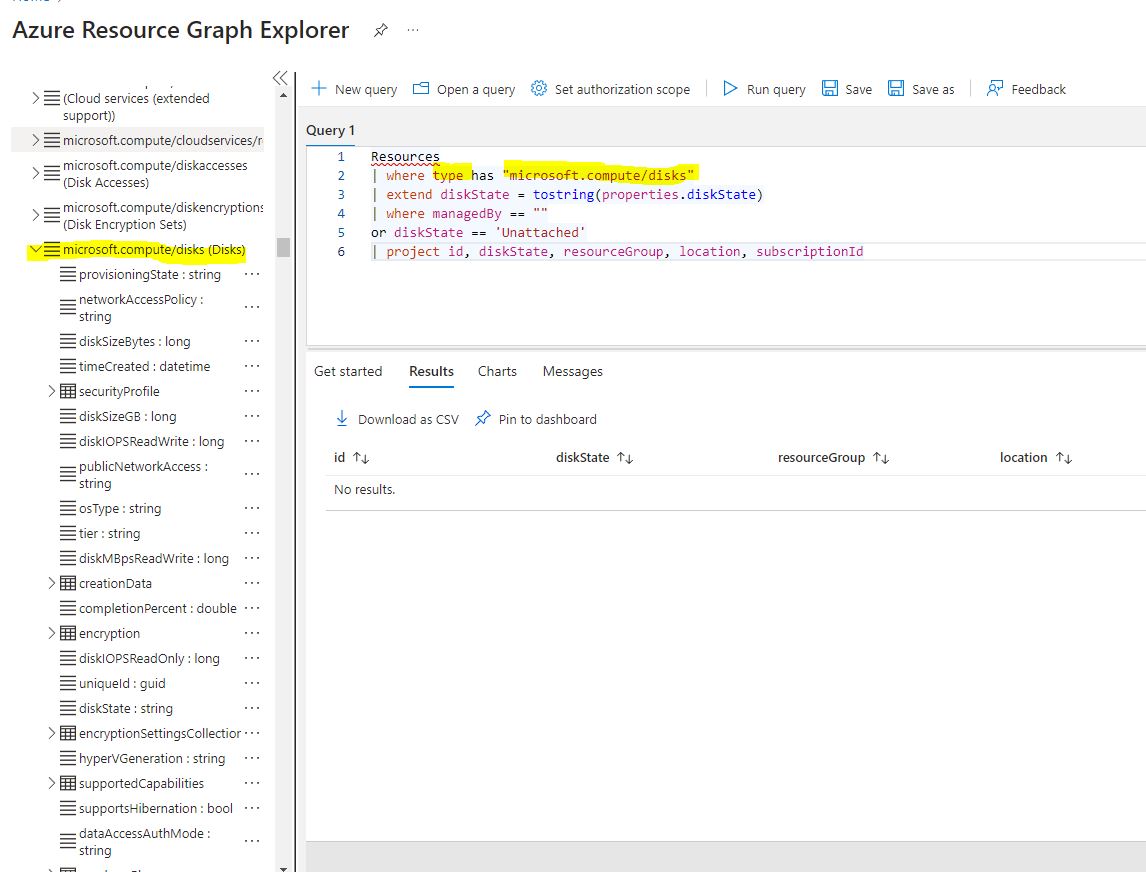
Security Alert Kql . Regardless of the source, these alerts are all stored together in the securityalert table in your log analytics workspace. To hopefully help point you in the right direction or resolve your issue, i'll share my findings below. As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. When it comes to creating a. Out of the box kql queries for: Defender for endpoint and azure sentinel hunting and detection queries in kql. In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. Ir on microsoft security incidents (kql edition), describes how different kql queries can help you detect and. This is helpful to join on devicenetworkevents or other tables that contain ip addresses to see if any ip from a.
from jefftechs.com
When it comes to creating a. This is helpful to join on devicenetworkevents or other tables that contain ip addresses to see if any ip from a. Regardless of the source, these alerts are all stored together in the securityalert table in your log analytics workspace. Defender for endpoint and azure sentinel hunting and detection queries in kql. Ir on microsoft security incidents (kql edition), describes how different kql queries can help you detect and. Out of the box kql queries for: In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. To hopefully help point you in the right direction or resolve your issue, i'll share my findings below. As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft.
