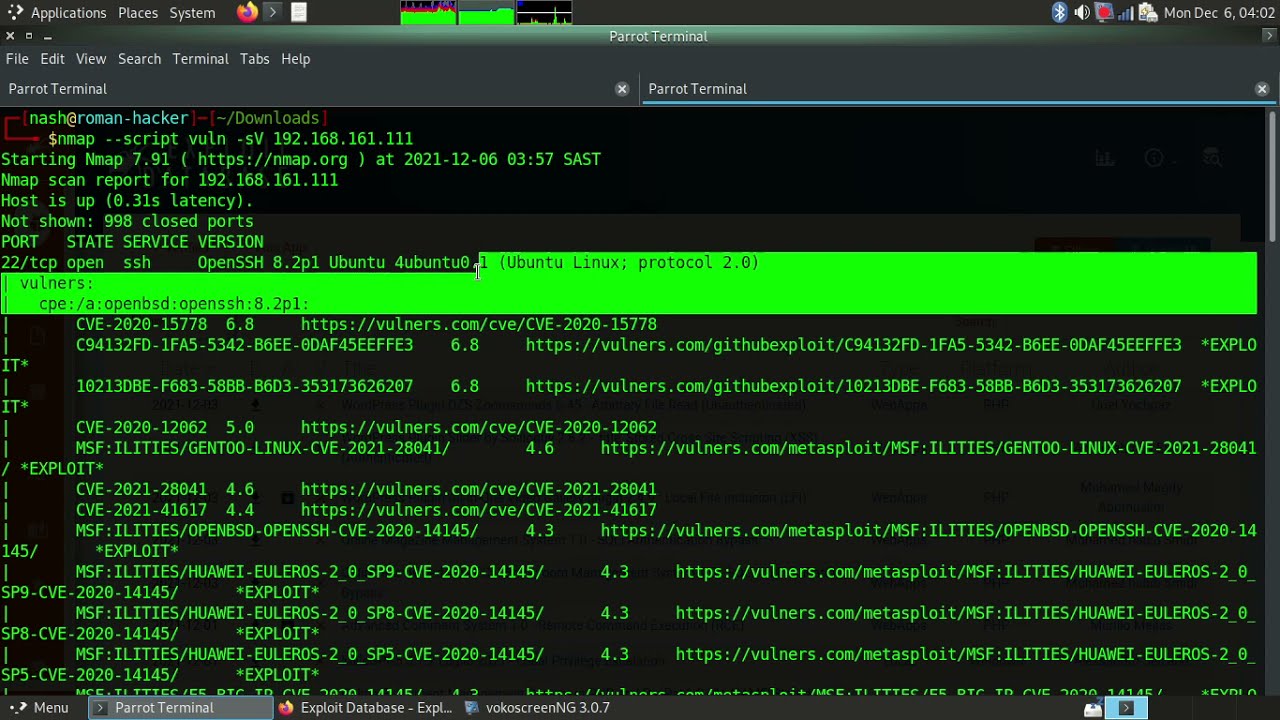
Vulnerability Scanner Command Line . It can be used to find vulnerabilities. Trivy has scanners that look for security issues, and targets where. In this article, we’ll look at how to use nmap for vulnerability scan. Running a vulnerability scan with vulscan requires two components: After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a host, and detect operating. Through the power of the nmap scripting engine (nse), it can be. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. You should have written permission before you ever try to scan a system or network. Nmap started as a simple network scanning command line tool.
from www.youtube.com
In this article, we’ll look at how to use nmap for vulnerability scan. You should have written permission before you ever try to scan a system or network. Nmap started as a simple network scanning command line tool. Trivy has scanners that look for security issues, and targets where. Through the power of the nmap scripting engine (nse), it can be. Running a vulnerability scan with vulscan requires two components: It can be used to find vulnerabilities. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a host, and detect operating. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner.
How to scan for vulnerabilities(CVE) using nmap YouTube
Vulnerability Scanner Command Line 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Nmap started as a simple network scanning command line tool. Trivy has scanners that look for security issues, and targets where. You should have written permission before you ever try to scan a system or network. It can be used to find vulnerabilities. Through the power of the nmap scripting engine (nse), it can be. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a host, and detect operating. Running a vulnerability scan with vulscan requires two components: In this article, we’ll look at how to use nmap for vulnerability scan. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner.
