What Components Of Hardware May Be Affected By Spam . experiencing spam is not only distressing, but it can pose a severe threat to the privacy of your personal data. just as there are technologies used by the attacker to commit phishing attacks, there are also technologies, both. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. Here, eset has put together a guide to what spam is,. If spammer activity is not restricted, email. This list, though not comprehensive, presents the most significant cpu and dram threats.
from stock.adobe.com
spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. Here, eset has put together a guide to what spam is,. If spammer activity is not restricted, email. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. experiencing spam is not only distressing, but it can pose a severe threat to the privacy of your personal data. This list, though not comprehensive, presents the most significant cpu and dram threats. just as there are technologies used by the attacker to commit phishing attacks, there are also technologies, both.
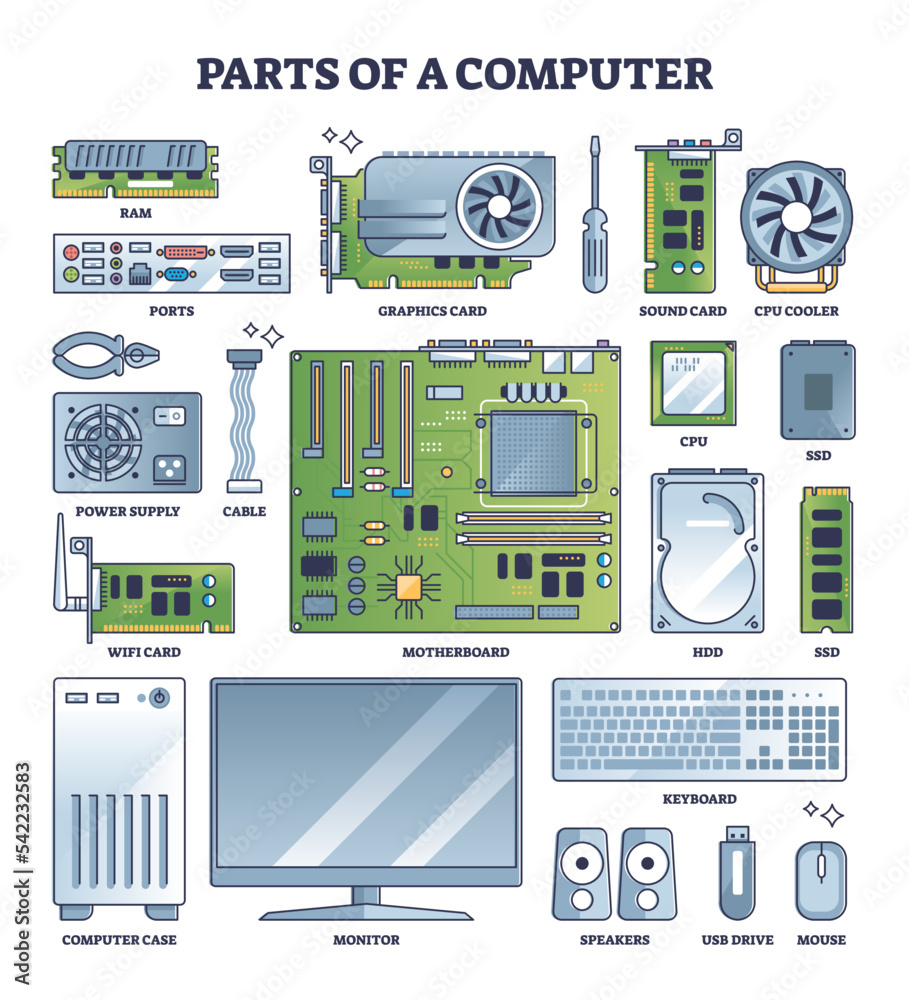
Parts of computer and PC hardware components in outline collection set
What Components Of Hardware May Be Affected By Spam Here, eset has put together a guide to what spam is,. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. This list, though not comprehensive, presents the most significant cpu and dram threats. spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. If spammer activity is not restricted, email. experiencing spam is not only distressing, but it can pose a severe threat to the privacy of your personal data. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. Here, eset has put together a guide to what spam is,. just as there are technologies used by the attacker to commit phishing attacks, there are also technologies, both.
