Security Monitoring Guidelines . • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a cyber. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous monitoring. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support.
from purplesec.us
• bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a cyber. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support. By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous monitoring. Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the.
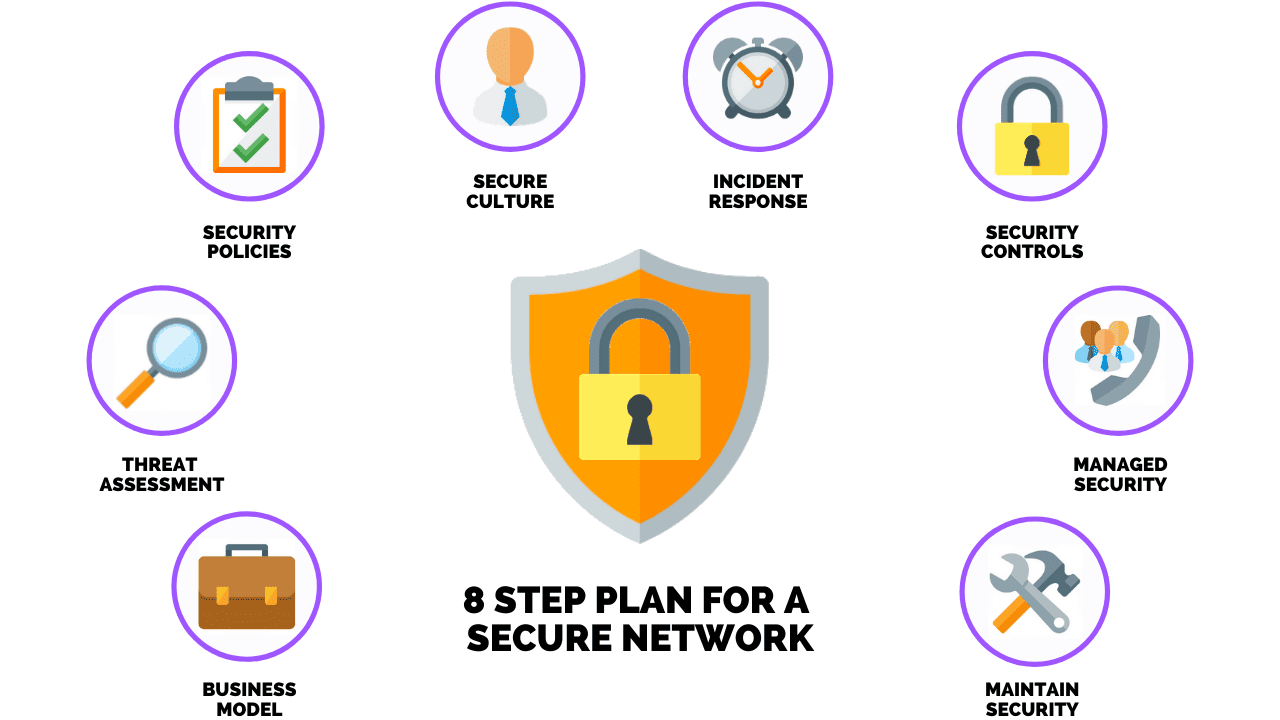
How To Develop & Implement A Network Security Plan
Security Monitoring Guidelines • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a cyber. By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous monitoring. Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a cyber. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support.
From industrialcyber.co
Cybersecurity Practices for Industrial Control Systems Industrial Cyber Security Monitoring Guidelines Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. Continuous security monitoring. Security Monitoring Guidelines.
From spaal.com.au
Alarm Installation & Monitoring Agreement Guidelines Security Security Monitoring Guidelines Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support. By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous monitoring. • bring all aspects of cyber security monitoring and logging together in one framework • gain. Security Monitoring Guidelines.
From www.safepaas.com
MonitorPaaS Continuous Controls Monitoring SafePaaS Security Monitoring Guidelines Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. Continuous security monitoring. Security Monitoring Guidelines.
From www.slideteam.net
Hotel Safety And Security Guidelines With Boxes And Arrows PowerPoint Security Monitoring Guidelines The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support. • bring all aspects of cyber security monitoring and logging together in one framework • gain senior. Security Monitoring Guidelines.
From www.esds.co.in
How to Prevent Data Breaches with Cyber security monitoring services? Security Monitoring Guidelines • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a cyber. Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous. Security Monitoring Guidelines.
From spaal.com.au
Alarm Installation & Monitoring Agreement Guidelines Security Security Monitoring Guidelines By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous monitoring. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. • bring. Security Monitoring Guidelines.
From www.slideteam.net
Dashboard For Cyber Security Real Time Monitoring Presentation Security Monitoring Guidelines • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a cyber. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support. The guide introduces the fundamentals of ongoing monitoring of information security in support of. Security Monitoring Guidelines.
From www.degruyter.com
Implementation of network information security monitoring system based Security Monitoring Guidelines The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support. Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with. Security Monitoring Guidelines.
From lkrllc.com
How Alarm Monitoring Works [INFOGRAPHIC] Security Monitoring Guidelines By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous monitoring. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management,. Security Monitoring Guidelines.
