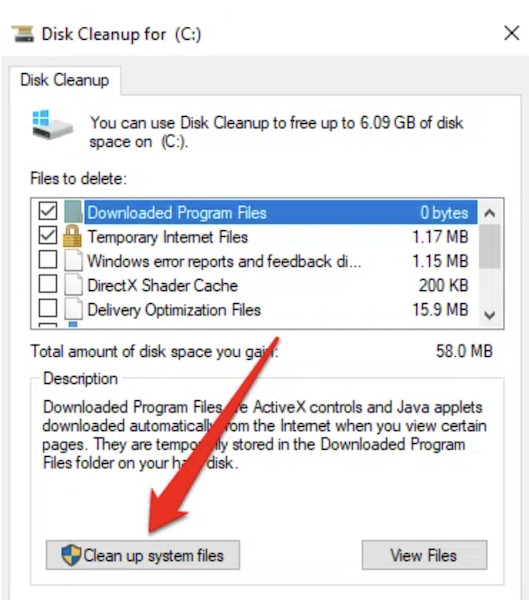
When Cleaning Up A System After A Compromise . Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. Application patching is equally important, particularly business productivity applications such as email clients, vpn clients,. How to recover systems in the event of a cyber attack. Recovering compromised systems after a cyber attack. Reinstalling a computer after it has been compromised can be. We recommend reinstalling your operating system, but if that is not practical you can try this option first. If you receive a security. If your computer has been compromised and infected with a virus or other malware you need to take action to keep your files from being. The following is a general guide on how to perform a clean reinstall of your computer. Giving customers back control of their environment after a compromise.
from tencomputer.com
If your computer has been compromised and infected with a virus or other malware you need to take action to keep your files from being. Giving customers back control of their environment after a compromise. Reinstalling a computer after it has been compromised can be. Recovering compromised systems after a cyber attack. We recommend reinstalling your operating system, but if that is not practical you can try this option first. Application patching is equally important, particularly business productivity applications such as email clients, vpn clients,. How to recover systems in the event of a cyber attack. The following is a general guide on how to perform a clean reinstall of your computer. Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. If you receive a security.
Fix Broken Registry Items on Windows 10, 8, 7
When Cleaning Up A System After A Compromise Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. The following is a general guide on how to perform a clean reinstall of your computer. Giving customers back control of their environment after a compromise. Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. If you receive a security. Recovering compromised systems after a cyber attack. Reinstalling a computer after it has been compromised can be. If your computer has been compromised and infected with a virus or other malware you need to take action to keep your files from being. How to recover systems in the event of a cyber attack. We recommend reinstalling your operating system, but if that is not practical you can try this option first. Application patching is equally important, particularly business productivity applications such as email clients, vpn clients,.
From www.facebook.com
DEEP CLEAN SERIES kitchen edition A long overdue deep clean of the When Cleaning Up A System After A Compromise Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. If you receive a security. Giving customers back control of their environment after a compromise. How to recover systems in the event of a cyber attack. Application patching is equally important, particularly business productivity applications such as email clients, vpn clients,.. When Cleaning Up A System After A Compromise.
From gearupwindows.com
Cleaning Up System Restore Points How to Delete Old Ones in Windows 10 When Cleaning Up A System After A Compromise How to recover systems in the event of a cyber attack. The following is a general guide on how to perform a clean reinstall of your computer. We recommend reinstalling your operating system, but if that is not practical you can try this option first. Giving customers back control of their environment after a compromise. Recovering compromised systems after a. When Cleaning Up A System After A Compromise.
From www.facebook.com
DEEP CLEAN SERIES kitchen edition A long overdue deep clean of the When Cleaning Up A System After A Compromise If your computer has been compromised and infected with a virus or other malware you need to take action to keep your files from being. If you receive a security. Recovering compromised systems after a cyber attack. Reinstalling a computer after it has been compromised can be. Ensure you follow up any pointers that suggest compromised systems could become a. When Cleaning Up A System After A Compromise.
From exofdhaqe.blob.core.windows.net
Water Treatment Plant In Quezon City at Harry Williams blog When Cleaning Up A System After A Compromise Reinstalling a computer after it has been compromised can be. How to recover systems in the event of a cyber attack. Giving customers back control of their environment after a compromise. Application patching is equally important, particularly business productivity applications such as email clients, vpn clients,. If you receive a security. We recommend reinstalling your operating system, but if that. When Cleaning Up A System After A Compromise.
