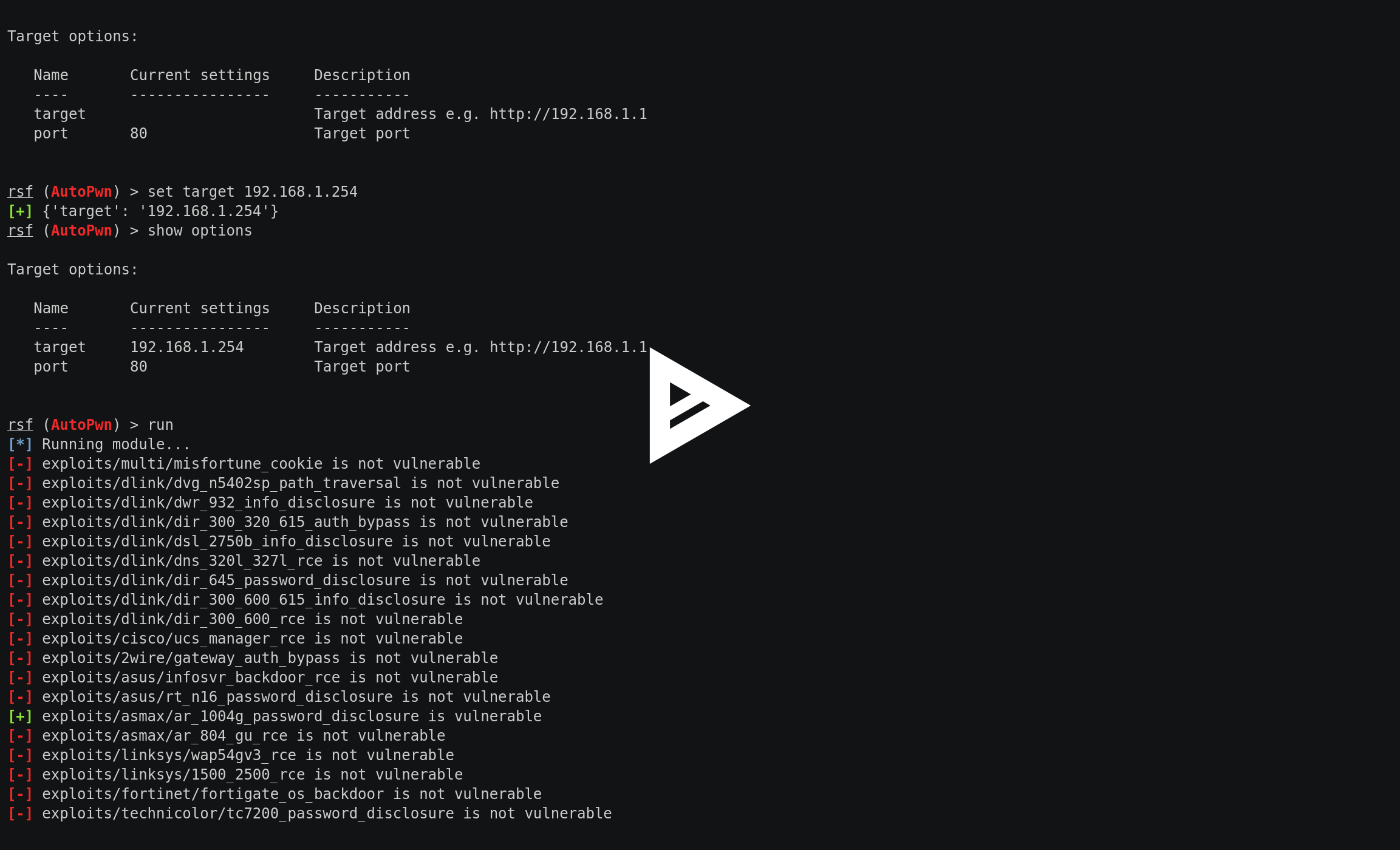
Routersploit List . The payloads module generates payloads for injection points. Exploitation framework for embedded devices. And the generic modules are for performing generic attacks. Contribute to threat9/routersploit development by creating an account on github. We can check their full list via the search bruteforce. It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: Check how vulnerable your router is and how easily it can be hacked with. Learn hacking routers with routersploit. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device.