From blog.aquasec.com
Trivy Vulnerability Scanner Joins the Aqua Opensource Family Vulnerability Scanner Command Line Running a vulnerability scan with vulscan requires two components: Nmap started as a simple network scanning command line tool. It can be used to find vulnerabilities. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on. Vulnerability Scanner Command Line.
From blah.cloud
Scanning for network vulnerabilities using nmap Blah, Cloud Vulnerability Scanner Command Line Trivy has scanners that look for security issues, and targets where. In this article, we’ll look at how to use nmap for vulnerability scan. You should have written permission before you ever try to scan a system or network. It can be used to find vulnerabilities. Running a vulnerability scan with vulscan requires two components: 40 rows trivy (pronunciation) is. Vulnerability Scanner Command Line.
From www.manageengine.com
Linux Vulnerability Scanner Scan Linux Server for Vulnerabilities Vulnerability Scanner Command Line It can be used to find vulnerabilities. Trivy has scanners that look for security issues, and targets where. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Nmap started as a simple network scanning command line tool. Through the power of the nmap scripting engine (nse), it can be. Running a vulnerability scan with vulscan requires two components:. Vulnerability Scanner Command Line.
From linuxhint.com
Best Vulnerability Scanning Tools Vulnerability Scanner Command Line 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. It can be used to find vulnerabilities. Running a vulnerability scan with vulscan requires two components: You should have written permission before you ever try to scan a system or network. Nmap started as a simple network scanning command line tool. Through the power of the nmap scripting engine. Vulnerability Scanner Command Line.
From www.getastra.com
Vulnerability Scanning Process and Types Astra Security Blog Vulnerability Scanner Command Line You should have written permission before you ever try to scan a system or network. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a host, and detect operating. Nmap started as a simple network scanning command line tool. 40 rows trivy (pronunciation) is a comprehensive. Vulnerability Scanner Command Line.
From hackertarget.com
Nikto Vulnerability Scanner Vulnerability Scanner Command Line Running a vulnerability scan with vulscan requires two components: In this article, we’ll look at how to use nmap for vulnerability scan. Trivy has scanners that look for security issues, and targets where. Through the power of the nmap scripting engine (nse), it can be. Nmap started as a simple network scanning command line tool. 40 rows trivy (pronunciation) is. Vulnerability Scanner Command Line.
From www.geeksforgeeks.org
Vulnnr Vulnerability Scanner and Auto Exploiter in Kali Linux Vulnerability Scanner Command Line After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a host, and detect operating. In this article, we’ll look at how to use nmap for vulnerability scan. Nmap started as a simple network scanning command line tool. It can be used to find vulnerabilities. Trivy has. Vulnerability Scanner Command Line.
From www.datamation.com
How to Easily Run a Vulnerability Scan Using Nmap Datamation Vulnerability Scanner Command Line You should have written permission before you ever try to scan a system or network. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Through the power of the nmap scripting engine (nse), it can be. It can be used to find vulnerabilities. Running a vulnerability scan with vulscan requires two components: After installing nmap, users can use. Vulnerability Scanner Command Line.
From reconshell.com
XRAY GUI Starter Vulnerability Scanner Testing Tools Vulnerability Scanner Command Line In this article, we’ll look at how to use nmap for vulnerability scan. Trivy has scanners that look for security issues, and targets where. You should have written permission before you ever try to scan a system or network. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan. Vulnerability Scanner Command Line.
From gbhackers.com
10 Best Vulnerability Scanner Tools 2023 (Updated) Vulnerability Scanner Command Line Running a vulnerability scan with vulscan requires two components: Trivy has scanners that look for security issues, and targets where. It can be used to find vulnerabilities. You should have written permission before you ever try to scan a system or network. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. After installing nmap, users can use the. Vulnerability Scanner Command Line.
From www.hackingloops.com
The Best Vulnerability Scanners within Kali Linux Vulnerability Scanner Command Line In this article, we’ll look at how to use nmap for vulnerability scan. Through the power of the nmap scripting engine (nse), it can be. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a. Vulnerability Scanner Command Line.
From www.hacknos.com
Nmap Vulnerability Scan Nmap Vulnerability Scan Nmap scan open ports Vulnerability Scanner Command Line After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a host, and detect operating. Trivy has scanners that look for security issues, and targets where. Running a vulnerability scan with vulscan requires two components: Nmap started as a simple network scanning command line tool. 40 rows. Vulnerability Scanner Command Line.
