Keycloak Authentication Oauth . An effective and isolated manner is. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to a centralized. In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication.
from www.azguards.com
Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. An effective and isolated manner is. Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to a centralized. In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application.
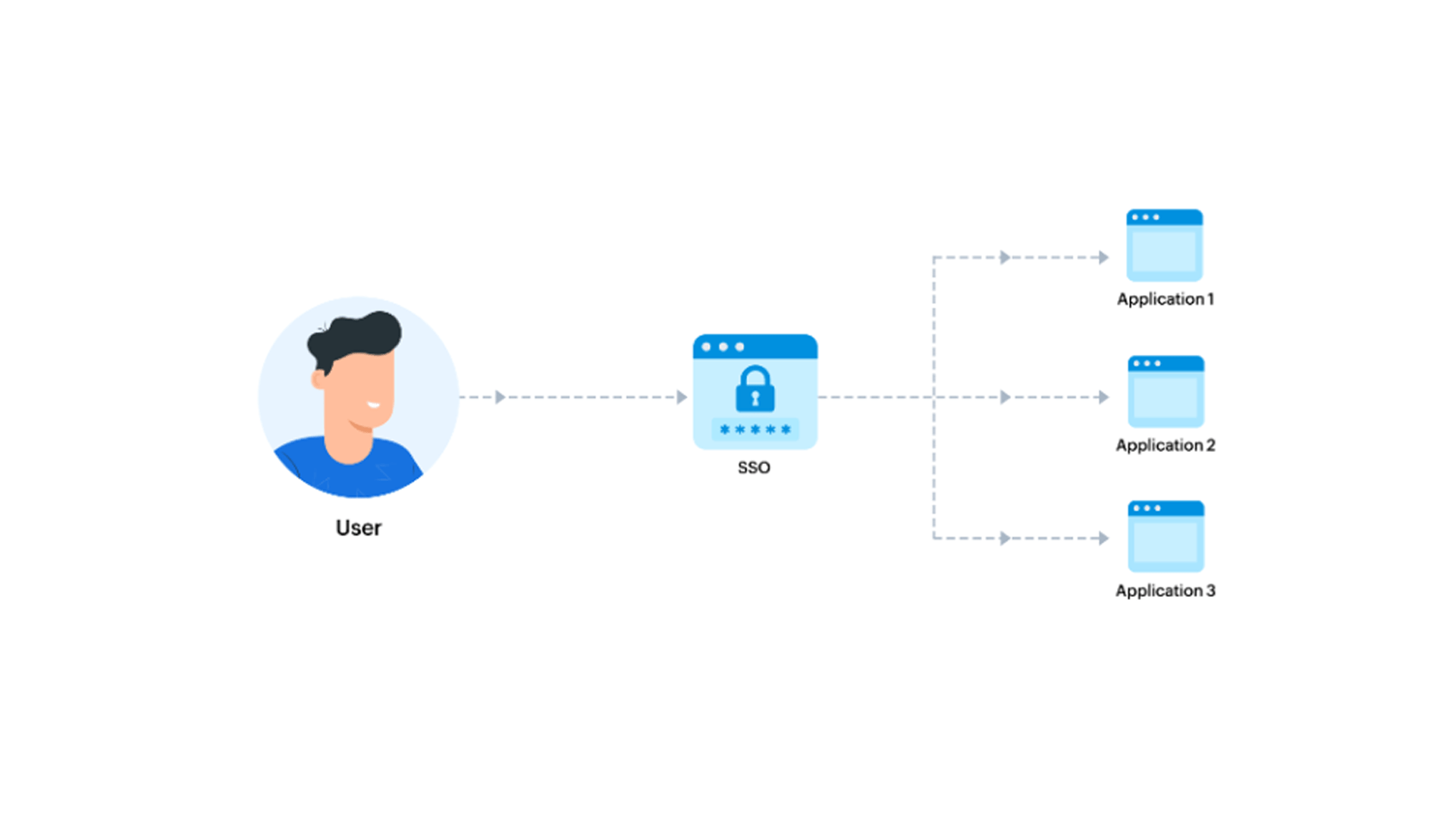
Single Sign on Setup Okta+ Keycloak using SMAIL and OIDC
Keycloak Authentication Oauth To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. An effective and isolated manner is. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication. Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to a centralized.
