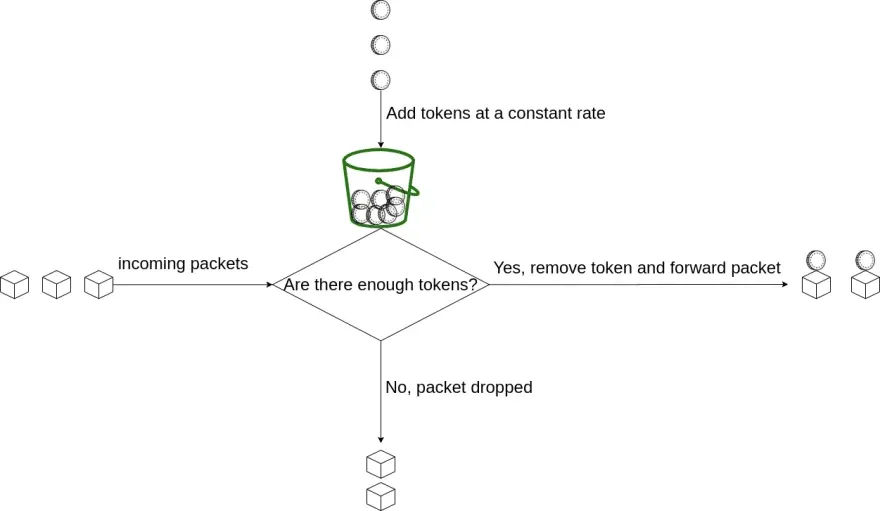
Leaky Bucket And Token Bucket Javatpoint . This will ensure that the water coming out is at some fixed rate, and also if the bucket gets full, then we will stop pouring water into it. Step 1 − let us imagine a. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and system. Token bucket ensures predictable traffic shaping as it allows for setting. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. 82 likes • 157,023 views. Suppose we have a bucket in which we are pouring water, at random points in time, but we have to get water at a fixed rate, to achieve this we will make a hole at the bottom of the bucket. Leaky bucket and token bucket. The leaky bucket algorithm enforces output patterns at the average rate, no matter how busy the traffic is. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. They help manage the rate of traffic flow in a network, but they do so in. The leaky bucket and token bucket are two algorithms used for rate limiting. They have different behaviors and use cases. Jan 25, 2014 • download as pptx, pdf •.
from botpenguin.com
Suppose we have a bucket in which we are pouring water, at random points in time, but we have to get water at a fixed rate, to achieve this we will make a hole at the bottom of the bucket. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. They help manage the rate of traffic flow in a network, but they do so in. Step 1 − let us imagine a. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket ensures predictable traffic shaping as it allows for setting. They have different behaviors and use cases. 82 likes • 157,023 views. The leaky bucket and token bucket are two algorithms used for rate limiting. This will ensure that the water coming out is at some fixed rate, and also if the bucket gets full, then we will stop pouring water into it.
What is Leaky Bucket Theory & its Applications?
Leaky Bucket And Token Bucket Javatpoint The leaky bucket algorithm enforces output patterns at the average rate, no matter how busy the traffic is. This will ensure that the water coming out is at some fixed rate, and also if the bucket gets full, then we will stop pouring water into it. They help manage the rate of traffic flow in a network, but they do so in. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and system. 82 likes • 157,023 views. They have different behaviors and use cases. Leaky bucket and token bucket. Jan 25, 2014 • download as pptx, pdf •. The leaky bucket and token bucket are two algorithms used for rate limiting. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. The leaky bucket algorithm enforces output patterns at the average rate, no matter how busy the traffic is. Suppose we have a bucket in which we are pouring water, at random points in time, but we have to get water at a fixed rate, to achieve this we will make a hole at the bottom of the bucket. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Step 1 − let us imagine a. Token bucket ensures predictable traffic shaping as it allows for setting.
From www.youtube.com
Leaky Bucket Algorithm YouTube Leaky Bucket And Token Bucket Javatpoint Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and system. 82 likes • 157,023 views. Leaky bucket and token bucket. The leaky bucket and token bucket are two algorithms used for rate limiting. Step 1 − let us imagine a. They help manage the rate of traffic flow in a. Leaky Bucket And Token Bucket Javatpoint.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID9128423 Leaky Bucket And Token Bucket Javatpoint Token bucket ensures predictable traffic shaping as it allows for setting. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and system. They help manage the rate of traffic flow in a network, but they do so in. Token bucket and leaky bucket are two algorithms used for network traffic shaping. Leaky Bucket And Token Bucket Javatpoint.
