Java Injection Vulnerability . My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. Injection prevention in java ¶. Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. Sample code used in tips is. This section aims to provide tips to handle injection in java application code. The simplest solution is to use preparedstatement instead of statement to. An application is vulnerable to attack when: Preventing sql injection in java code.
from www.vaadata.com
Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. The simplest solution is to use preparedstatement instead of statement to. This section aims to provide tips to handle injection in java application code. It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. An application is vulnerable to attack when: My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. Sample code used in tips is. Injection prevention in java ¶. Preventing sql injection in java code.
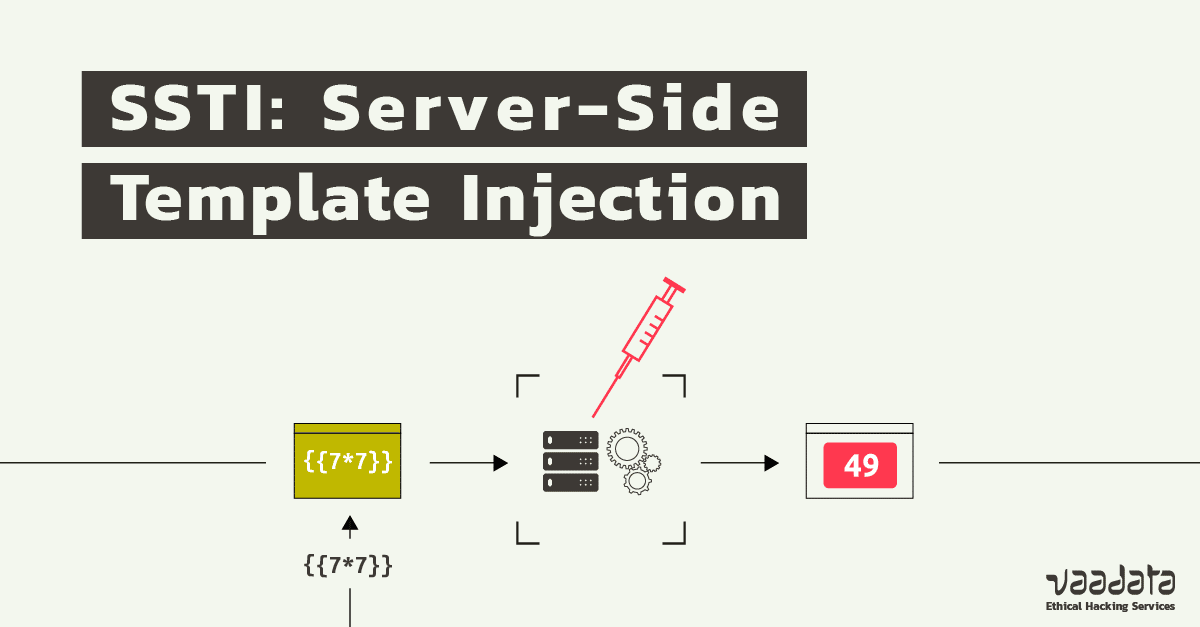
ServerSide Template Injection how to prevent it
Java Injection Vulnerability An application is vulnerable to attack when: Preventing sql injection in java code. Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. This section aims to provide tips to handle injection in java application code. The simplest solution is to use preparedstatement instead of statement to. An application is vulnerable to attack when: It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. Injection prevention in java ¶. Sample code used in tips is.
From www.youtube.com
Java Dependency Injection Tutorial YouTube Java Injection Vulnerability Preventing sql injection in java code. My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. An application is vulnerable to attack when: Sample code used in tips is.. Java Injection Vulnerability.
From github.com
SQL injection vulnerability exists in JFinal CMS 5.1.0 · Issue 38 Java Injection Vulnerability An application is vulnerable to attack when: The simplest solution is to use preparedstatement instead of statement to. Injection prevention in java ¶. It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. This section aims to provide tips to handle injection in java application code. Sample code. Java Injection Vulnerability.
From github.com
There is an SQL injection vulnerability in the crmeb_java system (/api Java Injection Vulnerability Preventing sql injection in java code. This section aims to provide tips to handle injection in java application code. My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability.. Java Injection Vulnerability.
From www.automox.com
What is SQL Injection Vulnerability? Java Injection Vulnerability Injection prevention in java ¶. Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. This section aims to provide tips to handle injection in java application code. Sample code used in tips is. An application is vulnerable to attack when: My best attempt at defending so far is to reject any. Java Injection Vulnerability.
From github.com
There is an SQL injection vulnerability in the crmeb_java system (/api Java Injection Vulnerability My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. This section aims to provide tips to handle injection in java application code. An application. Java Injection Vulnerability.