from www.clicksconcepts.com
We can check their full list via the search bruteforce. Exploitation framework for embedded devices. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Contribute to threat9/routersploit development by creating an account on github. Learn hacking routers with routersploit. And the generic modules are for performing generic attacks. Check how vulnerable your router is and how easily it can be hacked with. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software. The payloads module generates payloads for injection points.
Router Exploit Framework Click's Concepts, LLC
Routersploit List It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software. Check how vulnerable your router is and how easily it can be hacked with. It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software. Exploitation framework for embedded devices. We can check their full list via the search bruteforce. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. And the generic modules are for performing generic attacks. Learn hacking routers with routersploit. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: The payloads module generates payloads for injection points. Contribute to threat9/routersploit development by creating an account on github.
From github.com
GitHub threat9/routersploit Exploitation Framework for Embedded Devices Routersploit List And the generic modules are for performing generic attacks. Learn hacking routers with routersploit. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: It is natural that routers or cameras, depending on the version and publisher, have. Routersploit List.
From www.youtube.com
TUTORIAL HOW TO USE ROUTERSPLOIT YouTube Routersploit List Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Learn hacking routers with routersploit. We can check their full list via the search bruteforce. And the generic modules are for performing generic attacks. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: Exploitation framework for embedded. Routersploit List.
From pentestcore.com
آموزش ابزار RouterSploit در تست نفوذ پن تست کور Routersploit List And the generic modules are for performing generic attacks. Contribute to threat9/routersploit development by creating an account on github. Learn hacking routers with routersploit. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: Check how vulnerable your router is and how easily it can be hacked with. The payloads module generates payloads for injection points.. Routersploit List.
From www.youtube.com
RouterSploit Complete Tutorial YouTube Routersploit List Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Check how vulnerable your router is and how easily it can be hacked with. Learn hacking routers with routersploit. And the generic modules are for performing generic attacks. It is natural that routers or cameras, depending on the version and publisher, have. Routersploit List.
From www.youtube.com
RouterSploit Tutorial Protect Your Router From Getting Hacked Routersploit List Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: Contribute to threat9/routersploit development by creating an account on github. Exploitation framework for embedded devices. The payloads module generates payloads for injection points. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. And the generic modules are. Routersploit List.
From iemlabs.com
RouterSploit Cybersecurity Tool IEMLabs Blog Knowledge Base Routersploit List Learn hacking routers with routersploit. We can check their full list via the search bruteforce. Check how vulnerable your router is and how easily it can be hacked with. Exploitation framework for embedded devices. The payloads module generates payloads for injection points. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device.. Routersploit List.
From cyberpointsolution.com
Router and Switches Testing Tools Routersploit Framework Routersploit List Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. The payloads module generates payloads for injection points. Exploitation framework for embedded devices. Check how vulnerable your router is and how easily it can be hacked with. It is natural that routers or cameras, depending on the version and publisher, have their. Routersploit List.
From rucore.net
️ Routersploit Gaining Access to IoT Devices English Routersploit List Contribute to threat9/routersploit development by creating an account on github. We can check their full list via the search bruteforce. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: Check how vulnerable your router is and how easily it can be hacked with. Routersploit boasts of over 131 scanners modules for checking if an exploit. Routersploit List.
From pentesttools.net
RouterSploit v3.4.0 Exploitation Framework For Embedded Devices Routersploit List Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. We can check their full list via the search bruteforce. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions. Routersploit List.
