Scan Usage Examples . Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. Topics include subverting firewalls and intrusion detection. Here is an overview of the most popular scan types: The nmap scripting engine (nse) will help. Examples and diagrams show actual communication on the wire. If it receives an ack on the specific probed port, it means the port exist on. While nse has a complex implementation for efficiency, it is strikingly easy to use. Here are some nmap usage examples, from the simple and routine to a little more complex and esoteric. Nmap allows network admins to find. This sends only a tcp syn packet and waits for a tcp ack. Some actual ip addresses and domain.
from www.nibib.nih.gov
Some actual ip addresses and domain. While nse has a complex implementation for efficiency, it is strikingly easy to use. If it receives an ack on the specific probed port, it means the port exist on. This sends only a tcp syn packet and waits for a tcp ack. Here are some nmap usage examples, from the simple and routine to a little more complex and esoteric. Here is an overview of the most popular scan types: Nmap allows network admins to find. Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. The nmap scripting engine (nse) will help. Topics include subverting firewalls and intrusion detection.
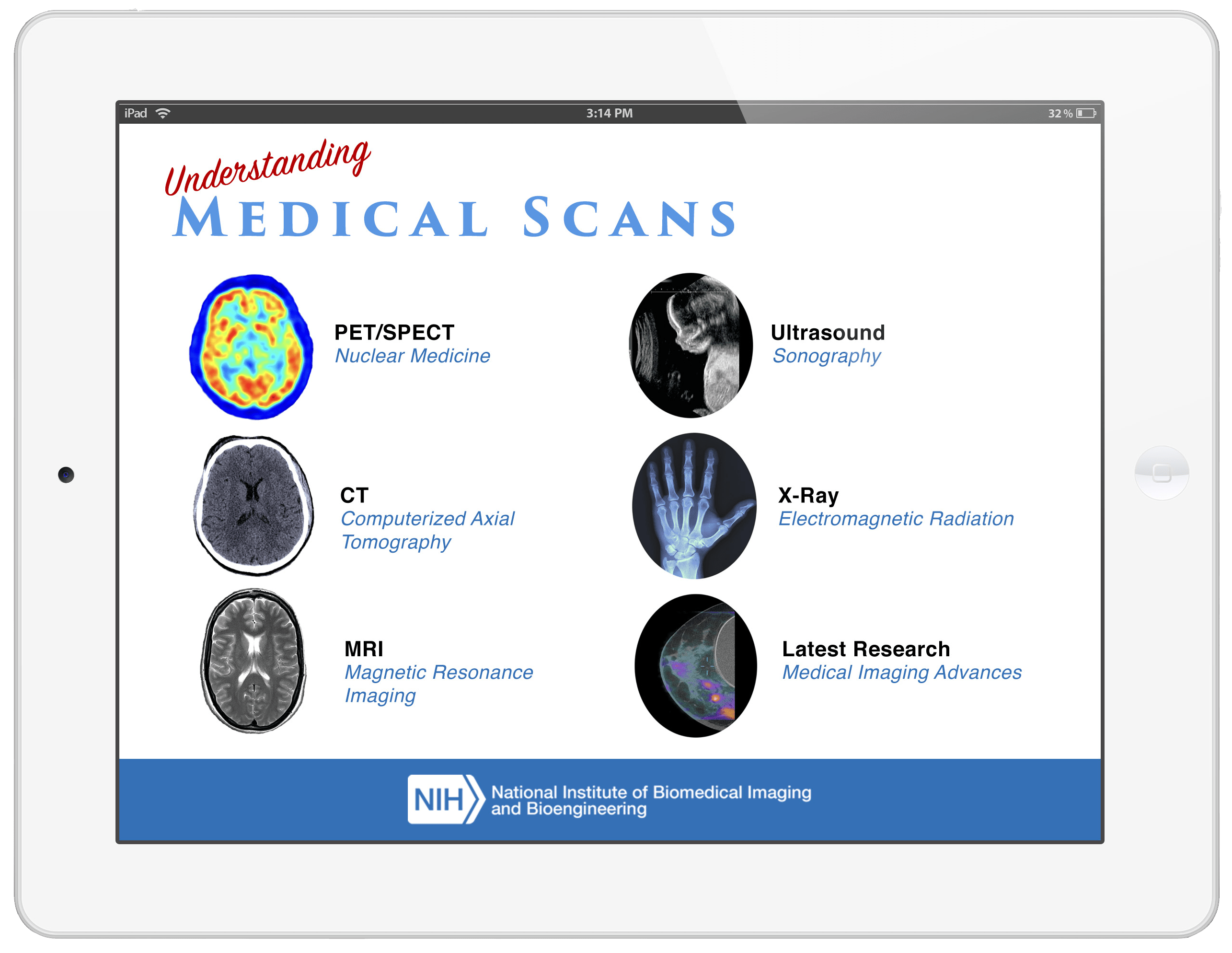
Understanding Medical Scans National Institute of Biomedical Imaging
Scan Usage Examples Some actual ip addresses and domain. Topics include subverting firewalls and intrusion detection. Here is an overview of the most popular scan types: If it receives an ack on the specific probed port, it means the port exist on. Examples and diagrams show actual communication on the wire. Here are some nmap usage examples, from the simple and routine to a little more complex and esoteric. Some actual ip addresses and domain. This sends only a tcp syn packet and waits for a tcp ack. Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. Nmap allows network admins to find. The nmap scripting engine (nse) will help. While nse has a complex implementation for efficiency, it is strikingly easy to use.