From www.youtube.com
How to Clean up System Reserved Partition in all Windows 10/8/7/XP in When Cleaning Up A System After A Compromise How to recover systems in the event of a cyber attack. We recommend reinstalling your operating system, but if that is not practical you can try this option first. Recovering compromised systems after a cyber attack. Giving customers back control of their environment after a compromise. The following is a general guide on how to perform a clean reinstall of. When Cleaning Up A System After A Compromise.
From consumingtech.com
Access Disk Cleanup in Windows 10 When Cleaning Up A System After A Compromise If you receive a security. Giving customers back control of their environment after a compromise. How to recover systems in the event of a cyber attack. The following is a general guide on how to perform a clean reinstall of your computer. We recommend reinstalling your operating system, but if that is not practical you can try this option first.. When Cleaning Up A System After A Compromise.
From theoceancleanup.com
The Ocean Cleanup When Cleaning Up A System After A Compromise Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. How to recover systems in the event of a cyber attack. The following is a general guide on how to perform a clean reinstall of your computer. Giving customers back control of their environment after a compromise. Reinstalling a computer after. When Cleaning Up A System After A Compromise.
From deal.town
NEW FLAVOR 🔵 Blue Raspberry Jocko Fuel When Cleaning Up A System After A Compromise Recovering compromised systems after a cyber attack. Giving customers back control of their environment after a compromise. Reinstalling a computer after it has been compromised can be. If your computer has been compromised and infected with a virus or other malware you need to take action to keep your files from being. Application patching is equally important, particularly business productivity. When Cleaning Up A System After A Compromise.
From flatworldknowledge.lardbucket.org
Where Are Vulnerabilities? Understanding the Weaknesses When Cleaning Up A System After A Compromise How to recover systems in the event of a cyber attack. Giving customers back control of their environment after a compromise. If you receive a security. Reinstalling a computer after it has been compromised can be. We recommend reinstalling your operating system, but if that is not practical you can try this option first. Application patching is equally important, particularly. When Cleaning Up A System After A Compromise.
From tencomputer.com
Fix Broken Registry Items on Windows 10, 8, 7 When Cleaning Up A System After A Compromise Reinstalling a computer after it has been compromised can be. Application patching is equally important, particularly business productivity applications such as email clients, vpn clients,. Recovering compromised systems after a cyber attack. If your computer has been compromised and infected with a virus or other malware you need to take action to keep your files from being. Giving customers back. When Cleaning Up A System After A Compromise.
From rescueclean911.com
Can Sunlight Kill Mold? Sunlight vs Bleach Cleaning 101 When Cleaning Up A System After A Compromise Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. How to recover systems in the event of a cyber attack. The following is a general guide on how to perform a clean reinstall of your computer. We recommend reinstalling your operating system, but if that is not practical you can. When Cleaning Up A System After A Compromise.
From ameristarfacilitysolutions.com
Deep Cleaning & Disinfecting Commercial Properties Ameristar Facility When Cleaning Up A System After A Compromise Reinstalling a computer after it has been compromised can be. If your computer has been compromised and infected with a virus or other malware you need to take action to keep your files from being. Application patching is equally important, particularly business productivity applications such as email clients, vpn clients,. Recovering compromised systems after a cyber attack. We recommend reinstalling. When Cleaning Up A System After A Compromise.
From slideplayer.com
CS 3700 Networks and Distributed Systems ppt download When Cleaning Up A System After A Compromise The following is a general guide on how to perform a clean reinstall of your computer. Recovering compromised systems after a cyber attack. How to recover systems in the event of a cyber attack. If your computer has been compromised and infected with a virus or other malware you need to take action to keep your files from being. If. When Cleaning Up A System After A Compromise.
From www.boredpanda.com
35 Satisfying Pics Of Spaces Before And After Being Cleaned Bored Panda When Cleaning Up A System After A Compromise The following is a general guide on how to perform a clean reinstall of your computer. Reinstalling a computer after it has been compromised can be. Giving customers back control of their environment after a compromise. We recommend reinstalling your operating system, but if that is not practical you can try this option first. Ensure you follow up any pointers. When Cleaning Up A System After A Compromise.
