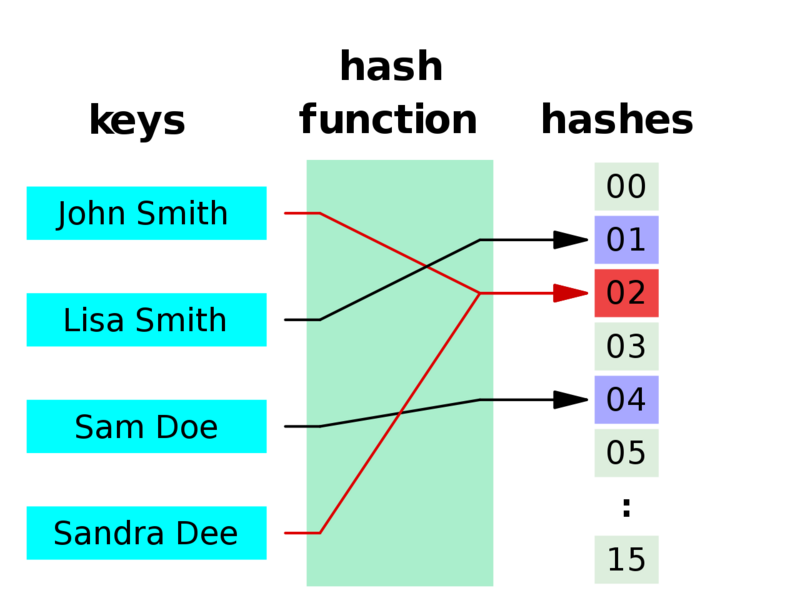
Define String Hash . Next, we introduced a hash table data structure. Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. then, we presented several examples of cryptographic attacks. the good and widely used way to define the hash of a string s of length n is. hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size.
from www.ritchievink.com
this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: the good and widely used way to define the hash of a string s of length n is. Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. Next, we introduced a hash table data structure. then, we presented several examples of cryptographic attacks. hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size.
Sparse neural networks and hash tables with Locality Sensitive Hashing Ritchie Vink
Define String Hash this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: the good and widely used way to define the hash of a string s of length n is. hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: Next, we introduced a hash table data structure. a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. then, we presented several examples of cryptographic attacks.
From coderworld109.blogspot.com
Basics of Hash Tables hash data structure cook the code Define String Hash Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. the good and widely used way to define the hash of a string s of length n is. Next, we introduced a hash table data structure. hashing is the practice of transforming a given key or string of characters into another. Define String Hash.
From datagy.io
Python SHA256 Hashing Algorithm Explained • datagy Define String Hash Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. the good and widely used way to define the hash of a string s of length n is. hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Next, we. Define String Hash.
From courses.cs.washington.edu
Making the String Hash Define String Hash Next, we introduced a hash table data structure. hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. a cryptographic hash function (chf) is a hash algorithm (a map of. Define String Hash.
From blog.kobros-tech.com
Simple hash function and hash table algorithm with an example of application for strings Define String Hash a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. Next, we introduced a hash table data structure. the good and widely used way to define the hash of a string s of length n is. this is a simple algorithm which takes. Define String Hash.
From www.slideserve.com
PPT Chapter 11 Hash Tables PowerPoint Presentation, free download ID371554 Define String Hash then, we presented several examples of cryptographic attacks. Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: the good and widely used way to define the. Define String Hash.
From programming.vip
Detailed explanation of string Hash example CF961F/CF985F Define String Hash this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. then, we presented several examples of cryptographic attacks. Hash (s). Define String Hash.
From www.chegg.com
Solved Suppose we were to define a hash code on strings s Define String Hash then, we presented several examples of cryptographic attacks. a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Next, we introduced a. Define String Hash.
From www.ritchievink.com
Sparse neural networks and hash tables with Locality Sensitive Hashing Ritchie Vink Define String Hash the good and widely used way to define the hash of a string s of length n is. then, we presented several examples of cryptographic attacks. a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. Next, we introduced a hash table data. Define String Hash.
From www.codingninjas.com
Hash Function in Data Structure Coding Ninjas Define String Hash a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. the good and widely used way to define the hash of a string s of length n is. then, we presented several examples of cryptographic attacks. hashing is the practice of transforming. Define String Hash.
From laptrinhx.com
How to implement a simple hash table in JavaScript LaptrinhX Define String Hash the good and widely used way to define the hash of a string s of length n is. Next, we introduced a hash table data structure. this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: Hash (s) = s [0] + s [1] ⋅. Define String Hash.
From www.ssla.co.uk
What is hash function? And how does it work ssla.co.uk Define String Hash then, we presented several examples of cryptographic attacks. a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: the. Define String Hash.
From www.ionos.ca
Hash functions definition, usage, and examples IONOS CA Define String Hash Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. Next, we introduced a hash table data structure. this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: hashing is the practice of transforming a given key or. Define String Hash.
From slideplayer.com
CS 5243 Algorithms Hash Tables. ppt download Define String Hash then, we presented several examples of cryptographic attacks. a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. Next, we introduced a hash table data structure. . Define String Hash.
