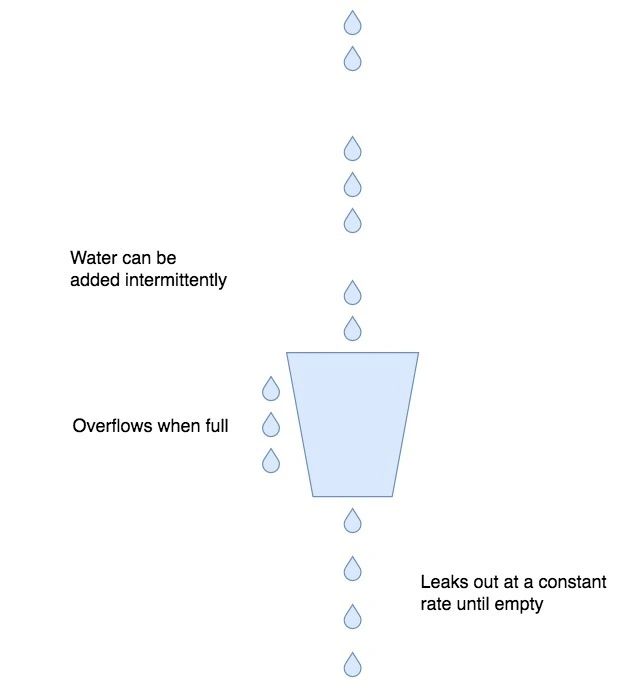
Leaky Bucket Algorithm Logic . The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. What is the leaky bucket algorithm? The leaky bucket algorithm is a traffic shaping algorithm to reduce the load the transport layer places on the network layer and reduce. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. It is often used in scenarios where a constant. Open loop and closed loop. Step 1 − let us imagine a. Write a program for congestion control using leaky bucket algorithm. The congesting control algorithms are basically divided into two groups: This algorithm is used to control the rate at which traffic is sent.
from api7.ai
Write a program for congestion control using leaky bucket algorithm. The congesting control algorithms are basically divided into two groups: The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. Open loop and closed loop. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Step 1 − let us imagine a. The leaky bucket algorithm is a traffic shaping algorithm to reduce the load the transport layer places on the network layer and reduce. This algorithm is used to control the rate at which traffic is sent. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. What is the leaky bucket algorithm?
How to Deal with Bursty Traffic Leaky Bucket and Token Bucket
Leaky Bucket Algorithm Logic The leaky bucket algorithm is a traffic shaping algorithm to reduce the load the transport layer places on the network layer and reduce. The leaky bucket algorithm is a traffic shaping algorithm to reduce the load the transport layer places on the network layer and reduce. A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. What is the leaky bucket algorithm? Step 1 − let us imagine a. This algorithm is used to control the rate at which traffic is sent. The congesting control algorithms are basically divided into two groups: Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. Write a program for congestion control using leaky bucket algorithm. It is often used in scenarios where a constant. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. Open loop and closed loop.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and Leaky Bucket Algorithm Logic Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket algorithm is a traffic shaping algorithm to reduce the load the transport layer places on the network layer and reduce. What is the leaky bucket algorithm? The leaky bucket algorithm is a network traffic management mechanism used to control. Leaky Bucket Algorithm Logic.
From www.researchgate.net
The Packet leaky Bucket Algorithm marked with low priority (maximum Leaky Bucket Algorithm Logic The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. Step 1 − let us imagine a. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket algorithm is a traffic shaping algorithm to reduce the load the transport. Leaky Bucket Algorithm Logic.
From www.studocu.com
Leaky Bucket Algorithm Leaky Bucket A leaking bucket is a simple Leaky Bucket Algorithm Logic A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. This algorithm is used to control the rate at which traffic is sent. The congesting control algorithms are basically divided into two groups: What is the leaky bucket algorithm? The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow. Leaky Bucket Algorithm Logic.
From exyypouit.blob.core.windows.net
Leaky Bucket Model at Nellie Shepler blog Leaky Bucket Algorithm Logic Write a program for congestion control using leaky bucket algorithm. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. This algorithm is used to control the rate at which traffic is sent. Open loop and closed loop. It is often used in scenarios where a constant. Leaky bucket. Leaky Bucket Algorithm Logic.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Algorithm Logic The congesting control algorithms are basically divided into two groups: A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. Write a program for congestion control using leaky bucket algorithm. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. The leaky bucket. Leaky Bucket Algorithm Logic.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Algorithm Logic A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. Write a program for congestion control using leaky bucket algorithm. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. What is the leaky bucket algorithm? Leaky bucket algorithm mainly controls the total amount. Leaky Bucket Algorithm Logic.
