Network Solutions Email Mfa . While signing in, you are. We would like to show you a description here but the site won’t allow us. One of the reasons why biometric authentication hasn’t taken off. This verification method works as follows: In the menu bar, click the settings icon. Use a security key that you connect with your computer via usb or wirelessly. Log in to your network solutions® account manager. You have the following options: How to manage verification methods or verification devices: Set up verification methods as soon as having set up an initial verification method, you have to set a recovery. On the left side of the page, click email. Now biometric recognition is just one of many mfa methods used in authentication. Depending on the configuration, you can increase the security when logging in by using an additional authentication that is executed after the usual. On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then.
from miniorange.com
We would like to show you a description here but the site won’t allow us. On the left side of the page, click email. You have the following options: Set up verification methods as soon as having set up an initial verification method, you have to set a recovery. Now biometric recognition is just one of many mfa methods used in authentication. Log in to your network solutions® account manager. Depending on the configuration, you can increase the security when logging in by using an additional authentication that is executed after the usual. One of the reasons why biometric authentication hasn’t taken off. How to manage verification methods or verification devices: While signing in, you are.
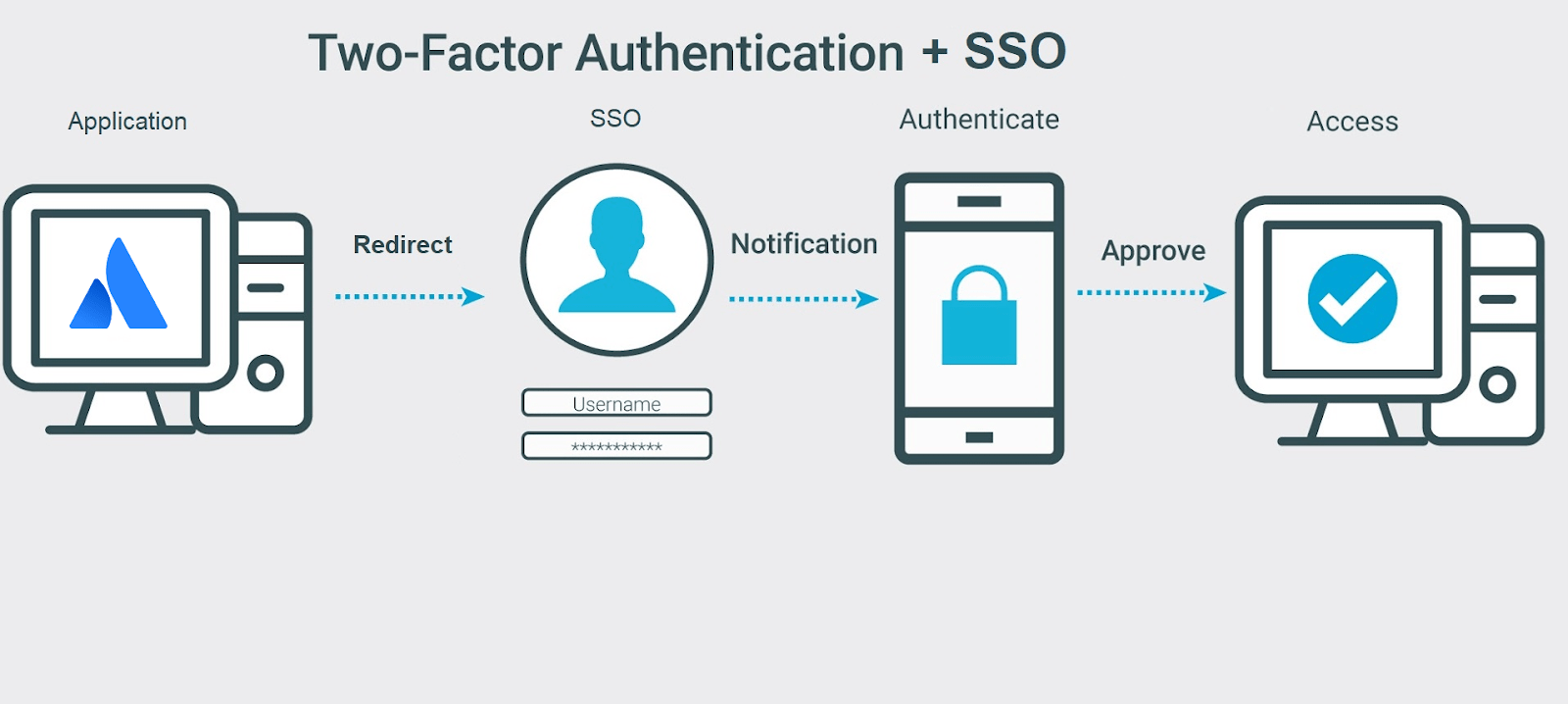
Two Factor Authentication (2FA/MFA) for Atlassian Applications
Network Solutions Email Mfa Set up verification methods as soon as having set up an initial verification method, you have to set a recovery. Set up verification methods as soon as having set up an initial verification method, you have to set a recovery. Log in to your network solutions® account manager. While signing in, you are. This verification method works as follows: We would like to show you a description here but the site won’t allow us. Now biometric recognition is just one of many mfa methods used in authentication. In the menu bar, click the settings icon. On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then. You have the following options: How to manage verification methods or verification devices: One of the reasons why biometric authentication hasn’t taken off. Depending on the configuration, you can increase the security when logging in by using an additional authentication that is executed after the usual. On the left side of the page, click email. Use a security key that you connect with your computer via usb or wirelessly.
