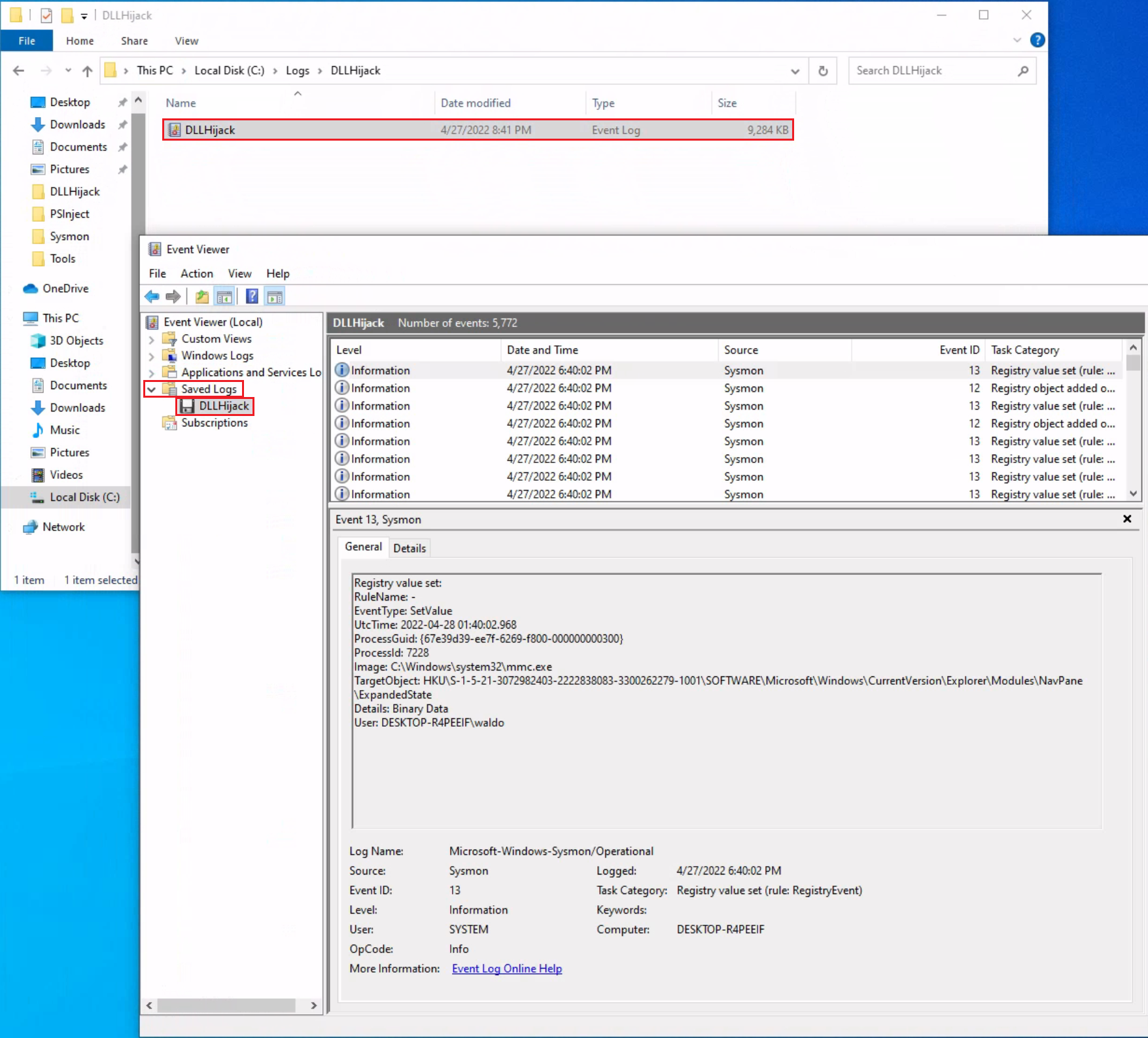
Windows Event Log Golden Ticket . note that if the attacker uses the ntlm password hash when creating the golden ticket, the tgt ticket will have rc4. — the event logs on the domain controller also show that system believes the attacker is the administrator, but the. This ticket leaves attackers to access any computers, files, folders, and most importantly domain controllers (dc). if the username and password are correct and the user account passes status and restriction checks, the dc grants the tgt. A golden ticket attack consist on the creation of a legitimate ticket granting ticket (tgt) impersonating any. — unfortunately, the native windows event logs do not include the tgt timestamps and ferreting out suspicious truly activity in the ocean of events. — golden ticket attack is part of kerberos authentication protocol. •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden ticket, so there is no universal rule to. — a golden ticket attack is a powerful attack capable of granting persistence in a windows active directory. Attackers should gain domain administrator privilege in active directory to create a golden ticket.
