Computer Network Exploitation . It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes. the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data. computer network exploitation refers to the act of conducting reconnaissance or espionage in the. computer network exploitation (cne) involves breaching and extracting valuable information from computer systems or networks. computer network exploitation (cne) is a technique through which computer networks are used to infiltrate target. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. These are conducted to steal data from a system or simply to obtain intelligence about networks,. computer network exploitation (cne) is computer espionage, the stealing of information. computer network exploitation, or cne, refers to espionage and reconnaissance operations.
from www.semanticscholar.org
enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. computer network exploitation (cne) is computer espionage, the stealing of information. computer network exploitation (cne) involves breaching and extracting valuable information from computer systems or networks. computer network exploitation, or cne, refers to espionage and reconnaissance operations. computer network exploitation refers to the act of conducting reconnaissance or espionage in the. It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes. the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. computer network exploitation (cne) is a technique through which computer networks are used to infiltrate target. These are conducted to steal data from a system or simply to obtain intelligence about networks,.
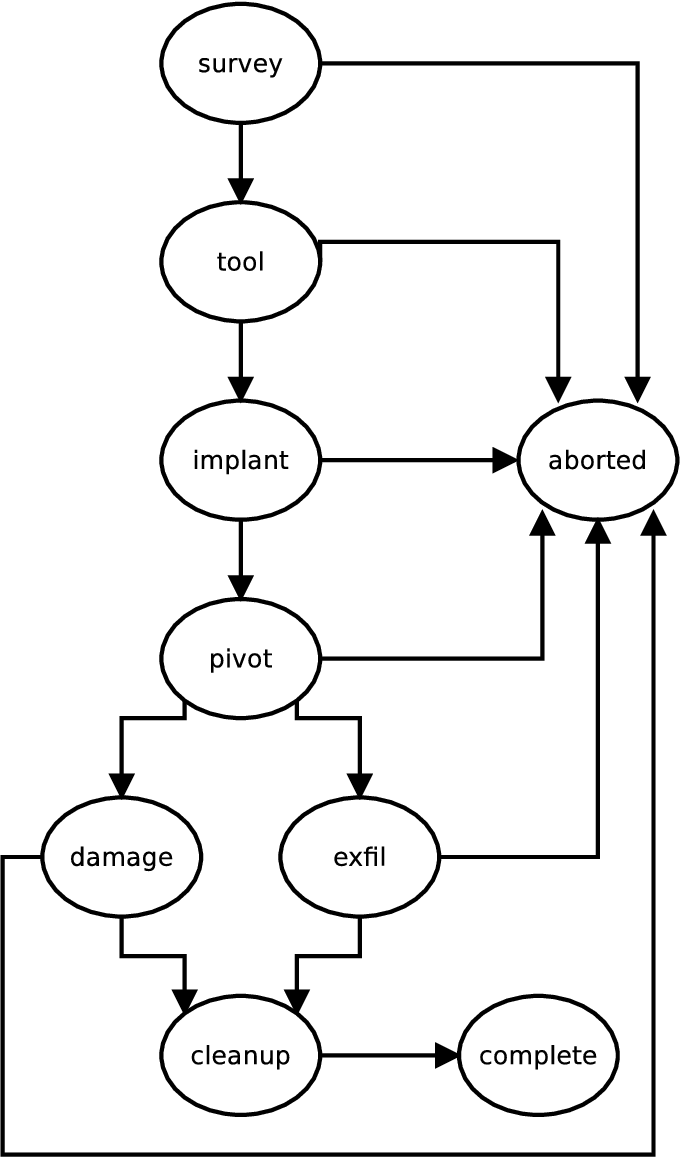
Figure 1 from A game theoretic model of computer network exploitation
Computer Network Exploitation enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data. computer network exploitation (cne) is a technique through which computer networks are used to infiltrate target. computer network exploitation refers to the act of conducting reconnaissance or espionage in the. the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. computer network exploitation (cne) is computer espionage, the stealing of information. enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data. It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. computer network exploitation, or cne, refers to espionage and reconnaissance operations. These are conducted to steal data from a system or simply to obtain intelligence about networks,. computer network exploitation (cne) involves breaching and extracting valuable information from computer systems or networks.
