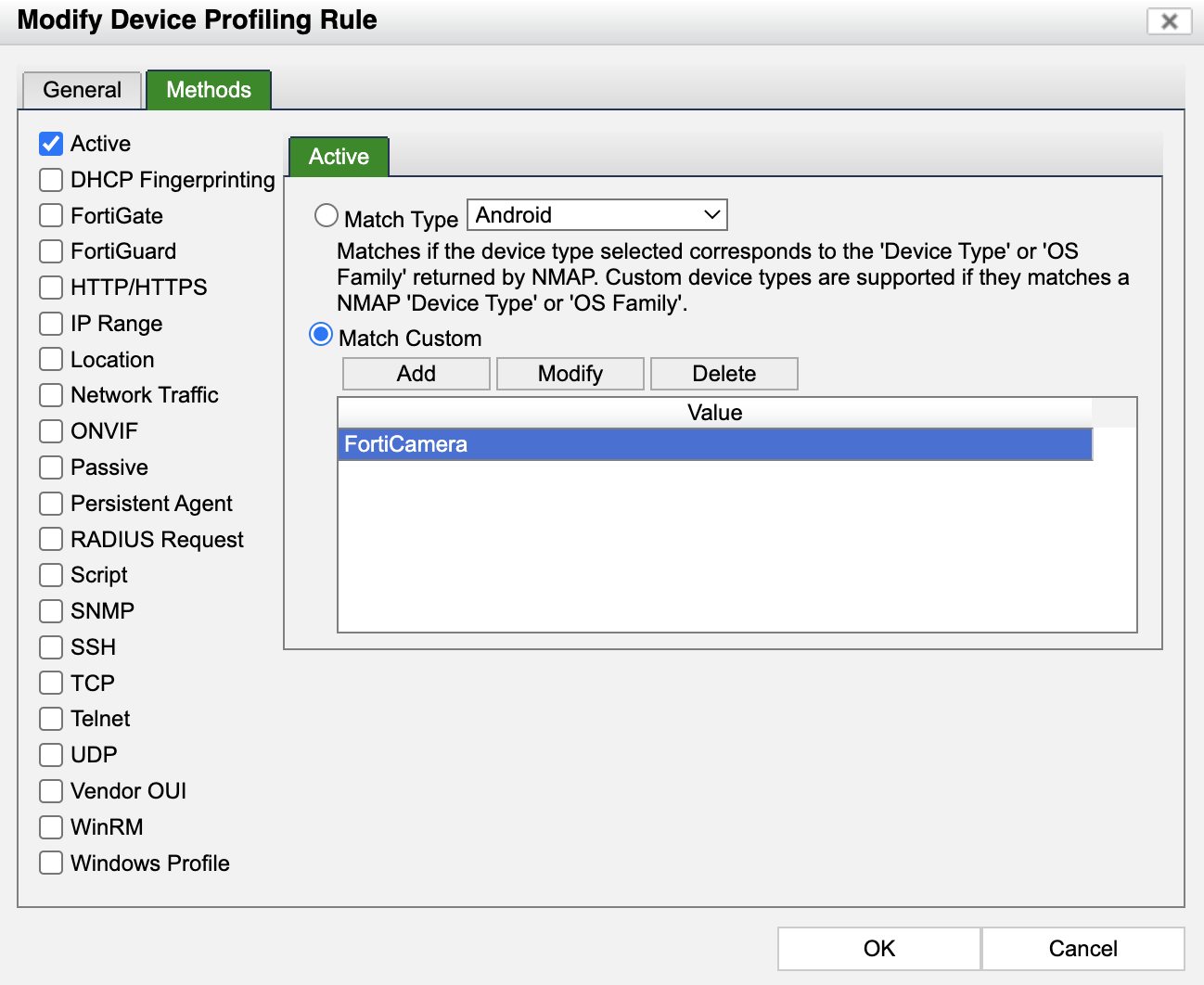
Fortinac Profiling Methods . the most commonly used methods are provided below: it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. In this section, we will create the profile definitions for iot. fortinac supports up to 26 methods of device profiling; fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices and iot. first, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately. the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. This method is beneficial in ot environments and for.
from docs.fortinet.com
the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices and iot. the most commonly used methods are provided below: In this section, we will create the profile definitions for iot. first, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately. This method is beneficial in ot environments and for. device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. fortinac supports up to 26 methods of device profiling;
Profiling IoT Devices FortiNACF 7.2.0
Fortinac Profiling Methods In this section, we will create the profile definitions for iot. device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. In this section, we will create the profile definitions for iot. fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices and iot. it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. This method is beneficial in ot environments and for. the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. the most commonly used methods are provided below: first, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately. fortinac supports up to 26 methods of device profiling;
From fortixpert.blogspot.com
Blog Técnico Nuevo FortiNACF Fortinac Profiling Methods the most commonly used methods are provided below: In this section, we will create the profile definitions for iot. device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as. Fortinac Profiling Methods.
