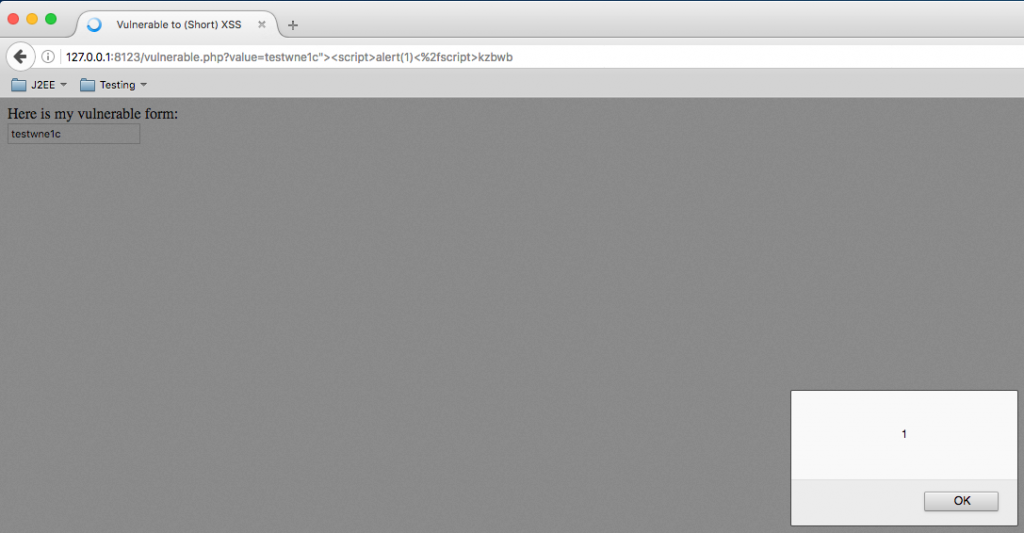
Shorten Xss Payload . this cheat sheet demonstrates that input filtering is an incomplete defense for xss by supplying testers with a series of xss. a collection of short xss payloads that can be used in different contexts. the most obvious method when attempting to beat a filter that truncates your input to a fixed maximum length is to shorten your attack payload by using javascript apis with the shortest possible length and removing characters that are usually included but are strictly unnecessary. the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. having small xss payloads or ways to shorten your payloads ensures that even the smallest unencoded output on a site can still lead to account. i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows.
from www.doyler.net
having small xss payloads or ways to shorten your payloads ensures that even the smallest unencoded output on a site can still lead to account. this cheat sheet demonstrates that input filtering is an incomplete defense for xss by supplying testers with a series of xss. the most obvious method when attempting to beat a filter that truncates your input to a fixed maximum length is to shorten your attack payload by using javascript apis with the shortest possible length and removing characters that are usually included but are strictly unnecessary. i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. a collection of short xss payloads that can be used in different contexts.
Short XSS Pwning your Browser in 30 Characters or Less
Shorten Xss Payload i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. a collection of short xss payloads that can be used in different contexts. having small xss payloads or ways to shorten your payloads ensures that even the smallest unencoded output on a site can still lead to account. the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. this cheat sheet demonstrates that input filtering is an incomplete defense for xss by supplying testers with a series of xss. i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. the most obvious method when attempting to beat a filter that truncates your input to a fixed maximum length is to shorten your attack payload by using javascript apis with the shortest possible length and removing characters that are usually included but are strictly unnecessary.
From research.digitalinterruption.com
A Deeper Look into XSS Payloads Digital Interruption Research Shorten Xss Payload the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. the most obvious method when attempting to beat a filter that truncates. Shorten Xss Payload.
From www.scribd.com
XSS Payloads Cheat Sheet PDF Html Element Java Script Shorten Xss Payload having small xss payloads or ways to shorten your payloads ensures that even the smallest unencoded output on a site can still lead to account. the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. i found an xss vulnerability on a large site, and i want to report. Shorten Xss Payload.
From www.hacking.land
XSSLOADER XSS Payload Generator / XSS Scanner / XSS Dork Finder Shorten Xss Payload i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. this cheat sheet demonstrates that input filtering is an incomplete defense for. Shorten Xss Payload.
From www.geeksforgeeks.org
XSSLoader XSS Scanner and Payload Generator Shorten Xss Payload i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. the most obvious method when attempting to beat a filter that truncates your input to a fixed maximum length is to shorten your attack payload by using javascript apis with the. Shorten Xss Payload.
From securityonline.info
XSS Chef generating custom XSS payloads Shorten Xss Payload a collection of short xss payloads that can be used in different contexts. the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only. Shorten Xss Payload.
