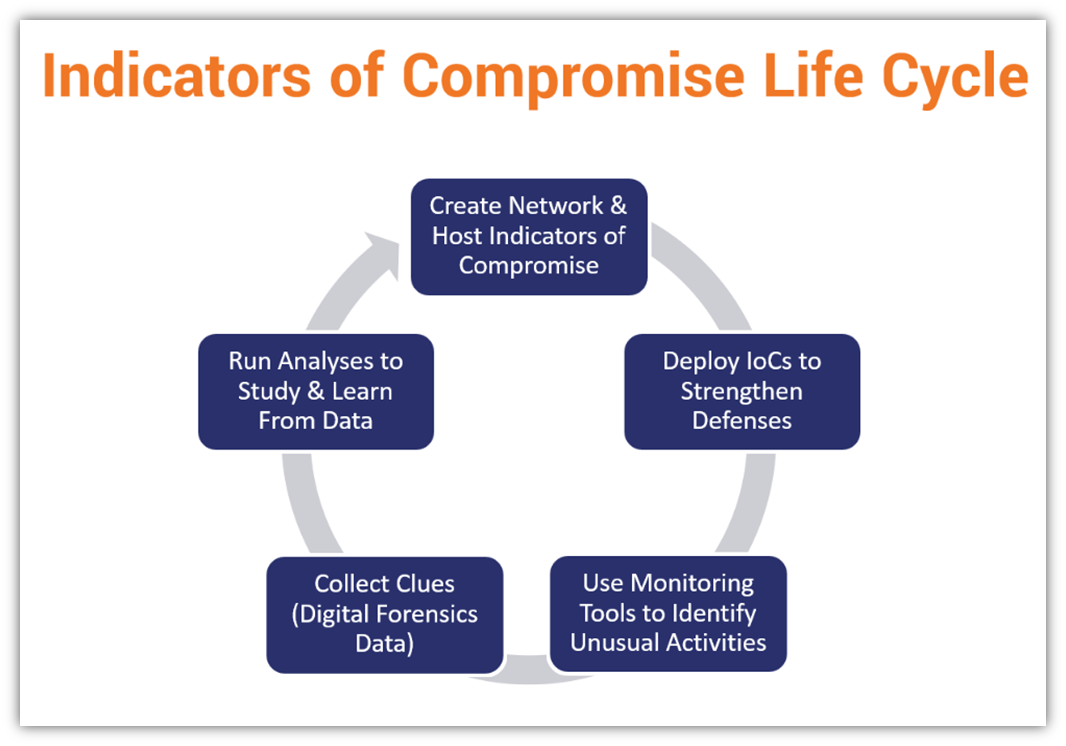
Indicators Of Compromise Report . During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack based on them. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. This guide explores the types of iocs, their. Their presence indicates a vulnerability within. For example, iocs can be unusual network traffic. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked.
from www.thesslstore.com
Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Their presence indicates a vulnerability within. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. This guide explores the types of iocs, their. During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack based on them. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. For example, iocs can be unusual network traffic.
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed
Indicators Of Compromise Report The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack based on them. The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack based on them. During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. Their presence indicates a vulnerability within. For example, iocs can be unusual network traffic. This guide explores the types of iocs, their. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat.
From www.researchgate.net
(PDF) Decaying Indicators of Compromise Indicators Of Compromise Report Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack based on them. Indicators of compromise (iocs) refer to data that indicates a system may. Indicators Of Compromise Report.
From www.sekoia.io
What is an Indicator of Compromise (IoC)? Sekoia.io Indicators Of Compromise Report Their presence indicates a vulnerability within. The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack based on them. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. During a cybersecurity incident, indicators of compromise (ioc) are clues. Indicators Of Compromise Report.
From flare.io
Indicators of Compromise (IOCs) and External Risk Monitoring Flare Indicators Of Compromise Report For example, iocs can be unusual network traffic. During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Their presence indicates a vulnerability within. The result of each completed case with an investigation is a report. Indicators Of Compromise Report.
