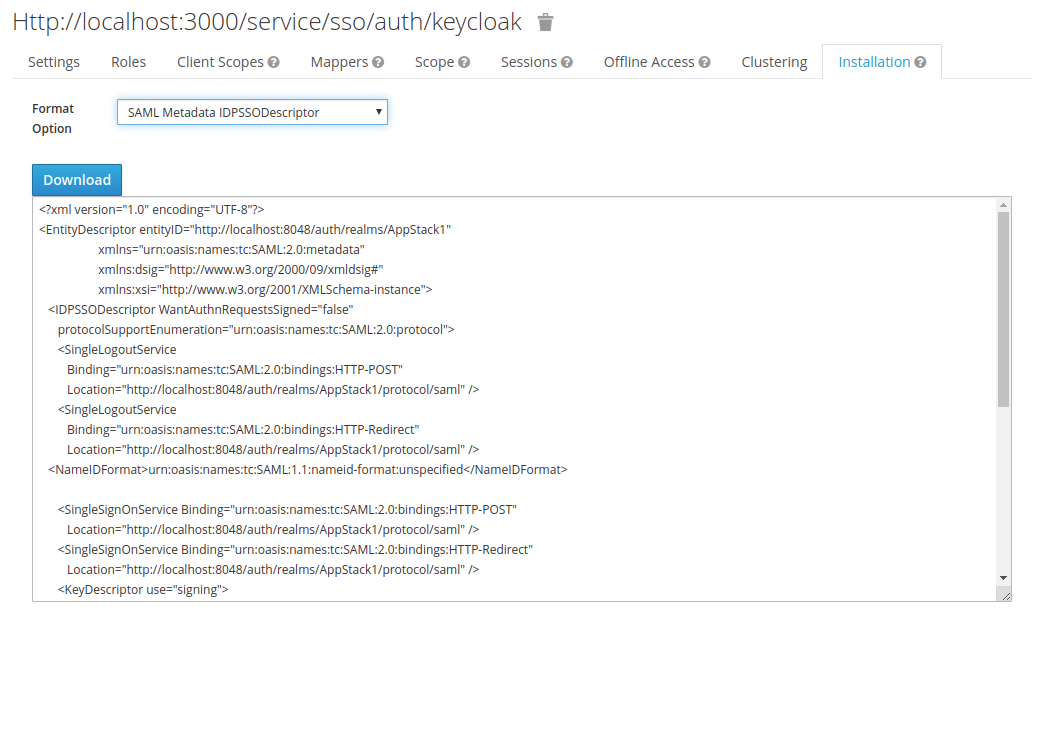
Keycloak Configuration Endpoint . Which protocol, such as saml or openid. Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. It lists endpoints and other configuration options. The application hostname or rest endpoint. In most cases, you do not need to deal with this endpoint directly. Must at least contain openid Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. Where to redirect the user when authentication is ) To use these endpoints with postman, we’ll. We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. Client configuration requires details like this:
from docs.anchore.com
To use these endpoints with postman, we’ll. Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. In most cases, you do not need to deal with this endpoint directly. Which protocol, such as saml or openid. We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. Where to redirect the user when authentication is ) Client configuration requires details like this: It lists endpoints and other configuration options. Must at least contain openid Keycloak exposes a variety of rest endpoints for oauth 2.0 flows.
KeyCloak SAML Example Anchore Enterprise Product Documentation
Keycloak Configuration Endpoint Where to redirect the user when authentication is ) Where to redirect the user when authentication is ) Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. It lists endpoints and other configuration options. Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. The application hostname or rest endpoint. Must at least contain openid In most cases, you do not need to deal with this endpoint directly. We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. Which protocol, such as saml or openid. Client configuration requires details like this: To use these endpoints with postman, we’ll.
From docs.anchore.com
KeyCloak SAML Example Anchore Enterprise Product Documentation Keycloak Configuration Endpoint To use these endpoints with postman, we’ll. Where to redirect the user when authentication is ) Which protocol, such as saml or openid. Must at least contain openid We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. It lists endpoints and other configuration. Keycloak Configuration Endpoint.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Configuration Endpoint Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. The application hostname or rest endpoint. Which protocol, such as saml or openid. Where to redirect the user when authentication is ) To use these endpoints with postman, we’ll. It lists endpoints and other configuration options. Must at least contain openid We are trying to evaluate keycloak as an. Keycloak Configuration Endpoint.
From docs.getunleash.io
How to set up Keycloak and Unleash to sync user groups Unleash Keycloak Configuration Endpoint Where to redirect the user when authentication is ) Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. Which protocol, such as saml or openid. Client configuration requires details like this: In. Keycloak Configuration Endpoint.
From blog.csdn.net
认证和授权系列主题:keycloak界面配置及认证流程详解_keycloak认证流程CSDN博客 Keycloak Configuration Endpoint Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. In most cases, you do not need to deal with this endpoint directly. To use these endpoints with postman, we’ll. Which protocol, such as saml or openid. It lists endpoints and other configuration options. The application hostname or rest endpoint. Where to redirect. Keycloak Configuration Endpoint.