From bootcamptoprod.com
Google Open Source Vulnerability Scanner How To Use It To Secure Your Vulnerability Scanner Command Line Running a vulnerability scan with vulscan requires two components: You should have written permission before you ever try to scan a system or network. In this article, we’ll look at how to use nmap for vulnerability scan. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on. Vulnerability Scanner Command Line.
From www.hackingarticles.in
Nmap for Pentester Vulnerability Scan Vulnerability Scanner Command Line 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a host, and detect operating. You should have written permission before you ever try to scan a system or network. Trivy has scanners that look for. Vulnerability Scanner Command Line.
From www.geeksforgeeks.org
Nuclei Fast and Customizable Vulnerability Scanner Vulnerability Scanner Command Line You should have written permission before you ever try to scan a system or network. Running a vulnerability scan with vulscan requires two components: Through the power of the nmap scripting engine (nse), it can be. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a. Vulnerability Scanner Command Line.
From www.dnsstuff.com
Top 15 Paid and Free Vulnerability Scanner Tools DNSstuff Vulnerability Scanner Command Line 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Nmap started as a simple network scanning command line tool. You should have written permission before you ever try to scan a system or network. In this article, we’ll look at how to use nmap for vulnerability scan. Through the power of the nmap scripting engine (nse), it can. Vulnerability Scanner Command Line.
From www.youtube.com
How to Use Nessus in Kali to Identify Vulnerabilities to Exploit with Vulnerability Scanner Command Line Trivy has scanners that look for security issues, and targets where. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. You should have written permission before you ever try to scan a system or network. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on. Vulnerability Scanner Command Line.
From www.geeksforgeeks.org
Nuclei Fast and Customizable Vulnerability Scanner Vulnerability Scanner Command Line Through the power of the nmap scripting engine (nse), it can be. In this article, we’ll look at how to use nmap for vulnerability scan. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a host, and detect operating. 40 rows trivy (pronunciation) is a comprehensive. Vulnerability Scanner Command Line.
From www.geeksforgeeks.org
Vulnnr Vulnerability Scanner and Auto Exploiter in Kali Linux Vulnerability Scanner Command Line 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Trivy has scanners that look for security issues, and targets where. Running a vulnerability scan with vulscan requires two components: It can be used to find vulnerabilities. Nmap started as a simple network scanning command line tool. After installing nmap, users can use the command line or zenmap to. Vulnerability Scanner Command Line.
From spyboy.blog
Nikto Scan Any site for Vulnerabilities Spyboy blog Vulnerability Scanner Command Line You should have written permission before you ever try to scan a system or network. Trivy has scanners that look for security issues, and targets where. Through the power of the nmap scripting engine (nse), it can be. In this article, we’ll look at how to use nmap for vulnerability scan. After installing nmap, users can use the command line. Vulnerability Scanner Command Line.
From ourcodeworld.com
How to scan for web server vulnerabilities with Nikto2 in Kali Linux Vulnerability Scanner Command Line Nmap started as a simple network scanning command line tool. Through the power of the nmap scripting engine (nse), it can be. It can be used to find vulnerabilities. Trivy has scanners that look for security issues, and targets where. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain,. Vulnerability Scanner Command Line.
From www.hacknos.com
Nmap Vulnerability Scan Nmap Vulnerability Scan Nmap scan open ports Vulnerability Scanner Command Line In this article, we’ll look at how to use nmap for vulnerability scan. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a host, and detect operating. Through the power of the nmap scripting engine. Vulnerability Scanner Command Line.
From vegabird.com
VOOKI Application and API Vulnerability Scanner Vooki Infosec Vulnerability Scanner Command Line Running a vulnerability scan with vulscan requires two components: In this article, we’ll look at how to use nmap for vulnerability scan. You should have written permission before you ever try to scan a system or network. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on. Vulnerability Scanner Command Line.
From vulners.com
Internal Vulnerability Scanner What is and Usage Vulners Vulnerability Scanner Command Line Trivy has scanners that look for security issues, and targets where. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Through the power of the nmap scripting engine (nse), it can be. It can be used to find vulnerabilities. Running a vulnerability scan with vulscan requires two components: Nmap started as a simple network scanning command line tool.. Vulnerability Scanner Command Line.