From docs.fortinet.com
How it Works FortiNACF 7.2.0 Document Library Fortinac Profiling Methods it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. fortinac supports up to 26 methods of device profiling; fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices and iot. the most. Fortinac Profiling Methods.
From docs.fortinet.com
Profiling IoT Devices FortiNACF 7.2.0 Fortinac Profiling Methods This method is beneficial in ot environments and for. first, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately. device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. the most commonly used methods are provided below: In this section, we. Fortinac Profiling Methods.
From www.csoonline.com
Securing IoT devices FortiNAC automates the process CSO Fortinac Profiling Methods the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. fortinac supports up to 26 methods of device profiling; it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. In. Fortinac Profiling Methods.
From www.scribd.com
FortiNAC FortiSwitch Integration Guide PDF Radius Computer Network Fortinac Profiling Methods device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. In this section, we will create the profile definitions for iot. it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. first, it enables. Fortinac Profiling Methods.
From docs.fortinet.com
Integration with FortiNAC FortiDeceptor 5.0.0 Fortinac Profiling Methods In this section, we will create the profile definitions for iot. device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. the most commonly used methods are provided below: fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices. Fortinac Profiling Methods.
From www.scribd.com
FortiNAC 8.5 Study PDF Radius Domain Name System Fortinac Profiling Methods This method is beneficial in ot environments and for. the most commonly used methods are provided below: fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices and iot. it scans the host database for rogues with ip addresses and assigns them a device type based on profiles. Fortinac Profiling Methods.
From docs.fortinet.com
Integration with FortiNAC FortiDeceptor 5.1.0 Document Library Fortinac Profiling Methods fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices and iot. the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. it scans the host database for rogues with ip addresses and assigns them. Fortinac Profiling Methods.
From www.scribd.com
FortiNAC v9.4 CSE HOL Lab Guide PDF PDF Radius Port Fortinac Profiling Methods it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. the most commonly used methods are provided below: device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. This method is beneficial in ot. Fortinac Profiling Methods.
From docs.fortinet.com
Integration with FortiNAC FortiDeceptor 5.0.0 Fortinac Profiling Methods device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. first, it enables detailed profiling of even headless devices using multiple information and behavior. Fortinac Profiling Methods.
From www.avfirewalls.com
FortiNAC CA500F Fortinac Profiling Methods the most commonly used methods are provided below: first, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately. the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. it scans the host database for rogues with. Fortinac Profiling Methods.
From docs.fortinet.com
Profiling IoT Devices FortiNACF 7.2.0 Fortinac Profiling Methods fortinac supports up to 26 methods of device profiling; the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. In. Fortinac Profiling Methods.
From www.youtube.com
FortiNAC Network Setup and Isolation Networks Configuration Explained Fortinac Profiling Methods the most commonly used methods are provided below: it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. fortinac. Fortinac Profiling Methods.
From fortixpert.blogspot.com
Blog Técnico Nuevo FortiNACF Fortinac Profiling Methods the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. first, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately. device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to. Fortinac Profiling Methods.
From docs.fortinet.com
Add an admin profile FortiNAC 8.5.0 Fortinac Profiling Methods the most commonly used methods are provided below: fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices and iot. fortinac supports up to 26 methods of device profiling; first, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately. In. Fortinac Profiling Methods.
From www.feenixbloom.com
'The Fortinac Persistent Agent What Is It And How to Keep Your App Fortinac Profiling Methods it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. This method is beneficial in ot environments and for. the device profiler feature in. Fortinac Profiling Methods.
From docs.fortinet.com
FortiSIEM Integration FortiNAC 9.4.0 Fortinac Profiling Methods the most commonly used methods are provided below: it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. first, it enables detailed profiling. Fortinac Profiling Methods.
From www.avfirewalls.com
FortiNAC M550F Fortinac Profiling Methods fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices and iot. This method is beneficial in ot environments and for. it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. first, it enables. Fortinac Profiling Methods.
From docs.fortinet.com
Replace FSSObased FortiNAC tag connector with REST API 7.0.4 Fortinac Profiling Methods first, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately. fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices and iot. the most commonly used methods are provided below: it scans the host database for rogues with ip addresses. Fortinac Profiling Methods.