from academy.hackthebox.com
if the username and password are correct and the user account passes status and restriction checks, the dc grants the tgt. — unfortunately, the native windows event logs do not include the tgt timestamps and ferreting out suspicious truly activity in the ocean of events. This ticket leaves attackers to access any computers, files, folders, and most importantly domain controllers (dc). — golden ticket attack is part of kerberos authentication protocol. — the event logs on the domain controller also show that system believes the attacker is the administrator, but the. A golden ticket attack consist on the creation of a legitimate ticket granting ticket (tgt) impersonating any. note that if the attacker uses the ntlm password hash when creating the golden ticket, the tgt ticket will have rc4. Attackers should gain domain administrator privilege in active directory to create a golden ticket. •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden ticket, so there is no universal rule to. — a golden ticket attack is a powerful attack capable of granting persistence in a windows active directory.
Windows Event Logs & Finding Evil Course HTB Academy
Windows Event Log Golden Ticket — golden ticket attack is part of kerberos authentication protocol. — unfortunately, the native windows event logs do not include the tgt timestamps and ferreting out suspicious truly activity in the ocean of events. Attackers should gain domain administrator privilege in active directory to create a golden ticket. •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden ticket, so there is no universal rule to. — the event logs on the domain controller also show that system believes the attacker is the administrator, but the. A golden ticket attack consist on the creation of a legitimate ticket granting ticket (tgt) impersonating any. — a golden ticket attack is a powerful attack capable of granting persistence in a windows active directory. — golden ticket attack is part of kerberos authentication protocol. if the username and password are correct and the user account passes status and restriction checks, the dc grants the tgt. note that if the attacker uses the ntlm password hash when creating the golden ticket, the tgt ticket will have rc4. This ticket leaves attackers to access any computers, files, folders, and most importantly domain controllers (dc).
From www.winhelponline.com
How to Export Windows Event Logs from Event Viewer » Windows Event Log Golden Ticket — a golden ticket attack is a powerful attack capable of granting persistence in a windows active directory. if the username and password are correct and the user account passes status and restriction checks, the dc grants the tgt. — the event logs on the domain controller also show that system believes the attacker is the administrator,. Windows Event Log Golden Ticket.
From mysupport.razer.com
How to export Windows Event Logs Windows Event Log Golden Ticket A golden ticket attack consist on the creation of a legitimate ticket granting ticket (tgt) impersonating any. This ticket leaves attackers to access any computers, files, folders, and most importantly domain controllers (dc). — the event logs on the domain controller also show that system believes the attacker is the administrator, but the. note that if the attacker. Windows Event Log Golden Ticket.
From miteshsureja.blogspot.com
Mitesh Sureja's Blog How to Read/Write Windows Event Logs? Windows Event Log Golden Ticket note that if the attacker uses the ntlm password hash when creating the golden ticket, the tgt ticket will have rc4. — a golden ticket attack is a powerful attack capable of granting persistence in a windows active directory. — unfortunately, the native windows event logs do not include the tgt timestamps and ferreting out suspicious truly. Windows Event Log Golden Ticket.
From www.rockwellautomation.com
Windows Event Logs Windows Event Log Golden Ticket A golden ticket attack consist on the creation of a legitimate ticket granting ticket (tgt) impersonating any. note that if the attacker uses the ntlm password hash when creating the golden ticket, the tgt ticket will have rc4. — a golden ticket attack is a powerful attack capable of granting persistence in a windows active directory. —. Windows Event Log Golden Ticket.
