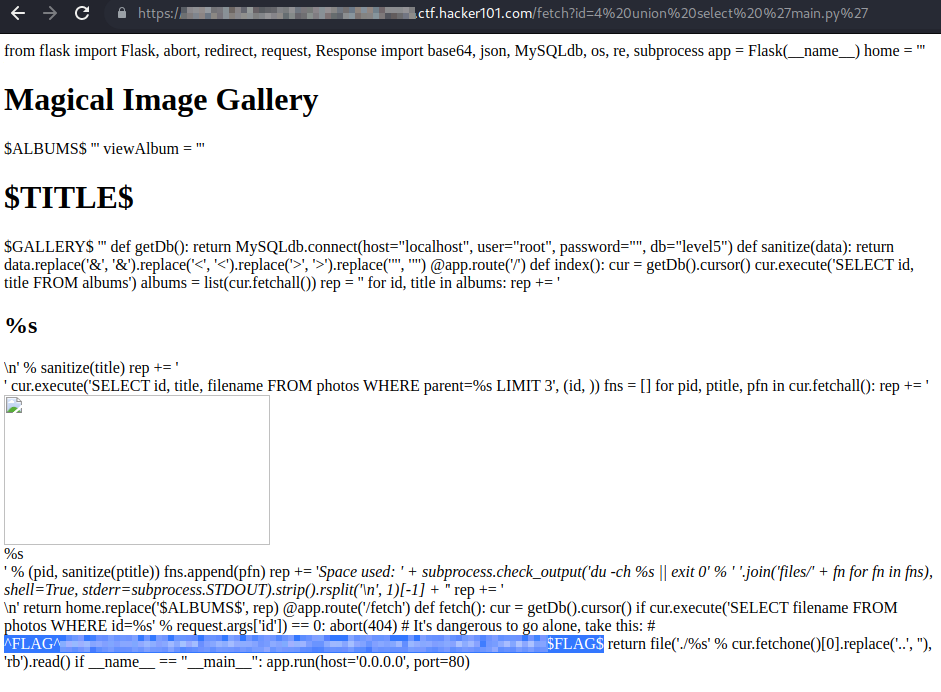
Photo Gallery Hacker101 . In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. So i started off with go buster but didn't find anything interesting. The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last flag. Consider how you might build this system yourself. This is a web challenge. This is my write up for the photo gallery challenge of hackerone's ctf. Ctf — hacker101 — photo gallery. This is the next challenge from hacker101 ctf after encrypted pastebin. As usual we get a link to webpage, it seems to be an image gallery, but one of the images is broken. A flask web application that pulls images from a database. My solution to the hacker101 image gallery challenge.
from d0rksec.github.io
Consider how you might build this system yourself. A flask web application that pulls images from a database. So i started off with go buster but didn't find anything interesting. The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. This is the next challenge from hacker101 ctf after encrypted pastebin. Ctf — hacker101 — photo gallery. This is my write up for the photo gallery challenge of hackerone's ctf. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last flag. In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. This is a web challenge.
Hacker101 Photo Gallery d0rksec
Photo Gallery Hacker101 This is a web challenge. In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. This is a web challenge. A flask web application that pulls images from a database. My solution to the hacker101 image gallery challenge. So i started off with go buster but didn't find anything interesting. The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. This is the next challenge from hacker101 ctf after encrypted pastebin. Consider how you might build this system yourself. This is my write up for the photo gallery challenge of hackerone's ctf. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last flag. As usual we get a link to webpage, it seems to be an image gallery, but one of the images is broken. Ctf — hacker101 — photo gallery.
From www.cnblogs.com
【hacker101 CTF】Photo Gallery yokan 博客园 Photo Gallery Hacker101 Consider how you might build this system yourself. As usual we get a link to webpage, it seems to be an image gallery, but one of the images is broken. The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. So i started off with go buster but didn't find anything interesting. This. Photo Gallery Hacker101.