Azure Alerts KQL, VM Availability and More Jeff Techs
Security Alert Kql Out of the box kql queries for: In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. Regardless of the source, these alerts are all stored together in the securityalert table in your log analytics workspace. This is helpful to join on devicenetworkevents or other tables that contain ip addresses to see if any ip from a. As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. Out of the box kql queries for: Defender for endpoint and azure sentinel hunting and detection queries in kql. To hopefully help point you in the right direction or resolve your issue, i'll share my findings below. When it comes to creating a. Ir on microsoft security incidents (kql edition), describes how different kql queries can help you detect and.
From in.security
KQL & LOLBAS Detection Ideas In.security Security Alert Kql Defender for endpoint and azure sentinel hunting and detection queries in kql. As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. Regardless of the source, these alerts are all stored together in the securityalert table in your log analytics workspace. Ir on microsoft security incidents. Security Alert Kql.
From community.imperva.com
Workflow for Working with Alerts WAF Gateway Fundamentals Part 9 Security Alert Kql When it comes to creating a. As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. This is helpful to join on devicenetworkevents or other tables that contain ip addresses to see if any ip from a. Regardless of the source, these alerts are all stored. Security Alert Kql.
From www.sklartechnology.com
Security Intelligence • Sklar Technology Partners Security Alert Kql Out of the box kql queries for: In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. Ir on microsoft security incidents (kql edition), describes how different kql queries can help you detect and. Defender for endpoint and azure sentinel hunting and detection queries in kql.. Security Alert Kql.
From learn.microsoft.com
Monitor Security Score using KQL/ Kusto using Log Analytics Workspace Microsoft Q&A Security Alert Kql In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. Defender for endpoint and azure sentinel hunting and detection queries in kql. To hopefully help point you in the right direction or resolve your issue, i'll share my findings below. Out of the box kql queries. Security Alert Kql.
From jefftechs.com
Azure Alerts KQL, VM Availability and More Jeff Techs Security Alert Kql When it comes to creating a. In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. Regardless of the source, these alerts are all stored together in the securityalert table in your log analytics workspace. To hopefully help point you in the right direction or resolve. Security Alert Kql.
From jefftechs.com
Azure Alerts KQL, VM Availability and More Jeff Techs Security Alert Kql In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. When it comes to creating a. Out of the box kql queries for: Regardless of the source, these alerts are all stored together in the securityalert table in your log analytics workspace. As an example, the. Security Alert Kql.
From cybergeeks.cloud
KQL fundamentals Let statement Cyber Geeks Cyber Security & Cloud Computing Security Alert Kql This is helpful to join on devicenetworkevents or other tables that contain ip addresses to see if any ip from a. Defender for endpoint and azure sentinel hunting and detection queries in kql. As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. Ir on microsoft. Security Alert Kql.
From emsroute.com
Microsoft Intune Audit Logs Hunting With KQL EMS Route Security Alert Kql This is helpful to join on devicenetworkevents or other tables that contain ip addresses to see if any ip from a. When it comes to creating a. Ir on microsoft security incidents (kql edition), describes how different kql queries can help you detect and. In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql). Security Alert Kql.
From www.modernsecurity.nl
Must Learn KQL Modern Security Security Alert Kql As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. When it comes to creating a. Defender for endpoint and azure sentinel hunting and detection queries in kql. To hopefully help point you in the right direction or resolve your issue, i'll share my findings below.. Security Alert Kql.
From jefftechs.com
Azure Alerts KQL, VM Availability and More Jeff Techs Security Alert Kql Ir on microsoft security incidents (kql edition), describes how different kql queries can help you detect and. This is helpful to join on devicenetworkevents or other tables that contain ip addresses to see if any ip from a. In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident. Security Alert Kql.
