Computer Image Verification And Authentication . To successfully subvert the verification and. A rich stream of research. Alter the data on the cartridge. checklist of computer image verification and authentication. researchers in academia and industry have devised four general approaches to image authentication: computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. image authentication is the technology of verifying image origin, integrity and authenticity. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer.
from dexatel.com
image authentication is the technology of verifying image origin, integrity and authenticity. checklist of computer image verification and authentication. To successfully subvert the verification and. A rich stream of research. Alter the data on the cartridge. researchers in academia and industry have devised four general approaches to image authentication: as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence.
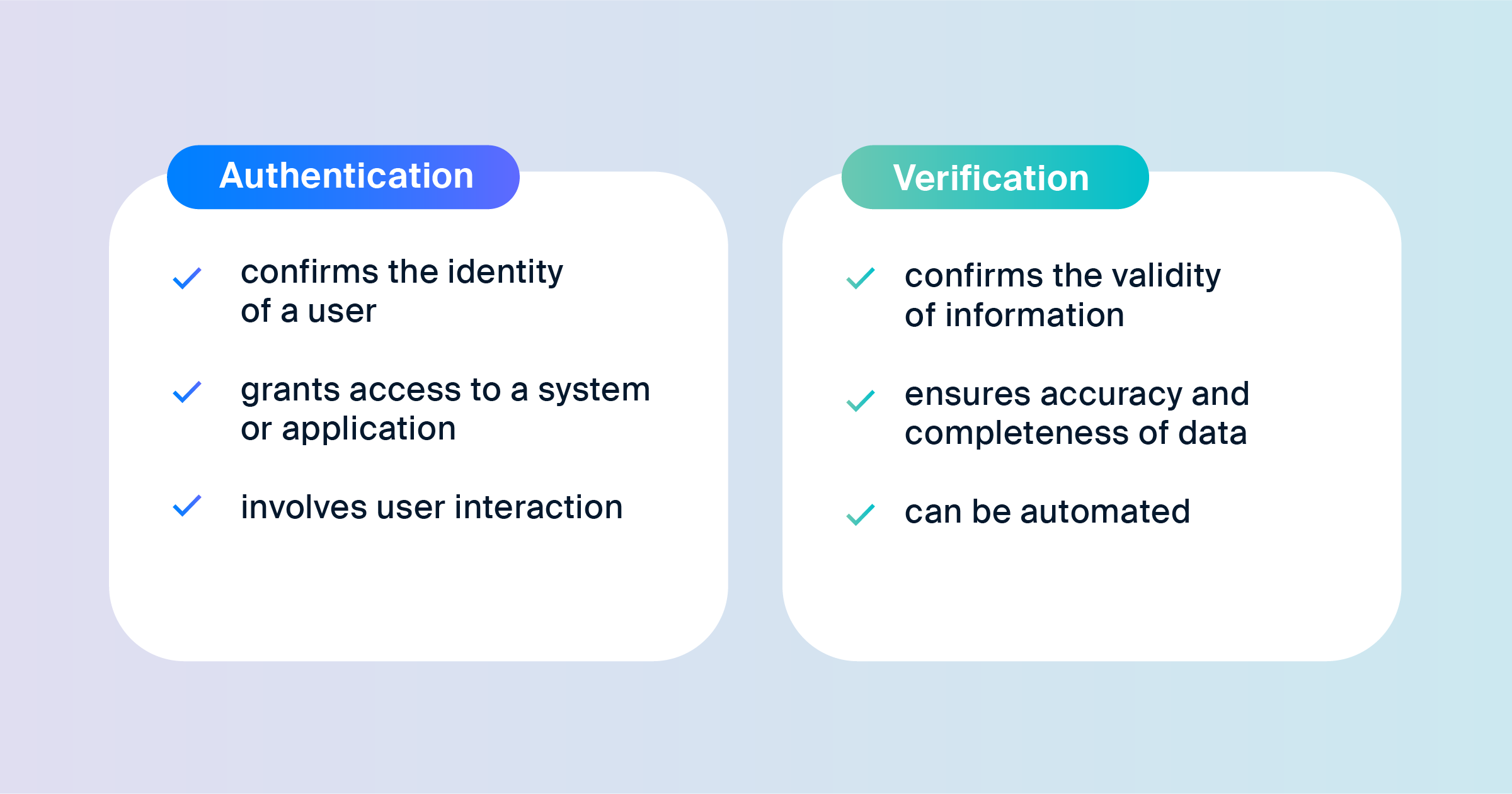
Authentication Vs. Verification Compare and Contrast
Computer Image Verification And Authentication computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. image authentication is the technology of verifying image origin, integrity and authenticity. A rich stream of research. checklist of computer image verification and authentication. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. Alter the data on the cartridge. researchers in academia and industry have devised four general approaches to image authentication: To successfully subvert the verification and. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence.
