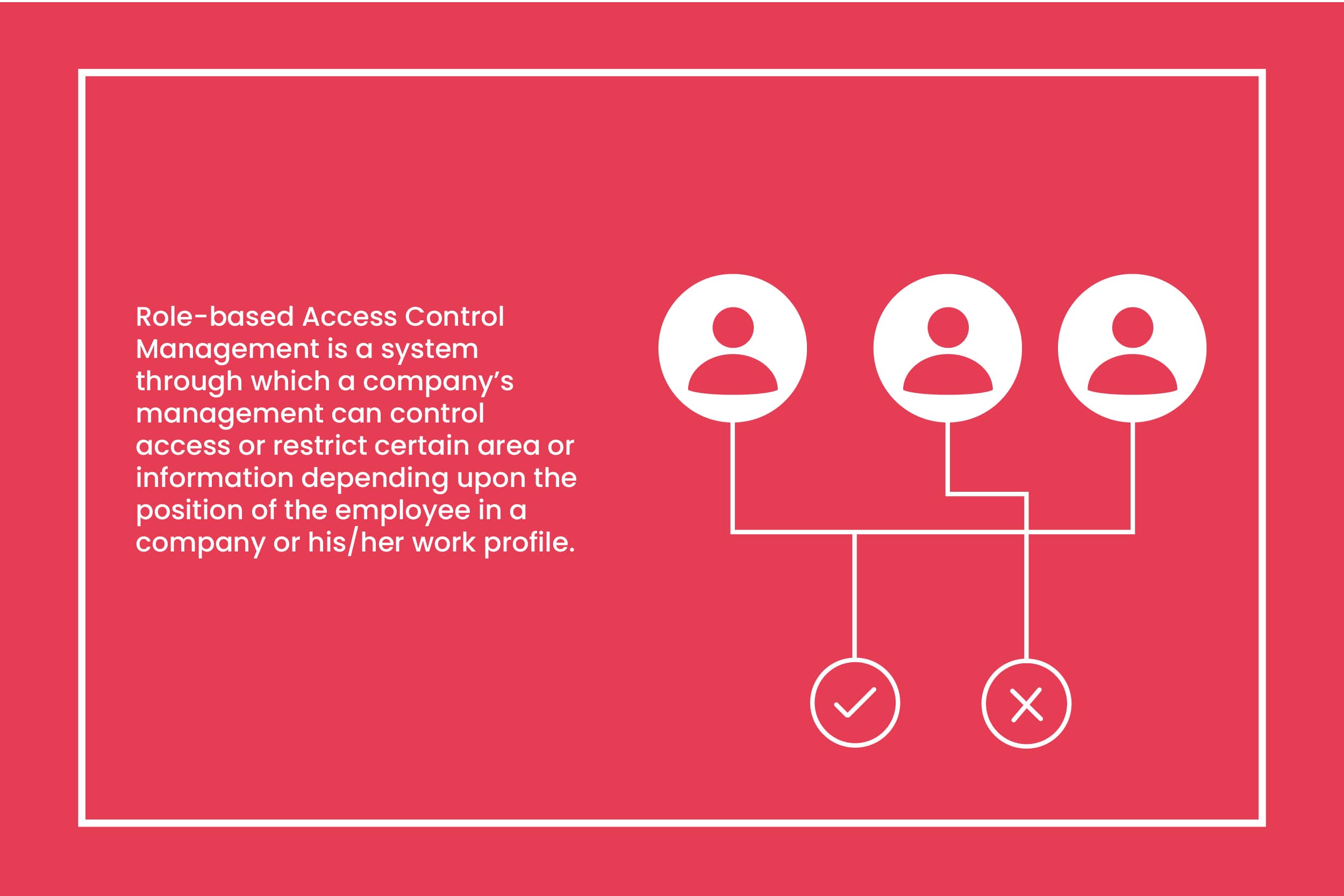
It Includes Registry Key Discretionary Access Control List . Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. Apply an audit access control entry (ace) to an object (e.g. If you’re unfamiliar with sacls, the concept is quite simple: A file, registry key) which logs when that object is successfully or. Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. If a windows object does not have a discretionary access control list (dacl), the system allows everyone full access to it. Discretionary access control list (dacl) a dacl (often mentioned as the acl) identify the users and groups that are assigned or denied access permissions on an object. Lets the user read and write the discretionary access control (dac) list for the key, which lets a user change the key's permissions. It contains a list of paired aces. A discretionary access control list (dacl) identifies the trustees that are allowed or denied access to a securable object.
