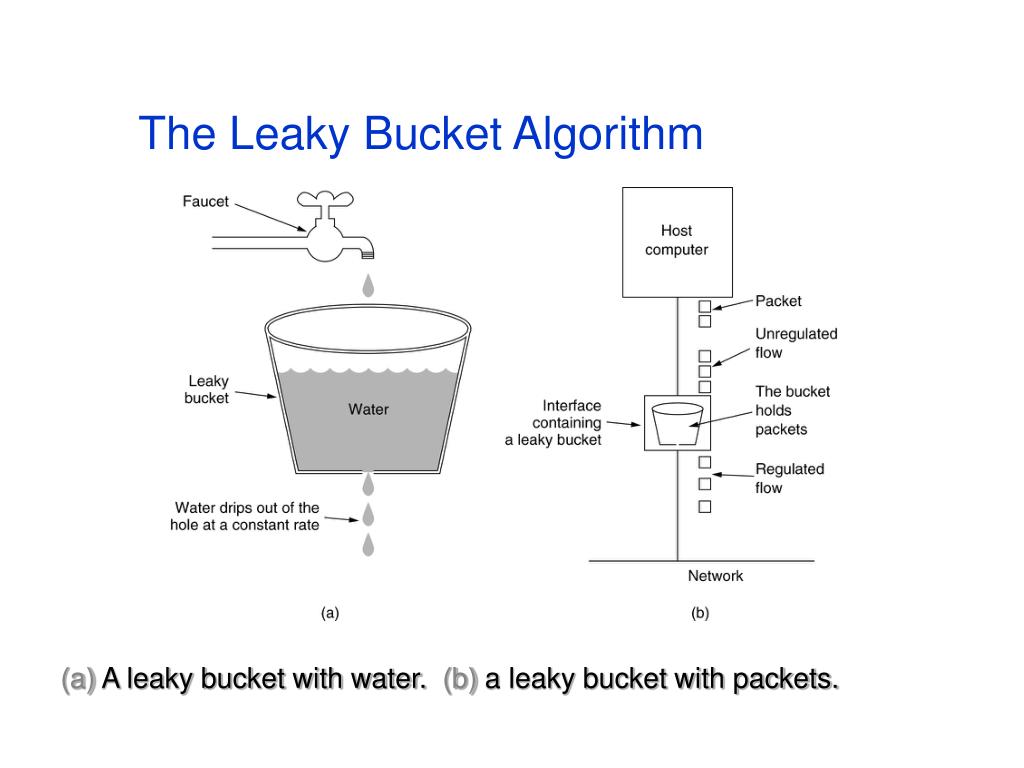
Leaky Bucket Algorithm Diagram . The leaky bucket algorithm is a network traffic management mechanism used to control the. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. It operates like a leaky bucket,. Picture a bucket with a. Step 1 − let us imagine a bucket with a small hole at the bottom where the rate at which water is poured into the bucket is not. Bursty chunks of traffic are stored in a bucket. What is the leaky bucket algorithm? The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network traffic. If you’re studying for gate. Flow diagram for leaky bucket algorithm. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic.
from www.slideserve.com
If you’re studying for gate. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. It operates like a leaky bucket,. Picture a bucket with a. Flow diagram for leaky bucket algorithm. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Step 1 − let us imagine a bucket with a small hole at the bottom where the rate at which water is poured into the bucket is not. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Bursty chunks of traffic are stored in a bucket. What is the leaky bucket algorithm?
PPT Flow Control PowerPoint Presentation, free download ID418287
Leaky Bucket Algorithm Diagram The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network traffic. Step 1 − let us imagine a bucket with a small hole at the bottom where the rate at which water is poured into the bucket is not. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. What is the leaky bucket algorithm? If you’re studying for gate. Bursty chunks of traffic are stored in a bucket. It operates like a leaky bucket,. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. The leaky bucket algorithm is a network traffic management mechanism used to control the. Picture a bucket with a. Flow diagram for leaky bucket algorithm.
From www.tech-maze.info
System Design Leaky Bucket Algorithm And Its UsesSystem Design Rohit Modi Leaky Bucket Algorithm Diagram If you’re studying for gate. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It operates like a leaky bucket,. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. What is the leaky bucket algorithm? Picture a bucket with a. Flow diagram. Leaky Bucket Algorithm Diagram.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Scientific Diagram Leaky Bucket Algorithm Diagram Picture a bucket with a. If you’re studying for gate. Step 1 − let us imagine a bucket with a small hole at the bottom where the rate at which water is poured into the bucket is not. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Bursty chunks of traffic are. Leaky Bucket Algorithm Diagram.
From www.rdiachenko.com
Exploring and Implementing the Leaky Bucket Rate Limiting Algorithm Leaky Bucket Algorithm Diagram The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It operates like a leaky bucket,. What is the leaky bucket algorithm? The leaky bucket algorithm is a network traffic management mechanism used to control the. Flow diagram for leaky bucket algorithm. Picture a bucket with a. Step. Leaky Bucket Algorithm Diagram.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Diagram Flow diagram for leaky bucket algorithm. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. It operates like a leaky bucket,. Picture a bucket with a. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. If you’re studying for gate. The leaky. Leaky Bucket Algorithm Diagram.