From www.alamy.com
2fa two factor authentication. Password verification and security. Code Computer Image Verification And Authentication image authentication is the technology of verifying image origin, integrity and authenticity. To successfully subvert the verification and. checklist of computer image verification and authentication. researchers in academia and industry have devised four general approaches to image authentication: computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. Alter the data on the. Computer Image Verification And Authentication.
From www.scribd.com
Image Verification and Authentication PDF Public Key Computer Image Verification And Authentication image authentication is the technology of verifying image origin, integrity and authenticity. researchers in academia and industry have devised four general approaches to image authentication: Alter the data on the cartridge. A rich stream of research. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. as law enforcement and other computer forensics. Computer Image Verification And Authentication.
From dexatel.com
Authentication Vs. Verification Compare and Contrast Computer Image Verification And Authentication as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. researchers in academia and industry have devised four general approaches to image authentication: checklist of computer image verification and authentication. image authentication is the technology of verifying image origin, integrity and authenticity. computer evidence processing steps, legal aspects of collecting. Computer Image Verification And Authentication.
From www.iproov.com
What's the Best Authentication Method? Analysis [2024] Computer Image Verification And Authentication checklist of computer image verification and authentication. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. A rich stream of research. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. image authentication is the technology of verifying image origin, integrity and authenticity. Alter the data on. Computer Image Verification And Authentication.
From www.idenfy.com
Identification Authentication Verification what are the differences Computer Image Verification And Authentication Alter the data on the cartridge. A rich stream of research. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. To successfully subvert the verification and. image authentication is the technology of verifying image origin, integrity and authenticity.. Computer Image Verification And Authentication.
From www.alamy.com
Identity access means verification and authentication control. Using Computer Image Verification And Authentication computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. checklist of computer image verification and authentication. image authentication is the technology of verifying image origin, integrity and authenticity. To successfully subvert the verification and. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. Alter the data. Computer Image Verification And Authentication.
From www.dreamstime.com
Two Steps Authentication on Computer. Stock Vector Illustration of Computer Image Verification And Authentication image authentication is the technology of verifying image origin, integrity and authenticity. A rich stream of research. researchers in academia and industry have devised four general approaches to image authentication: Alter the data on the cartridge. To successfully subvert the verification and. checklist of computer image verification and authentication. as law enforcement and other computer forensics. Computer Image Verification And Authentication.
From www.alamy.com
2FA two factor verification, key and lock, secure password and two Computer Image Verification And Authentication Alter the data on the cartridge. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. image authentication is the technology of verifying image origin, integrity and authenticity. A rich stream of research. To successfully subvert the verification and. researchers in academia and industry have devised four general approaches to image authentication: as. Computer Image Verification And Authentication.
From www.vecteezy.com
Twostep verification flat illustration vector template, OTP Computer Image Verification And Authentication computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. image authentication is the technology of verifying image origin, integrity and authenticity. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. researchers in academia and industry have devised four general approaches to image authentication: checklist of. Computer Image Verification And Authentication.
From dexatel.com
Authentication Vs. Verification Compare and Contrast Computer Image Verification And Authentication image authentication is the technology of verifying image origin, integrity and authenticity. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. checklist of computer image verification and authentication. Alter the data on the cartridge. A rich stream of research. To successfully subvert the verification and. as law enforcement and other computer forensics. Computer Image Verification And Authentication.