From www.youtube.com
Hash Tables A Simple Introduction YouTube Define String Hash the good and widely used way to define the hash of a string s of length n is. then, we presented several examples of cryptographic attacks. Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. this is a simple algorithm which takes into account byte order of each byte. Define String Hash.
From www.saksenengku.com
Apa itu Hashing? Cara kerja, Jenis, dan Pengaplikasiannya Saksenengku Network Define String Hash this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: the good and widely used way to define the hash of a string s of length n is. hashing is the practice of transforming a given key or string of characters into another value. Define String Hash.
From www.slideserve.com
PPT Maps and hashing PowerPoint Presentation, free download ID3518086 Define String Hash hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. the good and widely used way to define the hash of a string s of length n is. this is a simple algorithm which takes into account byte order of each byte in the string by. Define String Hash.
From www.ionos.ca
Hash functions definition, usage, and examples IONOS CA Define String Hash the good and widely used way to define the hash of a string s of length n is. this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: then, we presented several examples of cryptographic attacks. Next, we introduced a hash table data structure.. Define String Hash.
From slidetodoc.com
Hash Table 88621159 Data Structures and Algorithms 22561 Define String Hash a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. Next, we introduced a hash table data structure. then, we presented several examples of cryptographic attacks. the good and widely used way to define the hash of a string s of length n. Define String Hash.
From www.youtube.com
Python hash() Function A Simple Guide with Example YouTube Define String Hash hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. the good and widely used way to define the hash of a string s of length n is. Next, we introduced a hash table data structure. a cryptographic hash function (chf) is a hash algorithm (a. Define String Hash.
From www.chegg.com
7 If we define a hash function (or compression Define String Hash hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. the good and widely used way to define the hash of a string s of length n is. this is a simple algorithm which takes into account byte order of each byte in the string by. Define String Hash.
From codeahoy.com
Hash Functions CodeAhoy Define String Hash the good and widely used way to define the hash of a string s of length n is. hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. then, we presented several examples of cryptographic attacks. Hash (s) = s [0] + s [1] ⋅ p. Define String Hash.
From www.linuxscrew.com
Generate a Hash from String in Javascript, with Examples Define String Hash Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. Next, we introduced a hash table data structure. then, we presented several examples of cryptographic attacks. hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. the good and. Define String Hash.
From en.wikipedia.org
Hash table Wikipedia Define String Hash a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. then, we presented several examples of cryptographic attacks. hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. the good and. Define String Hash.
From pythonarray.com
Hashing Strings with Python Python Array Define String Hash this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. a cryptographic hash function (chf) is a hash algorithm (a map of an. Define String Hash.
From forums.ni.com
String hash to define unique filenames NI Community Define String Hash this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: the good and widely used way to define the hash of a string s of length n is. a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string. Define String Hash.
From www.slideserve.com
PPT Maps and hashing PowerPoint Presentation, free download ID3518086 Define String Hash a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. the good and widely used way to define the hash of a string s of length n is. this is a simple algorithm which takes into account byte order of each byte in. Define String Hash.
From www.youtube.com
Hash Tables Explained in Simple Terms YouTube Define String Hash hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Next, we introduced a hash table data structure. Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. the good and widely used way to define the hash of a. Define String Hash.
From exovzfhjc.blob.core.windows.net
Hash Types Examples at Lela Neal blog Define String Hash Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. Next, we introduced a hash table data structure. the good and widely used way to define the hash of a string s of length n is. hashing is the practice of transforming a given key or string of characters into another. Define String Hash.
From courses.cs.washington.edu
Good Hash Function for Strings? Define String Hash this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. the good and widely used way to define the hash of a string. Define String Hash.
From www.thesslstore.com
What Is a Hash Function in Cryptography? A Beginner’s Guide Hashed Out by The SSL Store™ Define String Hash a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. the good and widely used way to define the hash of a string s of length n is. this is a simple algorithm which takes into account byte order of each byte in. Define String Hash.
From www.slideserve.com
PPT Hashing PowerPoint Presentation, free download ID8895974 Define String Hash then, we presented several examples of cryptographic attacks. a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. Next, we introduced a hash table data structure. . Define String Hash.
From blog.evosec.fr
The Difference Between Hashing and Encryption Define String Hash this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: Next, we introduced a hash table data structure. Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. a cryptographic hash function (chf) is a hash algorithm (a. Define String Hash.
From www.slideserve.com
PPT Introduction to Hashing Hash Functions PowerPoint Presentation ID4175840 Define String Hash a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. then, we presented several examples of cryptographic attacks. this is a simple algorithm which takes into account byte order of each byte in the string by doing this style of algorithm: Hash (s). Define String Hash.
From velog.io
Hash Table Define String Hash hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. a cryptographic hash function (chf) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size. then, we presented several examples of cryptographic attacks. the good and. Define String Hash.
From exovzfhjc.blob.core.windows.net
Hash Types Examples at Lela Neal blog Define String Hash hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Hash (s) = s [0] + s [1] ⋅ p + s [2] ⋅ p 2 +. the good and widely used way to define the hash of a string s of length n is. this. Define String Hash.