From www.studocu.com
Difference between token bucket and leaky bucket What is the Leaky Bucket And Token Bucket Javatpoint 82 likes • 157,023 views. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Jan 25, 2014 • download as pptx, pdf •. The leaky bucket and token bucket are two algorithms used for rate limiting. They help manage the rate of traffic flow in a network, but they do so. Leaky Bucket And Token Bucket Javatpoint.
From www.slideserve.com
PPT Token Bucket Leaky Bucket PowerPoint Presentation, free download Leaky Bucket And Token Bucket Javatpoint They help manage the rate of traffic flow in a network, but they do so in. The leaky bucket and token bucket are two algorithms used for rate limiting. Step 1 − let us imagine a. They have different behaviors and use cases. Suppose we have a bucket in which we are pouring water, at random points in time, but. Leaky Bucket And Token Bucket Javatpoint.
From medium.com
Token Bucket vs Leaky Bucket. Token Bucket and Leaky Bucket are two Leaky Bucket And Token Bucket Javatpoint 82 likes • 157,023 views. Leaky bucket and token bucket. They help manage the rate of traffic flow in a network, but they do so in. The leaky bucket algorithm enforces output patterns at the average rate, no matter how busy the traffic is. This will ensure that the water coming out is at some fixed rate, and also if. Leaky Bucket And Token Bucket Javatpoint.
From www.thetechnicaltalk.com
Differentiate between leaky bucket and token bucket methods of traffic Leaky Bucket And Token Bucket Javatpoint The leaky bucket algorithm enforces output patterns at the average rate, no matter how busy the traffic is. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. They have different behaviors and use cases. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Step. Leaky Bucket And Token Bucket Javatpoint.
From api7.ai
How to Deal with Bursty Traffic Leaky Bucket and Token Bucket Leaky Bucket And Token Bucket Javatpoint Jan 25, 2014 • download as pptx, pdf •. Suppose we have a bucket in which we are pouring water, at random points in time, but we have to get water at a fixed rate, to achieve this we will make a hole at the bottom of the bucket. They have different behaviors and use cases. 82 likes • 157,023. Leaky Bucket And Token Bucket Javatpoint.
From www.slideshare.net
Chap24 Leaky Bucket And Token Bucket Javatpoint Token bucket ensures predictable traffic shaping as it allows for setting. 82 likes • 157,023 views. The leaky bucket and token bucket are two algorithms used for rate limiting. Suppose we have a bucket in which we are pouring water, at random points in time, but we have to get water at a fixed rate, to achieve this we will. Leaky Bucket And Token Bucket Javatpoint.
From www.youtube.com
Leaky Bucket Algorithm Token Bucket Algorithm Leaky Bucket Vs Token Leaky Bucket And Token Bucket Javatpoint The leaky bucket and token bucket are two algorithms used for rate limiting. The leaky bucket algorithm enforces output patterns at the average rate, no matter how busy the traffic is. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Leaky bucket and token bucket. They help manage the rate. Leaky Bucket And Token Bucket Javatpoint.
From www.slideserve.com
PPT Token Bucket Leaky Bucket PowerPoint Presentation, free download Leaky Bucket And Token Bucket Javatpoint Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Jan 25, 2014 • download as pptx, pdf •. The leaky bucket and token bucket are two algorithms used for rate limiting. Suppose we have a bucket in which we are pouring water, at random points in time, but we have to. Leaky Bucket And Token Bucket Javatpoint.
From www.youtube.com
Traffic Shaping Leaky Bucket Token Bucket Improve QoS Computer Leaky Bucket And Token Bucket Javatpoint 82 likes • 157,023 views. Step 1 − let us imagine a. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. They have different behaviors and use cases. They help manage the rate of traffic flow in a network, but they do so in. Token bucket and leaky bucket algorithms are two of. Leaky Bucket And Token Bucket Javatpoint.
From www.youtube.com
Token and Leaky Bucket Algorithm YouTube Leaky Bucket And Token Bucket Javatpoint They have different behaviors and use cases. Leaky bucket and token bucket. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and system. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Jan 25, 2014 • download as pptx, pdf •.. Leaky Bucket And Token Bucket Javatpoint.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket And Token Bucket Javatpoint Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and system. This will ensure that the water coming out is at some fixed rate, and also if the bucket gets full, then we will stop. Leaky Bucket And Token Bucket Javatpoint.
