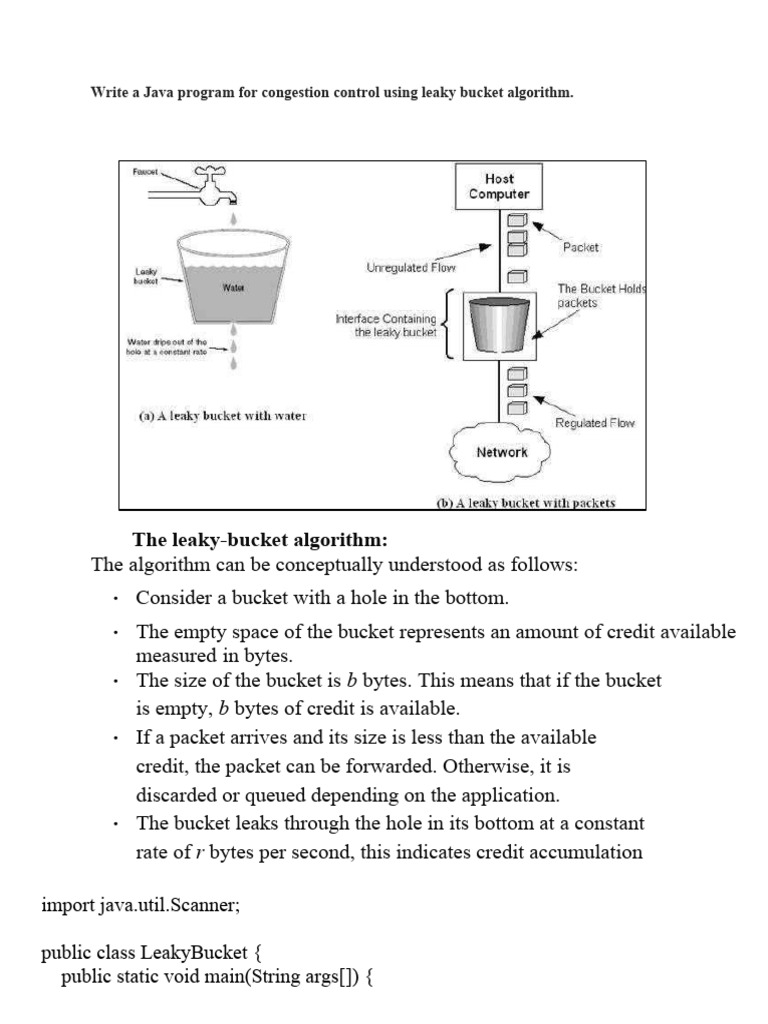
Leaky Bucket Algorithm Pdf . the leaky bucket algorithm converts bursty traffic into uniform traffic by allowing packets into a bucket that leaks out at a constant rate, discarding any packets. The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. a simple leaky bucket algorithm can be implemented using fifo queue. One can do very clever things. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. A fifo queue holds the packets. It regulates the rate at. the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control network traffic rates.
from www.scribd.com
The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. A fifo queue holds the packets. the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control network traffic rates. the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. One can do very clever things. the leaky bucket algorithm converts bursty traffic into uniform traffic by allowing packets into a bucket that leaks out at a constant rate, discarding any packets. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. a simple leaky bucket algorithm can be implemented using fifo queue. It regulates the rate at.
Write A Java Program For Congestion Control Using Leaky Bucket
Leaky Bucket Algorithm Pdf a simple leaky bucket algorithm can be implemented using fifo queue. It regulates the rate at. the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control network traffic rates. A fifo queue holds the packets. The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the leaky bucket algorithm converts bursty traffic into uniform traffic by allowing packets into a bucket that leaks out at a constant rate, discarding any packets. the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. a simple leaky bucket algorithm can be implemented using fifo queue. One can do very clever things.
From gamma.app
Leaky bucket algorithm Leaky Bucket Algorithm Pdf The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. A fifo queue holds the packets. It regulates the rate at. the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. a simple leaky bucket algorithm can be implemented using fifo queue. . Leaky Bucket Algorithm Pdf.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Algorithm Pdf A fifo queue holds the packets. the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control network traffic rates. One can do very clever things. in class, we introduced the leaky bucket. Leaky Bucket Algorithm Pdf.
From www.geeksforgeeks.org
Rate Limiting Algorithms System Design Leaky Bucket Algorithm Pdf the leaky bucket algorithm converts bursty traffic into uniform traffic by allowing packets into a bucket that leaks out at a constant rate, discarding any packets. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the leaky bucket algorithm imagine a bucket with a small hole in the. Leaky Bucket Algorithm Pdf.