From www.code4it.dev
Davide's Code and Architecture Notes 4 algorithms to implement Rate Leaky Bucket Algorithm Logic Step 1 − let us imagine a. The congesting control algorithms are basically divided into two groups: Write a program for congestion control using leaky bucket algorithm. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Open loop and closed loop. This algorithm is used to control the rate at which. Leaky Bucket Algorithm Logic.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Algorithm Logic What is the leaky bucket algorithm? Step 1 − let us imagine a. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. This algorithm is used to control the rate at which traffic is sent. Open loop and closed loop. Write a program for congestion control using leaky. Leaky Bucket Algorithm Logic.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm Logic Write a program for congestion control using leaky bucket algorithm. Open loop and closed loop. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. What is the leaky bucket algorithm? This algorithm is used to control the rate at which traffic is sent. Leaky bucket algorithm mainly controls. Leaky Bucket Algorithm Logic.
From slideplayer.com
Congestion Control Evaluation in Dynamic Network ppt download Leaky Bucket Algorithm Logic This algorithm is used to control the rate at which traffic is sent. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. Open loop and closed loop. The congesting control algorithms are basically divided into two groups: Write a program for congestion control using leaky bucket algorithm. The. Leaky Bucket Algorithm Logic.
From dev.to
Rate Limiter in System Design. Part 2 Commonly Used Algorithms DEV Leaky Bucket Algorithm Logic Open loop and closed loop. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. This algorithm is used to control the rate at which traffic is sent. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. What is the leaky. Leaky Bucket Algorithm Logic.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm Logic Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. The congesting control algorithms are basically divided into two groups: The leaky bucket algorithm is a network traffic management mechanism used to control the rate at. Leaky Bucket Algorithm Logic.
From www.geeksforgeeks.org
How to Design a Rate Limiter API Learn System Design Leaky Bucket Algorithm Logic The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. The congesting control algorithms are basically divided into two groups: This algorithm is used to control the rate at which traffic is sent. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of. Leaky Bucket Algorithm Logic.
From brainly.in
leaky bucket algorithm Brainly.in Leaky Bucket Algorithm Logic Write a program for congestion control using leaky bucket algorithm. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. It is often used in scenarios where a constant. The leaky bucket algorithm. Leaky Bucket Algorithm Logic.
From www.researchgate.net
Logical structure of leaky bucket Download Scientific Diagram Leaky Bucket Algorithm Logic A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. The congesting control algorithms are basically divided into two groups: The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. Step 1 − let us imagine a. Leaky bucket algorithm mainly controls the total. Leaky Bucket Algorithm Logic.
From www.youtube.com
Leaky Bucket vs Token Bucket Algorithm Leaky Bucket and Token Bucket Leaky Bucket Algorithm Logic Step 1 − let us imagine a. This algorithm is used to control the rate at which traffic is sent. Open loop and closed loop. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. What is the leaky bucket algorithm? The leaky bucket algorithm is a simple yet effective algorithm designed. Leaky Bucket Algorithm Logic.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Logic What is the leaky bucket algorithm? A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. It is often used in scenarios where a constant. Step 1 − let us imagine a. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. Leaky bucket. Leaky Bucket Algorithm Logic.
From www.semanticscholar.org
[PDF] Leaky Bucket Algorithm for Congestion Control Semantic Scholar Leaky Bucket Algorithm Logic The congesting control algorithms are basically divided into two groups: The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. This algorithm is used to control the rate at which traffic is sent. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to. Leaky Bucket Algorithm Logic.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID5320728 Leaky Bucket Algorithm Logic It is often used in scenarios where a constant. Step 1 − let us imagine a. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. Open loop and closed loop. The leaky bucket algorithm is. Leaky Bucket Algorithm Logic.
From www.researchgate.net
Selectivity of the conventional leaky bucket algorithm, the fuzzy leaky Leaky Bucket Algorithm Logic Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. This algorithm is used to control the rate at which traffic is sent. It is often used in scenarios where a. Leaky Bucket Algorithm Logic.
From www.youtube.com
Leaky Bucket Algorithm Token Bucket Algorithm Leaky Bucket Vs Token Leaky Bucket Algorithm Logic A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. The congesting control algorithms are basically divided into two groups: It is often used in scenarios where a constant. Open loop and closed loop.. Leaky Bucket Algorithm Logic.