From www.youtube.com
Exploit a Router Using RouterSploit [Tutorial] YouTube Routersploit List Learn hacking routers with routersploit. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: We can check their full list via the search bruteforce. Exploitation framework for embedded devices. Check how vulnerable your router is and how. Routersploit List.
From huaweicloud.csdn.net
安卓手机通过Termux免Root运行Routersploit对路由器进行渗透【Rsf】【渗透工具】【Termux】_ios_TY汤圆华为云 Routersploit List Exploitation framework for embedded devices. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Check how vulnerable your router is and how easily it can be hacked with. It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software. Routersploit also provides. Routersploit List.
From miloserdov.org
RouterSploit User Manual Ethical hacking and testing Routersploit List Learn hacking routers with routersploit. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software. Contribute to threat9/routersploit development by creating an account on github. Exploitation framework for embedded devices. We can. Routersploit List.
From www.pinterest.com
How to Exploit Routers on an Unrooted Android Phone Android phone Routersploit List Learn hacking routers with routersploit. Check how vulnerable your router is and how easily it can be hacked with. And the generic modules are for performing generic attacks. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Exploitation framework for embedded devices. The payloads module generates payloads for injection points. Routersploit. Routersploit List.
From rucore.net
️ Routersploit Gaining Access to IoT Devices English Routersploit List Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. We can check their full list via the search bruteforce. Contribute to threat9/routersploit development by creating an account on github. The payloads module generates payloads for injection points. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols:. Routersploit List.
From zahidknyha.com.ua
Routersploit termux как пользоваться Routersploit List Check how vulnerable your router is and how easily it can be hacked with. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: And the generic modules are for performing generic attacks. Exploitation framework for embedded devices. Contribute to threat9/routersploit development by creating an account on github. Learn hacking routers with routersploit. Routersploit boasts of. Routersploit List.
From www.youtube.com
RouterSploit Exploitation Framework for Embedded Devices Latest Routersploit List It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software. Check how vulnerable your router is and how easily it can be hacked with. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: Learn hacking routers with routersploit. And the generic modules are for performing. Routersploit List.
From techgyanmantra07.blogspot.com
Tech Gyan Exploit a Router Using RouterSploit Routersploit List Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: Contribute to threat9/routersploit development by creating an account on github. We can check their full list via the search bruteforce. Learn hacking routers with routersploit. It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software. Check. Routersploit List.
From www.youtube.com
Routersploit Tool Installation in Termux Termux thenoobhacker YouTube Routersploit List It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software. And the generic modules are for performing generic attacks. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target. Routersploit List.
From null-byte.wonderhowto.com
How to Exploit Routers on an Unrooted Android Phone « Null Byte Routersploit List Check how vulnerable your router is and how easily it can be hacked with. Exploitation framework for embedded devices. The payloads module generates payloads for injection points. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. It is natural that routers or cameras, depending on the version and publisher, have their. Routersploit List.
From www.freebuf.com
RouterSploit:一款功能强大的嵌入式设备渗透测试框架 FreeBuf网络安全行业门户 Routersploit List Check how vulnerable your router is and how easily it can be hacked with. Exploitation framework for embedded devices. The payloads module generates payloads for injection points. We can check their full list via the search bruteforce. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. And the generic modules are. Routersploit List.
From techgyanmantra07.blogspot.com
Tech Gyan Exploit a Router Using RouterSploit Routersploit List Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Check how vulnerable your router is and how easily it can be hacked with. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: Learn hacking routers with routersploit. And the generic modules are for performing generic attacks.. Routersploit List.
From benisnous.com
Exploiting Router with RouterSploit [Tutorial] Kali Linux Routersploit List Exploitation framework for embedded devices. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. The payloads module. Routersploit List.
From www.cyberpunk.rs
Router Exploitation Framework RouterSploit CYBERPUNK Routersploit List We can check their full list via the search bruteforce. Learn hacking routers with routersploit. Check how vulnerable your router is and how easily it can be hacked with. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target. Routersploit List.