From github.com
springsecurityoauth2clientforkeycloak/README.md at main · shinyay Keycloak Authentication Oauth This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net. Keycloak Authentication Oauth.
From securityboulevard.com
Common REST API Authentication Methods Explained Security Boulevard Keycloak Authentication Oauth To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. An effective and isolated manner is. In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication. Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex,. Keycloak Authentication Oauth.
From younite.us
Configuring SSO and OAuth with Keycloak Keycloak Authentication Oauth Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui An effective and isolated manner is. Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to. Keycloak Authentication Oauth.
From apisix.apache.org
Accessing APISIXDashboard from Everywhere with Keycloak Authentication Keycloak Authentication Oauth Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication. An effective and isolated manner is. To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we. Keycloak Authentication Oauth.
From docs.wundergraph.com
Keycloak OpenID Connect Authentication Example WunderGraph Docs Keycloak Authentication Oauth An effective and isolated manner is. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to a centralized. Oauth 2.0 is the industry standard authorization protocol, but it's. Keycloak Authentication Oauth.
From klafxccbi.blob.core.windows.net
Oauth2 Authorization Server Configuration Example at Thomas Osborne blog Keycloak Authentication Oauth An effective and isolated manner is. To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. In this tutorial, we will configure keycloak 21.0.1 as an. Keycloak Authentication Oauth.
From plugins.miniorange.com
Keycloak SSO Integration with Drupal OAuth/OpenID Client Keycloak Authentication Oauth This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to a centralized. An effective and isolated manner is. Oauth 2.0 is the industry standard authorization protocol, but it's. Keycloak Authentication Oauth.
From wilddiary.com
OAuth2 Authentication in Keycloak for Public Clients Keycloak Authentication Oauth Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure. Keycloak Authentication Oauth.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Authentication Oauth An effective and isolated manner is. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to a centralized. Oauth 2.0 is the industry standard authorization protocol, but it's. Keycloak Authentication Oauth.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Authentication Oauth This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication. Learn how to test a rest service that uses keycloak for authentication and. Keycloak Authentication Oauth.
From developers.redhat.com
Authentication and authorization using the Keycloak REST API Red Hat Keycloak Authentication Oauth An effective and isolated manner is. Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core. Keycloak Authentication Oauth.
From www.redpill-linpro.com
Get started with OpenID Connect and Keycloak /techblog Keycloak Authentication Oauth Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication. Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to a centralized. To integrate. Keycloak Authentication Oauth.
From morioh.com
How To Add Authentication to your Apps using OAuth2 Proxy Keycloak Authentication Oauth Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication. An effective. Keycloak Authentication Oauth.
From medium.com
Keycloak and IDP Configuration. This document provides stepbystep Keycloak Authentication Oauth An effective and isolated manner is. To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. Oauth 2.0 is the industry standard authorization protocol, but it's. Keycloak Authentication Oauth.
From walkingtree.tech
Keycloak Identity Access Management Solutions WalkingTree Technologies Keycloak Authentication Oauth This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. An effective and isolated manner is. Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui To integrate authentication and authorization into our applications using keycloak with oauth2. Keycloak Authentication Oauth.
From stackoverflow.com
oauth 2.0 Keycloak OAUTH2, SSO and two different access tokens for Keycloak Authentication Oauth In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication. To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to a centralized.. Keycloak Authentication Oauth.
From www.analyticsvidhya.com
Spring Security Oauth2 with Keycloak PKCE Authorization Code Flow Keycloak Authentication Oauth Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to a centralized. Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui An effective and isolated manner is. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication. Keycloak Authentication Oauth.
