype |. For example, we receive events from three different hosts: Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. Perform your search and apply your group by in splunk. Once you have your results, click the export button found above the results table on the splunk interface. And if you don't want events with no dest, you should add dest=* to your search query. A tag is a knowledge object that enables you to search for events that contain particular field values. For the stats command, fields that you specify in the by clause group the results based on those fields.
From www.primesoft.net
Retrospective Dashboard Queries in Splunk PrimeSoft Solutions Inc. Splunk Search Query Group By Field Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. You can assign one or more tags to any field/value combination,. Once you have your results, click the export button found above the results table on the splunk interface. For example, we receive events from three different hosts: |. Splunk Search Query Group By Field.
From stackoverflow.com
Splunk query Total or Count by field Stack Overflow Splunk Search Query Group By Field For the stats command, fields that you specify in the by clause group the results based on those fields. A tag is a knowledge object that enables you to search for events that contain particular field values. And if you don't want events with no dest, you should add dest=* to your search query. Perform your search and apply your. Splunk Search Query Group By Field.
From www.primesoft.net
Retrospective Dashboard Queries in Splunk PrimeSoft Solutions Inc. Splunk Search Query Group By Field You can assign one or more tags to any field/value combination,. | transaction user | table user, src, dest, logontype |. Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. For the stats command, fields that you specify in the by clause group the results based on those. Splunk Search Query Group By Field.
From www.tutorialspoint.com
Splunk Basic Search Splunk Search Query Group By Field Once you have your results, click the export button found above the results table on the splunk interface. Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. A tag is a knowledge object that enables you to search for events that contain particular field values. For example, we. Splunk Search Query Group By Field.
From community.splunk.com
Solved Splunk stats count group by multiple fields Splunk Community Splunk Search Query Group By Field Once you have your results, click the export button found above the results table on the splunk interface. For the stats command, fields that you specify in the by clause group the results based on those fields. | transaction user | table user, src, dest, logontype |. Grouping search results the from command also supports aggregation using the group by. Splunk Search Query Group By Field.
From www.stratosphereips.org
Getting Started With Splunk Basic Searching & Data Viz — Stratosphere IPS Splunk Search Query Group By Field Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. A tag is a knowledge object that enables you to search for events that contain particular field values. For example, we receive events from three different hosts: Perform your search and apply your group by in splunk. Once you. Splunk Search Query Group By Field.
From www.aldeid.com
Splunk aldeid Splunk Search Query Group By Field For the stats command, fields that you specify in the by clause group the results based on those fields. Perform your search and apply your group by in splunk. Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. | transaction user | table user, src, dest, logontype |.. Splunk Search Query Group By Field.
From docs.gravwell.io
Splunk Query Node — Gravwell v5.5.5 documentation Splunk Search Query Group By Field Search criteria | extract fields if necessary | stats or timechart A tag is a knowledge object that enables you to search for events that contain particular field values. For example, we receive events from three different hosts: You can assign one or more tags to any field/value combination,. Once you have your results, click the export button found above. Splunk Search Query Group By Field.
From padakuu.com
Splunk Basic Search Splunk Search Query Group By Field | transaction user | table user, src, dest, logontype |. You can assign one or more tags to any field/value combination,. Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. Search criteria | extract fields if necessary | stats or timechart And if you don't want events with. Splunk Search Query Group By Field.
From blog.scottlogic.com
Putting your machine data to use with Splunk Splunk Search Query Group By Field A tag is a knowledge object that enables you to search for events that contain particular field values. Search criteria | extract fields if necessary | stats or timechart Once you have your results, click the export button found above the results table on the splunk interface. You can assign one or more tags to any field/value combination,. | transaction. Splunk Search Query Group By Field.
From community.splunk.com
How read the data from splunk using search query Splunk Community Splunk Search Query Group By Field Once you have your results, click the export button found above the results table on the splunk interface. Perform your search and apply your group by in splunk. Search criteria | extract fields if necessary | stats or timechart So, here's one way you can mask the reallocation with a display location by checking to see if the reallocation is. Splunk Search Query Group By Field.
