Detect New Open S3 Buckets . So, how do you detect if your s3 bucket has been breached? Sign in to the aws management console and open the. It detects this activity by analyzing aws cloudtrail events for putbucketacl actions where the access control list (acl) grants. Use a scanner to find s3 buckets. Every 20 minutes (or so) you query/scan the dynamo table to see when the latest update is. There is tons of them on github. You can list your bucket by using the amazon s3 console, the aws cli, or the aws sdks. The first step is to monitor your bucket for any suspicious activity. Another solution would be to. A tool to find open s3 buckets and dump their contents 💧. This can be done through aws cloudtrail, which. Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. Can search using a wordlist or by monitoring the certstream network for domain names from. Yet another program to find readable s3 buckets. If you've earned a bug bounty using this tool, please consider donating to support.
from docs.aws.amazon.com
There is tons of them on github. Another solution would be to. Can search using a wordlist or by monitoring the certstream network for domain names from. The first step is to monitor your bucket for any suspicious activity. If you've earned a bug bounty using this tool, please consider donating to support. Sign in to the aws management console and open the. Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. It detects this activity by analyzing aws cloudtrail events for putbucketacl actions where the access control list (acl) grants. Every 20 minutes (or so) you query/scan the dynamo table to see when the latest update is. So, how do you detect if your s3 bucket has been breached?
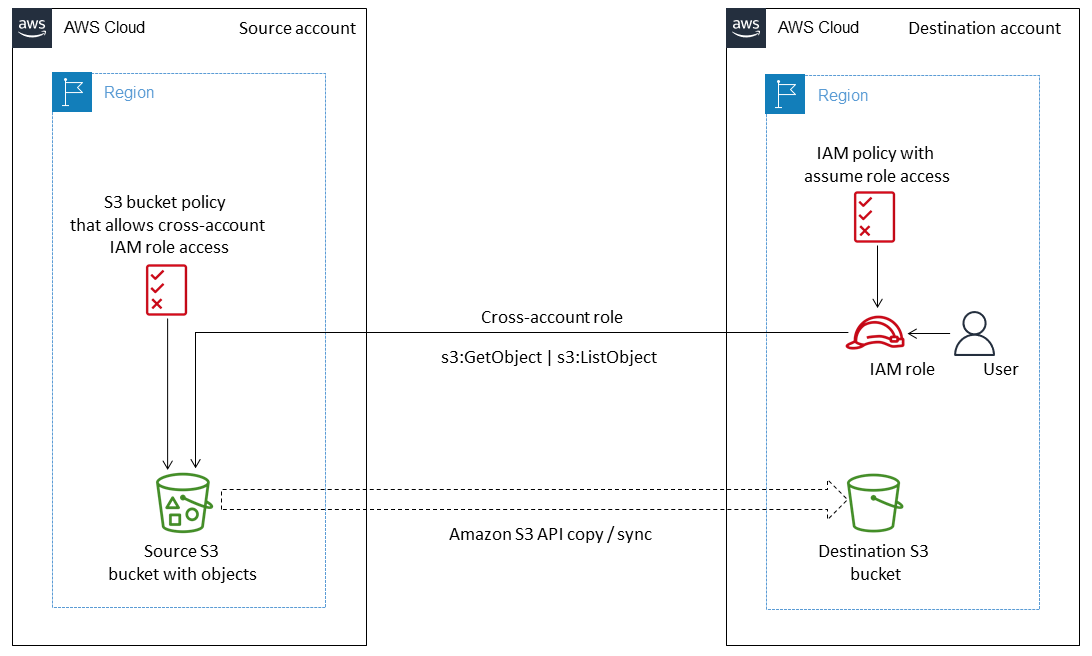
Copy data from an S3 bucket to another account and Region by using the
Detect New Open S3 Buckets There is tons of them on github. Sign in to the aws management console and open the. Every 20 minutes (or so) you query/scan the dynamo table to see when the latest update is. The first step is to monitor your bucket for any suspicious activity. A tool to find open s3 buckets and dump their contents 💧. It detects this activity by analyzing aws cloudtrail events for putbucketacl actions where the access control list (acl) grants. So, how do you detect if your s3 bucket has been breached? Can search using a wordlist or by monitoring the certstream network for domain names from. This can be done through aws cloudtrail, which. Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. If you've earned a bug bounty using this tool, please consider donating to support. Yet another program to find readable s3 buckets. You can list your bucket by using the amazon s3 console, the aws cli, or the aws sdks. Use a scanner to find s3 buckets. Another solution would be to. There is tons of them on github.