From israelenergy.web.fc2.com
Components Of Hardware Software And Peopleware Example What Components Of Hardware May Be Affected By Spam If spammer activity is not restricted, email. spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. Here, eset has put together a guide to what spam is,. This list, though not comprehensive, presents the most significant cpu and dram threats. meltdown and spectre raised the alarm. What Components Of Hardware May Be Affected By Spam.
From www.researchgate.net
Network Structure of the Hardware Components Download Scientific Diagram What Components Of Hardware May Be Affected By Spam spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. experiencing spam is not only distressing, but it can pose a severe threat to the privacy of your personal data. If spammer activity is not restricted, email. meltdown and spectre raised the alarm over vulnerabilities that. What Components Of Hardware May Be Affected By Spam.
From issuu.com
Hardware Mindmap with pictures by billy wang Issuu What Components Of Hardware May Be Affected By Spam a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. This list, though not comprehensive, presents the most significant cpu and dram threats. just as there are technologies used by the attacker to commit phishing attacks, there are also technologies, both. experiencing spam is not only distressing, but it can pose. What Components Of Hardware May Be Affected By Spam.
From exoegjiip.blob.core.windows.net
Elements Of Hardware at Charlene Anderson blog What Components Of Hardware May Be Affected By Spam spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. just as there are technologies used by the attacker to commit phishing attacks, there are also technologies, both. This list, though not comprehensive, presents the most significant cpu and dram threats. Here, eset has put together a. What Components Of Hardware May Be Affected By Spam.
From www.slideshare.net
What are Basic Hardware of What Components Of Hardware May Be Affected By Spam meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. experiencing spam is not only distressing, but it can pose a severe threat to the privacy of your personal data. . What Components Of Hardware May Be Affected By Spam.
From www.researchgate.net
Hardware system. The system consists of seven major components two What Components Of Hardware May Be Affected By Spam If spammer activity is not restricted, email. experiencing spam is not only distressing, but it can pose a severe threat to the privacy of your personal data. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. just as there are technologies used by the attacker to commit phishing attacks, there are. What Components Of Hardware May Be Affected By Spam.
From www.truecaller.com
Truecaller Insights Top 20 Countries Affected by Spam Calls in 2020 What Components Of Hardware May Be Affected By Spam just as there are technologies used by the attacker to commit phishing attacks, there are also technologies, both. experiencing spam is not only distressing, but it can pose a severe threat to the privacy of your personal data. Here, eset has put together a guide to what spam is,. a compromised physical component can undermine all additional. What Components Of Hardware May Be Affected By Spam.
From thecustomizewindows.com
Hardware Description Language Structure and Simulation What Components Of Hardware May Be Affected By Spam meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. just as there are technologies used by the attacker to commit phishing attacks, there are also technologies, both. spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. This list, though. What Components Of Hardware May Be Affected By Spam.
From intensivegraph945.weebly.com
Components Of Hardware Software And Peopleware Of Computer intensivegraph What Components Of Hardware May Be Affected By Spam Here, eset has put together a guide to what spam is,. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. experiencing spam is not only distressing, but it can pose a severe threat to the privacy of your personal data. a compromised physical component can undermine all additional layers of a. What Components Of Hardware May Be Affected By Spam.
From www.mindomo.com
HARDWARE Mind Map What Components Of Hardware May Be Affected By Spam experiencing spam is not only distressing, but it can pose a severe threat to the privacy of your personal data. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. This list, though not comprehensive, presents. What Components Of Hardware May Be Affected By Spam.
From fiberhigh-power.netlify.app
Components Of Hardware Software And Peopleware Example What Components Of Hardware May Be Affected By Spam a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. Here, eset has put together a guide to what spam is,. just as there are technologies used by the attacker to commit phishing attacks, there are. What Components Of Hardware May Be Affected By Spam.
