Router Access List Rules . This document describes how ip access control lists (acls) can filter network traffic. There are some recommended best practices when creating and applying access control lists (acl). If an acl has multiple entries, each entry is read. Access control list explained with examples. Learn cisco acls configuration commands with their. It also contains brief descriptions of the. Helpful hints for creating ip access lists. This tutorial explains how to configure cisco access control lists. Ip access list process and rules. To create a standard access list, it uses the following syntax. There are two basic rules, regardless of the type of acl that you want to configure: The network administrator should apply a standard acl closest.
from www.techtarget.com
It also contains brief descriptions of the. Helpful hints for creating ip access lists. Ip access list process and rules. This tutorial explains how to configure cisco access control lists. The network administrator should apply a standard acl closest. This document describes how ip access control lists (acls) can filter network traffic. Access control list explained with examples. To create a standard access list, it uses the following syntax. There are some recommended best practices when creating and applying access control lists (acl). If an acl has multiple entries, each entry is read.
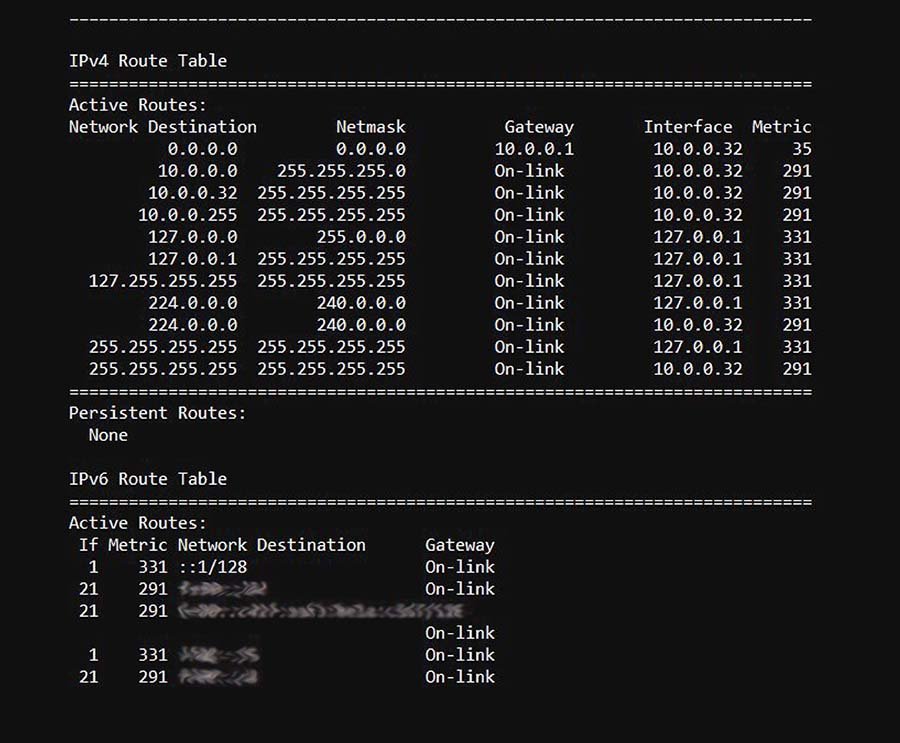
What is a Routing Table? A Definition from
Router Access List Rules This document describes how ip access control lists (acls) can filter network traffic. The network administrator should apply a standard acl closest. This tutorial explains how to configure cisco access control lists. Helpful hints for creating ip access lists. Ip access list process and rules. If an acl has multiple entries, each entry is read. There are two basic rules, regardless of the type of acl that you want to configure: Access control list explained with examples. This document describes how ip access control lists (acls) can filter network traffic. To create a standard access list, it uses the following syntax. There are some recommended best practices when creating and applying access control lists (acl). It also contains brief descriptions of the. Learn cisco acls configuration commands with their.
From www.ccnablog.com
ACLs (Access Control Lists) Part I CCNA Blog Router Access List Rules This tutorial explains how to configure cisco access control lists. There are some recommended best practices when creating and applying access control lists (acl). Learn cisco acls configuration commands with their. It also contains brief descriptions of the. To create a standard access list, it uses the following syntax. If an acl has multiple entries, each entry is read. Ip. Router Access List Rules.