From kb.froglogic.com
How to check the Windows event logs Windows Event Log Golden Ticket — golden ticket attack is part of kerberos authentication protocol. — a golden ticket attack is a powerful attack capable of granting persistence in a windows active directory. Attackers should gain domain administrator privilege in active directory to create a golden ticket. A golden ticket attack consist on the creation of a legitimate ticket granting ticket (tgt) impersonating. Windows Event Log Golden Ticket.
From windowsreport.com
10 Windows Event Log Best Practices You Should Know Windows Event Log Golden Ticket Attackers should gain domain administrator privilege in active directory to create a golden ticket. — the event logs on the domain controller also show that system believes the attacker is the administrator, but the. •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden ticket, so there is no universal rule to. . Windows Event Log Golden Ticket.
From www.windowscentral.com
How to use Event Viewer on Windows 10 Windows Central Windows Event Log Golden Ticket Attackers should gain domain administrator privilege in active directory to create a golden ticket. — a golden ticket attack is a powerful attack capable of granting persistence in a windows active directory. if the username and password are correct and the user account passes status and restriction checks, the dc grants the tgt. — the event logs. Windows Event Log Golden Ticket.
From www.vrogue.co
5 Best Windows 10 Event Log Viewers vrogue.co Windows Event Log Golden Ticket — unfortunately, the native windows event logs do not include the tgt timestamps and ferreting out suspicious truly activity in the ocean of events. if the username and password are correct and the user account passes status and restriction checks, the dc grants the tgt. This ticket leaves attackers to access any computers, files, folders, and most importantly. Windows Event Log Golden Ticket.
From windowsreport.com
5 best Windows 10 event log viewers Windows Event Log Golden Ticket — a golden ticket attack is a powerful attack capable of granting persistence in a windows active directory. note that if the attacker uses the ntlm password hash when creating the golden ticket, the tgt ticket will have rc4. — unfortunately, the native windows event logs do not include the tgt timestamps and ferreting out suspicious truly. Windows Event Log Golden Ticket.
From www.manageengine.com
What is Windows Event Log A complete guide from ADAudit Plus Windows Event Log Golden Ticket — unfortunately, the native windows event logs do not include the tgt timestamps and ferreting out suspicious truly activity in the ocean of events. if the username and password are correct and the user account passes status and restriction checks, the dc grants the tgt. — the event logs on the domain controller also show that system. Windows Event Log Golden Ticket.
From trevojnui.ru
Windows service event log event Windows Event Log Golden Ticket note that if the attacker uses the ntlm password hash when creating the golden ticket, the tgt ticket will have rc4. This ticket leaves attackers to access any computers, files, folders, and most importantly domain controllers (dc). if the username and password are correct and the user account passes status and restriction checks, the dc grants the tgt.. Windows Event Log Golden Ticket.
From www.manageengine.com
What is Windows Event Log A complete guide from ADAudit Plus Windows Event Log Golden Ticket •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden ticket, so there is no universal rule to. — golden ticket attack is part of kerberos authentication protocol. This ticket leaves attackers to access any computers, files, folders, and most importantly domain controllers (dc). — a golden ticket attack is a powerful. Windows Event Log Golden Ticket.
From academy.hackthebox.com
Windows Event Logs & Finding Evil Course HTB Academy Windows Event Log Golden Ticket •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden ticket, so there is no universal rule to. A golden ticket attack consist on the creation of a legitimate ticket granting ticket (tgt) impersonating any. — the event logs on the domain controller also show that system believes the attacker is the administrator,. Windows Event Log Golden Ticket.
From adsecurity.org
Detecting Kerberos Ticket (Golden Ticket & Silver Ticket) Use in Windows Event Log Golden Ticket — unfortunately, the native windows event logs do not include the tgt timestamps and ferreting out suspicious truly activity in the ocean of events. — golden ticket attack is part of kerberos authentication protocol. if the username and password are correct and the user account passes status and restriction checks, the dc grants the tgt. This ticket. Windows Event Log Golden Ticket.