From kayleypennington.blogspot.com
Mandiant Attack Lifecycle The Cyber Exploitation Life Cycle Infosec Computer Network Exploitation computer network exploitation (cne) is computer espionage, the stealing of information. the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. computer network exploitation (cne) is a technique through which computer networks are used. Computer Network Exploitation.
From www.newshub.co.nz
New Zealand spy agency uses network exploitation' to take Computer Network Exploitation computer network exploitation (cne) is a technique through which computer networks are used to infiltrate target. enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. the term computer network exploitation encompasses a range of. Computer Network Exploitation.
From theintercept.com
Computer Network Exploitation presentation The Intercept Computer Network Exploitation computer network exploitation, or cne, refers to espionage and reconnaissance operations. computer network exploitation refers to the act of conducting reconnaissance or espionage in the. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes. computer. Computer Network Exploitation.
From www.youtube.com
Advantages And Disadvantages of Computer Network In Hindi YouTube Computer Network Exploitation the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. computer network exploitation, or cne, refers to espionage and reconnaissance operations. computer network exploitation (cne) is a technique through which computer networks are used. Computer Network Exploitation.
From www.slideserve.com
PPT A Need for Better Network Visualization PowerPoint Presentation Computer Network Exploitation enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data. These are conducted to steal data from a system or simply to obtain intelligence about networks,. computer network exploitation refers to the act of conducting reconnaissance or espionage in the. equipment interference, also known as computer network exploitation, allows mi5 to. Computer Network Exploitation.
From le-guide.ma
Technicien informatiqueréseau Le Guide Computer Network Exploitation equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. These are conducted to steal data from a system or simply to obtain intelligence about networks,. computer network exploitation (cne) involves breaching and extracting valuable information from computer systems or networks. computer network exploitation refers to the act of conducting reconnaissance or. Computer Network Exploitation.
From www.zdnet.com
Book review Network Attacks and Exploitation A Framework Computer Network Exploitation It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes. computer network exploitation, or cne, refers to espionage and reconnaissance operations. These are conducted to steal data from a system or simply to obtain intelligence about networks,. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. . Computer Network Exploitation.
From www.researchgate.net
(PDF) Automated Computer Network Exploitation with Bayesian Decision Computer Network Exploitation These are conducted to steal data from a system or simply to obtain intelligence about networks,. enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data. It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes. computer network exploitation refers to the act of conducting reconnaissance or. Computer Network Exploitation.
From www.scribd.com
GCHQ Computer Network Exploitation PDF Freedom Of Information Act Computer Network Exploitation It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes. computer network exploitation refers to the act of conducting reconnaissance or espionage in the. computer network exploitation, or cne, refers to espionage and reconnaissance operations. computer network exploitation (cne) is computer espionage, the stealing of information. the term computer network exploitation. Computer Network Exploitation.
From www.larksuite.com
Computer Network Exploitation Computer Network Exploitation computer network exploitation, or cne, refers to espionage and reconnaissance operations. It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at. Computer Network Exploitation.
From theintercept.com
Computer Network Exploitation Comes to NSA/CSS The Intercept Computer Network Exploitation equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes. enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data. the term computer network exploitation encompasses a range of activities conducted. Computer Network Exploitation.
From vacif.com
Lỗ hổng bảo mật là gì và cách phòng chống hacker lợi dụng lỗ hổng bảo Computer Network Exploitation computer network exploitation, or cne, refers to espionage and reconnaissance operations. computer network exploitation (cne) is a technique through which computer networks are used to infiltrate target. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. computer network exploitation refers to the act of conducting reconnaissance or espionage in the.. Computer Network Exploitation.