From www.scribd.com
Write A Java Program For Congestion Control Using Leaky Bucket Leaky Bucket Algorithm Pdf the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control network traffic rates. A fifo queue holds the packets. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the leaky bucket algorithm converts bursty traffic into uniform traffic by allowing packets into. Leaky Bucket Algorithm Pdf.
From www.scribd.com
Leaky Bucket Algorithm PDF Engineering Leaky Bucket Algorithm Pdf in class, we introduced the leaky bucket as a way to police the transmission rate of a session. a simple leaky bucket algorithm can be implemented using fifo queue. It regulates the rate at. One can do very clever things. the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control network. Leaky Bucket Algorithm Pdf.
From www.researchgate.net
Leaky bucket approach. Download Scientific Diagram Leaky Bucket Algorithm Pdf The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. a simple leaky bucket algorithm can be implemented using fifo queue. the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. It regulates the rate at. the document discusses the leaky bucket. Leaky Bucket Algorithm Pdf.
From www.scribd.com
Congestion Control Using Leaky Bucket Algorithm PDF Network Leaky Bucket Algorithm Pdf in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control network traffic rates. the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. the. Leaky Bucket Algorithm Pdf.
From www.researchgate.net
(PDF) Intelligent leaky bucket algorithms for sustainablecellrate Leaky Bucket Algorithm Pdf One can do very clever things. The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. a simple leaky bucket algorithm can be implemented using fifo queue. the document discusses the. Leaky Bucket Algorithm Pdf.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm Pdf A fifo queue holds the packets. the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. It regulates the rate at. The above figure shows the leaky bucket algorithm that can. Leaky Bucket Algorithm Pdf.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm Pdf the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control network traffic rates. A fifo queue holds the packets. It regulates the rate at. The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. the leaky bucket algorithm imagine a bucket with a small hole. Leaky Bucket Algorithm Pdf.
From www.slideshare.net
Leaky bucket algorithm PDF Leaky Bucket Algorithm Pdf the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. One can do very clever things. A fifo queue holds the packets. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the leaky bucket algorithm is a traffic shaping algorithm. Leaky Bucket Algorithm Pdf.
From www.researchgate.net
(PDF) Performance Characteristics of a PacketBased LeakyBucket Leaky Bucket Algorithm Pdf The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. A fifo queue holds. Leaky Bucket Algorithm Pdf.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm Pdf A fifo queue holds the packets. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. It regulates the rate at. One can do very clever things. The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. the leaky bucket algorithm imagine a. Leaky Bucket Algorithm Pdf.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Algorithm Pdf the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. A fifo queue holds the packets. the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control network traffic rates. the leaky bucket algorithm is a traffic shaping algorithm used to control the flow. Leaky Bucket Algorithm Pdf.
From www.semanticscholar.org
[PDF] Leaky Bucket Algorithm for Congestion Control Semantic Scholar Leaky Bucket Algorithm Pdf a simple leaky bucket algorithm can be implemented using fifo queue. the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the document discusses the leaky bucket algorithm, which is. Leaky Bucket Algorithm Pdf.
From www.scribd.com
Program No. 8 Leaky Bucket Algorithm For Congestion Control PDF Leaky Bucket Algorithm Pdf a simple leaky bucket algorithm can be implemented using fifo queue. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. A fifo queue holds the packets. One can do very clever things. the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control. Leaky Bucket Algorithm Pdf.
From www.pdffiller.com
Fillable Online LEAKY BUCKET ALGORITHM Fax Email Print pdfFiller Leaky Bucket Algorithm Pdf the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. a simple leaky bucket algorithm can be implemented using fifo queue. in class, we introduced the leaky bucket as. Leaky Bucket Algorithm Pdf.
From www.scribd.com
Leaky Bucket Algorithm PDF Input/Output Computer File Leaky Bucket Algorithm Pdf A fifo queue holds the packets. the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. the leaky bucket algorithm converts bursty traffic into uniform traffic by allowing packets into a bucket that leaks out at a constant rate, discarding any packets. It regulates the rate at. One can. Leaky Bucket Algorithm Pdf.
From www.scribd.com
Leaky Bucket Algorithm 171FA04014 171FA04042 171FA04276 PDF Leaky Bucket Algorithm Pdf in class, we introduced the leaky bucket as a way to police the transmission rate of a session. a simple leaky bucket algorithm can be implemented using fifo queue. the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. It regulates the rate at. One can do very clever. Leaky Bucket Algorithm Pdf.
From www.researchgate.net
(PDF) Implementation of a police criterion calculator based on the Leaky Bucket Algorithm Pdf the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control network traffic rates. the leaky bucket algorithm converts bursty traffic into uniform traffic by allowing packets into a bucket that leaks out at. Leaky Bucket Algorithm Pdf.