From hackerone.com
Hacker101 for Hackers Photo Gallery Hacker101 A flask web application that pulls images from a database. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last flag. Ctf — hacker101 — photo gallery. This is my write up for the photo gallery challenge of hackerone's ctf. As usual we get a link to webpage, it. Photo Gallery Hacker101.
From www.hackerone.com
Introducing the Hacker101 CTF HackerOne Photo Gallery Hacker101 My solution to the hacker101 image gallery challenge. This is my write up for the photo gallery challenge of hackerone's ctf. In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. This is the next challenge from hacker101 ctf after encrypted pastebin. This is a web challenge. Ctf, the first two challenges are relatively trivial so. Photo Gallery Hacker101.
From hacker101.testerting.science
Photo Gallery FLAG1 hacker101ctf Photo Gallery Hacker101 So i started off with go buster but didn't find anything interesting. In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to. Photo Gallery Hacker101.
From blog.csdn.net
【hacker101 CTF】Photo Gallery_ctf photo galleryCSDN博客 Photo Gallery Hacker101 This is a web challenge. A flask web application that pulls images from a database. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last flag. Consider how you might build this system yourself. Ctf — hacker101 — photo gallery. My solution to the hacker101 image gallery challenge. The. Photo Gallery Hacker101.
From www.youtube.com
Hacker101 Mobile Hacking Crash Course YouTube Photo Gallery Hacker101 Consider how you might build this system yourself. A flask web application that pulls images from a database. This is the next challenge from hacker101 ctf after encrypted pastebin. As usual we get a link to webpage, it seems to be an image gallery, but one of the images is broken. This is a web challenge. This is my write. Photo Gallery Hacker101.
From medium.com
CTF — hacker101 — Photo Gallery. Hacker101 — CTF Challenge Write UP Photo Gallery Hacker101 The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. So i started off with go buster but didn't find anything interesting. A flask web application that pulls images from a database. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last. Photo Gallery Hacker101.
From www.cnblogs.com
【hacker101 CTF】Photo Gallery yokan 博客园 Photo Gallery Hacker101 This is a web challenge. A flask web application that pulls images from a database. As usual we get a link to webpage, it seems to be an image gallery, but one of the images is broken. So i started off with go buster but didn't find anything interesting. Ctf, the first two challenges are relatively trivial so i’ll overview. Photo Gallery Hacker101.
From www.youtube.com
CTF in Hacking How to get started into Capture the Flag Hacker101 Photo Gallery Hacker101 A flask web application that pulls images from a database. As usual we get a link to webpage, it seems to be an image gallery, but one of the images is broken. The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. My solution to the hacker101 image gallery challenge. Consider how you. Photo Gallery Hacker101.
From medium.com
Hacker101 CTF — Photo Gallery — 3/3 FLAGS (Español) by gus Medium Photo Gallery Hacker101 In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. This is a web challenge. This is the next challenge from hacker101 ctf after encrypted pastebin. So i started off with go buster but didn't find anything interesting. My solution to the hacker101 image gallery challenge. Consider how you might build this system yourself. This is. Photo Gallery Hacker101.
From www.youtube.com
Hacker101 CTF Photo Gallery () Flag1 YouTube Photo Gallery Hacker101 Consider how you might build this system yourself. This is a web challenge. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last flag. Ctf — hacker101 — photo gallery. So i started off with go buster but didn't find anything interesting. This is the next challenge from hacker101. Photo Gallery Hacker101.
From hackerone.com
Hacker101 for Hackers Photo Gallery Hacker101 This is a web challenge. This is the next challenge from hacker101 ctf after encrypted pastebin. Ctf — hacker101 — photo gallery. Consider how you might build this system yourself. A flask web application that pulls images from a database. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the. Photo Gallery Hacker101.