From socradar.io
AWS S3 Bucket Takeover Vulnerability Risks, Consequences, and Detection Detect New Open S3 Buckets This can be done through aws cloudtrail, which. Another solution would be to. You can list your bucket by using the amazon s3 console, the aws cli, or the aws sdks. So, how do you detect if your s3 bucket has been breached? Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour.. Detect New Open S3 Buckets.
From blog.checkpoint.com
Automatically Remediate Publicly Exposed S3 Buckets Check Point Software Detect New Open S3 Buckets If you've earned a bug bounty using this tool, please consider donating to support. So, how do you detect if your s3 bucket has been breached? This can be done through aws cloudtrail, which. A tool to find open s3 buckets and dump their contents 💧. Here is an example of a scanner written in ruby by github user nahamsec,. Detect New Open S3 Buckets.
From checkmarx.com
Hijacking S3 Buckets New Attack Technique Detect New Open S3 Buckets The first step is to monitor your bucket for any suspicious activity. Use a scanner to find s3 buckets. There is tons of them on github. Yet another program to find readable s3 buckets. Every 20 minutes (or so) you query/scan the dynamo table to see when the latest update is. It detects this activity by analyzing aws cloudtrail events. Detect New Open S3 Buckets.
From aws.amazon.com
Synchronizing Amazon S3 Buckets Using AWS Step Functions AWS Compute Blog Detect New Open S3 Buckets It detects this activity by analyzing aws cloudtrail events for putbucketacl actions where the access control list (acl) grants. Yet another program to find readable s3 buckets. A tool to find open s3 buckets and dump their contents 💧. Another solution would be to. Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz. Detect New Open S3 Buckets.
From aws.amazon.com
Detect Stripe keys in S3 buckets with Amazon Macie AWS Security Blog Detect New Open S3 Buckets Use a scanner to find s3 buckets. Another solution would be to. A tool to find open s3 buckets and dump their contents 💧. The first step is to monitor your bucket for any suspicious activity. Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. Every 20 minutes (or so) you query/scan. Detect New Open S3 Buckets.
From interworks.com
Creating and Sharing an AWS S3 Bucket InterWorks Detect New Open S3 Buckets If you've earned a bug bounty using this tool, please consider donating to support. Another solution would be to. Use a scanner to find s3 buckets. Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. You can list your bucket by using the amazon s3 console, the aws cli, or the aws. Detect New Open S3 Buckets.
From www.youtube.com
LAB Exercise 10 Exploit Open S3 Buckets using AWS CLI YouTube Detect New Open S3 Buckets If you've earned a bug bounty using this tool, please consider donating to support. Every 20 minutes (or so) you query/scan the dynamo table to see when the latest update is. So, how do you detect if your s3 bucket has been breached? There is tons of them on github. Use a scanner to find s3 buckets. Sign in to. Detect New Open S3 Buckets.
From docs.aws.amazon.com
Naming S3 buckets in your data layers AWS Prescriptive Guidance Detect New Open S3 Buckets Every 20 minutes (or so) you query/scan the dynamo table to see when the latest update is. So, how do you detect if your s3 bucket has been breached? Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. This can be done through aws cloudtrail, which. It detects this activity by analyzing. Detect New Open S3 Buckets.
From www.facebook.com
Common Cloud Attacks An Inside Look at Open S3 Buckets A glimpse Detect New Open S3 Buckets Another solution would be to. You can list your bucket by using the amazon s3 console, the aws cli, or the aws sdks. A tool to find open s3 buckets and dump their contents 💧. Can search using a wordlist or by monitoring the certstream network for domain names from. So, how do you detect if your s3 bucket has. Detect New Open S3 Buckets.
From www.geeksforgeeks.org
How To Store Data in a S3 Bucket? Detect New Open S3 Buckets The first step is to monitor your bucket for any suspicious activity. So, how do you detect if your s3 bucket has been breached? Use a scanner to find s3 buckets. Can search using a wordlist or by monitoring the certstream network for domain names from. Yet another program to find readable s3 buckets. It detects this activity by analyzing. Detect New Open S3 Buckets.
From ott3rly.com
Mass Hunting for Misconfigured AWS S3 Buckets Ott3rly Blog Detect New Open S3 Buckets Sign in to the aws management console and open the. This can be done through aws cloudtrail, which. Yet another program to find readable s3 buckets. Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. You can list your bucket by using the amazon s3 console, the aws cli, or the aws. Detect New Open S3 Buckets.
From janpapplegate.blob.core.windows.net
S3 Bucket Name Already Exists at janpapplegate blog Detect New Open S3 Buckets Can search using a wordlist or by monitoring the certstream network for domain names from. Use a scanner to find s3 buckets. This can be done through aws cloudtrail, which. Every 20 minutes (or so) you query/scan the dynamo table to see when the latest update is. There is tons of them on github. Another solution would be to. So,. Detect New Open S3 Buckets.