from thesecurepass.com
Discretionary access control list (dacl) a dacl (often mentioned as the acl) identify the users and groups that are assigned or denied access permissions on an object. If you’re unfamiliar with sacls, the concept is quite simple: If a windows object does not have a discretionary access control list (dacl), the system allows everyone full access to it. Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. Lets the user read and write the discretionary access control (dac) list for the key, which lets a user change the key's permissions. A discretionary access control list (dacl) identifies the trustees that are allowed or denied access to a securable object. Apply an audit access control entry (ace) to an object (e.g. A file, registry key) which logs when that object is successfully or. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. It contains a list of paired aces.
Discretionary Access Control System Usage, Pros & Cons
It Includes Registry Key Discretionary Access Control List Discretionary access control list (dacl) a dacl (often mentioned as the acl) identify the users and groups that are assigned or denied access permissions on an object. Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. It contains a list of paired aces. Lets the user read and write the discretionary access control (dac) list for the key, which lets a user change the key's permissions. If you’re unfamiliar with sacls, the concept is quite simple: Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. If a windows object does not have a discretionary access control list (dacl), the system allows everyone full access to it. A discretionary access control list (dacl) identifies the trustees that are allowed or denied access to a securable object. Apply an audit access control entry (ace) to an object (e.g. A file, registry key) which logs when that object is successfully or. Discretionary access control list (dacl) a dacl (often mentioned as the acl) identify the users and groups that are assigned or denied access permissions on an object.
From thesecurepass.com
Discretionary Access Control System Usage, Pros & Cons It Includes Registry Key Discretionary Access Control List Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. A discretionary access control list (dacl) identifies the trustees that are. It Includes Registry Key Discretionary Access Control List.
From leocontent.umgc.edu
Access Control It Includes Registry Key Discretionary Access Control List Apply an audit access control entry (ace) to an object (e.g. A file, registry key) which logs when that object is successfully or. Discretionary access control list (dacl) a dacl (often mentioned as the acl) identify the users and groups that are assigned or denied access permissions on an object. Lets the user read and write the discretionary access control. It Includes Registry Key Discretionary Access Control List.
From www.slideserve.com
PPT Chapter 4 Access Control (Part B) PowerPoint Presentation, free It Includes Registry Key Discretionary Access Control List A file, registry key) which logs when that object is successfully or. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. Apply an audit access control entry (ace) to an object (e.g. A discretionary access control list (dacl). It Includes Registry Key Discretionary Access Control List.
From www.slideserve.com
PPT Lecture 7 Access Control PowerPoint Presentation, free download It Includes Registry Key Discretionary Access Control List If a windows object does not have a discretionary access control list (dacl), the system allows everyone full access to it. If you’re unfamiliar with sacls, the concept is quite simple: It contains a list of paired aces. Lets the user read and write the discretionary access control (dac) list for the key, which lets a user change the key's. It Includes Registry Key Discretionary Access Control List.
From wentzwu.com
Discretionary and NonDiscretionary Access Control Policies by Wentz Wu It Includes Registry Key Discretionary Access Control List A file, registry key) which logs when that object is successfully or. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. A discretionary access control list (dacl) identifies the trustees that are allowed or denied access to a. It Includes Registry Key Discretionary Access Control List.