From medium.com
Hacker101 CTF — Photo Gallery — 3/3 FLAGS (Español) by gus Medium Photo Gallery Hacker101 So i started off with go buster but didn't find anything interesting. The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. Consider how you might build this system yourself. My solution to the hacker101 image gallery challenge. As usual we get a link to webpage, it seems to be an image gallery,. Photo Gallery Hacker101.
From hacker101.testerting.science
Photo Gallery FLAG0 hacker101ctf Photo Gallery Hacker101 So i started off with go buster but didn't find anything interesting. The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. As usual we get a link to webpage, it seems to be an image gallery, but one. Photo Gallery Hacker101.
From medium.com
Hacker101 CTF — Photo Gallery — 3/3 FLAGS (Español) by gus Medium Photo Gallery Hacker101 This is my write up for the photo gallery challenge of hackerone's ctf. So i started off with go buster but didn't find anything interesting. A flask web application that pulls images from a database. This is the next challenge from hacker101 ctf after encrypted pastebin. My solution to the hacker101 image gallery challenge. As usual we get a link. Photo Gallery Hacker101.
From www.youtube.com
Hacker101 CTF Photo Gallery All Levels Completed Capture The Flag Photo Gallery Hacker101 In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. Consider how you might build this system yourself. A flask web application that pulls images from a database. This is a web challenge. As usual we get a link. Photo Gallery Hacker101.
From d0rksec.github.io
Hacker101 Photo Gallery d0rksec Photo Gallery Hacker101 This is my write up for the photo gallery challenge of hackerone's ctf. In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. This is a web challenge. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last flag. My solution to the hacker101 image. Photo Gallery Hacker101.
From d0rksec.github.io
Hacker101 Photo Gallery d0rksec Photo Gallery Hacker101 As usual we get a link to webpage, it seems to be an image gallery, but one of the images is broken. This is my write up for the photo gallery challenge of hackerone's ctf. A flask web application that pulls images from a database. So i started off with go buster but didn't find anything interesting. In this video,. Photo Gallery Hacker101.
From www.youtube.com
hacker101 ctf magical Photo Gallery flag1 YouTube Photo Gallery Hacker101 The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. Ctf — hacker101 — photo gallery. This is a web challenge. This is my write up for the photo gallery challenge of hackerone's ctf. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on. Photo Gallery Hacker101.
From blog.csdn.net
【hacker101 CTF】Photo Gallery_ctf photo galleryCSDN博客 Photo Gallery Hacker101 Ctf — hacker101 — photo gallery. In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. So i started off with go buster but didn't find anything interesting. A flask web application that pulls images from a database. My solution to the hacker101 image gallery challenge. The application is vulnerable to multiple sql injections, which range. Photo Gallery Hacker101.
From www.hacker101.com
Home Hacker101 Photo Gallery Hacker101 My solution to the hacker101 image gallery challenge. In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. So i started off with go buster but didn't find anything interesting. The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. Ctf, the first two challenges are relatively trivial so. Photo Gallery Hacker101.
From www.secjuice.com
Hacker 101 CTF Photo Gallery Photo Gallery Hacker101 Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last flag. This is a web challenge. This is the next challenge from hacker101 ctf after encrypted pastebin. In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. This is my write up for the photo. Photo Gallery Hacker101.
From blog.csdn.net
【hacker101 CTF】Photo Gallery_ctf photo galleryCSDN博客 Photo Gallery Hacker101 So i started off with go buster but didn't find anything interesting. Consider how you might build this system yourself. Ctf — hacker101 — photo gallery. This is a web challenge. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last flag. My solution to the hacker101 image gallery. Photo Gallery Hacker101.
From www.youtube.com
[Hacker101] Photo Gallery Flag 2 YouTube Photo Gallery Hacker101 The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. A flask web application that pulls images from a database. Consider how you might build this system yourself. This is my write up for the photo gallery challenge of hackerone's ctf. This is the next challenge from hacker101 ctf after encrypted pastebin. Ctf,. Photo Gallery Hacker101.