From www.youtube.com
Standard Access List (ACL) for the Cisco CCNA Part 1 YouTube Router Access List Rules It also contains brief descriptions of the. The network administrator should apply a standard acl closest. This tutorial explains how to configure cisco access control lists. Ip access list process and rules. There are two basic rules, regardless of the type of acl that you want to configure: There are some recommended best practices when creating and applying access control. Router Access List Rules.
From www.youtube.com
How Access Lists work on Cisco routers YouTube Router Access List Rules This document describes how ip access control lists (acls) can filter network traffic. To create a standard access list, it uses the following syntax. Learn cisco acls configuration commands with their. Ip access list process and rules. Access control list explained with examples. This tutorial explains how to configure cisco access control lists. Helpful hints for creating ip access lists.. Router Access List Rules.
From www.ccexpert.us
Access Lists on Cisco Routers CCIE Security Cisco Certified Expert Router Access List Rules This document describes how ip access control lists (acls) can filter network traffic. There are some recommended best practices when creating and applying access control lists (acl). To create a standard access list, it uses the following syntax. There are two basic rules, regardless of the type of acl that you want to configure: This tutorial explains how to configure. Router Access List Rules.
From www.wikihow.com
How to Access a Router (with Pictures) wikiHow Router Access List Rules There are two basic rules, regardless of the type of acl that you want to configure: This tutorial explains how to configure cisco access control lists. Helpful hints for creating ip access lists. There are some recommended best practices when creating and applying access control lists (acl). This document describes how ip access control lists (acls) can filter network traffic.. Router Access List Rules.
From routerctrl.com
Router Operation Modes Explained (Router, Repeater, Access Point Router Access List Rules If an acl has multiple entries, each entry is read. Helpful hints for creating ip access lists. This tutorial explains how to configure cisco access control lists. Learn cisco acls configuration commands with their. This document describes how ip access control lists (acls) can filter network traffic. Access control list explained with examples. Ip access list process and rules. There. Router Access List Rules.
From www.slideserve.com
PPT CHAPTER 6 Access list & NAT PowerPoint Presentation, free Router Access List Rules There are two basic rules, regardless of the type of acl that you want to configure: Access control list explained with examples. Helpful hints for creating ip access lists. There are some recommended best practices when creating and applying access control lists (acl). Learn cisco acls configuration commands with their. This document describes how ip access control lists (acls) can. Router Access List Rules.
From www.cisco.com
Access Rules Configuration on RV320 and RV325 VPN Routers Cisco Router Access List Rules There are some recommended best practices when creating and applying access control lists (acl). This tutorial explains how to configure cisco access control lists. Ip access list process and rules. Helpful hints for creating ip access lists. Learn cisco acls configuration commands with their. To create a standard access list, it uses the following syntax. It also contains brief descriptions. Router Access List Rules.
From www.slideserve.com
PPT Access Control List (ACL) PowerPoint Presentation, free download Router Access List Rules This document describes how ip access control lists (acls) can filter network traffic. Learn cisco acls configuration commands with their. It also contains brief descriptions of the. There are two basic rules, regardless of the type of acl that you want to configure: To create a standard access list, it uses the following syntax. This tutorial explains how to configure. Router Access List Rules.
From www.wikihow.com
How to Access a Router (with Pictures) wikiHow Router Access List Rules The network administrator should apply a standard acl closest. It also contains brief descriptions of the. There are two basic rules, regardless of the type of acl that you want to configure: Learn cisco acls configuration commands with their. If an acl has multiple entries, each entry is read. This document describes how ip access control lists (acls) can filter. Router Access List Rules.
From www.ciscoforall.com
CCNA basic router commands for the 640607 exams » CiscoForAll Router Access List Rules This document describes how ip access control lists (acls) can filter network traffic. To create a standard access list, it uses the following syntax. There are two basic rules, regardless of the type of acl that you want to configure: It also contains brief descriptions of the. Ip access list process and rules. If an acl has multiple entries, each. Router Access List Rules.
From www.cisco.com
Access Rules Configuration on RV320 and RV325 VPN Routers Cisco Router Access List Rules Helpful hints for creating ip access lists. To create a standard access list, it uses the following syntax. Learn cisco acls configuration commands with their. If an acl has multiple entries, each entry is read. There are two basic rules, regardless of the type of acl that you want to configure: Access control list explained with examples. The network administrator. Router Access List Rules.
From www.slideserve.com
PPT Access Lists PowerPoint Presentation, free download ID6949680 Router Access List Rules If an acl has multiple entries, each entry is read. Learn cisco acls configuration commands with their. Helpful hints for creating ip access lists. The network administrator should apply a standard acl closest. Ip access list process and rules. There are some recommended best practices when creating and applying access control lists (acl). There are two basic rules, regardless of. Router Access List Rules.