From healthtian.com
CT Scan Definition, Uses and Procedure Healthtian Scan Usage Examples The nmap scripting engine (nse) will help. Here are some nmap usage examples, from the simple and routine to a little more complex and esoteric. Examples and diagrams show actual communication on the wire. Topics include subverting firewalls and intrusion detection. Some actual ip addresses and domain. While nse has a complex implementation for efficiency, it is strikingly easy to. Scan Usage Examples.
From differencify.com
Skimming and Scanning Concepts, Examples, Differences (Table) Scan Usage Examples Examples and diagrams show actual communication on the wire. While nse has a complex implementation for efficiency, it is strikingly easy to use. If it receives an ack on the specific probed port, it means the port exist on. Nmap allows network admins to find. Some actual ip addresses and domain. Using various scanning techniques, nmap uncovers live hosts, probes. Scan Usage Examples.
From www.setonimaging.com
Frequently asked questions about MRI Scans Seton Imaging Scan Usage Examples Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. Here are some nmap usage examples, from the simple and routine to a little more complex and esoteric. While nse has a complex implementation for efficiency, it is strikingly easy to use. If it receives an ack on the specific probed port, it means the. Scan Usage Examples.
From latesthackingnews.com
How to Scan for Vulnerabilities Using Nessus Latest Hacking News Scan Usage Examples Here is an overview of the most popular scan types: Here are some nmap usage examples, from the simple and routine to a little more complex and esoteric. Examples and diagrams show actual communication on the wire. Nmap allows network admins to find. This sends only a tcp syn packet and waits for a tcp ack. Some actual ip addresses. Scan Usage Examples.
From myvitalmetrics.com
DEXA Scan Results Understanding Your DEXA Scan Report Scan Usage Examples While nse has a complex implementation for efficiency, it is strikingly easy to use. Here are some nmap usage examples, from the simple and routine to a little more complex and esoteric. Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. Some actual ip addresses and domain. Here is an overview of the most. Scan Usage Examples.
From thedevnews.com
10 Examples Of Scanner Class In Java The Dev News Scan Usage Examples Here is an overview of the most popular scan types: Topics include subverting firewalls and intrusion detection. Some actual ip addresses and domain. This sends only a tcp syn packet and waits for a tcp ack. Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. Nmap allows network admins to find. Examples and diagrams. Scan Usage Examples.
From www.nibib.nih.gov
Understanding Medical Scans National Institute of Biomedical Imaging Scan Usage Examples If it receives an ack on the specific probed port, it means the port exist on. Some actual ip addresses and domain. Here is an overview of the most popular scan types: The nmap scripting engine (nse) will help. Nmap allows network admins to find. Examples and diagrams show actual communication on the wire. Using various scanning techniques, nmap uncovers. Scan Usage Examples.
From www.researchgate.net
Subject motion between acquisition frames. Examples of a PET/CT scan Scan Usage Examples If it receives an ack on the specific probed port, it means the port exist on. Some actual ip addresses and domain. Topics include subverting firewalls and intrusion detection. The nmap scripting engine (nse) will help. Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. Here are some nmap usage examples, from the simple. Scan Usage Examples.
From www.csusm.edu
Creating High Quality Scans Instructional and Information Technology Scan Usage Examples Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. While nse has a complex implementation for efficiency, it is strikingly easy to use. If it receives an ack on the specific probed port, it means the port exist on. Here is an overview of the most popular scan types: Examples and diagrams show actual. Scan Usage Examples.
From exysgckrw.blob.core.windows.net
What Is A 3D Ct Scan at Jennifer Nell blog Scan Usage Examples Here are some nmap usage examples, from the simple and routine to a little more complex and esoteric. Here is an overview of the most popular scan types: If it receives an ack on the specific probed port, it means the port exist on. The nmap scripting engine (nse) will help. Nmap allows network admins to find. This sends only. Scan Usage Examples.
From accurateimagingdiagnostics.com
Dexa Body Composition Scan DEXA at Accurate Imaging Diagnostics Scan Usage Examples The nmap scripting engine (nse) will help. If it receives an ack on the specific probed port, it means the port exist on. Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. Here is an overview of the most popular scan types: Examples and diagrams show actual communication on the wire. This sends only. Scan Usage Examples.