From docs.fortinet.com
Profiling IoT Devices FortiNACF 7.2.0 Fortinac Profiling Methods first, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately. the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. the most commonly used methods are provided below: fortinac leverages ai and machine learning from fortiguard. Fortinac Profiling Methods.
From docs.fortinet.com
Integration with FortiNAC FortiDeceptor 5.1.0 Document Library Fortinac Profiling Methods This method is beneficial in ot environments and for. fortinac supports up to 26 methods of device profiling; fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices and iot. In this section, we will create the profile definitions for iot. first, it enables detailed profiling of even. Fortinac Profiling Methods.
From www.youtube.com
Fortinac Configuring SelfGuest Registration on FortiNAC Easy Setup Fortinac Profiling Methods In this section, we will create the profile definitions for iot. This method is beneficial in ot environments and for. the most commonly used methods are provided below: it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. fortinac leverages ai and machine. Fortinac Profiling Methods.
From www.youtube.com
Part 2 FortiNAC Initial Setup YouTube Fortinac Profiling Methods first, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately. In this section, we will create the profile definitions for iot. device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. This method is beneficial in ot environments and for. the. Fortinac Profiling Methods.
From sanet.st
Fortinac Lab Beginner To Expert SoftArchive Fortinac Profiling Methods first, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately. it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. device profiling rules are used by the device profiler feature to categorize rogue hosts that connect. Fortinac Profiling Methods.
From docs.fortinet.com
Profiling IoT Devices FortiNACF 7.2.0 Fortinac Profiling Methods it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. This method is beneficial in ot environments and for. fortinac supports up to 26 methods of device profiling; fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of. Fortinac Profiling Methods.
From docs.fortinet.com
Layer 3 FortiNACF 7.2.0 Fortinac Profiling Methods fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices and iot. first, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately. device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network.. Fortinac Profiling Methods.
From 591cert.com
NSE6 FortiNAC 7.2 Exam NSE6FNC(7.2) 591 Lab Fortinac Profiling Methods fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices and iot. device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. first, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately.. Fortinac Profiling Methods.
From studylib.net
FortiNAC Persistent Agent Deployment and Configuration Fortinac Profiling Methods fortinac supports up to 26 methods of device profiling; it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. the most commonly used methods are provided below: This method is beneficial in ot environments and for. the device profiler feature in fortinac. Fortinac Profiling Methods.
From www.thenetworkdna.com
Leveraging FortiNAC to Strengthen Compliance with Industry Regulations Fortinac Profiling Methods fortinac supports up to 26 methods of device profiling; the most commonly used methods are provided below: the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices,. Fortinac Profiling Methods.
From acora.com
FortiNAC Network Access Control solution from Fortinac Profiling Methods fortinac supports up to 26 methods of device profiling; fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices and iot. device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. the most commonly used methods are provided. Fortinac Profiling Methods.
From docs.fortinet.com
Profiling IoT Devices FortiNACF 7.2.0 Fortinac Profiling Methods In this section, we will create the profile definitions for iot. the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. fortinac supports up to 26 methods of device profiling; This method is beneficial in ot environments and for. first, it enables detailed profiling. Fortinac Profiling Methods.
From www.emerald.com.vn
FORTINAC SECURITY FOR NETWORKS WITH IOT Fortinac Profiling Methods the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. the most commonly used methods are provided below: it scans the host database for rogues with ip addresses and assigns them a device type based on profiles or rules set up in. In this. Fortinac Profiling Methods.
From docs.fortinet.com
Profiling IoT Devices FortiNACF 7.2.0 Fortinac Profiling Methods device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. first, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately. This method is beneficial in ot environments and for. the device profiler feature in fortinac is used to classify unknown (rogue). Fortinac Profiling Methods.
From docs.fortinet.com
Ataglance visibility for profiled devices FortiNACF 7.2.0 Fortinac Profiling Methods device profiling rules are used by the device profiler feature to categorize rogue hosts that connect to the network. the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. it scans the host database for rogues with ip addresses and assigns them a device. Fortinac Profiling Methods.
From docs.fortinet.com
Profiling OT manufacturing devices FortiNACF 7.2.0 Fortinac Profiling Methods fortinac leverages ai and machine learning from fortiguard security services to provide detailed profiling of devices, including headless devices and iot. fortinac supports up to 26 methods of device profiling; the device profiler feature in fortinac is used to classify unknown (rogue) devices by using multiple different methods as criteria to register the. the most commonly. Fortinac Profiling Methods.