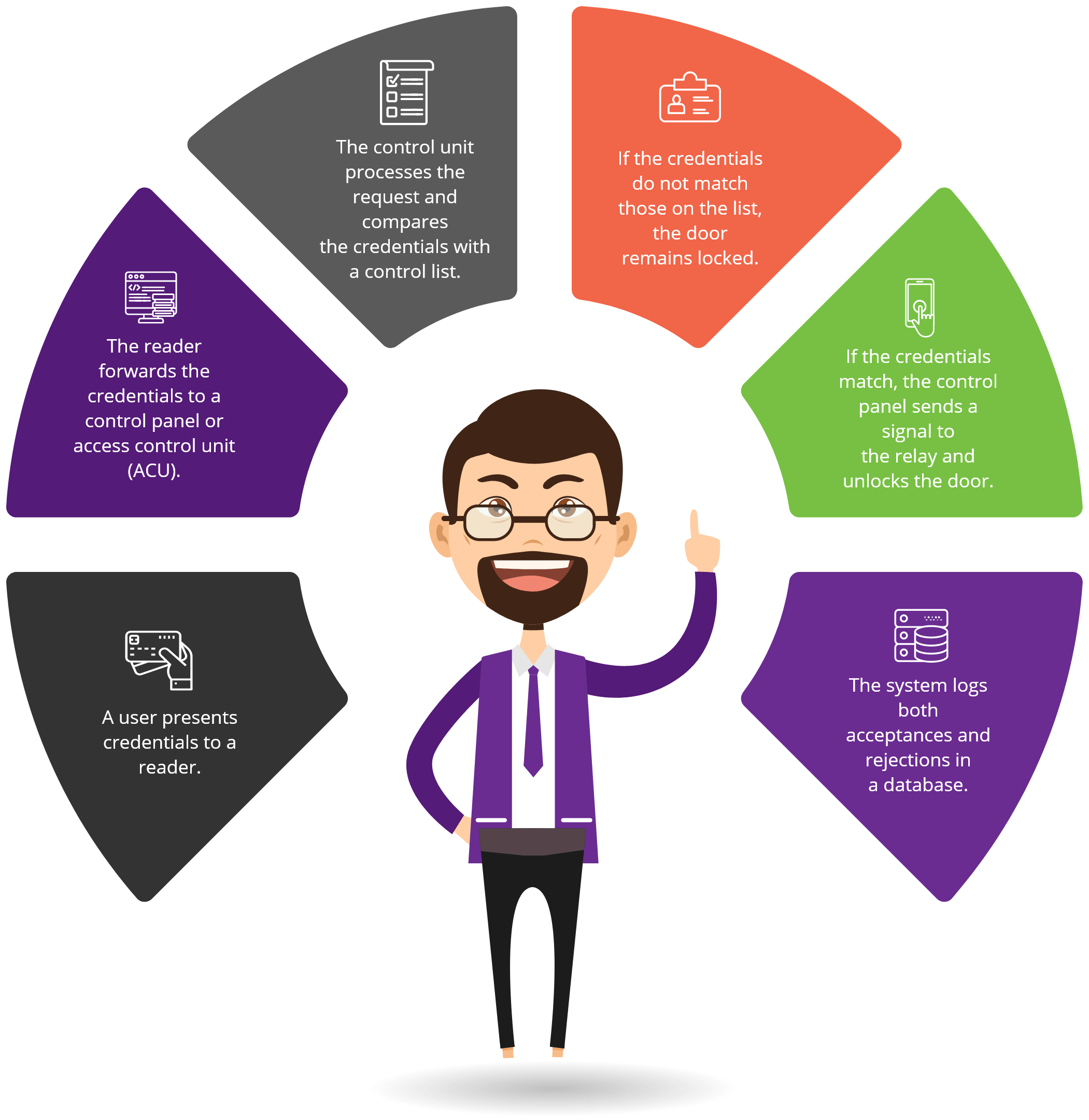
Access Control To Source Code . Control access to source code in line with published procedures. Iso 27001 8.4 access to source code requirement explanation: Assess your code use and code requirements and perform a risk assessment. Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. This includes conducting regular assessments of access. Limiting user access to your source code is crucial to prevent unauthorized modifications and leaks. Have policies and procedures in place. In order to thoroughly protect program source code, it is necessary to control access to it. How to comply with iso 27001 annex a 8.4. Write, approve, implement and communicate the documentation required for access to source code. Implementing authentication and authorization mechanisms to ensure that only authorised individuals can access the source. Provide read and/or write access to source code in conjunction with a set of clearly defined business requirements. This can be accomplished through various means, such as user. For each code type perform a risk assessment. Access to development tools should only be given to personnel who are part of.
from www.vrogue.co
Iso 27001 8.4 access to source code requirement explanation: This can be accomplished through various means, such as user. How to comply with iso 27001 annex a 8.4. Access to development tools should only be given to personnel who are part of. Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. Control access to source code in line with published procedures. In order to thoroughly protect program source code, it is necessary to control access to it. Implementing authentication and authorization mechanisms to ensure that only authorised individuals can access the source. Have policies and procedures in place. For each code type perform a risk assessment.