From jefftechs.com
Azure Alerts KQL, VM Availability and More Jeff Techs Security Alert Kql In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. Ir on microsoft security incidents (kql edition), describes how different kql queries can help you detect and. To hopefully help point you in the right direction or resolve your issue, i'll share my findings below. As. Security Alert Kql.
From jefftechs.com
Azure Alerts KQL, VM Availability and More Jeff Techs Security Alert Kql When it comes to creating a. In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. Out of the box kql queries for: Ir on microsoft security incidents (kql edition), describes how different kql queries can help you detect and. To hopefully help point you in. Security Alert Kql.
From www.elastic.co
Elastic Security UI Elastic Security Solution [master] Elastic Security Alert Kql Out of the box kql queries for: In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. Defender for endpoint and azure sentinel hunting and detection queries in kql. To hopefully help point you in the right direction or resolve your issue, i'll share my findings. Security Alert Kql.
From github.com
SentinelQueries/Security Alert/SecurityAlertTop20RandomStats.kql at main · reprise99/Sentinel Security Alert Kql When it comes to creating a. As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. Out of the box kql queries for: In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response. Security Alert Kql.
From cybergeeks.cloud
KQL Overview Kusto Query Language Cyber Geeks Cyber Security & Cloud Computing Security Alert Kql As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. Ir on microsoft security incidents (kql edition), describes how different kql queries can help you detect and. When it comes to creating a. Out of the box kql queries for: In this blog, we’ll show you. Security Alert Kql.
From www.dreamstime.com
Security Alert Computer Key Stock Image Image 24003941 Security Alert Kql This is helpful to join on devicenetworkevents or other tables that contain ip addresses to see if any ip from a. In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. As an example, the “high risk user security alert correlations” rules triggers alerts through joining. Security Alert Kql.
From jefftechs.com
Azure Alerts KQL, VM Availability and More Jeff Techs Security Alert Kql As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. Regardless of the source, these alerts are all stored together in the. Security Alert Kql.
From github.com
GitHub LearningKijo/KQL Threat Hunting query in Microsoft 365 Defender, XDR. Provide outof Security Alert Kql Out of the box kql queries for: As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. This is helpful to join on devicenetworkevents or other tables that contain ip addresses to see if any ip from a. Regardless of the source, these alerts are all. Security Alert Kql.
From www.youtube.com
Critical Security Alert Gmail Critical Security Alert in Google Account Critical Security Security Alert Kql In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. Out of the box kql queries for: As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. To hopefully help point you. Security Alert Kql.
From www.mbsecure.nl
KQL Cheat Sheet — MB Secure Security Alert Kql This is helpful to join on devicenetworkevents or other tables that contain ip addresses to see if any ip from a. In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. Defender for endpoint and azure sentinel hunting and detection queries in kql. To hopefully help. Security Alert Kql.
From jefftechs.com
Azure Alerts KQL, VM Availability and More Jeff Techs Security Alert Kql As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. Out of the box kql queries for: Ir on microsoft security incidents. Security Alert Kql.
From www.vecteezy.com
Alert sign. Attention warning attacker alert sign. Technology cyber security protection concept Security Alert Kql Regardless of the source, these alerts are all stored together in the securityalert table in your log analytics workspace. Defender for endpoint and azure sentinel hunting and detection queries in kql. As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. Out of the box kql. Security Alert Kql.
From www.youtube.com
Azure Sentinel webinar KQL part 1 of 3 Learn the KQL you need for Azure Sentinel YouTube Security Alert Kql As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. When it comes to creating a. Regardless of the source, these alerts are all stored together in the securityalert table in your log analytics workspace. Ir on microsoft security incidents (kql edition), describes how different kql. Security Alert Kql.
From www.researchgate.net
Overview of the Security Alerts Criticality Assessor Download Scientific Diagram Security Alert Kql This is helpful to join on devicenetworkevents or other tables that contain ip addresses to see if any ip from a. As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. Ir on microsoft security incidents (kql edition), describes how different kql queries can help you. Security Alert Kql.