From www.coursehero.com
[Solved] How is discretionary access control (DAC) implemented It Includes Registry Key Discretionary Access Control List Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. Apply an audit access control entry (ace) to an object (e.g. It contains a list of paired aces. A file, registry key) which logs when that object is successfully or. If you’re unfamiliar with sacls, the concept is quite simple: A discretionary. It Includes Registry Key Discretionary Access Control List.
From www.slideserve.com
PPT 8.2 Discretionary Access Control Models PowerPoint Presentation It Includes Registry Key Discretionary Access Control List Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. It contains a list of paired aces. Lets the user read and write the discretionary access control (dac) list for the key, which lets a user change the key's permissions. If a windows object does not have a discretionary access control list. It Includes Registry Key Discretionary Access Control List.
From www.threatkey.com
ThreatKey The Case for Discretionary Access Control It Includes Registry Key Discretionary Access Control List A discretionary access control list (dacl) identifies the trustees that are allowed or denied access to a securable object. If a windows object does not have a discretionary access control list (dacl), the system allows everyone full access to it. Discretionary access control list (dacl) a dacl (often mentioned as the acl) identify the users and groups that are assigned. It Includes Registry Key Discretionary Access Control List.
From content-1606--budibase.netlify.app
RoleBased Access Control Ultimate Guide It Includes Registry Key Discretionary Access Control List Apply an audit access control entry (ace) to an object (e.g. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. A discretionary access control list (dacl) identifies the trustees that are allowed or denied access to a securable. It Includes Registry Key Discretionary Access Control List.
From mavink.com
Role Based Access Control Matrix It Includes Registry Key Discretionary Access Control List Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. A file, registry key) which logs when that object is successfully or. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or. It Includes Registry Key Discretionary Access Control List.
From www.slideserve.com
PPT 8.2 Discretionary Access Control Models PowerPoint Presentation It Includes Registry Key Discretionary Access Control List Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. Apply an audit access control entry (ace) to an object (e.g. A discretionary access control list (dacl) identifies the trustees that are allowed or denied access to a securable object. Lets the user read and write the discretionary access control (dac) list. It Includes Registry Key Discretionary Access Control List.
From www.thesecurepass.com
Access Control System Types, Pros & Cons SecurePass It Includes Registry Key Discretionary Access Control List A file, registry key) which logs when that object is successfully or. Lets the user read and write the discretionary access control (dac) list for the key, which lets a user change the key's permissions. Apply an audit access control entry (ace) to an object (e.g. Information about the ace_string access mask components can be found in the msdn access_mask. It Includes Registry Key Discretionary Access Control List.
From matthewcaseres.gitbook.io
Discretionary Access Control OMSCS Notes It Includes Registry Key Discretionary Access Control List Lets the user read and write the discretionary access control (dac) list for the key, which lets a user change the key's permissions. If you’re unfamiliar with sacls, the concept is quite simple: A file, registry key) which logs when that object is successfully or. It contains a list of paired aces. Apply an audit access control entry (ace) to. It Includes Registry Key Discretionary Access Control List.
From www.omscs-notes.com
Discretionary Access Control OMSCS Notes It Includes Registry Key Discretionary Access Control List A discretionary access control list (dacl) identifies the trustees that are allowed or denied access to a securable object. Discretionary access control list (dacl) a dacl (often mentioned as the acl) identify the users and groups that are assigned or denied access permissions on an object. Lets the user read and write the discretionary access control (dac) list for the. It Includes Registry Key Discretionary Access Control List.
From www.slideserve.com
PPT Access Control PowerPoint Presentation, free download ID6099376 It Includes Registry Key Discretionary Access Control List It contains a list of paired aces. Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. Apply an audit access control entry (ace) to an object (e.g. A file, registry key) which logs when that object is successfully or. Discretionary access control list (dacl) a dacl (often mentioned as the acl). It Includes Registry Key Discretionary Access Control List.