From null-byte.wonderhowto.com
How to Seize Control of a Router with RouterSploit « Null Byte Routersploit List Check how vulnerable your router is and how easily it can be hacked with. Learn hacking routers with routersploit. And the generic modules are for performing generic attacks. We can check their full list via the search bruteforce. It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software. Routersploit boasts. Routersploit List.
From www.clicksconcepts.com
Router Exploit Framework Click's Concepts, LLC Routersploit List Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Contribute to threat9/routersploit development by creating an account on github. And the generic modules are for performing generic attacks. Check how vulnerable your router is and how easily it can be hacked with. Routersploit also provides the ability to bruteforce attack network. Routersploit List.
From blog.csdn.net
routersploit简单实例CSDN博客 Routersploit List Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. We can check their full list via the search bruteforce. Check how vulnerable your router is and how easily it can be hacked with. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: It is natural that. Routersploit List.
From telegra.ph
Проникновение в маршрутизаторы с помощью Routersploit Telegraph Routersploit List We can check their full list via the search bruteforce. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: And the generic modules are for performing generic attacks. Learn hacking routers with routersploit. Check how vulnerable your router is and how easily it can be hacked with. The payloads module generates payloads for injection points.. Routersploit List.
From www.pinterest.com
How to Exploit Routers on an Unrooted Android Phone Android phone Routersploit List Contribute to threat9/routersploit development by creating an account on github. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Learn hacking routers with routersploit. And the generic modules are for performing generic attacks. The payloads module generates payloads for injection points. Check how vulnerable your router is and how easily it. Routersploit List.
From securitytwins.com
RouterSploit Framework para la auditoría de routers Security Twins Routersploit List Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software. The payloads module generates payloads for injection points. Contribute to threat9/routersploit development by creating an account on github. Check how vulnerable your. Routersploit List.
From miloserdov.org
RouterSploit User Manual Ethical hacking and testing Routersploit List Learn hacking routers with routersploit. Exploitation framework for embedded devices. And the generic modules are for performing generic attacks. Check how vulnerable your router is and how easily it can be hacked with. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. We can check their full list via the search. Routersploit List.
From www.youtube.com
How To Install RouterSploit In Ubuntu/Termux Check The Security Of Routersploit List Exploitation framework for embedded devices. It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software. The payloads module generates payloads for injection points. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Routersploit also provides the ability to bruteforce attack network. Routersploit List.
From www.bilibili.com
安卓手机通过termux免Root运行Routersploit对路由器进行渗透【渗透工具】 哔哩哔哩 Routersploit List We can check their full list via the search bruteforce. It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software. And the generic modules are for performing generic attacks. Contribute to threat9/routersploit development by creating an account on github. Learn hacking routers with routersploit. Routersploit boasts of over 131 scanners. Routersploit List.
From www.kitploit.com
RouterSploit Router Exploitation Framework Routersploit List Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. The payloads module generates payloads for injection points. Learn hacking routers with routersploit. And the generic modules are for performing generic attacks. It is natural that routers or cameras, depending on the version and publisher, have their own flawed versions and software.. Routersploit List.
From gbhackers.com
Exploitation Framework for Embedded devices RouterSploit Routersploit List Check how vulnerable your router is and how easily it can be hacked with. Learn hacking routers with routersploit. Exploitation framework for embedded devices. Routersploit also provides the ability to bruteforce attack network services including, among others, protocols: The payloads module generates payloads for injection points. And the generic modules are for performing generic attacks. It is natural that routers. Routersploit List.
From www.prodefence.org
routersploit v3.2.0 released Router Exploitation Framework Routersploit List Check how vulnerable your router is and how easily it can be hacked with. We can check their full list via the search bruteforce. And the generic modules are for performing generic attacks. Learn hacking routers with routersploit. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Exploitation framework for embedded. Routersploit List.