From wiki.resolution.de
Keycloak configuration UserSync Keycloak Configuration Endpoint Must at least contain openid To use these endpoints with postman, we’ll. We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. Client configuration requires details like this: In most cases, you do not need to deal with this endpoint directly. It lists endpoints. Keycloak Configuration Endpoint.
From thainguyen.space
Setting up stepca with Keycloak Keycloak Configuration Endpoint Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. The application hostname or rest endpoint. Client configuration requires details like this: We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. Where to redirect the user. Keycloak Configuration Endpoint.
From github-wiki-see.page
Identity Provider Configuration Keycloak oidcwp/openidconnectgeneric GitHub Wiki Keycloak Configuration Endpoint Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. Where to redirect the user when authentication is ) Must at least contain openid We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. Which protocol, such. Keycloak Configuration Endpoint.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Configuration Endpoint To use these endpoints with postman, we’ll. Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. The application hostname or rest endpoint. Must at least contain openid In most cases, you do not need to deal with this endpoint directly. We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but. Keycloak Configuration Endpoint.
From help.hcltechsw.com
Sample KeyCloak configuration as an OIDC provider for Domino Keycloak Configuration Endpoint Where to redirect the user when authentication is ) Client configuration requires details like this: It lists endpoints and other configuration options. We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. In. Keycloak Configuration Endpoint.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Configuration Endpoint The application hostname or rest endpoint. Where to redirect the user when authentication is ) In most cases, you do not need to deal with this endpoint directly. Client configuration requires details like this: Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. Must at least contain openid Which protocol, such as. Keycloak Configuration Endpoint.
From docs.codeberg.org
Integrating with Keycloak Codeberg Documentation Keycloak Configuration Endpoint Client configuration requires details like this: It lists endpoints and other configuration options. Must at least contain openid Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. To use these endpoints with postman, we’ll. The application hostname or rest endpoint. Which. Keycloak Configuration Endpoint.
From linuxdatahub.com
How to configure keycloak as identity provider and identity broker ? LinuxDataHub Keycloak Configuration Endpoint Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. Must at least contain openid Where to redirect the user when authentication is ) In most cases, you do not need to deal with this endpoint directly. Client configuration requires details like this: The application hostname or rest endpoint. We are trying to evaluate keycloak as an sso solution,. Keycloak Configuration Endpoint.
From supabase.com
Login with Keycloak Supabase Docs Keycloak Configuration Endpoint To use these endpoints with postman, we’ll. Must at least contain openid It lists endpoints and other configuration options. Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. Which protocol, such as saml or openid. Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. The application hostname or rest endpoint.. Keycloak Configuration Endpoint.
From medium.com
Keycloak A real Scenario from Development to Production Keycloak Configuration Endpoint Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. Where to redirect the user when authentication is ) Must at least contain openid Which protocol, such as saml or openid. We are trying to evaluate keycloak as an sso solution, and. Keycloak Configuration Endpoint.
From blog.csdn.net
keycloak界面配置及认证流程详解_keycloak10打开客户端认证CSDN博客 Keycloak Configuration Endpoint We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. To use these endpoints with postman, we’ll. Where to redirect the user when authentication is ) The application hostname or rest endpoint. Must at least contain openid It lists endpoints and other configuration options.. Keycloak Configuration Endpoint.
From docs.getunleash.io
How to set up Keycloak and Unleash to sync user groups Unleash Keycloak Configuration Endpoint In most cases, you do not need to deal with this endpoint directly. Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. Client configuration requires details like this: Where to redirect the user when authentication is ) Which protocol, such as saml or openid. Must at least contain openid To use these. Keycloak Configuration Endpoint.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Configuration Endpoint Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. Client configuration requires details like this: To use these endpoints with postman, we’ll. Keycloak provides a policy enforcer that enables uma for your. Keycloak Configuration Endpoint.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Configuration Endpoint We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. To use these endpoints with postman, we’ll. Where to redirect the user when authentication is ) In. Keycloak Configuration Endpoint.
From blog.pascal-mietlicki.fr
Keycloak configuration et usage PASCAL MIETLICKI Keycloak Configuration Endpoint It lists endpoints and other configuration options. Where to redirect the user when authentication is ) The application hostname or rest endpoint. To use these endpoints with postman, we’ll. Client configuration requires details like this: We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the. Keycloak Configuration Endpoint.
From gauthier-cassany.com
Secure your Spring Boot Rest API with Keycloak Keycloak Configuration Endpoint Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. Where to redirect the user when authentication is ) In most cases, you do not need to deal with this endpoint directly. Must at least contain openid To use these endpoints with postman, we’ll. We are trying to evaluate keycloak as an sso. Keycloak Configuration Endpoint.