From www.akamai.com
What Are MultiFactor Authentication (MFA) Solutions? Akamai Network Solutions Email Mfa You have the following options: How to manage verification methods or verification devices: This verification method works as follows: One of the reasons why biometric authentication hasn’t taken off. Now biometric recognition is just one of many mfa methods used in authentication. On the left side of the page, click email. Use a security key that you connect with your. Network Solutions Email Mfa.
From gogeekz.com
5 Multi Factor Authentication Benefits Maximize Security Network Solutions Email Mfa While signing in, you are. On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then. Now biometric recognition is just one of many mfa methods used in authentication. Log in to your network solutions® account manager. In the menu bar, click the settings icon. This verification method works as follows: You have the. Network Solutions Email Mfa.
From www.macmister.com
How do I Migrate my Network Solutions Email to Office 365? Network Solutions Email Mfa Depending on the configuration, you can increase the security when logging in by using an additional authentication that is executed after the usual. Now biometric recognition is just one of many mfa methods used in authentication. This verification method works as follows: In the menu bar, click the settings icon. How to manage verification methods or verification devices: Set up. Network Solutions Email Mfa.
From www.scribd.com
Network Solutions mail Guide PDF Application Icon Network Solutions Email Mfa In the menu bar, click the settings icon. One of the reasons why biometric authentication hasn’t taken off. How to manage verification methods or verification devices: You have the following options: This verification method works as follows: Now biometric recognition is just one of many mfa methods used in authentication. Depending on the configuration, you can increase the security when. Network Solutions Email Mfa.
From xtraxtor.com
How to Add Network Solutions Email to Outlook? Network Solutions Email Mfa On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then. We would like to show you a description here but the site won’t allow us. Use a security key that you connect with your computer via usb or wirelessly. You have the following options: While signing in, you are. On the left side. Network Solutions Email Mfa.
From www.macmister.com
How do I Migrate my Network Solutions Email to Office 365? Network Solutions Email Mfa Log in to your network solutions® account manager. We would like to show you a description here but the site won’t allow us. Use a security key that you connect with your computer via usb or wirelessly. On the left side of the page, click email. On the mailbox list page, click the vertical ellipsis on the mailbox you wanted. Network Solutions Email Mfa.
From www.youtube.com
Network Solutions Email Email Recovery Email Restore Email Backup Network Solutions Email Mfa This verification method works as follows: Use a security key that you connect with your computer via usb or wirelessly. On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then. In the menu bar, click the settings icon. Log in to your network solutions® account manager. You have the following options: Depending on. Network Solutions Email Mfa.
From www.adviksoft.com
How to Migrate Network Solutions Email to Office 365? Network Solutions Email Mfa On the left side of the page, click email. You have the following options: This verification method works as follows: One of the reasons why biometric authentication hasn’t taken off. While signing in, you are. Use a security key that you connect with your computer via usb or wirelessly. Now biometric recognition is just one of many mfa methods used. Network Solutions Email Mfa.
From andy89.hashnode.dev
9 Best Practices for Multifactor Authentication (MFA) Network Solutions Email Mfa Now biometric recognition is just one of many mfa methods used in authentication. While signing in, you are. You have the following options: In the menu bar, click the settings icon. One of the reasons why biometric authentication hasn’t taken off. Set up verification methods as soon as having set up an initial verification method, you have to set a. Network Solutions Email Mfa.
From xtraxtor.com
How to Transfer Network Solutions Email to Gmail with Attachments? Network Solutions Email Mfa How to manage verification methods or verification devices: Now biometric recognition is just one of many mfa methods used in authentication. Depending on the configuration, you can increase the security when logging in by using an additional authentication that is executed after the usual. On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access,. Network Solutions Email Mfa.