From www.vrogue.co
Ccna Complete Course Access Control List Acl Configur vrogue.co Router Access List Rules To create a standard access list, it uses the following syntax. The network administrator should apply a standard acl closest. This document describes how ip access control lists (acls) can filter network traffic. Helpful hints for creating ip access lists. Learn cisco acls configuration commands with their. Access control list explained with examples. This tutorial explains how to configure cisco. Router Access List Rules.
From www.slideserve.com
PPT Basic IP Traffic Management with Access Lists PowerPoint Router Access List Rules There are some recommended best practices when creating and applying access control lists (acl). There are two basic rules, regardless of the type of acl that you want to configure: Access control list explained with examples. Helpful hints for creating ip access lists. If an acl has multiple entries, each entry is read. To create a standard access list, it. Router Access List Rules.
From www.slideserve.com
PPT Access Lists PowerPoint Presentation, free download ID6949680 Router Access List Rules There are some recommended best practices when creating and applying access control lists (acl). This tutorial explains how to configure cisco access control lists. Helpful hints for creating ip access lists. This document describes how ip access control lists (acls) can filter network traffic. Ip access list process and rules. There are two basic rules, regardless of the type of. Router Access List Rules.
From in.pinterest.com
Router Access List Configuration Router, Networking, List Router Access List Rules Ip access list process and rules. It also contains brief descriptions of the. Helpful hints for creating ip access lists. This tutorial explains how to configure cisco access control lists. There are some recommended best practices when creating and applying access control lists (acl). There are two basic rules, regardless of the type of acl that you want to configure:. Router Access List Rules.
From www.slideserve.com
PPT CN2668 Routers and Switches PowerPoint Presentation, free Router Access List Rules There are some recommended best practices when creating and applying access control lists (acl). Ip access list process and rules. It also contains brief descriptions of the. There are two basic rules, regardless of the type of acl that you want to configure: Helpful hints for creating ip access lists. This document describes how ip access control lists (acls) can. Router Access List Rules.
From www.youtube.com
What is ACL (Access Control List) YouTube Router Access List Rules Access control list explained with examples. This tutorial explains how to configure cisco access control lists. There are some recommended best practices when creating and applying access control lists (acl). There are two basic rules, regardless of the type of acl that you want to configure: Helpful hints for creating ip access lists. Learn cisco acls configuration commands with their.. Router Access List Rules.
From www.slideserve.com
PPT packet filters using cisco access lists PowerPoint Presentation Router Access List Rules There are some recommended best practices when creating and applying access control lists (acl). Access control list explained with examples. It also contains brief descriptions of the. The network administrator should apply a standard acl closest. If an acl has multiple entries, each entry is read. This document describes how ip access control lists (acls) can filter network traffic. Ip. Router Access List Rules.
From www.howtonetwork.com
Access Control Lists ACLs Router Access List Rules This tutorial explains how to configure cisco access control lists. To create a standard access list, it uses the following syntax. There are two basic rules, regardless of the type of acl that you want to configure: The network administrator should apply a standard acl closest. There are some recommended best practices when creating and applying access control lists (acl).. Router Access List Rules.
From www.slideserve.com
PPT Basic IP Traffic Management with Access Lists PowerPoint Router Access List Rules The network administrator should apply a standard acl closest. Helpful hints for creating ip access lists. If an acl has multiple entries, each entry is read. There are some recommended best practices when creating and applying access control lists (acl). It also contains brief descriptions of the. This document describes how ip access control lists (acls) can filter network traffic.. Router Access List Rules.
From www.tomsguide.com
How to access your router's settings Tom's Guide Router Access List Rules Access control list explained with examples. This document describes how ip access control lists (acls) can filter network traffic. Learn cisco acls configuration commands with their. To create a standard access list, it uses the following syntax. If an acl has multiple entries, each entry is read. Ip access list process and rules. There are some recommended best practices when. Router Access List Rules.
From www.slideserve.com
PPT CHAPTER 6 Access list & NAT PowerPoint Presentation, free Router Access List Rules Ip access list process and rules. This document describes how ip access control lists (acls) can filter network traffic. Helpful hints for creating ip access lists. It also contains brief descriptions of the. If an acl has multiple entries, each entry is read. There are some recommended best practices when creating and applying access control lists (acl). The network administrator. Router Access List Rules.