From www.slideshare.net
MIS Presentation Chapter III Hardware What Components Of Hardware May Be Affected By Spam just as there are technologies used by the attacker to commit phishing attacks, there are also technologies, both. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. Here, eset has put together a guide to. What Components Of Hardware May Be Affected By Spam.
From exodfkbqg.blob.core.windows.net
Hardware Interface Examples at Albert Demarest blog What Components Of Hardware May Be Affected By Spam If spammer activity is not restricted, email. spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. Here, eset has put together a guide to what spam is,. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. just as there. What Components Of Hardware May Be Affected By Spam.
From www.erp-information.com
Hardware vs Software (Features, Examples, and Types) What Components Of Hardware May Be Affected By Spam spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. Here, eset has put together a guide to what spam is,. If spammer activity is not restricted, email. experiencing spam. What Components Of Hardware May Be Affected By Spam.
From www.vectorstock.com
Hardware infographic concept flat style Royalty Free Vector What Components Of Hardware May Be Affected By Spam This list, though not comprehensive, presents the most significant cpu and dram threats. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. Here, eset has put together a guide to what spam is,. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. spam, with. What Components Of Hardware May Be Affected By Spam.
From hisbom.weebly.com
List Computer Hardware Components hisbom What Components Of Hardware May Be Affected By Spam meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. just as there are technologies used by the attacker to commit phishing attacks, there are also technologies, both. If spammer activity is not restricted, email. Here,. What Components Of Hardware May Be Affected By Spam.
From www.truecaller.com
Truecaller Insights Top 20 Countries Affected by Spam Calls in 2020 What Components Of Hardware May Be Affected By Spam spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. Here, eset has put together a guide to what spam is,. This list, though not comprehensive, presents the most significant cpu and dram threats. just as there are technologies used by the attacker to commit phishing attacks,. What Components Of Hardware May Be Affected By Spam.
From www.truecaller.com
Truecaller Insights Top 20 Countries Affected By Spam Calls In 2021 What Components Of Hardware May Be Affected By Spam just as there are technologies used by the attacker to commit phishing attacks, there are also technologies, both. If spammer activity is not restricted, email. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. spam, with its mass reach via botnets (networks of computers used to automate mass emails), has. What Components Of Hardware May Be Affected By Spam.
From www.researchgate.net
Structure of hardware components Download Scientific Diagram What Components Of Hardware May Be Affected By Spam experiencing spam is not only distressing, but it can pose a severe threat to the privacy of your personal data. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. Here, eset has put together a guide to what spam is,. spam, with its mass reach via botnets (networks of computers. What Components Of Hardware May Be Affected By Spam.
From techcrunch.com
Spam calls grew 18 in 2019 TechCrunch What Components Of Hardware May Be Affected By Spam a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. experiencing spam is not only distressing, but it can pose a severe threat to the privacy of your personal data. If spammer activity is not restricted, email. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular. What Components Of Hardware May Be Affected By Spam.
From www.researchgate.net
Mapping of components to hardware Download Scientific Diagram What Components Of Hardware May Be Affected By Spam just as there are technologies used by the attacker to commit phishing attacks, there are also technologies, both. Here, eset has put together a guide to what spam is,. spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. a compromised physical component can undermine all. What Components Of Hardware May Be Affected By Spam.
From exoxsiohy.blob.core.windows.net
Internal Hardware Drawing at David Matos blog What Components Of Hardware May Be Affected By Spam a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. experiencing spam is not only distressing, but it can pose a severe threat to the privacy of your personal data. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. just as there are technologies. What Components Of Hardware May Be Affected By Spam.
From en.ppt-online.org
Hardware Systems online presentation What Components Of Hardware May Be Affected By Spam a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. Here, eset has put together a guide to what spam is,. just as there are technologies used by the attacker to commit phishing attacks, there are also technologies, both. If spammer activity is not restricted, email. meltdown and spectre raised the. What Components Of Hardware May Be Affected By Spam.