From www.researchgate.net
Leaky bucket approach. Download Scientific Diagram Leaky Bucket Algorithm Diagram The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Flow diagram for leaky bucket algorithm. If you’re studying for gate. The leaky bucket algorithm provides an elegant solution to the. Leaky Bucket Algorithm Diagram.
From www.youtube.com
Leaky Bucket Algorithm Token Bucket Algorithm Leaky Bucket Vs Token Bucket Congestion Leaky Bucket Algorithm Diagram The leaky bucket algorithm is a network traffic management mechanism used to control the. What is the leaky bucket algorithm? It operates like a leaky bucket,. If you’re studying for gate. Picture a bucket with a. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Step 1 − let us imagine a bucket with a. Leaky Bucket Algorithm Diagram.
From www.slideserve.com
PPT Flow Control PowerPoint Presentation, free download ID418287 Leaky Bucket Algorithm Diagram If you’re studying for gate. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. The leaky bucket algorithm is a network traffic management mechanism used to control the. Picture a bucket with a. What is the leaky bucket. Leaky Bucket Algorithm Diagram.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Algorithm Diagram If you’re studying for gate. The leaky bucket algorithm is a network traffic management mechanism used to control the. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network. Leaky Bucket Algorithm Diagram.
From www.researchgate.net
Intelligent leaky bucket algorithm. Download Scientific Diagram Leaky Bucket Algorithm Diagram If you’re studying for gate. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Flow diagram for leaky bucket algorithm. Picture a bucket with a. Step 1 − let us imagine a bucket with a small hole at the bottom where the rate at which water is poured into the bucket is not. It operates. Leaky Bucket Algorithm Diagram.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm Diagram Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network traffic. Step 1 − let us imagine a bucket with a small hole at the bottom where the rate at which water is poured into the bucket is not. If you’re studying for. Leaky Bucket Algorithm Diagram.
From conceptdraw.com
Leaky bucket diagram Leaky Bucket Algorithm Diagram What is the leaky bucket algorithm? Picture a bucket with a. Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network traffic. Bursty chunks of traffic are stored in a bucket. It operates like a leaky bucket,. If you’re studying for gate. The. Leaky Bucket Algorithm Diagram.
From www.researchgate.net
Algorithm to Implement the Leaky Bucket and the Token Bucket Download Scientific Diagram Leaky Bucket Algorithm Diagram Flow diagram for leaky bucket algorithm. If you’re studying for gate. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Step 1 − let us imagine a bucket with a small hole at. Leaky Bucket Algorithm Diagram.
From www.thetechnicaltalk.com
Differentiate between leaky bucket and token bucket methods of traffic shaping The Technical Talk Leaky Bucket Algorithm Diagram Picture a bucket with a. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Flow diagram for leaky bucket algorithm. Bursty chunks of traffic are stored in a bucket. It. Leaky Bucket Algorithm Diagram.
From www.researchgate.net
Mean queueing delay of the conventional leaky bucket algorithm, the... Download Scientific Diagram Leaky Bucket Algorithm Diagram The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. If you’re studying for gate. Flow diagram for leaky bucket algorithm. Just like a hole at the bottom of a water bucket leaks water out at a fixed rate,. Leaky Bucket Algorithm Diagram.
From www.youtube.com
Leaky And Token Bucket Algorithms YouTube Leaky Bucket Algorithm Diagram What is the leaky bucket algorithm? The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Picture a bucket with a. If you’re studying for gate. Step 1 − let us imagine a bucket with a small hole at the bottom where the rate at which water is poured into the bucket is not. Flow diagram. Leaky Bucket Algorithm Diagram.
From www.researchgate.net
2. Optimal control tokenbucket algorithm flowchart (part 1). Download Scientific Diagram Leaky Bucket Algorithm Diagram The leaky bucket algorithm is a network traffic management mechanism used to control the. Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network traffic. It operates like a leaky bucket,. Bursty chunks of traffic are stored in a bucket. Step 1 −. Leaky Bucket Algorithm Diagram.
From www.researchgate.net
Selectivity of the conventional leaky bucket algorithm, the fuzzy leaky... Download Scientific Leaky Bucket Algorithm Diagram Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network traffic. The leaky bucket algorithm is a network traffic management mechanism used to control the. Bursty chunks of traffic are stored in a bucket. Step 1 − let us imagine a bucket with. Leaky Bucket Algorithm Diagram.
From www.youtube.com
Leaky bucket and Token bucket with GATE PYQs. Clear Explanation YouTube Leaky Bucket Algorithm Diagram The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. It operates like a leaky bucket,. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Step 1 − let us imagine a bucket with a small hole at the bottom where the rate at which water is poured. Leaky Bucket Algorithm Diagram.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket Algorithm Diagram If you’re studying for gate. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Flow diagram for leaky bucket algorithm. Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network traffic. Picture a bucket with. Leaky Bucket Algorithm Diagram.