From www.slideserve.com
PPT Access Control Lists PowerPoint Presentation, free download ID Router Access List Rules There are two basic rules, regardless of the type of acl that you want to configure: The network administrator should apply a standard acl closest. If an acl has multiple entries, each entry is read. Access control list explained with examples. It also contains brief descriptions of the. Ip access list process and rules. Helpful hints for creating ip access. Router Access List Rules.
From www.comparitech.com
How to create & configure an access control list (ACL) stepbystep Router Access List Rules Access control list explained with examples. Helpful hints for creating ip access lists. It also contains brief descriptions of the. This tutorial explains how to configure cisco access control lists. To create a standard access list, it uses the following syntax. If an acl has multiple entries, each entry is read. Learn cisco acls configuration commands with their. There are. Router Access List Rules.
From www.techtarget.com
What is a Routing Table? A Definition from Router Access List Rules This tutorial explains how to configure cisco access control lists. To create a standard access list, it uses the following syntax. Learn cisco acls configuration commands with their. There are some recommended best practices when creating and applying access control lists (acl). Access control list explained with examples. The network administrator should apply a standard acl closest. If an acl. Router Access List Rules.
From www.networkeducator.com
What Is Access Control List (ACL) & How It Works Network Educator Router Access List Rules The network administrator should apply a standard acl closest. Ip access list process and rules. Access control list explained with examples. Helpful hints for creating ip access lists. This tutorial explains how to configure cisco access control lists. It also contains brief descriptions of the. Learn cisco acls configuration commands with their. To create a standard access list, it uses. Router Access List Rules.
From ccnaciscocertifiednetworkassociate.blogspot.com
ACL in Router(Access Control List) Router Access List Rules Ip access list process and rules. Helpful hints for creating ip access lists. To create a standard access list, it uses the following syntax. This document describes how ip access control lists (acls) can filter network traffic. It also contains brief descriptions of the. Access control list explained with examples. This tutorial explains how to configure cisco access control lists.. Router Access List Rules.
From www.scribd.com
A Comprehensive Guide to Access Control Lists for IPv4 and IPv6 Router Access List Rules There are some recommended best practices when creating and applying access control lists (acl). To create a standard access list, it uses the following syntax. It also contains brief descriptions of the. The network administrator should apply a standard acl closest. Access control list explained with examples. Ip access list process and rules. If an acl has multiple entries, each. Router Access List Rules.
From www.securew2.com
Windows Access Control ACL, DACL, SACL, & ACE Router Access List Rules If an acl has multiple entries, each entry is read. Ip access list process and rules. Helpful hints for creating ip access lists. There are two basic rules, regardless of the type of acl that you want to configure: This document describes how ip access control lists (acls) can filter network traffic. There are some recommended best practices when creating. Router Access List Rules.
From ipcisco.com
Routing Table Cisco Router Routing Tables ⋆ IpCisco Router Access List Rules There are some recommended best practices when creating and applying access control lists (acl). The network administrator should apply a standard acl closest. There are two basic rules, regardless of the type of acl that you want to configure: It also contains brief descriptions of the. This tutorial explains how to configure cisco access control lists. If an acl has. Router Access List Rules.
From www.slideserve.com
PPT Access Lists PowerPoint Presentation, free download ID6949680 Router Access List Rules This tutorial explains how to configure cisco access control lists. It also contains brief descriptions of the. This document describes how ip access control lists (acls) can filter network traffic. Helpful hints for creating ip access lists. There are two basic rules, regardless of the type of acl that you want to configure: If an acl has multiple entries, each. Router Access List Rules.
From www.youtube.com
Configure Cisco Named Standard Access Control List ACL on Cisco routers Router Access List Rules This document describes how ip access control lists (acls) can filter network traffic. To create a standard access list, it uses the following syntax. It also contains brief descriptions of the. There are some recommended best practices when creating and applying access control lists (acl). Ip access list process and rules. This tutorial explains how to configure cisco access control. Router Access List Rules.
From www.slideserve.com
PPT Network Plus Unit 5 Section 1 Security PowerPoint Presentation Router Access List Rules Access control list explained with examples. There are two basic rules, regardless of the type of acl that you want to configure: The network administrator should apply a standard acl closest. This tutorial explains how to configure cisco access control lists. This document describes how ip access control lists (acls) can filter network traffic. Helpful hints for creating ip access. Router Access List Rules.