Types Of Access Control System Infographics Access Control System Vrogue
Access Control To Source Code Assess your code use and code requirements and perform a risk assessment. Implementing authentication and authorization mechanisms to ensure that only authorised individuals can access the source. Have policies and procedures in place. Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. Control access to source code in line with published procedures. How to comply with iso 27001 annex a 8.4. For each code type perform a risk assessment. Access to development tools should only be given to personnel who are part of. Iso 27001 8.4 access to source code requirement explanation: Provide read and/or write access to source code in conjunction with a set of clearly defined business requirements. Assess your code use and code requirements and perform a risk assessment. This includes conducting regular assessments of access. In order to thoroughly protect program source code, it is necessary to control access to it. Write, approve, implement and communicate the documentation required for access to source code. This can be accomplished through various means, such as user. Limiting user access to your source code is crucial to prevent unauthorized modifications and leaks.
From www.devopsschool.com
Top 5 Open Source Code Management tools Access Control To Source Code In order to thoroughly protect program source code, it is necessary to control access to it. Access to development tools should only be given to personnel who are part of. For each code type perform a risk assessment. Provide read and/or write access to source code in conjunction with a set of clearly defined business requirements. Iso 27001 8.4 access. Access Control To Source Code.
From viettuans.vn
Network Access Control là gì? Ứng dụng thực tiễn của Network Access Co Access Control To Source Code How to comply with iso 27001 annex a 8.4. Limiting user access to your source code is crucial to prevent unauthorized modifications and leaks. For each code type perform a risk assessment. Assess your code use and code requirements and perform a risk assessment. This can be accomplished through various means, such as user. Iso 27001 8.4 access to source. Access Control To Source Code.
From www.secureye.com
Access Control System Need Security for Every Organization Secureye Access Control To Source Code For each code type perform a risk assessment. Write, approve, implement and communicate the documentation required for access to source code. This can be accomplished through various means, such as user. Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. In order to thoroughly protect program source code, it is necessary to control. Access Control To Source Code.
From stackdiary.com
AccessControlRequestMethod HTTP Access Control To Source Code Control access to source code in line with published procedures. How to comply with iso 27001 annex a 8.4. Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. For each code type perform a risk assessment. Iso 27001 8.4 access to source code requirement explanation: Assess your code use and code requirements and. Access Control To Source Code.
From www.arnica.io
[arnica] Automated Developer Access Management Access Control To Source Code Write, approve, implement and communicate the documentation required for access to source code. Assess your code use and code requirements and perform a risk assessment. Access to development tools should only be given to personnel who are part of. Control access to source code in line with published procedures. This can be accomplished through various means, such as user. Section. Access Control To Source Code.
From www.vrogue.co
Types Of Access Control System Infographics Access Control System Vrogue Access Control To Source Code Access to development tools should only be given to personnel who are part of. Limiting user access to your source code is crucial to prevent unauthorized modifications and leaks. Control access to source code in line with published procedures. Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. In order to thoroughly protect. Access Control To Source Code.
From www.splunk.com
Source Code Management An Introduction Splunk Access Control To Source Code Control access to source code in line with published procedures. Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. Iso 27001 8.4 access to source code requirement explanation: For each code type perform a risk assessment. Implementing authentication and authorization mechanisms to ensure that only authorised individuals can access the source. Provide read. Access Control To Source Code.
From software-solutions-online.com
Access Using Expressions (Calculated Fields) In Form Controls VBA and Access Control To Source Code Implementing authentication and authorization mechanisms to ensure that only authorised individuals can access the source. Access to development tools should only be given to personnel who are part of. Provide read and/or write access to source code in conjunction with a set of clearly defined business requirements. Iso 27001 8.4 access to source code requirement explanation: Section 8.3 of iso. Access Control To Source Code.
From kintronics.com
Access Control Installation Kintronics Access Control To Source Code Limiting user access to your source code is crucial to prevent unauthorized modifications and leaks. Provide read and/or write access to source code in conjunction with a set of clearly defined business requirements. Implementing authentication and authorization mechanisms to ensure that only authorised individuals can access the source. For each code type perform a risk assessment. This includes conducting regular. Access Control To Source Code.