From www.youtube.com
Leaky And Token Bucket Algorithms YouTube Leaky Bucket Algorithm Logic What is the leaky bucket algorithm? This algorithm is used to control the rate at which traffic is sent. Write a program for congestion control using leaky bucket algorithm. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. It is often used in scenarios where a constant. The. Leaky Bucket Algorithm Logic.
From www.youtube.com
Leaky bucket algorithm YouTube Leaky Bucket Algorithm Logic Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. What. Leaky Bucket Algorithm Logic.
From www.researchgate.net
Token bucket algorithm Download Scientific Diagram Leaky Bucket Algorithm Logic The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket algorithm is. Leaky Bucket Algorithm Logic.
From api7.ai
How to Deal with Bursty Traffic Leaky Bucket and Token Bucket Leaky Bucket Algorithm Logic What is the leaky bucket algorithm? This algorithm is used to control the rate at which traffic is sent. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network.. Leaky Bucket Algorithm Logic.
From www.youtube.com
Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm Logic This algorithm is used to control the rate at which traffic is sent. What is the leaky bucket algorithm? The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Open loop. Leaky Bucket Algorithm Logic.
From www.scribd.com
Leaky Bucket algorithm PDF Leaky Bucket Algorithm Logic The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. It is often used in scenarios where a constant. The leaky bucket algorithm is a traffic shaping algorithm to reduce the load the transport layer places on the network layer and reduce. The leaky bucket algorithm is a network traffic. Leaky Bucket Algorithm Logic.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket Algorithm Logic The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. This algorithm is used to control the rate at which traffic is sent. Write a program for congestion control using leaky bucket algorithm. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to. Leaky Bucket Algorithm Logic.
From api7.ai
How to Deal with Bursty Traffic Leaky Bucket and Token Bucket Leaky Bucket Algorithm Logic Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. This algorithm is used to control the rate at which traffic is sent. Write a program for congestion control using leaky bucket algorithm. A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. Step 1 −. Leaky Bucket Algorithm Logic.
From github.com
GitHub HirenAmbekar/LeakyBucketAlgorithmDemonstration This is a Leaky Bucket Algorithm Logic The leaky bucket algorithm is a simple yet effective algorithm designed to regulate the flow of data through a network. A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. It is often used in scenarios where a constant. This algorithm is used to control the rate at which traffic is sent. Step 1. Leaky Bucket Algorithm Logic.
From exyypouit.blob.core.windows.net
Leaky Bucket Model at Nellie Shepler blog Leaky Bucket Algorithm Logic This algorithm is used to control the rate at which traffic is sent. Write a program for congestion control using leaky bucket algorithm. A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. What is the leaky bucket algorithm? The leaky bucket algorithm is a network traffic management mechanism used to control the rate. Leaky Bucket Algorithm Logic.
From www.semanticscholar.org
[PDF] Leaky Bucket Algorithm for Congestion Control Semantic Scholar Leaky Bucket Algorithm Logic It is often used in scenarios where a constant. Open loop and closed loop. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted. The congesting control algorithms are basically divided into two groups: A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping. Leaky Bucket Algorithm Logic.
From towardsdev.com
Leaky Bucket vs Token Bucket in Rate Limiting Algorithms by David Lee Leaky Bucket Algorithm Logic The congesting control algorithms are basically divided into two groups: It is often used in scenarios where a constant. A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. Write a program for congestion control using leaky bucket algorithm. The leaky bucket algorithm is a network traffic management mechanism used to control the rate. Leaky Bucket Algorithm Logic.
From www.youtube.com
Leaky Bucket vs Token Bucket Algorithm Leaky Bucket and Token Bucket Leaky Bucket Algorithm Logic A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. This algorithm is used to control the rate at which traffic is sent. Write a program for congestion control using leaky bucket algorithm. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted.. Leaky Bucket Algorithm Logic.
From www.slideserve.com
PPT Leaky Bucket Algorithm PowerPoint Presentation ID418337 Leaky Bucket Algorithm Logic The congesting control algorithms are basically divided into two groups: This algorithm is used to control the rate at which traffic is sent. A leaky bucket execution and a token bucket execution are predominantly used for traffic shaping algorithms. It is often used in scenarios where a constant. Step 1 − let us imagine a. Write a program for congestion. Leaky Bucket Algorithm Logic.