From jefftechs.com
Azure Alerts KQL, VM Availability and More Jeff Techs Security Alert Kql To hopefully help point you in the right direction or resolve your issue, i'll share my findings below. When it comes to creating a. Out of the box kql queries for: Regardless of the source, these alerts are all stored together in the securityalert table in your log analytics workspace. This is helpful to join on devicenetworkevents or other tables. Security Alert Kql.
From jefftechs.com
Azure Alerts KQL, VM Availability and More Jeff Techs Security Alert Kql Defender for endpoint and azure sentinel hunting and detection queries in kql. To hopefully help point you in the right direction or resolve your issue, i'll share my findings below. Regardless of the source, these alerts are all stored together in the securityalert table in your log analytics workspace. When it comes to creating a. As an example, the “high. Security Alert Kql.
From www.sqlservercentral.com
KQL Series Security Monitoring with Azure Data Explorer SQLServerCentral Security Alert Kql To hopefully help point you in the right direction or resolve your issue, i'll share my findings below. In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. Ir on microsoft security incidents (kql edition), describes how different kql queries can help you detect and. When. Security Alert Kql.
From www.youtube.com
Automating Security Alerts with Power Automate & Cloud App Security YouTube Security Alert Kql This is helpful to join on devicenetworkevents or other tables that contain ip addresses to see if any ip from a. As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. Defender for endpoint and azure sentinel hunting and detection queries in kql. Ir on microsoft. Security Alert Kql.
From stefanpems.github.io
Security Monitoring Azure Key Vault Managed HSM with Microsoft Sentinel Stefanpe’s Blog Security Alert Kql As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. Regardless of the source, these alerts are all stored together in the securityalert table in your log analytics workspace. Ir on microsoft security incidents (kql edition), describes how different kql queries can help you detect and.. Security Alert Kql.
From jefftechs.com
Azure Alerts KQL, VM Availability and More Jeff Techs Security Alert Kql Defender for endpoint and azure sentinel hunting and detection queries in kql. Out of the box kql queries for: When it comes to creating a. This is helpful to join on devicenetworkevents or other tables that contain ip addresses to see if any ip from a. Regardless of the source, these alerts are all stored together in the securityalert table. Security Alert Kql.
From learn.microsoft.com
How do I run a KQL query for security alerts/incidents in Microsoft Sentinel for a user or list Security Alert Kql Ir on microsoft security incidents (kql edition), describes how different kql queries can help you detect and. In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. When it comes to creating a. To hopefully help point you in the right direction or resolve your issue,. Security Alert Kql.
From jefftechs.com
Azure Alerts KQL, VM Availability and More Jeff Techs Security Alert Kql As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft products with securityincident in microsoft. Out of the box kql queries for: To hopefully help point you in the right direction or resolve your issue, i'll share my findings below. Ir on microsoft security incidents (kql edition), describes how different kql. Security Alert Kql.
From cybergeeks.cloud
KQL Overview Kusto Query Language Cyber Geeks Cyber Security & Cloud Computing Security Alert Kql To hopefully help point you in the right direction or resolve your issue, i'll share my findings below. Ir on microsoft security incidents (kql edition), describes how different kql queries can help you detect and. Out of the box kql queries for: Defender for endpoint and azure sentinel hunting and detection queries in kql. Regardless of the source, these alerts. Security Alert Kql.
From jefftechs.com
Azure Alerts KQL, VM Availability and More Jeff Techs Security Alert Kql In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. Defender for endpoint and azure sentinel hunting and detection queries in kql. Regardless of the source, these alerts are all stored together in the securityalert table in your log analytics workspace. Ir on microsoft security incidents. Security Alert Kql.
From support.pipedrive.com
Security alerts Knowledge Base Pipedrive Security Alert Kql Ir on microsoft security incidents (kql edition), describes how different kql queries can help you detect and. In this blog, we’ll show you how microsoft incident response uses the kusto query language (kql) to quickly analyze data during incident response investigations. As an example, the “high risk user security alert correlations” rules triggers alerts through joining the securityalert from microsoft. Security Alert Kql.