From www.wallarm.com
What are Indicators of Compromise (IOC)? Indicators Of Compromise Report Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. For example, iocs can be unusual network traffic. The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack based on them. Indicators of compromise (iocs) are artifacts that. Indicators Of Compromise Report.
From www.packetlabs.net
What are Indicators of Compromise (IoCs)? Indicators Of Compromise Report An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Indicators of compromise. Indicators Of Compromise Report.
From any.run
IoC Indicators of Compromise ANY.RUN Blog Indicators Of Compromise Report Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. This guide explores the types of iocs, their. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Indicators of compromise are behaviors or. Indicators Of Compromise Report.
From www.upguard.com
What are Indicators of Compromise (IOCs)? UpGuard Indicators Of Compromise Report Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Indicators of compromise (iocs). Indicators Of Compromise Report.
From www.xcitium.com
What are Indicators of Compromise Security? IOC Meaning Indicators Of Compromise Report Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Indicators of compromise. Indicators Of Compromise Report.
From www.semanticscholar.org
Indicator of compromise Semantic Scholar Indicators Of Compromise Report Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack based on them. This guide explores the types of iocs, their. Their presence indicates a vulnerability within. For example, iocs can be unusual network traffic. During. Indicators Of Compromise Report.
From nevelexlabs.com
Dashboard Report Indicators of Compromise Nevelex Labs Indicators Of Compromise Report This guide explores the types of iocs, their. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack. Indicators Of Compromise Report.
From www.redpacketsecurity.com
Indicators of compromise (IOCs) how we collect and use them Indicators Of Compromise Report The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack based on them. For example, iocs can be unusual network traffic. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. During a cybersecurity incident, indicators of compromise (ioc). Indicators Of Compromise Report.
From www.slideshare.net
Security Analytics to Identify the 12 Indicators of Compromise Indicators Of Compromise Report Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise are behaviors or data which show that a. Indicators Of Compromise Report.
From nevelexlabs.com
Dashboard Report Indicators of Compromise Nevelex Labs Indicators Of Compromise Report Their presence indicates a vulnerability within. During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise are behaviors. Indicators Of Compromise Report.
From www.forensicfocus.com
Indicators of Compromise What's Interesting, What's Not and What Else Indicators Of Compromise Report Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. This guide explores the types of iocs, their. For example, iocs can be unusual network traffic. Their presence indicates a vulnerability within. An indicator of compromise (ioc) is a piece of digital forensics. Indicators Of Compromise Report.
From www.dreamstime.com
Conceptual Hand Writing Showing Indicators of Compromise. Business Indicators Of Compromise Report This guide explores the types of iocs, their. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. For example, iocs can be unusual network traffic.. Indicators Of Compromise Report.
From es.scribd.com
Top 15 Indicators of Compromise PDF Denial Of Service Attack Indicators Of Compromise Report Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. The result of each completed case with an investigation is a report that collects all. Indicators Of Compromise Report.
From www.lepide.com
What are Indicators of Compromise? Indicators Of Compromise Report Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Their presence indicates a vulnerability within. For example, iocs can be unusual network traffic. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators. Indicators Of Compromise Report.
From fineproxy.org
Indicator of Compromise (IOC) FineProxy Glossary Indicators Of Compromise Report Their presence indicates a vulnerability within. During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. This guide explores the types of iocs, their. Indicators of compromise (iocs) refer to data that indicates a system may. Indicators Of Compromise Report.
From hstechdocs.helpsystems.com
Reports Indicators Of Compromise Report Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack based on them. For example, iocs can be unusual network traffic. An indicator of compromise. Indicators Of Compromise Report.
From www.isdecisions.com
Key Indicators of Compromise to Prevent a Breach Indicators Of Compromise Report Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. For example, iocs can be unusual network traffic. During a cybersecurity incident,. Indicators Of Compromise Report.