From www.stationx.net
Splunk Cheat Sheet Search and Query Commands Splunk Search Query Group By Field And if you don't want events with no dest, you should add dest=* to your search query. You can assign one or more tags to any field/value combination,. Perform your search and apply your group by in splunk. Search criteria | extract fields if necessary | stats or timechart Grouping search results the from command also supports aggregation using the. Splunk Search Query Group By Field.
From docs.splunk.com
Basic searches and search results Splunk Documentation Splunk Search Query Group By Field So, here's one way you can mask the reallocation with a display location by checking to see if the reallocation is the same. Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. And if you don't want events with no dest, you should add dest=* to your search. Splunk Search Query Group By Field.
From kinneygroup.com
Everything You Need To Know About Splunk Search Modes Kinney Group Splunk Search Query Group By Field A tag is a knowledge object that enables you to search for events that contain particular field values. So, here's one way you can mask the reallocation with a display location by checking to see if the reallocation is the same. Once you have your results, click the export button found above the results table on the splunk interface. You. Splunk Search Query Group By Field.
From www.tutorialspoint.com
Splunk Search Language Splunk Search Query Group By Field For the stats command, fields that you specify in the by clause group the results based on those fields. For example, we receive events from three different hosts: Search criteria | extract fields if necessary | stats or timechart Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in.. Splunk Search Query Group By Field.
From queirozf.com
Splunk Groupby Examples with Stats Splunk Search Query Group By Field A tag is a knowledge object that enables you to search for events that contain particular field values. Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. And if you don't want events with no dest, you should add dest=* to your search query. Perform your search and. Splunk Search Query Group By Field.
From karunsubramanian.com
Two Useful Settings to Improve Splunk Search Interface Splunk Search Query Group By Field For the stats command, fields that you specify in the by clause group the results based on those fields. A tag is a knowledge object that enables you to search for events that contain particular field values. Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. And if. Splunk Search Query Group By Field.
From hodgkins.io
Splunk Spotlight The Lookup Command Splunk Search Query Group By Field Perform your search and apply your group by in splunk. You can assign one or more tags to any field/value combination,. For example, we receive events from three different hosts: A tag is a knowledge object that enables you to search for events that contain particular field values. | transaction user | table user, src, dest, logontype |. Search criteria. Splunk Search Query Group By Field.
From www.rocschool.com
Splunk 基本搜索 Splunk Search Query Group By Field So, here's one way you can mask the reallocation with a display location by checking to see if the reallocation is the same. Search criteria | extract fields if necessary | stats or timechart You can assign one or more tags to any field/value combination,. Grouping search results the from command also supports aggregation using the group by clause in. Splunk Search Query Group By Field.
From thesecmaster.com
Install Splunk Search Head on Linux StepbyStep Guide Splunk Search Query Group By Field | transaction user | table user, src, dest, logontype |. Once you have your results, click the export button found above the results table on the splunk interface. So, here's one way you can mask the reallocation with a display location by checking to see if the reallocation is the same. And if you don't want events with no dest,. Splunk Search Query Group By Field.
From docs.splunk.com
Basic searches and search results Splunk Documentation Splunk Search Query Group By Field And if you don't want events with no dest, you should add dest=* to your search query. Search criteria | extract fields if necessary | stats or timechart For example, we receive events from three different hosts: So, here's one way you can mask the reallocation with a display location by checking to see if the reallocation is the same.. Splunk Search Query Group By Field.
From www.primesoft.net
Retrospective Dashboard Queries in Splunk PrimeSoft Solutions Inc. Splunk Search Query Group By Field | transaction user | table user, src, dest, logontype |. And if you don't want events with no dest, you should add dest=* to your search query. Once you have your results, click the export button found above the results table on the splunk interface. For example, we receive events from three different hosts: Perform your search and apply your. Splunk Search Query Group By Field.
From docs.splunk.com
Basic searches and search results Splunk Documentation Splunk Search Query Group By Field And if you don't want events with no dest, you should add dest=* to your search query. You can assign one or more tags to any field/value combination,. | transaction user | table user, src, dest, logontype |. Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. Once. Splunk Search Query Group By Field.