From nhattruong.blog
XSS Polyglots Test multiple XSS scenarios with ONE payload. Nhat Shorten Xss Payload having small xss payloads or ways to shorten your payloads ensures that even the smallest unencoded output on a site can still lead to account. the most obvious method when attempting to beat a filter that truncates your input to a fixed maximum length is to shorten your attack payload by using javascript apis with the shortest possible. Shorten Xss Payload.
From www.kitploit.com
XSSLOADER XSS Payload Generator / XSS Scanner / XSS Dork Finder Shorten Xss Payload the most obvious method when attempting to beat a filter that truncates your input to a fixed maximum length is to shorten your attack payload by using javascript apis with the shortest possible length and removing characters that are usually included but are strictly unnecessary. i found an xss vulnerability on a large site, and i want to. Shorten Xss Payload.
From techkynotes.blogspot.com
Using Burp Suite Brute Force payloads using XSS Validator(Extension Shorten Xss Payload i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. this cheat sheet demonstrates that input filtering is an incomplete defense for xss by supplying testers with a series of xss. the most obvious method when attempting to beat a. Shorten Xss Payload.
From github.com
XSS_Cheat_Sheet_2020_Edition/xss_payload_list.txt at master Shorten Xss Payload a collection of short xss payloads that can be used in different contexts. having small xss payloads or ways to shorten your payloads ensures that even the smallest unencoded output on a site can still lead to account. i found an xss vulnerability on a large site, and i want to report it, but the only limit. Shorten Xss Payload.
From www.whiteoaksecurity.com
Blind XSS & GCP Functions GCPXSSCanary White Oak Security Shorten Xss Payload having small xss payloads or ways to shorten your payloads ensures that even the smallest unencoded output on a site can still lead to account. the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. this cheat sheet demonstrates that input filtering is an incomplete defense for xss by. Shorten Xss Payload.
From www.doyler.net
Short XSS Pwning your Browser in 30 Characters or Less Shorten Xss Payload a collection of short xss payloads that can be used in different contexts. the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only. Shorten Xss Payload.
From github.com
xsspayloads/xsspayloadlist.html at master · andrysec/xsspayloads Shorten Xss Payload this cheat sheet demonstrates that input filtering is an incomplete defense for xss by supplying testers with a series of xss. a collection of short xss payloads that can be used in different contexts. the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. having small xss payloads. Shorten Xss Payload.
From github.com
GitHub agentjacker/AdvancedXSSPayloads Advanced XSS Payloads that Shorten Xss Payload a collection of short xss payloads that can be used in different contexts. i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. the poc payload was enough to demonstrate that somebody with a short domain name could exploit the. Shorten Xss Payload.
From exploit.ph
eXploit Reflected XSS at PentesterAcademy Shorten Xss Payload a collection of short xss payloads that can be used in different contexts. the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. the most obvious method when attempting to beat a filter that truncates your input to a fixed maximum length is to shorten your attack payload by. Shorten Xss Payload.
From www.kitploit.com
XSSLOADER XSS Payload Generator / XSS Scanner / XSS Dork Finder Shorten Xss Payload a collection of short xss payloads that can be used in different contexts. i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. the most obvious method when attempting to beat a filter that truncates your input to a fixed. Shorten Xss Payload.
From www.doyler.net
Short XSS Pwning your Browser in 30 Characters or Less Shorten Xss Payload i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. a collection of short xss payloads that can be used in different contexts. the poc payload was enough to demonstrate that somebody with a short domain name could exploit the. Shorten Xss Payload.
From zhuanlan.zhihu.com
XSS常见payload 知乎 Shorten Xss Payload the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. a collection of short xss payloads that can be used in different contexts. this cheat sheet demonstrates that input filtering is an incomplete defense for xss by supplying testers with a series of xss. the most obvious method. Shorten Xss Payload.
From techkynotes.blogspot.com
Using Burp Suite Brute Force payloads using XSS Validator(Extension Shorten Xss Payload this cheat sheet demonstrates that input filtering is an incomplete defense for xss by supplying testers with a series of xss. having small xss payloads or ways to shorten your payloads ensures that even the smallest unencoded output on a site can still lead to account. a collection of short xss payloads that can be used in. Shorten Xss Payload.
From jardel.tec.br
Coleção de Payloads para XSS Cybersec Spot Shorten Xss Payload i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. having small xss payloads or ways to shorten your payloads ensures that even the smallest unencoded output on a site can still lead to account. the poc payload was enough. Shorten Xss Payload.