From www.scribd.com
Network Based Packet Transmission Congestion Control Using Enhanced Leaky Bucket Algorithm Pdf the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. a. Leaky Bucket Algorithm Pdf.
From www.slideshare.net
Mini Project final report on " LEAKY BUCKET ALGORITHM " PDF Leaky Bucket Algorithm Pdf the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. a simple leaky bucket algorithm can be implemented using fifo queue. the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control network traffic rates. A fifo queue holds the packets. It regulates the. Leaky Bucket Algorithm Pdf.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID1753059 Leaky Bucket Algorithm Pdf One can do very clever things. the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. A fifo queue holds the packets. It regulates the rate at. The above figure shows the. Leaky Bucket Algorithm Pdf.
From www.youtube.com
Leaky bucket and Token bucket with GATE PYQs. Clear Explanation YouTube Leaky Bucket Algorithm Pdf the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. It regulates the rate at. A fifo queue holds the packets. a simple leaky bucket algorithm can be implemented using fifo queue. . Leaky Bucket Algorithm Pdf.
From www.scribd.com
Leaky Bucket Algorithm PDF Leaky Bucket Algorithm Pdf A fifo queue holds the packets. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. One can do very clever things. a simple leaky bucket algorithm can be implemented using fifo queue. the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control. Leaky Bucket Algorithm Pdf.
From www.youtube.com
Mastering the Leaky Bucket Algorithm A StepbyStep Guide? algorithm Leaky Bucket Algorithm Pdf a simple leaky bucket algorithm can be implemented using fifo queue. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. A fifo queue holds the packets. It regulates the. Leaky Bucket Algorithm Pdf.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm Pdf One can do very clever things. the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. A fifo queue holds the packets. a simple leaky bucket algorithm can be implemented using fifo queue. in class, we introduced the leaky bucket as a way to police the transmission rate. Leaky Bucket Algorithm Pdf.
From www.researchgate.net
(PDF) Leaky bucketinspired power output smoothing with loadadaptive Leaky Bucket Algorithm Pdf the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. One can do very clever things. The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. A fifo queue holds the packets. the document discusses the leaky bucket algorithm, which is a traffic. Leaky Bucket Algorithm Pdf.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and Leaky Bucket Algorithm Pdf in class, we introduced the leaky bucket as a way to police the transmission rate of a session. The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. One can do very clever things. the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in. Leaky Bucket Algorithm Pdf.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID4138688 Leaky Bucket Algorithm Pdf One can do very clever things. the leaky bucket algorithm converts bursty traffic into uniform traffic by allowing packets into a bucket that leaks out at a constant rate, discarding any packets. The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. the leaky bucket algorithm imagine a bucket with a. Leaky Bucket Algorithm Pdf.
From www.scribd.com
CRC Leaky Bucket Algorithm PDF Network Congestion Network Packet Leaky Bucket Algorithm Pdf the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. the leaky bucket algorithm imagine a bucket with a small hole in the bottom, as illustrated in fig. The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. It regulates the rate. Leaky Bucket Algorithm Pdf.
From www.researchgate.net
Intelligent Leaky Bucket Algorithms for SustainableCellRate Usage Leaky Bucket Algorithm Pdf One can do very clever things. the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control network traffic rates. the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. in class, we introduced the leaky bucket as a way to police the. Leaky Bucket Algorithm Pdf.
From www.semanticscholar.org
[PDF] Leaky Bucket Algorithm for Congestion Control Semantic Scholar Leaky Bucket Algorithm Pdf the leaky bucket algorithm converts bursty traffic into uniform traffic by allowing packets into a bucket that leaks out at a constant rate, discarding any packets. the document discusses the leaky bucket algorithm, which is a traffic shaping mechanism used to control network traffic rates. in class, we introduced the leaky bucket as a way to police. Leaky Bucket Algorithm Pdf.
From www.scribd.com
An Overview of the Leaky Bucket Algorithm for Traffic Shaping and Rate Leaky Bucket Algorithm Pdf A fifo queue holds the packets. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. the leaky bucket algorithm is a traffic shaping algorithm used to control the flow of data in a network. It regulates the rate at. One can do very clever things. the leaky bucket. Leaky Bucket Algorithm Pdf.
From www.slideshare.net
Leaky bucket algorithm PDF Leaky Bucket Algorithm Pdf The above figure shows the leaky bucket algorithm that can be used to police the traffic flow. in class, we introduced the leaky bucket as a way to police the transmission rate of a session. a simple leaky bucket algorithm can be implemented using fifo queue. One can do very clever things. the leaky bucket algorithm imagine. Leaky Bucket Algorithm Pdf.