From www.youtube.com
Restrict access to your S3 buckets YouTube Detect New Open S3 Buckets Use a scanner to find s3 buckets. Can search using a wordlist or by monitoring the certstream network for domain names from. You can list your bucket by using the amazon s3 console, the aws cli, or the aws sdks. It detects this activity by analyzing aws cloudtrail events for putbucketacl actions where the access control list (acl) grants. Every. Detect New Open S3 Buckets.
From github.com
GitHub AkshayRatheesh/samplenodejsuploadawsS3bucket sample node Detect New Open S3 Buckets Can search using a wordlist or by monitoring the certstream network for domain names from. Every 20 minutes (or so) you query/scan the dynamo table to see when the latest update is. Use a scanner to find s3 buckets. Sign in to the aws management console and open the. The first step is to monitor your bucket for any suspicious. Detect New Open S3 Buckets.
From www.geeksforgeeks.org
S3Scanner Scan For Open S3 Buckets And Dump Detect New Open S3 Buckets Sign in to the aws management console and open the. You can list your bucket by using the amazon s3 console, the aws cli, or the aws sdks. A tool to find open s3 buckets and dump their contents 💧. Every 20 minutes (or so) you query/scan the dynamo table to see when the latest update is. Another solution would. Detect New Open S3 Buckets.
From pprakash.me
Sync S3 bucket to multiple S3 buckets in different region Technology Detect New Open S3 Buckets Sign in to the aws management console and open the. So, how do you detect if your s3 bucket has been breached? Use a scanner to find s3 buckets. Can search using a wordlist or by monitoring the certstream network for domain names from. It detects this activity by analyzing aws cloudtrail events for putbucketacl actions where the access control. Detect New Open S3 Buckets.
From onlineappsdba.com
Amazon S3 Bucket Overview, Errors & Resolutions Detect New Open S3 Buckets A tool to find open s3 buckets and dump their contents 💧. Sign in to the aws management console and open the. Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. Every 20 minutes (or so) you query/scan the dynamo table to see when the latest update is. There is tons of. Detect New Open S3 Buckets.
From www.linuxhunters.com
S3Scanner A tool to find open S3 buckets and dump their contents Detect New Open S3 Buckets So, how do you detect if your s3 bucket has been breached? The first step is to monitor your bucket for any suspicious activity. Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. Every 20 minutes (or so) you query/scan the dynamo table to see when the latest update is. If you've. Detect New Open S3 Buckets.
From docs.aws.amazon.com
Copy data from an S3 bucket to another account and Region by using the Detect New Open S3 Buckets So, how do you detect if your s3 bucket has been breached? It detects this activity by analyzing aws cloudtrail events for putbucketacl actions where the access control list (acl) grants. There is tons of them on github. Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. Another solution would be to.. Detect New Open S3 Buckets.
From www.hava.io
Amazon S3 Fundamentals Detect New Open S3 Buckets A tool to find open s3 buckets and dump their contents 💧. Sign in to the aws management console and open the. This can be done through aws cloudtrail, which. If you've earned a bug bounty using this tool, please consider donating to support. The first step is to monitor your bucket for any suspicious activity. You can list your. Detect New Open S3 Buckets.
From www.intelligentdiscovery.io
AWS S3 Bucket Encryption Security Best Practice Detect New Open S3 Buckets The first step is to monitor your bucket for any suspicious activity. You can list your bucket by using the amazon s3 console, the aws cli, or the aws sdks. Can search using a wordlist or by monitoring the certstream network for domain names from. So, how do you detect if your s3 bucket has been breached? Every 20 minutes. Detect New Open S3 Buckets.
From gbhackers.com
AWS Announced Malware Detection Tool For S3 Buckets Detect New Open S3 Buckets You can list your bucket by using the amazon s3 console, the aws cli, or the aws sdks. Can search using a wordlist or by monitoring the certstream network for domain names from. So, how do you detect if your s3 bucket has been breached? The first step is to monitor your bucket for any suspicious activity. A tool to. Detect New Open S3 Buckets.
From www.youtube.com
Detect AWS S3 Public Buckets using Splunk YouTube Detect New Open S3 Buckets So, how do you detect if your s3 bucket has been breached? You can list your bucket by using the amazon s3 console, the aws cli, or the aws sdks. This can be done through aws cloudtrail, which. Sign in to the aws management console and open the. The first step is to monitor your bucket for any suspicious activity.. Detect New Open S3 Buckets.