From osr507doc.xinuos.com
Basic hardware configuration What Components Of Hardware May Be Affected By Spam This list, though not comprehensive, presents the most significant cpu and dram threats. Here, eset has put together a guide to what spam is,. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay. What Components Of Hardware May Be Affected By Spam.
From dxolvsxvp.blob.core.windows.net
Components Of The Hardware Of A Computer at Lisa Rueb blog What Components Of Hardware May Be Affected By Spam If spammer activity is not restricted, email. spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. experiencing spam is not only distressing, but it can pose a severe threat to. What Components Of Hardware May Be Affected By Spam.
From www.truecaller.com
Truecaller Insights Top 20 Countries Affected By Spam Calls In 2021 What Components Of Hardware May Be Affected By Spam spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. Here, eset has put together a guide to what spam is,. just as there are technologies used by the attacker. What Components Of Hardware May Be Affected By Spam.
From www.researchgate.net
Hardware and software components Download Scientific Diagram What Components Of Hardware May Be Affected By Spam If spammer activity is not restricted, email. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. just as there are technologies used by the attacker to commit phishing attacks, there are also technologies, both. spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been. What Components Of Hardware May Be Affected By Spam.
From exoegjiip.blob.core.windows.net
Elements Of Hardware at Charlene Anderson blog What Components Of Hardware May Be Affected By Spam Here, eset has put together a guide to what spam is,. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. spam, with its mass reach via botnets (networks of computers used to automate mass emails),. What Components Of Hardware May Be Affected By Spam.
From embeddedsimplified.blogspot.com
Embedded Simplified EMBEDDED SYSTEM HARDWARE COMPONENTS What Components Of Hardware May Be Affected By Spam This list, though not comprehensive, presents the most significant cpu and dram threats. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. If spammer activity is not restricted, email. experiencing spam is not only distressing,. What Components Of Hardware May Be Affected By Spam.
From stock.adobe.com
Parts of computer and PC hardware components in outline collection set What Components Of Hardware May Be Affected By Spam a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. Here, eset has put together a guide to what spam is,. If spammer activity is not restricted, email. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. spam, with its mass reach via botnets (networks. What Components Of Hardware May Be Affected By Spam.
From dxopvdqwi.blob.core.windows.net
Hardware Components Examples at Janice Milam blog What Components Of Hardware May Be Affected By Spam This list, though not comprehensive, presents the most significant cpu and dram threats. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. If spammer activity is not restricted, email. spam, with its mass reach via. What Components Of Hardware May Be Affected By Spam.
From dxopvdqwi.blob.core.windows.net
Hardware Components Examples at Janice Milam blog What Components Of Hardware May Be Affected By Spam meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. This list, though not comprehensive, presents the most significant cpu and dram threats. If spammer activity is not restricted, email. just as there are technologies used. What Components Of Hardware May Be Affected By Spam.
From www.researchgate.net
The hardware composition of the system Download Scientific Diagram What Components Of Hardware May Be Affected By Spam experiencing spam is not only distressing, but it can pose a severe threat to the privacy of your personal data. This list, though not comprehensive, presents the most significant cpu and dram threats. meltdown and spectre raised the alarm over vulnerabilities that attackers can exploit in popular hardware. If spammer activity is not restricted, email. a compromised. What Components Of Hardware May Be Affected By Spam.
From nikhildecodingthejargon.weebly.com
Hardware Components Decoding The Jargon What Components Of Hardware May Be Affected By Spam spam, with its mass reach via botnets (networks of computers used to automate mass emails), has been a mainstay for the. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. Here, eset has put together a guide to what spam is,. meltdown and spectre raised the alarm over vulnerabilities that. What Components Of Hardware May Be Affected By Spam.
From mazcompany.weebly.com
Chapter 3 Hardware Components MAZ company What Components Of Hardware May Be Affected By Spam Here, eset has put together a guide to what spam is,. a compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. just as there are technologies used by the attacker to commit phishing attacks, there are also technologies, both. This list, though not comprehensive, presents the most significant cpu and dram threats.. What Components Of Hardware May Be Affected By Spam.