From daillyresource.blogspot.com
How to use Splunk SPL commands to write better queries Part I Splunk Search Query Group By Field And if you don't want events with no dest, you should add dest=* to your search query. So, here's one way you can mask the reallocation with a display location by checking to see if the reallocation is the same. Perform your search and apply your group by in splunk. | transaction user | table user, src, dest, logontype |.. Splunk Search Query Group By Field.
From community.splunk.com
Using Eval field in regular expression Splunk Community Splunk Search Query Group By Field For the stats command, fields that you specify in the by clause group the results based on those fields. So, here's one way you can mask the reallocation with a display location by checking to see if the reallocation is the same. Search criteria | extract fields if necessary | stats or timechart Perform your search and apply your group. Splunk Search Query Group By Field.
From examples.javacodegeeks.com
Splunk Search Language Example Java Code Geeks Splunk Search Query Group By Field Perform your search and apply your group by in splunk. You can assign one or more tags to any field/value combination,. Once you have your results, click the export button found above the results table on the splunk interface. Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in.. Splunk Search Query Group By Field.
From docs.splunk.com
Use fields to search Splunk Documentation Splunk Search Query Group By Field For the stats command, fields that you specify in the by clause group the results based on those fields. A tag is a knowledge object that enables you to search for events that contain particular field values. Once you have your results, click the export button found above the results table on the splunk interface. Perform your search and apply. Splunk Search Query Group By Field.
From community.splunk.com
Solved Splunk stats count group by multiple fields Splunk Community Splunk Search Query Group By Field Perform your search and apply your group by in splunk. Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. For the stats command, fields that you specify in the by clause group the results based on those fields. A tag is a knowledge object that enables you to. Splunk Search Query Group By Field.
From www.stratosphereips.org
Getting Started With Splunk Basic Searching & Data Viz — Stratosphere IPS Splunk Search Query Group By Field So, here's one way you can mask the reallocation with a display location by checking to see if the reallocation is the same. Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. And if you don't want events with no dest, you should add dest=* to your search. Splunk Search Query Group By Field.
From www.stationx.net
Splunk Cheat Sheet Search and Query Commands Splunk Search Query Group By Field | transaction user | table user, src, dest, logontype |. For example, we receive events from three different hosts: For the stats command, fields that you specify in the by clause group the results based on those fields. You can assign one or more tags to any field/value combination,. Grouping search results the from command also supports aggregation using the. Splunk Search Query Group By Field.
From www.stationx.net
Splunk Cheat Sheet Search and Query Commands Splunk Search Query Group By Field Once you have your results, click the export button found above the results table on the splunk interface. For the stats command, fields that you specify in the by clause group the results based on those fields. Search criteria | extract fields if necessary | stats or timechart Perform your search and apply your group by in splunk. | transaction. Splunk Search Query Group By Field.
From geek-university.com
Example search Splunk Splunk Search Query Group By Field | transaction user | table user, src, dest, logontype |. Once you have your results, click the export button found above the results table on the splunk interface. Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. And if you don't want events with no dest, you should. Splunk Search Query Group By Field.
From docs.splunk.com
Basic searches and search results Splunk Documentation Splunk Search Query Group By Field | transaction user | table user, src, dest, logontype |. You can assign one or more tags to any field/value combination,. Search criteria | extract fields if necessary | stats or timechart For the stats command, fields that you specify in the by clause group the results based on those fields. Grouping search results the from command also supports aggregation. Splunk Search Query Group By Field.
From blog.scottlogic.com
Putting your machine data to use with Splunk Splunk Search Query Group By Field And if you don't want events with no dest, you should add dest=* to your search query. For the stats command, fields that you specify in the by clause group the results based on those fields. Perform your search and apply your group by in splunk. A tag is a knowledge object that enables you to search for events that. Splunk Search Query Group By Field.
From www.stratosphereips.org
Getting Started With Splunk Basic Searching & Data Viz — Stratosphere IPS Splunk Search Query Group By Field Grouping search results the from command also supports aggregation using the group by clause in conjunction with aggregate functions calls in. You can assign one or more tags to any field/value combination,. Search criteria | extract fields if necessary | stats or timechart A tag is a knowledge object that enables you to search for events that contain particular field. Splunk Search Query Group By Field.