From www.slideserve.com
PPT Token Bucket Leaky Bucket PowerPoint Presentation, free download Leaky Bucket And Token Bucket Javatpoint Leaky bucket and token bucket. 82 likes • 157,023 views. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. The leaky bucket and token bucket are two algorithms used for rate limiting. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. They help manage. Leaky Bucket And Token Bucket Javatpoint.
From www.slideserve.com
PPT ATM CONGESTION CONTROL PowerPoint Presentation, free download Leaky Bucket And Token Bucket Javatpoint Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. This will ensure that the water coming out is at some fixed rate, and also if the bucket gets full, then we will stop pouring water into it. They help manage the rate of traffic flow in a network, but they do so in.. Leaky Bucket And Token Bucket Javatpoint.
From www.slideserve.com
PPT Token Bucket Leaky Bucket PowerPoint Presentation, free download Leaky Bucket And Token Bucket Javatpoint The leaky bucket and token bucket are two algorithms used for rate limiting. Suppose we have a bucket in which we are pouring water, at random points in time, but we have to get water at a fixed rate, to achieve this we will make a hole at the bottom of the bucket. Leaky bucket algorithm mainly controls the total. Leaky Bucket And Token Bucket Javatpoint.
From www.youtube.com
19 Leaky and Token Buckets YouTube Leaky Bucket And Token Bucket Javatpoint The leaky bucket algorithm enforces output patterns at the average rate, no matter how busy the traffic is. 82 likes • 157,023 views. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Token bucket and. Leaky Bucket And Token Bucket Javatpoint.
From designcodesolve.com
Rate Limiting Token and Leaky Bucket Implementation and Explanation Leaky Bucket And Token Bucket Javatpoint Jan 25, 2014 • download as pptx, pdf •. The leaky bucket algorithm enforces output patterns at the average rate, no matter how busy the traffic is. The leaky bucket and token bucket are two algorithms used for rate limiting. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and system.. Leaky Bucket And Token Bucket Javatpoint.
From www.slideserve.com
PPT Token Bucket Leaky Bucket PowerPoint Presentation, free download Leaky Bucket And Token Bucket Javatpoint Suppose we have a bucket in which we are pouring water, at random points in time, but we have to get water at a fixed rate, to achieve this we will make a hole at the bottom of the bucket. They have different behaviors and use cases. Token bucket can send large bursts at a faster rate while leaky bucket. Leaky Bucket And Token Bucket Javatpoint.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and Leaky Bucket And Token Bucket Javatpoint They have different behaviors and use cases. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Suppose we have a bucket in which we are pouring water, at random points in time, but we have to get water at a fixed rate, to achieve this we will make a hole at the bottom. Leaky Bucket And Token Bucket Javatpoint.
From songhayoung.github.io
[System Design] Leaky bucket / token bucket SUMFIのBlog Leaky Bucket And Token Bucket Javatpoint 82 likes • 157,023 views. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. The leaky bucket and token bucket are two algorithms used for rate limiting. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. This will ensure that the. Leaky Bucket And Token Bucket Javatpoint.
From www.youtube.com
Leaky And Token Bucket Algorithms YouTube Leaky Bucket And Token Bucket Javatpoint Step 1 − let us imagine a. Jan 25, 2014 • download as pptx, pdf •. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and system. 82 likes • 157,023 views. Suppose we have a bucket in which we are pouring water, at random points in time, but we have. Leaky Bucket And Token Bucket Javatpoint.
From slidetodoc.com
Token Bucket Leaky Bucket Leaky Bucket a A Leaky Bucket And Token Bucket Javatpoint 82 likes • 157,023 views. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and system. Step 1 − let us imagine a. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Jan 25, 2014 • download as pptx, pdf •. Leaky bucket and. Leaky Bucket And Token Bucket Javatpoint.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket And Token Bucket Javatpoint 82 likes • 157,023 views. Token bucket ensures predictable traffic shaping as it allows for setting. Leaky bucket and token bucket. Suppose we have a bucket in which we are pouring water, at random points in time, but we have to get water at a fixed rate, to achieve this we will make a hole at the bottom of the. Leaky Bucket And Token Bucket Javatpoint.