From www.reddit.com
Revisiting XSS payloads in PNG IDAT chunks Shorten Xss Payload a collection of short xss payloads that can be used in different contexts. having small xss payloads or ways to shorten your payloads ensures that even the smallest unencoded output on a site can still lead to account. the most obvious method when attempting to beat a filter that truncates your input to a fixed maximum length. Shorten Xss Payload.
From www.kitploit.com
XSSLOADER XSS Payload Generator / XSS Scanner / XSS Dork Finder Shorten Xss Payload this cheat sheet demonstrates that input filtering is an incomplete defense for xss by supplying testers with a series of xss. i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. the poc payload was enough to demonstrate that somebody. Shorten Xss Payload.
From www.jianshu.com
XSS深入分析 简书 Shorten Xss Payload i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. this cheat sheet demonstrates that input filtering is an incomplete defense for xss by supplying testers with a series of xss. a collection of short xss payloads that can be. Shorten Xss Payload.
From github.com
xsspayloadlist/LICENSE at master · payloadbox/xsspayloadlist · GitHub Shorten Xss Payload i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. a collection of short xss payloads that can be used in different contexts. the most obvious method when attempting to beat a filter that truncates your input to a fixed. Shorten Xss Payload.
From github.com
GitHub pgaijin66/XSSPayloads This repository holds all the list of Shorten Xss Payload having small xss payloads or ways to shorten your payloads ensures that even the smallest unencoded output on a site can still lead to account. this cheat sheet demonstrates that input filtering is an incomplete defense for xss by supplying testers with a series of xss. the most obvious method when attempting to beat a filter that. Shorten Xss Payload.
From github.com
xss payload when devloper block alert method · Issue 40 · PortSwigger Shorten Xss Payload the most obvious method when attempting to beat a filter that truncates your input to a fixed maximum length is to shorten your attack payload by using javascript apis with the shortest possible length and removing characters that are usually included but are strictly unnecessary. i found an xss vulnerability on a large site, and i want to. Shorten Xss Payload.
From www.vaadata.com
XSS Principles, Attacks and Security Best Practices Shorten Xss Payload i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. a collection of short xss payloads that can be used in different contexts. having small xss payloads or ways to shorten your payloads ensures that even the smallest unencoded output. Shorten Xss Payload.
From www.youtube.com
Xss Payload Generator Xss Scanner Xss Dork Finder YouTube Shorten Xss Payload the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. the most obvious method when attempting to beat a filter that truncates. Shorten Xss Payload.
From awesomeopensource.com
Xss Catcher Shorten Xss Payload having small xss payloads or ways to shorten your payloads ensures that even the smallest unencoded output on a site can still lead to account. i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. the poc payload was enough. Shorten Xss Payload.
From blog.csdn.net
Guide to understanding XSS XSS payloads, attack vectors, BeEF hooking Shorten Xss Payload the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. this cheat sheet demonstrates that input filtering is an incomplete defense for. Shorten Xss Payload.
From www.youtube.com
How to build XSS payloads CrossSite Scripting(XSS) Tutorial Shorten Xss Payload i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only allows. this cheat sheet demonstrates that input filtering is an incomplete defense for xss by supplying testers with a series of xss. the poc payload was enough to demonstrate that somebody. Shorten Xss Payload.
From www.devzery.com
XSS Payloads A Comprehensive Guide to Protection Shorten Xss Payload the most obvious method when attempting to beat a filter that truncates your input to a fixed maximum length is to shorten your attack payload by using javascript apis with the shortest possible length and removing characters that are usually included but are strictly unnecessary. i found an xss vulnerability on a large site, and i want to. Shorten Xss Payload.
From www.doyler.net
Short XSS Pwning your Browser in 30 Characters or Less Shorten Xss Payload a collection of short xss payloads that can be used in different contexts. the most obvious method when attempting to beat a filter that truncates your input to a fixed maximum length is to shorten your attack payload by using javascript apis with the shortest possible length and removing characters that are usually included but are strictly unnecessary.. Shorten Xss Payload.
From twitter.com
HackGit on Twitter "TinyXSSPayloads A collection of tiny XSS Shorten Xss Payload the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. a collection of short xss payloads that can be used in different contexts. the most obvious method when attempting to beat a filter that truncates your input to a fixed maximum length is to shorten your attack payload by. Shorten Xss Payload.
From cloud.tencent.com
一篇文章带你从XSS入门到进阶(附Fuzzing+BypassWAF+Payloads)腾讯云开发者社区腾讯云 Shorten Xss Payload a collection of short xss payloads that can be used in different contexts. the poc payload was enough to demonstrate that somebody with a short domain name could exploit the xss. i found an xss vulnerability on a large site, and i want to report it, but the only limit to the vulnerability is that it only. Shorten Xss Payload.