From techcommunity.microsoft.com
Active Directory Access Control List Attacks and Defense Microsoft It Includes Registry Key Discretionary Access Control List A file, registry key) which logs when that object is successfully or. Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. Lets the user read and write the discretionary access control (dac) list for the key, which lets a user change the key's permissions. It contains a list of paired aces.. It Includes Registry Key Discretionary Access Control List.
From nordlayer.com
What is Discretionary Access Control? NordLayer Learn It Includes Registry Key Discretionary Access Control List A file, registry key) which logs when that object is successfully or. If you’re unfamiliar with sacls, the concept is quite simple: A discretionary access control list (dacl) identifies the trustees that are allowed or denied access to a securable object. Discretionary access control list (dacl) a dacl (often mentioned as the acl) identify the users and groups that are. It Includes Registry Key Discretionary Access Control List.
From digitalmediaglobe.com
What is a Registry Key? What is a Registry Value? Detail Explanation! It Includes Registry Key Discretionary Access Control List Discretionary access control list (dacl) a dacl (often mentioned as the acl) identify the users and groups that are assigned or denied access permissions on an object. Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. Apply an audit access control entry (ace) to an object (e.g. A file, registry key). It Includes Registry Key Discretionary Access Control List.
From www.slideserve.com
PPT Access control models and policies PowerPoint Presentation, free It Includes Registry Key Discretionary Access Control List It contains a list of paired aces. If you’re unfamiliar with sacls, the concept is quite simple: Apply an audit access control entry (ace) to an object (e.g. A file, registry key) which logs when that object is successfully or. If a windows object does not have a discretionary access control list (dacl), the system allows everyone full access to. It Includes Registry Key Discretionary Access Control List.
From spectralops.io
6 Examples of Discretionary Access Control (DAC) Spectral It Includes Registry Key Discretionary Access Control List It contains a list of paired aces. A file, registry key) which logs when that object is successfully or. Apply an audit access control entry (ace) to an object (e.g. Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. Discretionary access control list (dacl) a dacl (often mentioned as the acl). It Includes Registry Key Discretionary Access Control List.
From securityboulevard.com
6 Examples of Discretionary Access Control (DAC) Security Boulevard It Includes Registry Key Discretionary Access Control List Lets the user read and write the discretionary access control (dac) list for the key, which lets a user change the key's permissions. If a windows object does not have a discretionary access control list (dacl), the system allows everyone full access to it. A discretionary access control list (dacl) identifies the trustees that are allowed or denied access to. It Includes Registry Key Discretionary Access Control List.
From www.scribd.com
Discretionary access control PDF It Includes Registry Key Discretionary Access Control List Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. Apply an audit access control entry (ace) to an object (e.g.. It Includes Registry Key Discretionary Access Control List.
From thesecurepass.com
Discretionary Access Control System Usage, Pros & Cons It Includes Registry Key Discretionary Access Control List A file, registry key) which logs when that object is successfully or. It contains a list of paired aces. Apply an audit access control entry (ace) to an object (e.g. If a windows object does not have a discretionary access control list (dacl), the system allows everyone full access to it. Information about the ace_string access mask components can be. It Includes Registry Key Discretionary Access Control List.
From medium.com
what is discretionary access control (DAC) by Erion Xu Medium It Includes Registry Key Discretionary Access Control List A discretionary access control list (dacl) identifies the trustees that are allowed or denied access to a securable object. If a windows object does not have a discretionary access control list (dacl), the system allows everyone full access to it. It contains a list of paired aces. Each permission rule in an acl is known as an access control entry. It Includes Registry Key Discretionary Access Control List.