From www.pulumi.com
Serverless App to Copy and Zip Objects Between Amazon S3 Buckets Detect New Open S3 Buckets You can list your bucket by using the amazon s3 console, the aws cli, or the aws sdks. Sign in to the aws management console and open the. It detects this activity by analyzing aws cloudtrail events for putbucketacl actions where the access control list (acl) grants. If you've earned a bug bounty using this tool, please consider donating to. Detect New Open S3 Buckets.
From www.vrogue.co
How To Find Large Files In An Aws S3 Bucket Using Com vrogue.co Detect New Open S3 Buckets Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. Another solution would be to. So, how do you detect if your s3 bucket has been breached? You can list your bucket by using the amazon s3 console, the aws cli, or the aws sdks. A tool to find open s3 buckets and. Detect New Open S3 Buckets.
From itnext.io
Transfer terabytes of data between AWS s3 buckets crossaccount, cross Detect New Open S3 Buckets Every 20 minutes (or so) you query/scan the dynamo table to see when the latest update is. It detects this activity by analyzing aws cloudtrail events for putbucketacl actions where the access control list (acl) grants. The first step is to monitor your bucket for any suspicious activity. Another solution would be to. You can list your bucket by using. Detect New Open S3 Buckets.
From medium.com
AWS s3 website add cloudfront. first one open the new s3 bucket and Detect New Open S3 Buckets Use a scanner to find s3 buckets. Can search using a wordlist or by monitoring the certstream network for domain names from. Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. Another solution would be to. A tool to find open s3 buckets and dump their contents 💧. Yet another program to. Detect New Open S3 Buckets.
From binaryguy.tech
Quickest Ways to List Files in S3 Bucket Detect New Open S3 Buckets There is tons of them on github. Sign in to the aws management console and open the. It detects this activity by analyzing aws cloudtrail events for putbucketacl actions where the access control list (acl) grants. Can search using a wordlist or by monitoring the certstream network for domain names from. You can list your bucket by using the amazon. Detect New Open S3 Buckets.
From innovationm.co
S3 Bucket InnovationM Blog Detect New Open S3 Buckets Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. A tool to find open s3 buckets and dump their contents 💧. The first step is to monitor your bucket for any suspicious activity. Use a scanner to find s3 buckets. It detects this activity by analyzing aws cloudtrail events for putbucketacl actions. Detect New Open S3 Buckets.
From security.packt.com
Detect AWS S3 Bucket Misconfiguration using OpenSource tools Packt Detect New Open S3 Buckets It detects this activity by analyzing aws cloudtrail events for putbucketacl actions where the access control list (acl) grants. Can search using a wordlist or by monitoring the certstream network for domain names from. Yet another program to find readable s3 buckets. Another solution would be to. A tool to find open s3 buckets and dump their contents 💧. You. Detect New Open S3 Buckets.
From www.networkingsignal.com
What Is S3 Bucket In AWS And How To Create It? Detect New Open S3 Buckets You can list your bucket by using the amazon s3 console, the aws cli, or the aws sdks. A tool to find open s3 buckets and dump their contents 💧. Can search using a wordlist or by monitoring the certstream network for domain names from. Another solution would be to. So, how do you detect if your s3 bucket has. Detect New Open S3 Buckets.
From www.cougar.eu.com
Create S3 Bucket Detect New Open S3 Buckets Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. Use a scanner to find s3 buckets. Every 20 minutes (or so) you query/scan the dynamo table to see when the latest update is. A tool to find open s3 buckets and dump their contents 💧. So, how do you detect if your. Detect New Open S3 Buckets.
From www.ctfiot.com
Hijacking S3 Buckets New Attack Technique Exploited in the Wild by Detect New Open S3 Buckets So, how do you detect if your s3 bucket has been breached? Sign in to the aws management console and open the. This can be done through aws cloudtrail, which. A tool to find open s3 buckets and dump their contents 💧. Another solution would be to. Here is an example of a scanner written in ruby by github user. Detect New Open S3 Buckets.
From www.geeksforgeeks.org
S3Scanner Scan For Open S3 Buckets And Dump Detect New Open S3 Buckets You can list your bucket by using the amazon s3 console, the aws cli, or the aws sdks. This can be done through aws cloudtrail, which. Every 20 minutes (or so) you query/scan the dynamo table to see when the latest update is. The first step is to monitor your bucket for any suspicious activity. If you've earned a bug. Detect New Open S3 Buckets.
From www.techlear.com
How to create a lifecycle policy for an S3 Bucket on AWS Techlear Detect New Open S3 Buckets Here is an example of a scanner written in ruby by github user nahamsec, aka behrouz sadeghipour. So, how do you detect if your s3 bucket has been breached? Use a scanner to find s3 buckets. A tool to find open s3 buckets and dump their contents 💧. The first step is to monitor your bucket for any suspicious activity.. Detect New Open S3 Buckets.