From www.anyclean.co.uk
End Of Tenancy Cleaning Bushy Park KT8 No Compromises With Quality When Cleaning Up A System After A Compromise Recovering compromised systems after a cyber attack. Application patching is equally important, particularly business productivity applications such as email clients, vpn clients,. We recommend reinstalling your operating system, but if that is not practical you can try this option first. The following is a general guide on how to perform a clean reinstall of your computer. Ensure you follow up. When Cleaning Up A System After A Compromise.
From www.cnet.com
How to clean out junk files in Windows 10 When Cleaning Up A System After A Compromise Recovering compromised systems after a cyber attack. How to recover systems in the event of a cyber attack. Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. If your computer has been compromised and infected with a virus or other malware you need to take action to keep your files. When Cleaning Up A System After A Compromise.
From cloud-atlas.readthedocs.io
清理旧Windows升级文件 — Cloud Atlas beta 文档 When Cleaning Up A System After A Compromise How to recover systems in the event of a cyber attack. Recovering compromised systems after a cyber attack. Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. If your computer has been compromised and infected with a virus or other malware you need to take action to keep your files. When Cleaning Up A System After A Compromise.
From www.guidingtech.com
6 Ways to Remove Residual Files After Uninstalling Software on Windows When Cleaning Up A System After A Compromise The following is a general guide on how to perform a clean reinstall of your computer. If your computer has been compromised and infected with a virus or other malware you need to take action to keep your files from being. Recovering compromised systems after a cyber attack. Reinstalling a computer after it has been compromised can be. If you. When Cleaning Up A System After A Compromise.
From biesse.com
Biesse Winline When Cleaning Up A System After A Compromise Reinstalling a computer after it has been compromised can be. Application patching is equally important, particularly business productivity applications such as email clients, vpn clients,. The following is a general guide on how to perform a clean reinstall of your computer. If your computer has been compromised and infected with a virus or other malware you need to take action. When Cleaning Up A System After A Compromise.
From www.youtube.com
How to clean junk files on windows 10? YouTube When Cleaning Up A System After A Compromise Application patching is equally important, particularly business productivity applications such as email clients, vpn clients,. Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. Giving customers back control of their environment after a compromise. If your computer has been compromised and infected with a virus or other malware you need. When Cleaning Up A System After A Compromise.
From deephacks.org
Extending the Functional Life of an Older Laptop When Cleaning Up A System After A Compromise Giving customers back control of their environment after a compromise. How to recover systems in the event of a cyber attack. Recovering compromised systems after a cyber attack. Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. Reinstalling a computer after it has been compromised can be. The following is. When Cleaning Up A System After A Compromise.
From www.homeparte.com
Everything About AC Chemical Wash and Cleaning Home Parte When Cleaning Up A System After A Compromise Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. If you receive a security. Reinstalling a computer after it has been compromised can be. Recovering compromised systems after a cyber attack. The following is a general guide on how to perform a clean reinstall of your computer. Giving customers back. When Cleaning Up A System After A Compromise.
From absolutelycleanservices.com
House Washing Absolutely Clean Services When Cleaning Up A System After A Compromise We recommend reinstalling your operating system, but if that is not practical you can try this option first. Giving customers back control of their environment after a compromise. Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. The following is a general guide on how to perform a clean reinstall. When Cleaning Up A System After A Compromise.
From www.makro.co.za
Snuggletime Foldable Baby High Chair High Chair (White) Makro When Cleaning Up A System After A Compromise Giving customers back control of their environment after a compromise. The following is a general guide on how to perform a clean reinstall of your computer. We recommend reinstalling your operating system, but if that is not practical you can try this option first. How to recover systems in the event of a cyber attack. Ensure you follow up any. When Cleaning Up A System After A Compromise.
From www.thisiscolossal.com
The Ocean Cleanup Conceptualizes Its Third Massive Apparatus to Remove When Cleaning Up A System After A Compromise If you receive a security. Giving customers back control of their environment after a compromise. We recommend reinstalling your operating system, but if that is not practical you can try this option first. Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. If your computer has been compromised and infected. When Cleaning Up A System After A Compromise.