From songhayoung.github.io
[System Design] Leaky bucket / token bucket SUMFIのBlog Leaky Bucket Algorithm Diagram The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. If you’re studying for gate. Step 1 − let us imagine a bucket with a small hole at the bottom where the rate at which water is poured into the bucket is not. What is the leaky bucket algorithm? The leaky bucket algorithm. Leaky Bucket Algorithm Diagram.
From www.researchgate.net
Responsiveness of the conventional leaky bucket algorithm, the fuzzy... Download Scientific Leaky Bucket Algorithm Diagram If you’re studying for gate. Picture a bucket with a. Bursty chunks of traffic are stored in a bucket. Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network traffic. It operates like a leaky bucket,. The leaky bucket algorithm is a network. Leaky Bucket Algorithm Diagram.
From www.researchgate.net
The Packet leaky Bucket Algorithm marked with low priority (maximum... Download Scientific Diagram Leaky Bucket Algorithm Diagram The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. If you’re studying for gate. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Step 1 − let us imagine a bucket with a small hole at the bottom where the rate at. Leaky Bucket Algorithm Diagram.
From in.pinterest.com
Leaky Bucket Algorithm educlick Algorithm, Computer network, Networking Leaky Bucket Algorithm Diagram If you’re studying for gate. What is the leaky bucket algorithm? Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network traffic. Bursty chunks of traffic are stored in a bucket. Picture a bucket with a. The leaky bucket algorithm is a simple. Leaky Bucket Algorithm Diagram.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and closed loop) YouTube Leaky Bucket Algorithm Diagram What is the leaky bucket algorithm? The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Step 1 − let us imagine a bucket with a small hole at the bottom where the rate at which water is poured into the bucket is not. It operates like a. Leaky Bucket Algorithm Diagram.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Scientific Diagram Leaky Bucket Algorithm Diagram Picture a bucket with a. What is the leaky bucket algorithm? Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network traffic. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. If you’re studying for. Leaky Bucket Algorithm Diagram.
From www.youtube.com
Traffic Shaping Leaky Bucket Token Bucket Improve QoS Computer Networks Part 3 YouTube Leaky Bucket Algorithm Diagram If you’re studying for gate. What is the leaky bucket algorithm? The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network. Leaky Bucket Algorithm Diagram.
From www.youtube.com
Leaky Bucket vs Token Bucket Algorithm Leaky Bucket and Token Bucket Difference YouTube Leaky Bucket Algorithm Diagram Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network traffic. Bursty chunks of traffic are stored in a bucket. What is the leaky bucket algorithm? The leaky bucket algorithm is a network traffic management mechanism used to control the. Flow diagram for. Leaky Bucket Algorithm Diagram.
From lowleveldesign.io
Design a Distributed Scalable API Rate Limiter Leaky Bucket Algorithm Diagram Flow diagram for leaky bucket algorithm. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. The leaky bucket algorithm is a network traffic management mechanism used to control the. Bursty chunks of traffic are stored in a bucket. Step 1 − let us imagine a bucket with. Leaky Bucket Algorithm Diagram.
From www.rdiachenko.com
Exploring and Implementing the Leaky Bucket Rate Limiting Algorithm Leaky Bucket Algorithm Diagram If you’re studying for gate. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Flow diagram for leaky bucket algorithm. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Picture a bucket with a. Step 1 − let us. Leaky Bucket Algorithm Diagram.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Diagram The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. If you’re studying for gate. Bursty chunks of traffic are stored in a bucket. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It operates like a leaky bucket,. Flow. Leaky Bucket Algorithm Diagram.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Algorithm Diagram The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. If you’re studying for gate. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Flow diagram for leaky bucket algorithm. It operates like a leaky bucket,. Bursty chunks of traffic are stored in a bucket. Picture a bucket. Leaky Bucket Algorithm Diagram.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm Diagram If you’re studying for gate. The leaky bucket algorithm is a network traffic management mechanism used to control the. Picture a bucket with a. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. It operates like a leaky bucket,. What is the leaky bucket algorithm? The leaky bucket algorithm is a traffic. Leaky Bucket Algorithm Diagram.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID4138688 Leaky Bucket Algorithm Diagram If you’re studying for gate. Flow diagram for leaky bucket algorithm. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network. Leaky Bucket Algorithm Diagram.
From www.researchgate.net
Responsiveness of the conventional leaky bucket algorithm, the fuzzy... Download Scientific Leaky Bucket Algorithm Diagram The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Just like a hole at the bottom. Leaky Bucket Algorithm Diagram.
From www.thetechnicaltalk.com
Differentiate between leaky bucket and token bucket methods of traffic shaping The Technical Talk Leaky Bucket Algorithm Diagram It operates like a leaky bucket,. If you’re studying for gate. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Just like a hole at the bottom of a water bucket leaks water out at a fixed rate, the leaky bucket algorithm does the same with network traffic. The leaky bucket algorithm is a simple. Leaky Bucket Algorithm Diagram.