From medium.com
Understanding and Preventing SQL Injection Vulnerabilities in Java Injection Vulnerability The simplest solution is to use preparedstatement instead of statement to. Sample code used in tips is. It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. An application is. Java Injection Vulnerability.
From www.acunetix.com
Java Vulnerability Scanner Java Injection Vulnerability Preventing sql injection in java code. It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. An application is vulnerable to attack when: The simplest solution is to use preparedstatement instead of statement to. Sample code used in tips is. This section aims to provide tips to handle. Java Injection Vulnerability.
From blog.meterian.com
Vulnerability Focus Command Injection Ship software without Java Injection Vulnerability My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. Injection prevention in java ¶. The simplest solution is to use preparedstatement instead of statement to. Preventing sql injection in java code. This section aims to provide tips to handle injection in java application code. It can. Java Injection Vulnerability.
From www.vaadata.com
ServerSide Template Injection how to prevent it Java Injection Vulnerability This section aims to provide tips to handle injection in java application code. Preventing sql injection in java code. An application is vulnerable to attack when: Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. The simplest solution is to use preparedstatement instead of statement to. It can include everything from. Java Injection Vulnerability.
From securitylabs.datadoghq.com
The Spring4Shell vulnerability Overview, detection, and remediation Java Injection Vulnerability Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. Preventing sql injection in java code. An application is vulnerable to attack when: This section aims to provide tips to handle injection in java application code. My best attempt at defending so far is to reject any entries that match file.isabsolute() and. Java Injection Vulnerability.
From www.geeksforgeeks.org
What are Injection Flaws? Java Injection Vulnerability This section aims to provide tips to handle injection in java application code. Preventing sql injection in java code. An application is vulnerable to attack when: The simplest solution is to use preparedstatement instead of statement to. It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. Sample. Java Injection Vulnerability.
From github.com
There is an SQL injection vulnerability in the crmeb_java system (/api Java Injection Vulnerability The simplest solution is to use preparedstatement instead of statement to. This section aims to provide tips to handle injection in java application code. Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. An application is vulnerable to attack when: It can include everything from sql and xss — the rock. Java Injection Vulnerability.
From github.com
GitHub Grantex/SQLinjectionvulnerabilityassessor The SQL Java Injection Vulnerability Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. It can include everything from sql and xss — the rock stars of injection — to improper control of. Java Injection Vulnerability.
From github.com
There is a sql injection vulnerability exists in crmeb_java · Issue 9 Java Injection Vulnerability The simplest solution is to use preparedstatement instead of statement to. This section aims to provide tips to handle injection in java application code. Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. Injection prevention in java ¶. Sample code used in tips is. My best attempt at defending so far. Java Injection Vulnerability.
From www.stackspot.com
Application Security Automatic Fixes for Vulnerabilities with AI Java Injection Vulnerability The simplest solution is to use preparedstatement instead of statement to. Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. Injection prevention in java ¶. This section aims to provide tips to handle injection in java application code. An application is vulnerable to attack when: Preventing sql injection in java code.. Java Injection Vulnerability.
From www.slideserve.com
PPT Finding Security Vulnerabilities in Java Applications with Static Java Injection Vulnerability It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. An application is vulnerable to attack when: Sample code used in tips is. This section aims to provide tips to handle injection in java application code. Preventing sql injection in java code. Depending on the permissions of the. Java Injection Vulnerability.
From github.com
There is a sql injection vulnerability in the crmeb_java system /api Java Injection Vulnerability This section aims to provide tips to handle injection in java application code. Preventing sql injection in java code. The simplest solution is to use preparedstatement instead of statement to. Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. An application is vulnerable to attack when: Injection prevention in java ¶.. Java Injection Vulnerability.
From www.theknowledgeacademy.com
SQL Injection in Cyber Security A Brief Guide Java Injection Vulnerability Injection prevention in java ¶. My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. Sample code used in tips is. Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. The simplest solution is to use preparedstatement instead. Java Injection Vulnerability.
From www.artofit.org
Sql injection vulnerability how to prevent it devstringx Artofit Java Injection Vulnerability It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. Sample code used in tips is. The simplest solution is to use preparedstatement instead of statement to. Preventing sql injection in java code. This section aims to provide tips to handle injection in java application code. Depending on. Java Injection Vulnerability.
From www.geeksforgeeks.org
Vulnnr Vulnerability Scanner and Auto Exploiter in Kali Linux Java Injection Vulnerability My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. Sample code used in tips is. It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. An application is vulnerable to attack when: This section. Java Injection Vulnerability.