From wiki.pscs.co.uk
how_toobtaining_windows_event_log Windows Event Log Golden Ticket — the event logs on the domain controller also show that system believes the attacker is the administrator, but the. A golden ticket attack consist on the creation of a legitimate ticket granting ticket (tgt) impersonating any. if the username and password are correct and the user account passes status and restriction checks, the dc grants the tgt.. Windows Event Log Golden Ticket.
From documentation.trendminer.com
How to get Windows event logs? Windows Event Log Golden Ticket note that if the attacker uses the ntlm password hash when creating the golden ticket, the tgt ticket will have rc4. — the event logs on the domain controller also show that system believes the attacker is the administrator, but the. — unfortunately, the native windows event logs do not include the tgt timestamps and ferreting out. Windows Event Log Golden Ticket.
From www.youtube.com
Powershell Get Windows Events Logs, GetEventLog, GetWinEvent cmdlet Windows Event Log Golden Ticket — the event logs on the domain controller also show that system believes the attacker is the administrator, but the. •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden ticket, so there is no universal rule to. — a golden ticket attack is a powerful attack capable of granting persistence in. Windows Event Log Golden Ticket.
From www.rockwellautomation.com
Windows Event Logs Windows Event Log Golden Ticket — unfortunately, the native windows event logs do not include the tgt timestamps and ferreting out suspicious truly activity in the ocean of events. — a golden ticket attack is a powerful attack capable of granting persistence in a windows active directory. A golden ticket attack consist on the creation of a legitimate ticket granting ticket (tgt) impersonating. Windows Event Log Golden Ticket.
From forensafe.com
Windows Event Logs Windows Event Log Golden Ticket — unfortunately, the native windows event logs do not include the tgt timestamps and ferreting out suspicious truly activity in the ocean of events. •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden ticket, so there is no universal rule to. — the event logs on the domain controller also show. Windows Event Log Golden Ticket.
From www.rockwellautomation.com
Windows Event Logs Windows Event Log Golden Ticket — the event logs on the domain controller also show that system believes the attacker is the administrator, but the. A golden ticket attack consist on the creation of a legitimate ticket granting ticket (tgt) impersonating any. — a golden ticket attack is a powerful attack capable of granting persistence in a windows active directory. Attackers should gain. Windows Event Log Golden Ticket.
From fast-lisa.unibo.it
How To View Windows Event Log Command Line Discount fastlisa.unibo.it Windows Event Log Golden Ticket — golden ticket attack is part of kerberos authentication protocol. note that if the attacker uses the ntlm password hash when creating the golden ticket, the tgt ticket will have rc4. — a golden ticket attack is a powerful attack capable of granting persistence in a windows active directory. Attackers should gain domain administrator privilege in active. Windows Event Log Golden Ticket.
From www.manageengine.com
What is Windows Event Log A complete guide from ADAudit Plus Windows Event Log Golden Ticket — golden ticket attack is part of kerberos authentication protocol. This ticket leaves attackers to access any computers, files, folders, and most importantly domain controllers (dc). •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden ticket, so there is no universal rule to. note that if the attacker uses the ntlm. Windows Event Log Golden Ticket.
From www.tactig.com
How to Configure and Analyze Event Logs in Windows 10? Tactig Windows Event Log Golden Ticket — the event logs on the domain controller also show that system believes the attacker is the administrator, but the. — golden ticket attack is part of kerberos authentication protocol. — unfortunately, the native windows event logs do not include the tgt timestamps and ferreting out suspicious truly activity in the ocean of events. if the. Windows Event Log Golden Ticket.
From www.coretechnologies.com
Essential Windows Services EventLog / Windows Event Log The Core Windows Event Log Golden Ticket This ticket leaves attackers to access any computers, files, folders, and most importantly domain controllers (dc). — unfortunately, the native windows event logs do not include the tgt timestamps and ferreting out suspicious truly activity in the ocean of events. if the username and password are correct and the user account passes status and restriction checks, the dc. Windows Event Log Golden Ticket.
From www.manageengine.com
What is Windows Event Log A complete guide from ADAudit Plus Windows Event Log Golden Ticket This ticket leaves attackers to access any computers, files, folders, and most importantly domain controllers (dc). — golden ticket attack is part of kerberos authentication protocol. A golden ticket attack consist on the creation of a legitimate ticket granting ticket (tgt) impersonating any. •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden. Windows Event Log Golden Ticket.