From techcommunity.microsoft.com
Active Directory Access Control List Attacks and Defense Microsoft It Includes Registry Key Discretionary Access Control List A discretionary access control list (dacl) identifies the trustees that are allowed or denied access to a securable object. If a windows object does not have a discretionary access control list (dacl), the system allows everyone full access to it. If you’re unfamiliar with sacls, the concept is quite simple: It contains a list of paired aces. Discretionary access control. It Includes Registry Key Discretionary Access Control List.
From blog.nortechcontrol.com
What Is Access Control? (Simple Guide) It Includes Registry Key Discretionary Access Control List Apply an audit access control entry (ace) to an object (e.g. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. It contains a list of paired aces. A file, registry key) which logs when that object is successfully. It Includes Registry Key Discretionary Access Control List.
From www.slideserve.com
PPT Chapter 4 Access Control (Part B) PowerPoint Presentation, free It Includes Registry Key Discretionary Access Control List Lets the user read and write the discretionary access control (dac) list for the key, which lets a user change the key's permissions. If you’re unfamiliar with sacls, the concept is quite simple: Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. If a windows object does not have a discretionary. It Includes Registry Key Discretionary Access Control List.
From www.slideserve.com
PPT Access control models and policies PowerPoint Presentation, free It Includes Registry Key Discretionary Access Control List A file, registry key) which logs when that object is successfully or. Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or. It Includes Registry Key Discretionary Access Control List.
From www.slideserve.com
PPT Access Control Models PowerPoint Presentation, free download ID It Includes Registry Key Discretionary Access Control List It contains a list of paired aces. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. A discretionary access control list (dacl) identifies the trustees that are allowed or denied access to a securable object. Discretionary access control. It Includes Registry Key Discretionary Access Control List.
From cyberhoot.com
Discretionary Access Controls (DAC) CyberHoot It Includes Registry Key Discretionary Access Control List Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. A file, registry key) which logs when that object is successfully or. If a windows object does not have a discretionary access control list (dacl), the system allows everyone full access to it. Each permission rule in an acl is known as. It Includes Registry Key Discretionary Access Control List.
From www.slideserve.com
PPT 8.2 Discretionary Access Control Models PowerPoint Presentation It Includes Registry Key Discretionary Access Control List It contains a list of paired aces. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. If you’re unfamiliar with sacls, the concept is quite simple: Lets the user read and write the discretionary access control (dac) list. It Includes Registry Key Discretionary Access Control List.
From www.youtube.com
Discretionary Access Control List (DACL) Network Encyclopedia YouTube It Includes Registry Key Discretionary Access Control List If you’re unfamiliar with sacls, the concept is quite simple: Discretionary access control list (dacl) a dacl (often mentioned as the acl) identify the users and groups that are assigned or denied access permissions on an object. Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified. It Includes Registry Key Discretionary Access Control List.
From matthewcaseres.gitbook.io
Discretionary Access Control OMSCS Notes It Includes Registry Key Discretionary Access Control List Apply an audit access control entry (ace) to an object (e.g. It contains a list of paired aces. If you’re unfamiliar with sacls, the concept is quite simple: Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. If. It Includes Registry Key Discretionary Access Control List.
From thesecurepass.com
Discretionary Access Control System Usage, Pros & Cons It Includes Registry Key Discretionary Access Control List Each permission rule in an acl is known as an access control entry (ace), which controls access to an object by a specified trustee, such as a person, group, or session. If a windows object does not have a discretionary access control list (dacl), the system allows everyone full access to it. Lets the user read and write the discretionary. It Includes Registry Key Discretionary Access Control List.
From www.slideserve.com
PPT Access Control PowerPoint Presentation, free download ID2788302 It Includes Registry Key Discretionary Access Control List Information about the ace_string access mask components can be found in the msdn access_mask article, which includes pointers. Apply an audit access control entry (ace) to an object (e.g. It contains a list of paired aces. A discretionary access control list (dacl) identifies the trustees that are allowed or denied access to a securable object. If you’re unfamiliar with sacls,. It Includes Registry Key Discretionary Access Control List.