From www.toptut.com
How To Login Network Solutions mail? Network Solutions Email Mfa On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then. Now biometric recognition is just one of many mfa methods used in authentication. We would like to show you a description here but the site won’t allow us. While signing in, you are. Set up verification methods as soon as having set up. Network Solutions Email Mfa.
From store.cuanswers.com
Network MFA Product categories CU*Answers Store Network Solutions Email Mfa Now biometric recognition is just one of many mfa methods used in authentication. This verification method works as follows: You have the following options: In the menu bar, click the settings icon. While signing in, you are. How to manage verification methods or verification devices: Set up verification methods as soon as having set up an initial verification method, you. Network Solutions Email Mfa.
From customerservice.networksolutions.com
How Do I Access My Email? Network Solutions Support Network Solutions Email Mfa Now biometric recognition is just one of many mfa methods used in authentication. One of the reasons why biometric authentication hasn’t taken off. In the menu bar, click the settings icon. How to manage verification methods or verification devices: Set up verification methods as soon as having set up an initial verification method, you have to set a recovery. Use. Network Solutions Email Mfa.
From www.networksolutions.com
Guide for Transferring Domain Names to Network Solutions Network Network Solutions Email Mfa On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then. On the left side of the page, click email. While signing in, you are. You have the following options: One of the reasons why biometric authentication hasn’t taken off. Set up verification methods as soon as having set up an initial verification method,. Network Solutions Email Mfa.
From www.logintc.com
F5 MultiFactor Authentication (MFA) LoginTC Network Solutions Email Mfa One of the reasons why biometric authentication hasn’t taken off. Now biometric recognition is just one of many mfa methods used in authentication. Use a security key that you connect with your computer via usb or wirelessly. You have the following options: How to manage verification methods or verification devices: This verification method works as follows: Set up verification methods. Network Solutions Email Mfa.
From escapecreative.io
How to Setup Network Solutions Email Forwarding Network Solutions Email Mfa We would like to show you a description here but the site won’t allow us. Depending on the configuration, you can increase the security when logging in by using an additional authentication that is executed after the usual. On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then. While signing in, you are.. Network Solutions Email Mfa.
From customerservice.networksolutions.com
How to Create and Manage a Mailbox Network Solutions Support Network Solutions Email Mfa While signing in, you are. Now biometric recognition is just one of many mfa methods used in authentication. We would like to show you a description here but the site won’t allow us. One of the reasons why biometric authentication hasn’t taken off. Use a security key that you connect with your computer via usb or wirelessly. On the mailbox. Network Solutions Email Mfa.
From www.macmister.com
How do I Migrate my Network Solutions Email to Office 365? Network Solutions Email Mfa Use a security key that you connect with your computer via usb or wirelessly. How to manage verification methods or verification devices: This verification method works as follows: In the menu bar, click the settings icon. While signing in, you are. Now biometric recognition is just one of many mfa methods used in authentication. Log in to your network solutions®. Network Solutions Email Mfa.
From www.progreso.com.sg
MultiFactor Authentication (MFA) Progreso Networks & Security Network Solutions Email Mfa In the menu bar, click the settings icon. Now biometric recognition is just one of many mfa methods used in authentication. How to manage verification methods or verification devices: Log in to your network solutions® account manager. You have the following options: Use a security key that you connect with your computer via usb or wirelessly. On the mailbox list. Network Solutions Email Mfa.
From www.adviksoft.com
How to Add Network Solutions Email to Outlook? Network Solutions Email Mfa On the left side of the page, click email. We would like to show you a description here but the site won’t allow us. Now biometric recognition is just one of many mfa methods used in authentication. In the menu bar, click the settings icon. Depending on the configuration, you can increase the security when logging in by using an. Network Solutions Email Mfa.
From www.avaren.com
Multi Factor Authentication (MFA/2FA) Solutions Dallas/Fort Worth Network Solutions Email Mfa How to manage verification methods or verification devices: Use a security key that you connect with your computer via usb or wirelessly. You have the following options: Depending on the configuration, you can increase the security when logging in by using an additional authentication that is executed after the usual. Now biometric recognition is just one of many mfa methods. Network Solutions Email Mfa.
From www.cloudpartner.fi
Azure MFA Extensions and Network Policy Server SetAzApp name Network Solutions Email Mfa You have the following options: On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then. In the menu bar, click the settings icon. This verification method works as follows: Now biometric recognition is just one of many mfa methods used in authentication. Set up verification methods as soon as having set up an. Network Solutions Email Mfa.