From www.linkedin.com
Role Based Access Control ( RBAC ) Access Control To Source Code Control access to source code in line with published procedures. Assess your code use and code requirements and perform a risk assessment. Access to development tools should only be given to personnel who are part of. For each code type perform a risk assessment. Iso 27001 8.4 access to source code requirement explanation: Section 8.3 of iso 27001 outlines the. Access Control To Source Code.
From 9to5answer.com
[Solved] AMP Access Control Allow Source Origin header 9to5Answer Access Control To Source Code How to comply with iso 27001 annex a 8.4. This includes conducting regular assessments of access. In order to thoroughly protect program source code, it is necessary to control access to it. Provide read and/or write access to source code in conjunction with a set of clearly defined business requirements. Write, approve, implement and communicate the documentation required for access. Access Control To Source Code.
From www.cdvi.co.uk
What is access control? Access control explained CDVI UK Access Control To Source Code Access to development tools should only be given to personnel who are part of. This includes conducting regular assessments of access. Iso 27001 8.4 access to source code requirement explanation: This can be accomplished through various means, such as user. Limiting user access to your source code is crucial to prevent unauthorized modifications and leaks. Control access to source code. Access Control To Source Code.
From www.lumenci.com
Access Control Mechanisms Blog Posts Lumenci Access Control To Source Code Control access to source code in line with published procedures. Limiting user access to your source code is crucial to prevent unauthorized modifications and leaks. Assess your code use and code requirements and perform a risk assessment. Provide read and/or write access to source code in conjunction with a set of clearly defined business requirements. In order to thoroughly protect. Access Control To Source Code.
From catalog.securityceu.com
What are the 3 types of access control? Access Control To Source Code Provide read and/or write access to source code in conjunction with a set of clearly defined business requirements. Have policies and procedures in place. Implementing authentication and authorization mechanisms to ensure that only authorised individuals can access the source. Assess your code use and code requirements and perform a risk assessment. Iso 27001 8.4 access to source code requirement explanation:. Access Control To Source Code.
From securitypatterns.io
How to Write A Security Pattern Source Code Management Access Control To Source Code For each code type perform a risk assessment. This includes conducting regular assessments of access. Control access to source code in line with published procedures. Assess your code use and code requirements and perform a risk assessment. This can be accomplished through various means, such as user. Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access. Access Control To Source Code.
From www.securitybooster.net
Access to source code Security Booster Access Control To Source Code Assess your code use and code requirements and perform a risk assessment. Access to development tools should only be given to personnel who are part of. Write, approve, implement and communicate the documentation required for access to source code. Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. For each code type perform. Access Control To Source Code.
From medium.com
Authentication Controls. An access control system is the set of… by Access Control To Source Code Implementing authentication and authorization mechanisms to ensure that only authorised individuals can access the source. Iso 27001 8.4 access to source code requirement explanation: Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. Assess your code use and code requirements and perform a risk assessment. Write, approve, implement and communicate the documentation required. Access Control To Source Code.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 Access Control To Source Code How to comply with iso 27001 annex a 8.4. Write, approve, implement and communicate the documentation required for access to source code. Provide read and/or write access to source code in conjunction with a set of clearly defined business requirements. Limiting user access to your source code is crucial to prevent unauthorized modifications and leaks. Control access to source code. Access Control To Source Code.
From www.customguide.com
Change a Controls Data Source CustomGuide Access Control To Source Code This can be accomplished through various means, such as user. How to comply with iso 27001 annex a 8.4. This includes conducting regular assessments of access. For each code type perform a risk assessment. In order to thoroughly protect program source code, it is necessary to control access to it. Write, approve, implement and communicate the documentation required for access. Access Control To Source Code.
From www.springboard.com
How To an Information Security Analyst [9 Step Guide] Access Control To Source Code This can be accomplished through various means, such as user. For each code type perform a risk assessment. Control access to source code in line with published procedures. Write, approve, implement and communicate the documentation required for access to source code. Limiting user access to your source code is crucial to prevent unauthorized modifications and leaks. Implementing authentication and authorization. Access Control To Source Code.
From www.bankinfosecurity.com
NIST Guide Aims to Ease Access Control BankInfoSecurity Access Control To Source Code For each code type perform a risk assessment. Have policies and procedures in place. Assess your code use and code requirements and perform a risk assessment. Limiting user access to your source code is crucial to prevent unauthorized modifications and leaks. Iso 27001 8.4 access to source code requirement explanation: Access to development tools should only be given to personnel. Access Control To Source Code.
From www.youtube.com
Source Control Tip 7 Staging commits in VS Code YouTube Access Control To Source Code Implementing authentication and authorization mechanisms to ensure that only authorised individuals can access the source. Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. Provide read and/or write access to source code in conjunction with a set of clearly defined business requirements. Limiting user access to your source code is crucial to prevent. Access Control To Source Code.