From www.reflectiz.com
The Complete List of Data Security Standards Reflectiz Security Monitoring Guidelines The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. Continuous security monitoring. Security Monitoring Guidelines.
From www.cyres-consulting.com
Learn about cybersecurity monitoring and event evaluation Security Monitoring Guidelines The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with. Security Monitoring Guidelines.
From www.en-standard.eu
BS ISO/IEC 270072020 Information security, cybersecurity and privacy Security Monitoring Guidelines Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous monitoring. • bring. Security Monitoring Guidelines.
From www.readkong.com
Information security management guidelines Australian Government Security Monitoring Guidelines The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support. • bring all aspects of cyber security monitoring and logging together in one framework • gain senior. Security Monitoring Guidelines.
From www.detectx.com.au
NIST CSF vs ISO 27001/2 vs NIST 80053 vs SCF DETECTX Cloud Security Monitoring Guidelines By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous monitoring. • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a cyber. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and. Security Monitoring Guidelines.
From www.comptia.org
Complete Guide to IT Risk Management CompTIA Security Monitoring Guidelines Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. • bring all aspects of cyber security monitoring and logging together in one framework • gain senior. Security Monitoring Guidelines.
From xmcyber.com
Continuous Control Monitoring (CCM) XM Cyber Security Monitoring Guidelines • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a cyber. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and. Security Monitoring Guidelines.
From www.yokogawa.com
Cybersecurity Policies & Procedures Yokogawa Electric Corporation Security Monitoring Guidelines • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a cyber. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the.. Security Monitoring Guidelines.
From www.quality-assurance-solutions.com
Computer Protection Security Guidelines Security Monitoring Guidelines • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a cyber. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and. Security Monitoring Guidelines.
From www.3pillarglobal.com
Industrial of Things (IIoT) Cybersecurity 3Pillar Global Security Monitoring Guidelines The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. By integrating security. Security Monitoring Guidelines.
From issuu.com
ISMSDOCA063 Information Security Guidelines for Project Management Security Monitoring Guidelines Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a cyber.. Security Monitoring Guidelines.
From gca.isa.org
Excerpt 2 Industrial Cybersecurity Case Studies and Best Practices Security Monitoring Guidelines The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats. Security Monitoring Guidelines.
From ptp.cloud
SOAR based Security Monitoring PTP Cloud Experts Biotech Enablers Security Monitoring Guidelines Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support. • bring all aspects of cyber security monitoring and logging together in one framework • gain senior. Security Monitoring Guidelines.
From www.smartsheet.com
Free Cybersecurity Risk Assessment Templates Smartsheet Security Monitoring Guidelines The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous monitoring. • bring. Security Monitoring Guidelines.
From www.virtualmetric.com
Network Security Monitoring Essential Guide VirtualMetric Security Monitoring Guidelines The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats. Security Monitoring Guidelines.
From www.iahss.org
Security Design Guidelines for Healthcare Facilities 3rd Edition Security Monitoring Guidelines • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a cyber. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and. Security Monitoring Guidelines.
From atriade.com
Best Practices for Secure Method of Facility Monitoring Facility Security Security Monitoring Guidelines The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous monitoring. • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a. Security Monitoring Guidelines.
From secureframe.com
6 Benefits of Continuous Monitoring for Cybersecurity Security Monitoring Guidelines The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous monitoring. Continuous security. Security Monitoring Guidelines.
From purplesec.us
How To Develop & Implement A Network Security Plan Security Monitoring Guidelines Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support. Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with. Security Monitoring Guidelines.
From medium.com
Cyber Security Monitoring and Management Best Practices by Delta IT Security Monitoring Guidelines • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a cyber. Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and. Security Monitoring Guidelines.
From www.arcweb.com
Continuous ICS Security Monitoring Needed ARC Advisory Security Monitoring Guidelines • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a cyber. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous. Security Monitoring Guidelines.
From cybersecurity.yale.edu
Yale's Minimum Security Standards (MSS) Security Monitoring Guidelines Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats. Security Monitoring Guidelines.
From www.esds.co.in
How to Prevent Data Breaches with Cyber security monitoring services? Security Monitoring Guidelines Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous monitoring. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. Continuous security. Security Monitoring Guidelines.
From 24-7-home-security.com
Understand How Home Alarm Monitoring Works and Alarm Response Times in Security Monitoring Guidelines By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous monitoring. Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. The guide introduces the fundamentals of ongoing monitoring of information security in support of risk management, with discussion of. • bring. Security Monitoring Guidelines.
From www.ftq360.com
Electronic Surveillance Inspection Checklist FTQ360 Security Monitoring Guidelines Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls, vulnerabilities, and other cyber threats to support. By integrating security testing into the devsecops model, your organization can put in place the basis of. Security Monitoring Guidelines.
From gut.bmj.com
Surveillance guidelines after removal of colorectal adenomatous polyps Security Monitoring Guidelines Implement a holistic monitoring strategy that relies on modern threat detection mechanisms that can be integrated with the platform. By integrating security testing into the devsecops model, your organization can put in place the basis of a continuous monitoring. • bring all aspects of cyber security monitoring and logging together in one framework • gain senior management support for a. Security Monitoring Guidelines.