From www.youtube.com
Hacker101 CTF Photo Gallery (Medium) Live Walkthrough YouTube Photo Gallery Hacker101 So i started off with go buster but didn't find anything interesting. This is the next challenge from hacker101 ctf after encrypted pastebin. Ctf — hacker101 — photo gallery. As usual we get a link to webpage, it seems to be an image gallery, but one of the images is broken. This is a web challenge. The application is vulnerable. Photo Gallery Hacker101.
From www.producthunt.com
Hacker101 Product Information, Latest Updates, and Reviews 2024 Photo Gallery Hacker101 This is a web challenge. This is the next challenge from hacker101 ctf after encrypted pastebin. Consider how you might build this system yourself. My solution to the hacker101 image gallery challenge. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last flag. Ctf — hacker101 — photo gallery.. Photo Gallery Hacker101.
From blog.csdn.net
【hacker101 CTF】Photo Gallery_ctf photo galleryCSDN博客 Photo Gallery Hacker101 The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. A flask web application that pulls images from a database. In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. As usual we get a link to webpage, it seems to be an image gallery, but one of the. Photo Gallery Hacker101.
From medium.com
Hacker101 CTF — Photo Gallery — 3/3 FLAGS (Español) by gus Medium Photo Gallery Hacker101 The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. A flask web application that pulls images from a database. This is a web challenge. This is the next challenge from hacker101 ctf after encrypted pastebin. Ctf — hacker101. Photo Gallery Hacker101.
From www.youtube.com
Playing with SQLMap and Solving Hacker101's "Photo Gallery" CTF Level Photo Gallery Hacker101 Ctf — hacker101 — photo gallery. The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last flag. This is my write up for the photo gallery challenge of hackerone's ctf. This is. Photo Gallery Hacker101.
From medium.com
Hacker101 CTF — Photo Gallery — 3/3 FLAGS (Español) by gus Medium Photo Gallery Hacker101 The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last flag. This is the next challenge from hacker101 ctf after encrypted pastebin. This is a web challenge. Consider how you might build. Photo Gallery Hacker101.
From www.youtube.com
[Hacker101 CTF] A little something to get you started Solution YouTube Photo Gallery Hacker101 The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. As usual we get a link to webpage, it seems to be an image gallery, but one of the images is broken. Ctf, the first two challenges are relatively. Photo Gallery Hacker101.
From d0rksec.github.io
Hacker101 Photo Gallery d0rksec Photo Gallery Hacker101 Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last flag. A flask web application that pulls images from a database. As usual we get a link to webpage, it seems to be an image gallery, but one of the images is broken. So i started off with go. Photo Gallery Hacker101.
From www.youtube.com
[Hacker101] Photo Gallery Flag 1 YouTube Photo Gallery Hacker101 Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i want to focus on the last flag. Ctf — hacker101 — photo gallery. The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. This is the next challenge from hacker101 ctf after encrypted pastebin. Consider how you might. Photo Gallery Hacker101.
From www.youtube.com
Hacker101 Photo Gallery CTF All Flags Detailed Solution Flag 0 Photo Gallery Hacker101 In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. Ctf — hacker101 — photo gallery. My solution to the hacker101 image gallery challenge. The application is vulnerable to multiple sql injections, which range from information disclosure to remote code execution. Ctf, the first two challenges are relatively trivial so i’ll overview their solutions but i. Photo Gallery Hacker101.
From www.youtube.com
[Hacker101] Photo Gallery Flag 3 YouTube Photo Gallery Hacker101 This is the next challenge from hacker101 ctf after encrypted pastebin. This is a web challenge. In this video, tib3rius (mostly) solves the medium rated photo gallery challenge from hacker101. As usual we get a link to webpage, it seems to be an image gallery, but one of the images is broken. Consider how you might build this system yourself.. Photo Gallery Hacker101.