From www.thenetworkdna.com
Top 5 MultiFactor Authentication (MFA) solutions in 2024 The Network DNA Network Solutions Email Mfa In the menu bar, click the settings icon. Log in to your network solutions® account manager. While signing in, you are. We would like to show you a description here but the site won’t allow us. Use a security key that you connect with your computer via usb or wirelessly. On the left side of the page, click email. You. Network Solutions Email Mfa.
From www.secict.com
MFA Exploring Duo and Other Prominent Provider Secure ICT Solutions Network Solutions Email Mfa In the menu bar, click the settings icon. Use a security key that you connect with your computer via usb or wirelessly. Set up verification methods as soon as having set up an initial verification method, you have to set a recovery. We would like to show you a description here but the site won’t allow us. One of the. Network Solutions Email Mfa.
From miniorange.com
Two Factor Authentication (2FA/MFA) for Atlassian Applications Network Solutions Email Mfa This verification method works as follows: Use a security key that you connect with your computer via usb or wirelessly. Set up verification methods as soon as having set up an initial verification method, you have to set a recovery. On the left side of the page, click email. We would like to show you a description here but the. Network Solutions Email Mfa.
From modern-networks.co.uk
The benefits of MultiFactor Authentication (MFA) Modern Networks Network Solutions Email Mfa On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then. Depending on the configuration, you can increase the security when logging in by using an additional authentication that is executed after the usual. We would like to show you a description here but the site won’t allow us. While signing in, you are.. Network Solutions Email Mfa.
From www.researchgate.net
MFA implementation with azure and cisco. NPS, network policy server Network Solutions Email Mfa We would like to show you a description here but the site won’t allow us. While signing in, you are. This verification method works as follows: Set up verification methods as soon as having set up an initial verification method, you have to set a recovery. Use a security key that you connect with your computer via usb or wirelessly.. Network Solutions Email Mfa.
From www.paloaltonetworks.in
Why MultiFactor Authentication Should be at the Root of Your Security Network Solutions Email Mfa You have the following options: While signing in, you are. On the left side of the page, click email. We would like to show you a description here but the site won’t allow us. This verification method works as follows: One of the reasons why biometric authentication hasn’t taken off. Now biometric recognition is just one of many mfa methods. Network Solutions Email Mfa.
From www.adviksoft.com
How to Add Network Solutions Email to Outlook? Network Solutions Email Mfa While signing in, you are. This verification method works as follows: One of the reasons why biometric authentication hasn’t taken off. Use a security key that you connect with your computer via usb or wirelessly. Set up verification methods as soon as having set up an initial verification method, you have to set a recovery. On the mailbox list page,. Network Solutions Email Mfa.
From www.youtube.com
Network Solutions Email Setup Email Client Setup IMAP Windows Mail Network Solutions Email Mfa Now biometric recognition is just one of many mfa methods used in authentication. We would like to show you a description here but the site won’t allow us. This verification method works as follows: Log in to your network solutions® account manager. On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then. In. Network Solutions Email Mfa.
From www.adviksoft.com
How to Migrate Network Solutions to Gmail Account? Network Solutions Email Mfa In the menu bar, click the settings icon. On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then. Now biometric recognition is just one of many mfa methods used in authentication. While signing in, you are. This verification method works as follows: Log in to your network solutions® account manager. How to manage. Network Solutions Email Mfa.
From corbettsoftware.com
Best Methods to Add Network Solutions Email to Outlook Corbett Blog Network Solutions Email Mfa One of the reasons why biometric authentication hasn’t taken off. We would like to show you a description here but the site won’t allow us. On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then. Log in to your network solutions® account manager. In the menu bar, click the settings icon. You have. Network Solutions Email Mfa.
From xtraxtor.com
How to Migrate Email from Network Solutions to Office 365? Network Solutions Email Mfa On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then. You have the following options: In the menu bar, click the settings icon. This verification method works as follows: We would like to show you a description here but the site won’t allow us. Set up verification methods as soon as having set. Network Solutions Email Mfa.
From www.pei.com
MultiFactor Authentication Features with Office 365 and Azure PEI Network Solutions Email Mfa How to manage verification methods or verification devices: Depending on the configuration, you can increase the security when logging in by using an additional authentication that is executed after the usual. One of the reasons why biometric authentication hasn’t taken off. Use a security key that you connect with your computer via usb or wirelessly. While signing in, you are.. Network Solutions Email Mfa.
From community.cisco.com
Network Access and Segmentation with DUO MFA and ISE Configuration Network Solutions Email Mfa In the menu bar, click the settings icon. On the mailbox list page, click the vertical ellipsis on the mailbox you wanted to access, then. This verification method works as follows: Set up verification methods as soon as having set up an initial verification method, you have to set a recovery. You have the following options: How to manage verification. Network Solutions Email Mfa.