From www.drupal.org
Configure Keycloak as OAuth Provider (version 20.x or higher) Drupal Keycloak Authentication Oauth Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to a centralized. Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui An effective and isolated manner is. To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure. Keycloak Authentication Oauth.
From laptrinhx.com
Securing Applications With Keycloak Using OAuth 2.0 Authorization Keycloak Authentication Oauth Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we. Keycloak Authentication Oauth.
From plugins.miniorange.com
Keycloak SSO Integration with Drupal OAuth/OpenID Client Keycloak Authentication Oauth An effective and isolated manner is. Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. This spring security tutorial will explore how to use keycloak and spring security oauth2 module. Keycloak Authentication Oauth.
From medium.com
Keycloak and Oauth2. Keycloak is an opensource identity and… by Keycloak Authentication Oauth In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication. Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to a. Keycloak Authentication Oauth.
From frameworks.readthedocs.io
Keycloak OAuth2 PKCE — Framework Repositories 1.0 documentation Keycloak Authentication Oauth In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex,. Keycloak Authentication Oauth.
From www.redhat.com
How to architect OAuth 2.0 authorization using Keycloak Enable Architect Keycloak Authentication Oauth To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to a centralized. Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui An effective and isolated manner. Keycloak Authentication Oauth.
From community.ibm.com
Extending Keycloak's authentication capabilities by integrating with Keycloak Authentication Oauth To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to a centralized. Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. Learn how. Keycloak Authentication Oauth.
From www.springcloud.io
Unified authentication authorization platform keycloak Introduction Keycloak Authentication Oauth An effective and isolated manner is. Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15. Keycloak Authentication Oauth.
From www.mdpi.com
Sensors Free FullText Applying Spring Security Framework with Keycloak Authentication Oauth In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication. To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and. Keycloak Authentication Oauth.
From janus-idp.io
Enabling Keycloak Authentication in Backstage Janus Keycloak Authentication Oauth Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. An effective and isolated manner is. In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider. Keycloak Authentication Oauth.
From stackoverflow.com
rest Keycloak Oauth2 Authentication Flow Stack Overflow Keycloak Authentication Oauth An effective and isolated manner is. Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. In this tutorial, we will configure keycloak 21.0.1 as. Keycloak Authentication Oauth.
From qiita.com
KeycloakのToken ExchangeをSAML2対応した話 OAuth Qiita Keycloak Authentication Oauth In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication. Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui This. Keycloak Authentication Oauth.
From devopsi.pl
Keycloak an introduction to easy user management Keycloak Authentication Oauth An effective and isolated manner is. Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. Keycloak can be easily configured as an oauth 2.0 server, enabling applications. Keycloak Authentication Oauth.
From www.keycloak.org
Authorization Services Guide Keycloak Authentication Oauth To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui An effective and isolated. Keycloak Authentication Oauth.
From uptrace.dev
Keycloak Auth Keycloak Authentication Oauth Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication. Keycloak can be easily configured as an oauth 2.0 server, enabling applications to securely delegate authentication to a. Keycloak Authentication Oauth.
From www.azguards.com
Single Sign on Setup Okta+ Keycloak using SMAIL and OIDC Keycloak Authentication Oauth In this tutorial, we will configure keycloak 21.0.1 as an oauth2 provider in angular 15 and.net core 6.0 to enable secure authentication. To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first configure keycloak. Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at. Keycloak Authentication Oauth.
From andrevianna-1662831931436.hashnode.dev
Understanding the Powerful Keycloak Tool Keycloak Authentication Oauth Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring. Keycloak Authentication Oauth.
From www.thomasvitale.com
Introducing Keycloak for Identity and Access Management Keycloak Authentication Oauth An effective and isolated manner is. Learn how to test a rest service that uses keycloak for authentication and authorization with swagger ui Oauth 2.0 is the industry standard authorization protocol, but it's also huge, complex, and even a bit scary at first. To integrate authentication and authorization into our applications using keycloak with oauth2 and openid, we must first. Keycloak Authentication Oauth.