From www.pinterest.com
Self Cleaning Kitchen Clean kitchen, Kitchen signs, Kitchen rules sign When Cleaning Up A System After A Compromise We recommend reinstalling your operating system, but if that is not practical you can try this option first. Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. If you receive a security. The following is a general guide on how to perform a clean reinstall of your computer. How to. When Cleaning Up A System After A Compromise.
From open.lib.umn.edu
13.3 Where Are Vulnerabilities? Understanding the Weaknesses When Cleaning Up A System After A Compromise Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. Giving customers back control of their environment after a compromise. The following is a general guide on how to perform a clean reinstall of your computer. We recommend reinstalling your operating system, but if that is not practical you can try. When Cleaning Up A System After A Compromise.
From kreafolk.com
Nail Salon Checklist How To Make Sure Your Salon Is Clean & Safe When Cleaning Up A System After A Compromise The following is a general guide on how to perform a clean reinstall of your computer. If your computer has been compromised and infected with a virus or other malware you need to take action to keep your files from being. Giving customers back control of their environment after a compromise. Recovering compromised systems after a cyber attack. How to. When Cleaning Up A System After A Compromise.
From www.performancecleaning.com.au
What Are the Most Overlooked Office Areas That Require Professional When Cleaning Up A System After A Compromise Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your systems further. Giving customers back control of their environment after a compromise. Reinstalling a computer after it has been compromised can be. How to recover systems in the event of a cyber attack. If you receive a security. We recommend reinstalling your operating. When Cleaning Up A System After A Compromise.
From pasadenadrycleaning.com
Convenient Laundry PickUp and Delivery in Pasadena Pasadena Dry When Cleaning Up A System After A Compromise Recovering compromised systems after a cyber attack. If you receive a security. How to recover systems in the event of a cyber attack. Reinstalling a computer after it has been compromised can be. Giving customers back control of their environment after a compromise. Ensure you follow up any pointers that suggest compromised systems could become a springboard to attack your. When Cleaning Up A System After A Compromise.
From cgjnxdfthrts.blogspot.com
compromise assessment malaysia racun shopee promo indonesia When Cleaning Up A System After A Compromise Application patching is equally important, particularly business productivity applications such as email clients, vpn clients,. Reinstalling a computer after it has been compromised can be. Giving customers back control of their environment after a compromise. How to recover systems in the event of a cyber attack. Recovering compromised systems after a cyber attack. We recommend reinstalling your operating system, but. When Cleaning Up A System After A Compromise.
From pasadenadrycleaning.com
Convenient Laundry PickUp and Delivery in Pasadena Pasadena Dry When Cleaning Up A System After A Compromise If you receive a security. The following is a general guide on how to perform a clean reinstall of your computer. Recovering compromised systems after a cyber attack. We recommend reinstalling your operating system, but if that is not practical you can try this option first. How to recover systems in the event of a cyber attack. Giving customers back. When Cleaning Up A System After A Compromise.
From cloud-atlas.readthedocs.io
清理旧Windows升级文件 — Cloud Atlas beta 文档 When Cleaning Up A System After A Compromise If your computer has been compromised and infected with a virus or other malware you need to take action to keep your files from being. The following is a general guide on how to perform a clean reinstall of your computer. We recommend reinstalling your operating system, but if that is not practical you can try this option first. Ensure. When Cleaning Up A System After A Compromise.
From exokikiss.blob.core.windows.net
Is There Free Land In Missouri at Sidney Quiroz blog When Cleaning Up A System After A Compromise We recommend reinstalling your operating system, but if that is not practical you can try this option first. How to recover systems in the event of a cyber attack. Giving customers back control of their environment after a compromise. If your computer has been compromised and infected with a virus or other malware you need to take action to keep. When Cleaning Up A System After A Compromise.
From servi-tek.net
Never Compromise Healthcare Cleaning Services ServiTek When Cleaning Up A System After A Compromise How to recover systems in the event of a cyber attack. We recommend reinstalling your operating system, but if that is not practical you can try this option first. Giving customers back control of their environment after a compromise. Reinstalling a computer after it has been compromised can be. Ensure you follow up any pointers that suggest compromised systems could. When Cleaning Up A System After A Compromise.