From vegabird.com
VOOKI Application and API Vulnerability Scanner Vooki Infosec Vulnerability Scanner Command Line Running a vulnerability scan with vulscan requires two components: 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a host, and detect operating. Trivy has scanners that look for security issues, and targets where. It. Vulnerability Scanner Command Line.
From www.redlings.com
Top 10 Vulnerability Scanners for 2022 >>Redlings Vulnerability Scanner Command Line Trivy has scanners that look for security issues, and targets where. You should have written permission before you ever try to scan a system or network. Running a vulnerability scan with vulscan requires two components: Nmap started as a simple network scanning command line tool. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. In this article, we’ll. Vulnerability Scanner Command Line.
From linuxhint.com
How to scan for services and vulnerabilities with Nmap Vulnerability Scanner Command Line Running a vulnerability scan with vulscan requires two components: In this article, we’ll look at how to use nmap for vulnerability scan. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Nmap started as a simple network scanning command line tool. You should have written permission before you ever try to scan a system or network. After installing. Vulnerability Scanner Command Line.
From www.youtube.com
How to scan for vulnerabilities(CVE) using nmap YouTube Vulnerability Scanner Command Line In this article, we’ll look at how to use nmap for vulnerability scan. Nmap started as a simple network scanning command line tool. Running a vulnerability scan with vulscan requires two components: 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Through the power of the nmap scripting engine (nse), it can be. You should have written permission. Vulnerability Scanner Command Line.
From devsday.ru
Scanning vulnerabilities with Nikto DevsDay.ru Vulnerability Scanner Command Line Through the power of the nmap scripting engine (nse), it can be. In this article, we’ll look at how to use nmap for vulnerability scan. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a host, and detect operating. Nmap started as a simple network scanning. Vulnerability Scanner Command Line.
From www.oreilly.com
Vulnerability scanning with nmap Mastering Kali Linux for Advanced Vulnerability Scanner Command Line Trivy has scanners that look for security issues, and targets where. Through the power of the nmap scripting engine (nse), it can be. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a host, and detect operating. Running a vulnerability scan with vulscan requires two components:. Vulnerability Scanner Command Line.
From blog.cloudflare.com
Introducing Flan Scan Cloudflare’s Lightweight Network Vulnerability Vulnerability Scanner Command Line Running a vulnerability scan with vulscan requires two components: After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a host, and detect operating. Through the power of the nmap scripting engine (nse), it can be. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner.. Vulnerability Scanner Command Line.
From www.redlings.com
Top 10 Vulnerability Scanners for 2022 >>Redlings Vulnerability Scanner Command Line Running a vulnerability scan with vulscan requires two components: It can be used to find vulnerabilities. You should have written permission before you ever try to scan a system or network. Trivy has scanners that look for security issues, and targets where. Through the power of the nmap scripting engine (nse), it can be. Nmap started as a simple network. Vulnerability Scanner Command Line.
From www.tecmint.com
WPSeku A Vulnerability Scanner to Find Security Issues in WordPress Vulnerability Scanner Command Line You should have written permission before you ever try to scan a system or network. After installing nmap, users can use the command line or zenmap to execute simple commands to map the local domain, scan ports on a host, and detect operating. It can be used to find vulnerabilities. Running a vulnerability scan with vulscan requires two components: 40. Vulnerability Scanner Command Line.
From int64software.com
Free Windows Privilege Escalation Vulnerability Scan Tool Int64 Vulnerability Scanner Command Line Trivy has scanners that look for security issues, and targets where. Nmap started as a simple network scanning command line tool. You should have written permission before you ever try to scan a system or network. In this article, we’ll look at how to use nmap for vulnerability scan. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner.. Vulnerability Scanner Command Line.
From www.geeksforgeeks.org
Nuclei Fast and Customizable Vulnerability Scanner Vulnerability Scanner Command Line Running a vulnerability scan with vulscan requires two components: Nmap started as a simple network scanning command line tool. It can be used to find vulnerabilities. You should have written permission before you ever try to scan a system or network. 40 rows trivy (pronunciation) is a comprehensive and versatile security scanner. Trivy has scanners that look for security issues,. Vulnerability Scanner Command Line.