From docs.getunleash.io
How to set up Keycloak and Unleash to sync user groups Unleash Keycloak Configuration Endpoint Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. Where to redirect the user when authentication is ) It lists endpoints and other configuration options. Must at least contain openid Which protocol, such as saml or openid. We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is. Keycloak Configuration Endpoint.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Configuration Endpoint The application hostname or rest endpoint. It lists endpoints and other configuration options. Which protocol, such as saml or openid. Where to redirect the user when authentication is ) Must at least contain openid To use these endpoints with postman, we’ll. In most cases, you do not need to deal with this endpoint directly. We are trying to evaluate keycloak. Keycloak Configuration Endpoint.
From janus-idp.io
Enabling Keycloak Authentication in Backstage Janus Keycloak Configuration Endpoint The application hostname or rest endpoint. To use these endpoints with postman, we’ll. It lists endpoints and other configuration options. We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. In most cases, you do not need to deal with this endpoint directly. Where. Keycloak Configuration Endpoint.
From stackoverflow.com
node.js keycloak redirection for different endpoints Stack Overflow Keycloak Configuration Endpoint In most cases, you do not need to deal with this endpoint directly. Client configuration requires details like this: Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. The application hostname or rest endpoint. We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but. Keycloak Configuration Endpoint.
From www.distributedgenomics.ca
Keycloak Our Journey on How to Contribute to the Project Keycloak Configuration Endpoint The application hostname or rest endpoint. Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. Where to redirect the user when authentication is ) Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. Client configuration requires details like this: Which protocol, such as saml or openid. In most cases, you. Keycloak Configuration Endpoint.
From sis-cc.gitlab.io
Keycloak configuration .Stat Suite documentation Keycloak Configuration Endpoint It lists endpoints and other configuration options. Which protocol, such as saml or openid. In most cases, you do not need to deal with this endpoint directly. Where to redirect the user when authentication is ) Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. Keycloak exposes a variety of rest endpoints. Keycloak Configuration Endpoint.
From www.thomasvitale.com
Introducing Keycloak for Identity and Access Management Keycloak Configuration Endpoint Must at least contain openid In most cases, you do not need to deal with this endpoint directly. The application hostname or rest endpoint. Client configuration requires details like this: Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. It lists endpoints and other configuration options. Where to redirect the user when. Keycloak Configuration Endpoint.
From docs.getunleash.io
How to set up Keycloak and Unleash to sync user groups Unleash Keycloak Configuration Endpoint The application hostname or rest endpoint. In most cases, you do not need to deal with this endpoint directly. Where to redirect the user when authentication is ) Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. To use these endpoints. Keycloak Configuration Endpoint.
From www.aimprosoft.com
Liferay SSO Integration with Keycloak Why Do We Need It and How to Configure One? Aimprosoft Keycloak Configuration Endpoint Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. It lists endpoints and other configuration options. Client configuration requires details like this: Must at least contain openid Where to redirect the user when authentication is ) We are trying to evaluate. Keycloak Configuration Endpoint.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Configuration Endpoint To use these endpoints with postman, we’ll. Which protocol, such as saml or openid. In most cases, you do not need to deal with this endpoint directly. Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. Must at least contain openid Client configuration requires details like this: Where to redirect the user. Keycloak Configuration Endpoint.
From docs.getunleash.io
How to set up Keycloak and Unleash to sync user groups Unleash Keycloak Configuration Endpoint It lists endpoints and other configuration options. To use these endpoints with postman, we’ll. Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. Which protocol, such as saml or openid. We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. The application. Keycloak Configuration Endpoint.
From dangibbs.uk
Setting Grafana Roles with Keycloak over OAuth Keycloak Configuration Endpoint The application hostname or rest endpoint. Must at least contain openid Which protocol, such as saml or openid. Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. Where to redirect the user when authentication is ) We are trying to evaluate keycloak as an sso solution, and it looks good in many. Keycloak Configuration Endpoint.
From documentation.wazuh.com
Keycloak Setup single signon with readonly role Keycloak Configuration Endpoint Keycloak provides a policy enforcer that enables uma for your resource server so it can obtain a. In most cases, you do not need to deal with this endpoint directly. Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. Which protocol, such as saml or openid. Must at least contain openid The application hostname or rest endpoint. Where. Keycloak Configuration Endpoint.
From www.baeldung.com
Accessing Keycloak Endpoints Using Postman Baeldung Keycloak Configuration Endpoint Must at least contain openid Which protocol, such as saml or openid. In most cases, you do not need to deal with this endpoint directly. Where to redirect the user when authentication is ) Client configuration requires details like this: We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation. Keycloak Configuration Endpoint.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Configuration Endpoint The application hostname or rest endpoint. We are trying to evaluate keycloak as an sso solution, and it looks good in many respects, but the documentation is painfully lacking in the basics. To use these endpoints with postman, we’ll. Keycloak exposes a variety of rest endpoints for oauth 2.0 flows. Where to redirect the user when authentication is ) Client. Keycloak Configuration Endpoint.