From github.com
There is a sql injection vulnerability exists in crmeb_java · Issue 9 Java Injection Vulnerability This section aims to provide tips to handle injection in java application code. Sample code used in tips is. Injection prevention in java ¶. My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. Depending on the permissions of the compromised application, attackers might be able to. Java Injection Vulnerability.
From www.xenonstack.com
Spring4shell A Critical Vulnerability in Spring Java Framework Java Injection Vulnerability Sample code used in tips is. It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. An application is vulnerable to attack when: The simplest solution is to use preparedstatement instead of statement to. Injection prevention in java ¶. My best attempt at defending so far is to. Java Injection Vulnerability.
From securityboulevard.com
10 Critical Vulnerabilities Found in ERP Applications Security Boulevard Java Injection Vulnerability This section aims to provide tips to handle injection in java application code. It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. Sample code used in tips is. Injection prevention in java ¶. An application is vulnerable to attack when: Depending on the permissions of the compromised. Java Injection Vulnerability.
From github.com
There is a sql injection vulnerability in the crmeb_java system /api Java Injection Vulnerability Sample code used in tips is. Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. Injection prevention in java ¶. An application is vulnerable to attack when: Preventing sql. Java Injection Vulnerability.
From docs.pega.com
Check for Java injection vulnerabilities (8.3) Pega Java Injection Vulnerability My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. Preventing sql injection in java code. Injection prevention in java ¶. The simplest solution is. Java Injection Vulnerability.
From secromix.com
OWASP TOP 10 INJECTION VULNERABILITY SecroMix Java Injection Vulnerability An application is vulnerable to attack when: Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. Sample code used in tips is. Injection prevention in java ¶. My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. Preventing. Java Injection Vulnerability.
From www.acunetix.com
How To Prevent SQL Injections in Java Java Injection Vulnerability It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. Preventing sql injection in java code. Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. This section aims to provide tips to handle injection in java application code. An. Java Injection Vulnerability.
From github.com
There is a sql injection vulnerability in the crmeb_java system /api Java Injection Vulnerability Sample code used in tips is. An application is vulnerable to attack when: It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. This section aims to provide tips to handle injection in java application code. Depending on the permissions of the compromised application, attackers might be able. Java Injection Vulnerability.
From blog.geekster.in
SQL Injection Prevention in Java Top Tips for Secure Code Java Injection Vulnerability My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. Depending on the permissions of the compromised application, attackers might be able to use the. Java Injection Vulnerability.
From hackernoon.com
What is an SQL Injection Attack? How To Prevent SQL Injection Java Injection Vulnerability Injection prevention in java ¶. My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. Depending on the permissions of the compromised application, attackers might. Java Injection Vulnerability.
From spectralops.io
Top 10 Most Common Java Vulnerabilities You Need to Prevent Spectral Java Injection Vulnerability Sample code used in tips is. Preventing sql injection in java code. This section aims to provide tips to handle injection in java application code. The simplest solution is to use preparedstatement instead of statement to. An application is vulnerable to attack when: Injection prevention in java ¶. It can include everything from sql and xss — the rock stars. Java Injection Vulnerability.
From github.com
There is a sql injection vulnerability exists in crmeb_java · Issue 9 Java Injection Vulnerability An application is vulnerable to attack when: It can include everything from sql and xss — the rock stars of injection — to improper control of resource identifiers, which. Injection prevention in java ¶. This section aims to provide tips to handle injection in java application code. My best attempt at defending so far is to reject any entries that. Java Injection Vulnerability.
From www.youtube.com
Detecting Absence of Java Script Injection vulnerability using Mozilla Java Injection Vulnerability This section aims to provide tips to handle injection in java application code. Sample code used in tips is. Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. The simplest solution is to use preparedstatement instead of statement to. Preventing sql injection in java code. Injection prevention in java ¶. It. Java Injection Vulnerability.
From www.globaldots.com
How to Prevent SQL Injection Attacks? Best Practices GlobalDots Java Injection Vulnerability Injection prevention in java ¶. My best attempt at defending so far is to reject any entries that match file.isabsolute() and then rely on file.getcanonicalpath() to resolve any. An application is vulnerable to attack when: The simplest solution is to use preparedstatement instead of statement to. Depending on the permissions of the compromised application, attackers might be able to use. Java Injection Vulnerability.
From maximilienandile.github.io
Dependency injection What is it ? How to do it in Java ? Why to use Java Injection Vulnerability The simplest solution is to use preparedstatement instead of statement to. An application is vulnerable to attack when: Depending on the permissions of the compromised application, attackers might be able to use the template injection vulnerability. Sample code used in tips is. Preventing sql injection in java code. My best attempt at defending so far is to reject any entries. Java Injection Vulnerability.