From www.makeuseof.com
What Do the Indicators of Compromise Mean? The Best Tools to Help Indicators Of Compromise Report For example, iocs can be unusual network traffic. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. This guide explores the types of iocs, their. The result of each completed case with an investigation is a report that collects all. Indicators Of Compromise Report.
From www.linkedin.com
Indicators of Compromise (IOCs) Explained Indicators Of Compromise Report Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack based on them. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an. Indicators Of Compromise Report.
From www.teramind.co
10 Indicators of Compromise (IOC) Examples To Look Out For Indicators Of Compromise Report During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Their presence indicates a vulnerability within. For example, iocs can be unusual network traffic. The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack based on them. Indicators of compromise (iocs). Indicators Of Compromise Report.
From www.researchgate.net
(PDF) Indicators of Compromise as an Instrument for Threat Intelligence Indicators Of Compromise Report Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have been breached. The result of each completed case with an investigation is a report that collects all the indicators of compromise and. Indicators Of Compromise Report.
From makrushin.com
Indicators of compromise as a way to reduce risk · Denis Makrushin Indicators Of Compromise Report For example, iocs can be unusual network traffic. The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack based on them. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. During a cybersecurity incident, indicators of compromise. Indicators Of Compromise Report.
From www.linkedin.com
What are IT Security Indicators of Compromise? Indicators Of Compromise Report The result of each completed case with an investigation is a report that collects all the indicators of compromise and indicators of attack based on them. This guide explores the types of iocs, their. During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Indicators of compromise are behaviors or data which show that. Indicators Of Compromise Report.
From www.onlinesolutionsgroup.de
Indicators of Compromise (IoCs) ⏩ Online Marketing Glossar der OSG Indicators Of Compromise Report During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. For example, iocs can be unusual network traffic. Indicators of compromise (iocs) refer to data that indicates a system may have been. Indicators Of Compromise Report.
From cyberhoot.com
Indicators of Compromise (IoC) CyberHoot Indicators Of Compromise Report This guide explores the types of iocs, their. Their presence indicates a vulnerability within. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. For example, iocs can be unusual network traffic. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been. Indicators Of Compromise Report.
From www.youtube.com
What are the Indicators of compromise YouTube Indicators Of Compromise Report Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. The result of each completed case with an investigation is a report that collects all the indicators of compromise and. Indicators Of Compromise Report.
From www.sentinelone.com
What are Indicators of Compromise (IoCs)? An Easy Guide Indicators Of Compromise Report Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Their presence indicates a vulnerability within. Indicators of compromise (iocs) refer to data that indicates a system may have been infiltrated by a cyber threat. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. An indicator of compromise (ioc) is. Indicators Of Compromise Report.
From www.lepide.com
What are Indicators of Compromise? Indicators Of Compromise Report Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. For example, iocs can be unusual network traffic. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. During. Indicators Of Compromise Report.
From www.armordot.com
Indicators of Compromise in Threat Intelligence Let's speak some Indicators Of Compromise Report Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. During a cybersecurity incident, indicators of compromise (ioc) are. Indicators Of Compromise Report.
From www.thesslstore.com
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed Indicators Of Compromise Report Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Their presence indicates a vulnerability within. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. Indicators of compromise. Indicators Of Compromise Report.
From www.rstcloud.com
Public Database of 10M Indicators of Compromise RST Cloud Indicators Of Compromise Report This guide explores the types of iocs, their. Indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Indicators of compromise (iocs) are artifacts that indicate a potential intrusion. During. Indicators Of Compromise Report.
From www.cyberwiki.in
Indicators of Compromise (IoCs) CyberWiki Encyclopedia of Cybersecurity Indicators Of Compromise Report During a cybersecurity incident, indicators of compromise (ioc) are clues and evidence of a data breach. Indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Their presence indicates a vulnerability within. An indicator of compromise (ioc) is a piece of digital forensics that suggests that an endpoint or network may have. Indicators Of Compromise Report.