From www.bbc.co.uk
Verification and authentication Security and authentication Eduqas Computer Image Verification And Authentication checklist of computer image verification and authentication. To successfully subvert the verification and. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. A rich stream of research. researchers in academia and industry have devised four general approaches to image authentication: as law enforcement and other computer forensics investigators become more familiar with. Computer Image Verification And Authentication.
From www.alamy.com
2FA, two factor verification icon of vector outline laptop computer Computer Image Verification And Authentication image authentication is the technology of verifying image origin, integrity and authenticity. researchers in academia and industry have devised four general approaches to image authentication: computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. Alter the data on the cartridge. checklist of computer image verification and authentication. as law enforcement and. Computer Image Verification And Authentication.
From www.alamy.com
2FA two factor verification and password authentication, vector Computer Image Verification And Authentication Alter the data on the cartridge. A rich stream of research. researchers in academia and industry have devised four general approaches to image authentication: image authentication is the technology of verifying image origin, integrity and authenticity. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. as law enforcement and other computer forensics. Computer Image Verification And Authentication.
From www.dreamstime.com
Two steps authentication. stock vector. Illustration of authorize Computer Image Verification And Authentication checklist of computer image verification and authentication. To successfully subvert the verification and. image authentication is the technology of verifying image origin, integrity and authenticity. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. A rich stream of research. as law enforcement and other computer forensics investigators become more familiar with handling. Computer Image Verification And Authentication.
From swoopnow.com
User Authentication Understanding the Basics & Top Tips Computer Image Verification And Authentication checklist of computer image verification and authentication. image authentication is the technology of verifying image origin, integrity and authenticity. To successfully subvert the verification and. Alter the data on the cartridge. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. researchers in academia and industry have devised four general approaches. Computer Image Verification And Authentication.
From www.alamy.com
2FA two factor verification icon with vector authentication password Computer Image Verification And Authentication Alter the data on the cartridge. researchers in academia and industry have devised four general approaches to image authentication: as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. image authentication is the technology of verifying image origin, integrity and authenticity. To successfully subvert the verification and. computer evidence processing steps,. Computer Image Verification And Authentication.
From www.vectorstock.com
Two steps authentication computer verification Vector Image Computer Image Verification And Authentication computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. image authentication is the technology of verifying image origin, integrity and authenticity. checklist of computer image verification and authentication. To successfully subvert the verification and. researchers in. Computer Image Verification And Authentication.
From www.freepik.com
Premium Vector Secure email otp authentication and verification method Computer Image Verification And Authentication A rich stream of research. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. researchers in academia and industry have devised four general approaches to image authentication: checklist of computer image verification and authentication. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. Alter the data. Computer Image Verification And Authentication.
From www.dreamstime.com
Enable Two Step Verification 2FA 2 Steps Authentication Secure Computer Image Verification And Authentication researchers in academia and industry have devised four general approaches to image authentication: checklist of computer image verification and authentication. A rich stream of research. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. To successfully subvert the verification and. as law enforcement and other computer forensics investigators become more familiar with. Computer Image Verification And Authentication.
From www.alamy.com
2FA Two factor authentication on laptop computer and mobile phone app Computer Image Verification And Authentication A rich stream of research. researchers in academia and industry have devised four general approaches to image authentication: To successfully subvert the verification and. Alter the data on the cartridge. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. image authentication is the technology of verifying image origin, integrity and authenticity. checklist. Computer Image Verification And Authentication.
From www.alamy.com
Two steps authentication concept. Computer monitor with login into Computer Image Verification And Authentication Alter the data on the cartridge. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. To successfully subvert the verification and. researchers in academia and industry have devised four general approaches to image authentication: A rich stream of research. checklist of computer image verification and authentication. image authentication is the technology of. Computer Image Verification And Authentication.
From dexatel.com
Authentication Vs. Verification Compare and Contrast Computer Image Verification And Authentication To successfully subvert the verification and. researchers in academia and industry have devised four general approaches to image authentication: as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. image authentication is the technology of verifying image origin, integrity and authenticity. checklist of computer image verification and authentication. computer evidence. Computer Image Verification And Authentication.
From youverify.co
Identification Vs Verification Vs Authentication Understanding the Computer Image Verification And Authentication computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. Alter the data on the cartridge. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. researchers in academia and industry have devised four general approaches to image authentication: A rich stream of research. To successfully subvert the verification. Computer Image Verification And Authentication.