From www.choisir-ordinateur.com
Tout savoir sur le système d'exploitation Windows Computer Network Exploitation computer network exploitation (cne) is computer espionage, the stealing of information. computer network exploitation (cne) is a technique through which computer networks are used to infiltrate target. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. computer network exploitation (cne) involves breaching and extracting valuable information from computer systems or. Computer Network Exploitation.
From www.triplecyber.com
TripleCyber Computer Network Exploitation Services Computer Network Exploitation These are conducted to steal data from a system or simply to obtain intelligence about networks,. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. computer network exploitation (cne) is computer espionage, the stealing of information. enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather. Computer Network Exploitation.
From webapi.bu.edu
🎉 Cyber warfare research topics. Cyber Warfare Research Paper. 20221015 Computer Network Exploitation computer network exploitation refers to the act of conducting reconnaissance or espionage in the. It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes. computer network exploitation (cne) is computer espionage, the stealing of information. These are conducted to steal data from a system or simply to obtain intelligence about networks,. the. Computer Network Exploitation.
From dxobbxteq.blob.core.windows.net
Network Exploitation Basics at Karla Skelly blog Computer Network Exploitation These are conducted to steal data from a system or simply to obtain intelligence about networks,. enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data. computer network exploitation (cne) is computer espionage, the stealing of information. computer network exploitation refers to the act of conducting reconnaissance or espionage in the.. Computer Network Exploitation.
From www.linkedin.com
Computer Network Computer Network Exploitation These are conducted to steal data from a system or simply to obtain intelligence about networks,. the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. computer network exploitation (cne) involves breaching and extracting valuable information from computer systems or networks. computer network exploitation (cne) is a technique through which. Computer Network Exploitation.
From www.onepointsync.com
How Cyber Security Can Improve Productivity and Profitability Computer Network Exploitation It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes. These are conducted to steal data from a system or simply to obtain intelligence about networks,. the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. computer network exploitation refers to the act of conducting reconnaissance. Computer Network Exploitation.
From slidetodoc.com
A Game Theoretic Model of Computer Network Exploitation Computer Network Exploitation computer network exploitation (cne) is computer espionage, the stealing of information. enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. the term computer network exploitation encompasses a range of activities conducted by threat actors,. Computer Network Exploitation.
From securityonline.info
Network Exploitation, Reconnaissance & Vulnerability Engine Computer Network Exploitation equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data. the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. computer network exploitation, or cne, refers to espionage. Computer Network Exploitation.
From dxobbxteq.blob.core.windows.net
Network Exploitation Basics at Karla Skelly blog Computer Network Exploitation computer network exploitation (cne) is a technique through which computer networks are used to infiltrate target. These are conducted to steal data from a system or simply to obtain intelligence about networks,. computer network exploitation (cne) involves breaching and extracting valuable information from computer systems or networks. equipment interference, also known as computer network exploitation, allows mi5. Computer Network Exploitation.
From www.dreamstime.com
Computer Vulnerability Exploitation Gradient Linear Vector Icons Set Computer Network Exploitation computer network exploitation (cne) is computer espionage, the stealing of information. enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data. computer network exploitation (cne) involves breaching and extracting valuable information from computer systems or networks. computer network exploitation (cne) is a technique through which computer networks are used to. Computer Network Exploitation.
From www.studocu.com
Advanced web attack and exploitation Computer Networks Studocu Computer Network Exploitation computer network exploitation (cne) is a technique through which computer networks are used to infiltrate target. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. computer network exploitation (cne) involves breaching and extracting valuable information from computer systems or networks. These are conducted to steal data from a system or simply. Computer Network Exploitation.
From publicintelligence.net
People’s Republic of China Cyber Warfare and Computer Network Computer Network Exploitation the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. computer network exploitation, or cne, refers to espionage and reconnaissance operations. computer network exploitation refers to the act of conducting reconnaissance or espionage in the. computer network exploitation (cne) is computer espionage, the stealing of information. computer network. Computer Network Exploitation.