From www.xcitium.com
What is a Golden Ticket Attack? How to Protect Your Network Windows Event Log Golden Ticket note that if the attacker uses the ntlm password hash when creating the golden ticket, the tgt ticket will have rc4. This ticket leaves attackers to access any computers, files, folders, and most importantly domain controllers (dc). Attackers should gain domain administrator privilege in active directory to create a golden ticket. if the username and password are correct. Windows Event Log Golden Ticket.
From www.manageengine.com
What is Windows Event Log A complete guide from ADAudit Plus Windows Event Log Golden Ticket •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden ticket, so there is no universal rule to. note that if the attacker uses the ntlm password hash when creating the golden ticket, the tgt ticket will have rc4. — a golden ticket attack is a powerful attack capable of granting persistence. Windows Event Log Golden Ticket.
From www.qomplx.com
Golden Ticket Attacks Explained QOMPLX Windows Event Log Golden Ticket •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden ticket, so there is no universal rule to. — the event logs on the domain controller also show that system believes the attacker is the administrator, but the. Attackers should gain domain administrator privilege in active directory to create a golden ticket. . Windows Event Log Golden Ticket.
From www.windowscentral.com
How to use Event Viewer on Windows 10 Windows Central Windows Event Log Golden Ticket note that if the attacker uses the ntlm password hash when creating the golden ticket, the tgt ticket will have rc4. •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden ticket, so there is no universal rule to. — golden ticket attack is part of kerberos authentication protocol. — the. Windows Event Log Golden Ticket.
From www.whatsupgold.com
Using PowerShell to Search and Troubleshoot Windows Event Logs Windows Event Log Golden Ticket This ticket leaves attackers to access any computers, files, folders, and most importantly domain controllers (dc). •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden ticket, so there is no universal rule to. — golden ticket attack is part of kerberos authentication protocol. — the event logs on the domain controller. Windows Event Log Golden Ticket.
From davescomputertips.com
Windows 10 Quick Tips Event Viewer Daves Computer Tips Windows Event Log Golden Ticket Attackers should gain domain administrator privilege in active directory to create a golden ticket. — golden ticket attack is part of kerberos authentication protocol. This ticket leaves attackers to access any computers, files, folders, and most importantly domain controllers (dc). — a golden ticket attack is a powerful attack capable of granting persistence in a windows active directory.. Windows Event Log Golden Ticket.
From www.manageengine.com
What is Windows Event Log A complete guide from ADAudit Plus Windows Event Log Golden Ticket if the username and password are correct and the user account passes status and restriction checks, the dc grants the tgt. — unfortunately, the native windows event logs do not include the tgt timestamps and ferreting out suspicious truly activity in the ocean of events. A golden ticket attack consist on the creation of a legitimate ticket granting. Windows Event Log Golden Ticket.
From www.eginnovations.com
What is Windows Event Log? eG Innovations Windows Event Log Golden Ticket — a golden ticket attack is a powerful attack capable of granting persistence in a windows active directory. — the event logs on the domain controller also show that system believes the attacker is the administrator, but the. note that if the attacker uses the ntlm password hash when creating the golden ticket, the tgt ticket will. Windows Event Log Golden Ticket.
From wiki.pscs.co.uk
how_toobtaining_windows_event_log Windows Event Log Golden Ticket note that if the attacker uses the ntlm password hash when creating the golden ticket, the tgt ticket will have rc4. — the event logs on the domain controller also show that system believes the attacker is the administrator, but the. •windows event logs does not distinguish the use of legitimate tgt ticket versus a golden ticket,. Windows Event Log Golden Ticket.
From www.how.com.vn
Cómo revisar el registro de eventos de IIS en Windows Wiki Windows Windows Event Log Golden Ticket — the event logs on the domain controller also show that system believes the attacker is the administrator, but the. This ticket leaves attackers to access any computers, files, folders, and most importantly domain controllers (dc). Attackers should gain domain administrator privilege in active directory to create a golden ticket. — a golden ticket attack is a powerful. Windows Event Log Golden Ticket.