From dexatel.com
Authentication Vs. Verification Compare and Contrast Computer Image Verification And Authentication A rich stream of research. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. researchers in academia and industry have devised four general approaches to image authentication: computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. checklist of computer image verification and authentication. image authentication. Computer Image Verification And Authentication.
From www.youtube.com
AQA GCSE Computer Science Validation, Verification & Authentication Computer Image Verification And Authentication computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. researchers in academia and industry have devised four general approaches to image authentication: To successfully subvert the verification and. image authentication is the technology of verifying image origin,. Computer Image Verification And Authentication.
From techwarn.com
Why and how to use twofactor authentication? Computer Image Verification And Authentication A rich stream of research. checklist of computer image verification and authentication. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. Alter the data on the cartridge. researchers in academia and industry have devised four general approaches to image authentication: as law enforcement and other computer forensics investigators become more familiar with. Computer Image Verification And Authentication.
From www.alamy.com
2FA password authentication icon, 2 factor verification login access Computer Image Verification And Authentication as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. Alter the data on the cartridge. researchers in academia and industry have devised four general approaches to image authentication: A rich stream of research. image authentication is the technology of verifying image origin, integrity and authenticity. computer evidence processing steps, legal. Computer Image Verification And Authentication.
From www.alamy.com
Account verification isometric landing page, smartphone, computer and Computer Image Verification And Authentication checklist of computer image verification and authentication. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. image authentication is the technology of verifying image origin, integrity and authenticity. To successfully subvert the verification and. A rich stream of research. computer evidence processing steps, legal aspects of collecting and preserving computer. Computer Image Verification And Authentication.
From www.alamy.com
2FA authentication and two factor verification vector icon of secure Computer Image Verification And Authentication computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. Alter the data on the cartridge. A rich stream of research. image authentication is the technology of verifying image origin, integrity and authenticity. researchers in academia and industry have devised four general approaches to image authentication: as law enforcement and other computer forensics. Computer Image Verification And Authentication.
From avopix.com
Two steps authentication on computer. Login and Royalty Free Stock Computer Image Verification And Authentication computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. Alter the data on the cartridge. researchers in academia and industry have devised four general approaches to image authentication: To successfully subvert the verification and. A rich stream of. Computer Image Verification And Authentication.
From www.idenfy.com
What is Biometric Authentication? iDenfy Computer Image Verification And Authentication as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. Alter the data on the cartridge. checklist of computer image verification and authentication. A rich stream of research. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. To successfully subvert the verification and. researchers in academia and. Computer Image Verification And Authentication.
From www.alamy.com
2 step authentication hires stock photography and images Alamy Computer Image Verification And Authentication Alter the data on the cartridge. A rich stream of research. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. image authentication is the technology of verifying image origin, integrity and authenticity. checklist of computer image verification and authentication. researchers in academia and industry have devised four general approaches to image authentication:. Computer Image Verification And Authentication.
From www.alamy.com
Two steps authentication hires stock photography and images Alamy Computer Image Verification And Authentication checklist of computer image verification and authentication. A rich stream of research. image authentication is the technology of verifying image origin, integrity and authenticity. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. Alter the data on the cartridge. as law enforcement and other computer forensics investigators become more familiar with handling. Computer Image Verification And Authentication.
From hackforlab.com
Computer Image Verification and Authentication Computer Image Verification And Authentication checklist of computer image verification and authentication. as law enforcement and other computer forensics investigators become more familiar with handling evidential computer. A rich stream of research. researchers in academia and industry have devised four general approaches to image authentication: Alter the data on the cartridge. image authentication is the technology of verifying image origin, integrity. Computer Image Verification And Authentication.
From www.dreamstime.com
Two Step of Authentication with Password. Two Factor of Verification Computer Image Verification And Authentication image authentication is the technology of verifying image origin, integrity and authenticity. computer evidence processing steps, legal aspects of collecting and preserving computer forensic evidence. Alter the data on the cartridge. To successfully subvert the verification and. researchers in academia and industry have devised four general approaches to image authentication: checklist of computer image verification and. Computer Image Verification And Authentication.