From www.slideserve.com
PPT Packet Switches with Output and Shared Buffer PowerPoint Leaky Bucket And Token Bucket Javatpoint They help manage the rate of traffic flow in a network, but they do so in. This will ensure that the water coming out is at some fixed rate, and also if the bucket gets full, then we will stop pouring water into it. Token bucket ensures predictable traffic shaping as it allows for setting. Leaky bucket and token bucket.. Leaky Bucket And Token Bucket Javatpoint.
From www.scribd.com
Traffic Shaping Leaky Bucket and Token Bucket PDF Leaky Bucket And Token Bucket Javatpoint 82 likes • 157,023 views. Leaky bucket and token bucket. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and system. The leaky bucket algorithm enforces output patterns at the average rate, no. Leaky Bucket And Token Bucket Javatpoint.
From www.youtube.com
Leaky bucket and Token bucket with GATE PYQs. Clear Explanation YouTube Leaky Bucket And Token Bucket Javatpoint They have different behaviors and use cases. Token bucket ensures predictable traffic shaping as it allows for setting. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. They help manage the rate of traffic flow in a network, but they do so in. The leaky bucket and token bucket are two. Leaky Bucket And Token Bucket Javatpoint.
From gamma.app
Comprendre les techniques Leaky Bucket et Token Bucket Leaky Bucket And Token Bucket Javatpoint Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket ensures predictable traffic shaping as it allows for setting. This will ensure that the water coming out is at some fixed rate, and also if the bucket gets full, then we will stop pouring water into it. Token bucket. Leaky Bucket And Token Bucket Javatpoint.
From www.slideserve.com
PPT Flow Control PowerPoint Presentation, free download ID418287 Leaky Bucket And Token Bucket Javatpoint The leaky bucket and token bucket are two algorithms used for rate limiting. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Jan 25, 2014 • download as pptx, pdf •. Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Token bucket and leaky. Leaky Bucket And Token Bucket Javatpoint.
From www.thetechnicaltalk.com
Differentiate between leaky bucket and token bucket methods of traffic Leaky Bucket And Token Bucket Javatpoint Jan 25, 2014 • download as pptx, pdf •. The leaky bucket and token bucket are two algorithms used for rate limiting. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Suppose we have a bucket in which we are pouring water, at random points in time, but we have to. Leaky Bucket And Token Bucket Javatpoint.
From www.youtube.com
Leaky Bucket vs Token Bucket Algorithm Leaky Bucket and Token Bucket Leaky Bucket And Token Bucket Javatpoint Step 1 − let us imagine a. Leaky bucket and token bucket. This will ensure that the water coming out is at some fixed rate, and also if the bucket gets full, then we will stop pouring water into it. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky. Leaky Bucket And Token Bucket Javatpoint.
From www.youtube.com
Leaky Bucket vs Token Bucket Algorithm Leaky Bucket and Token Bucket Leaky Bucket And Token Bucket Javatpoint Token bucket and leaky bucket are two algorithms used for network traffic shaping and rate limiting. Step 1 − let us imagine a. The leaky bucket and token bucket are two algorithms used for rate limiting. Suppose we have a bucket in which we are pouring water, at random points in time, but we have to get water at a. Leaky Bucket And Token Bucket Javatpoint.
From pdfslide.net
(Download PPT Powerpoint) Token Bucket Leaky Bucket Leaky Bucket And Token Bucket Javatpoint The leaky bucket algorithm enforces output patterns at the average rate, no matter how busy the traffic is. The leaky bucket and token bucket are two algorithms used for rate limiting. Suppose we have a bucket in which we are pouring water, at random points in time, but we have to get water at a fixed rate, to achieve this. Leaky Bucket And Token Bucket Javatpoint.
From medium.com
Implementing Rate Limiting in Java from Scratch — Leaky Bucket and Leaky Bucket And Token Bucket Javatpoint Jan 25, 2014 • download as pptx, pdf •. Leaky bucket and token bucket. Token bucket and leaky bucket algorithms are two of the methods used often in managing the network traffic and system. 82 likes • 157,023 views. The leaky bucket and token bucket are two algorithms used for rate limiting. This will ensure that the water coming out. Leaky Bucket And Token Bucket Javatpoint.
From towardsdev.com
Leaky Bucket vs Token Bucket in Rate Limiting Algorithms by David Lee Leaky Bucket And Token Bucket Javatpoint Token bucket ensures predictable traffic shaping as it allows for setting. 82 likes • 157,023 views. The leaky bucket and token bucket are two algorithms used for rate limiting. Token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Step 1 − let us imagine a. This will ensure that the. Leaky Bucket And Token Bucket Javatpoint.