From theintercept.com
Computer Network Exploitation presentation The Intercept Computer Network Exploitation the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. computer network exploitation (cne) is a technique through which computer networks are used to infiltrate target. These are conducted to steal data from a system or simply to obtain intelligence about networks,. computer network exploitation, or cne, refers to espionage. Computer Network Exploitation.
From www.kernrh.fr
Technicien d’exploitation informatique Kern RH Computer Network Exploitation computer network exploitation refers to the act of conducting reconnaissance or espionage in the. the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. computer network exploitation (cne) is computer espionage, the stealing of information. It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes.. Computer Network Exploitation.
From www.semanticscholar.org
Figure 1 from A game theoretic model of computer network exploitation Computer Network Exploitation the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. computer network exploitation refers to the act of conducting reconnaissance or espionage in the. These are conducted to steal data from a system or simply to obtain intelligence about networks,. computer network exploitation (cne) is a technique through which computer. Computer Network Exploitation.
From dxobbxteq.blob.core.windows.net
Network Exploitation Basics at Karla Skelly blog Computer Network Exploitation It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes. These are conducted to steal data from a system or simply to obtain intelligence about networks,. computer network exploitation, or cne, refers to espionage and reconnaissance operations. enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data.. Computer Network Exploitation.
From dokumen.tips
(PDF) Controlling Computer Network Operations Procon …procon.bg Computer Network Exploitation computer network exploitation, or cne, refers to espionage and reconnaissance operations. the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. equipment interference, also known as computer network exploitation, allows mi5 to gather communications or other. These are conducted to steal data from a system or simply to obtain intelligence. Computer Network Exploitation.
From www.pdfprof.com
ES for Endpoint Systèmes D'Exploitation Computer Network Exploitation enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data. the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. computer network exploitation refers to the act of conducting reconnaissance or espionage in the. It includes monitoring, cyber espionage, and manipulation of data for. Computer Network Exploitation.
From www.hackercombat.com
4 Most Memorable In History Hacker Combat Computer Network Exploitation It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes. computer network exploitation (cne) is computer espionage, the stealing of information. the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. computer network exploitation (cne) involves breaching and extracting valuable information from computer systems or. Computer Network Exploitation.
From cyberwiedza.pl
Computer Network Exploitation CyberWiedza.pl Cyberbezpieczeństwo Computer Network Exploitation computer network exploitation (cne) involves breaching and extracting valuable information from computer systems or networks. computer network exploitation (cne) is a technique through which computer networks are used to infiltrate target. computer network exploitation (cne) is computer espionage, the stealing of information. computer network exploitation, or cne, refers to espionage and reconnaissance operations. It includes monitoring,. Computer Network Exploitation.
From production.public.theintercept.cloud
Computer Network Exploitation Classification Guide The Intercept Computer Network Exploitation computer network exploitation, or cne, refers to espionage and reconnaissance operations. enabling operations and intelligence collection capabilities conducted through the use of computer networks to gather data. the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. These are conducted to steal data from a system or simply to obtain. Computer Network Exploitation.
From www.nzherald.co.nz
Spy agency uses network exploitation’ to take digital Computer Network Exploitation computer network exploitation (cne) is a technique through which computer networks are used to infiltrate target. computer network exploitation refers to the act of conducting reconnaissance or espionage in the. computer network exploitation, or cne, refers to espionage and reconnaissance operations. These are conducted to steal data from a system or simply to obtain intelligence about networks,.. Computer Network Exploitation.
From www.devx.com
Computer Network Exploitation Glossary Computer Network Exploitation the term computer network exploitation encompasses a range of activities conducted by threat actors, aimed at leveraging. It includes monitoring, cyber espionage, and manipulation of data for intelligence gathering and other purposes. These are conducted to steal data from a system or simply to obtain intelligence about networks,. computer network exploitation refers to the act of conducting reconnaissance. Computer Network Exploitation.