From gmetrix.freshdesk.com
How to Modify an Access Code Technical Support Access Control To Source Code This can be accomplished through various means, such as user. This includes conducting regular assessments of access. Assess your code use and code requirements and perform a risk assessment. Access to development tools should only be given to personnel who are part of. Control access to source code in line with published procedures. Section 8.3 of iso 27001 outlines the. Access Control To Source Code.
From www.permit.io
What Is AttributeBased Access Control (ABAC)? Permit Access Control To Source Code How to comply with iso 27001 annex a 8.4. Control access to source code in line with published procedures. This can be accomplished through various means, such as user. Have policies and procedures in place. This includes conducting regular assessments of access. Provide read and/or write access to source code in conjunction with a set of clearly defined business requirements.. Access Control To Source Code.
From www.sourcecodester.com
Patient's Record using MS Access Database Free source code, tutorials Access Control To Source Code In order to thoroughly protect program source code, it is necessary to control access to it. This includes conducting regular assessments of access. Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. Access to development tools should only be given to personnel who are part of. Write, approve, implement and communicate the documentation. Access Control To Source Code.
From www.techtarget.com
What is Access Control? Access Control To Source Code Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. How to comply with iso 27001 annex a 8.4. Access to development tools should only be given to personnel who are part of. Have policies and procedures in place. In order to thoroughly protect program source code, it is necessary to control access to. Access Control To Source Code.
From www.electronicsforu.com
Access Control System Installation Wiring & Working Full Guide Access Control To Source Code This can be accomplished through various means, such as user. Assess your code use and code requirements and perform a risk assessment. In order to thoroughly protect program source code, it is necessary to control access to it. Control access to source code in line with published procedures. Access to development tools should only be given to personnel who are. Access Control To Source Code.
From code.visualstudio.com
Source Control API Visual Studio Code Extension API Access Control To Source Code This includes conducting regular assessments of access. In order to thoroughly protect program source code, it is necessary to control access to it. Control access to source code in line with published procedures. Provide read and/or write access to source code in conjunction with a set of clearly defined business requirements. How to comply with iso 27001 annex a 8.4.. Access Control To Source Code.
From www.resmo.com
9 Access Control Best Practices Resmo Access Control To Source Code How to comply with iso 27001 annex a 8.4. For each code type perform a risk assessment. Limiting user access to your source code is crucial to prevent unauthorized modifications and leaks. Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. Control access to source code in line with published procedures. In order. Access Control To Source Code.
From www.youtube.com
How to Program an Access Control Keypad and Troubleshooting Access Control To Source Code This includes conducting regular assessments of access. Write, approve, implement and communicate the documentation required for access to source code. Control access to source code in line with published procedures. In order to thoroughly protect program source code, it is necessary to control access to it. Assess your code use and code requirements and perform a risk assessment. Section 8.3. Access Control To Source Code.
From garantir.io
KeyBased Authentication Using Cryptographic Access Controls Garantir Access Control To Source Code This can be accomplished through various means, such as user. Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. Access to development tools should only be given to personnel who are part of. Provide read and/or write access to source code in conjunction with a set of clearly defined business requirements. In order. Access Control To Source Code.
From help.educationperfect.com
How do I create access codes for my classes? Education Perfect Access Control To Source Code Write, approve, implement and communicate the documentation required for access to source code. Control access to source code in line with published procedures. Iso 27001 8.4 access to source code requirement explanation: This includes conducting regular assessments of access. Access to development tools should only be given to personnel who are part of. In order to thoroughly protect program source. Access Control To Source Code.
From mgiaccess.com
Access Control System 2023 A Guide from Basics to Advanced Techniques Access Control To Source Code Have policies and procedures in place. This includes conducting regular assessments of access. This can be accomplished through various means, such as user. How to comply with iso 27001 annex a 8.4. Limiting user access to your source code is crucial to prevent unauthorized modifications and leaks. Access to development tools should only be given to personnel who are part. Access Control To Source Code.
From software-solutions-online.com
Access Forms, Fields From Multiple Tables VBA and Tutorials Access Control To Source Code Access to development tools should only be given to personnel who are part of. Write, approve, implement and communicate the documentation required for access to source code. Control access to source code in line with published procedures. Section 8.3 of iso 27001 outlines the requirements for identifying and controlling access to source code. Have policies and procedures in place. This. Access Control To Source Code.
From www.securiwiser.com
Understanding Data Access Control What it is and How it Works Access Control To Source Code Assess your code use and code requirements and perform a risk assessment. Provide read and/or write access to source code in conjunction with a set of clearly defined business requirements. Write, approve, implement and communicate the documentation required for access to source code. For each code type perform a risk assessment. Section 8.3 of iso 27001 outlines the requirements for. Access Control To Source Code.