From bokastutor.com
13 Methods of Environmental Scanning [Explained] BokasTutor Scan Usage Examples Topics include subverting firewalls and intrusion detection. Here is an overview of the most popular scan types: Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. Here are some nmap usage examples, from the simple and routine to a little more complex and esoteric. While nse has a complex implementation for efficiency, it is. Scan Usage Examples.
From www.verywellhealth.com
CT Scan (CAT Scan) Uses, Side Effects, Procedure, Results Scan Usage Examples Some actual ip addresses and domain. Examples and diagrams show actual communication on the wire. This sends only a tcp syn packet and waits for a tcp ack. Topics include subverting firewalls and intrusion detection. Here is an overview of the most popular scan types: While nse has a complex implementation for efficiency, it is strikingly easy to use. If. Scan Usage Examples.
From www.csusm.edu
Creating High Quality Scans Instructional and Information Technology Scan Usage Examples Nmap allows network admins to find. Topics include subverting firewalls and intrusion detection. The nmap scripting engine (nse) will help. Here is an overview of the most popular scan types: Some actual ip addresses and domain. If it receives an ack on the specific probed port, it means the port exist on. While nse has a complex implementation for efficiency,. Scan Usage Examples.
From business.paytm.com
Scan to Order for restaurants Blog Paytm For Business App Scan Usage Examples If it receives an ack on the specific probed port, it means the port exist on. Some actual ip addresses and domain. While nse has a complex implementation for efficiency, it is strikingly easy to use. Examples and diagrams show actual communication on the wire. This sends only a tcp syn packet and waits for a tcp ack. Here are. Scan Usage Examples.
From dxoczwmtu.blob.core.windows.net
What Is A Cat Scan And Ct Scan at Joseph Cox blog Scan Usage Examples Topics include subverting firewalls and intrusion detection. This sends only a tcp syn packet and waits for a tcp ack. If it receives an ack on the specific probed port, it means the port exist on. Here is an overview of the most popular scan types: Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential. Scan Usage Examples.
From numberdyslexia.com
Skimming And Scanning Examples & Effective Strategies Number Dyslexia Scan Usage Examples Here are some nmap usage examples, from the simple and routine to a little more complex and esoteric. The nmap scripting engine (nse) will help. If it receives an ack on the specific probed port, it means the port exist on. Some actual ip addresses and domain. Topics include subverting firewalls and intrusion detection. Here is an overview of the. Scan Usage Examples.
From assist.plus.konicaminolta.asia
How to setup Scan to SMB Konica Minolta+ Assist Scan Usage Examples While nse has a complex implementation for efficiency, it is strikingly easy to use. Topics include subverting firewalls and intrusion detection. Here is an overview of the most popular scan types: Nmap allows network admins to find. The nmap scripting engine (nse) will help. Here are some nmap usage examples, from the simple and routine to a little more complex. Scan Usage Examples.
From 7esl.com
MRI vs. CT Scan Understanding Medical Terms • 7ESL Scan Usage Examples Here are some nmap usage examples, from the simple and routine to a little more complex and esoteric. This sends only a tcp syn packet and waits for a tcp ack. Examples and diagrams show actual communication on the wire. Some actual ip addresses and domain. The nmap scripting engine (nse) will help. Nmap allows network admins to find. While. Scan Usage Examples.
From dxourlmrp.blob.core.windows.net
What Exactly Is A CtScan at Tory Lightner blog Scan Usage Examples While nse has a complex implementation for efficiency, it is strikingly easy to use. If it receives an ack on the specific probed port, it means the port exist on. Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. Examples and diagrams show actual communication on the wire. Topics include subverting firewalls and intrusion. Scan Usage Examples.
From www.slideshare.net
API Usage Scans •A producer Scan Usage Examples Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. Here are some nmap usage examples, from the simple and routine to a little more complex and esoteric. Nmap allows network admins to find. If it receives an ack on the specific probed port, it means the port exist on. The nmap scripting engine (nse). Scan Usage Examples.
From dxozzsgop.blob.core.windows.net
What Is Pet Scan Vs Ct Scan at Regina Bell blog Scan Usage Examples If it receives an ack on the specific probed port, it means the port exist on. Here is an overview of the most popular scan types: Some actual ip addresses and domain. Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. While nse has a complex implementation for efficiency, it is strikingly easy to. Scan Usage Examples.
From www.rapid7.com
How to Use OpenVAS to Audit the Security of Your Network (2/2) Rapid7 Scan Usage Examples Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. If it receives an ack on the specific probed port, it means the port exist on. Here are some nmap usage examples, from the simple and routine to a little more complex and esoteric. The nmap scripting engine (nse) will help. Topics include subverting firewalls. Scan Usage Examples.
From www.csusm.edu
Creating High Quality Scans Accessibility at CSUSM CSUSM Scan Usage Examples While nse has a complex implementation for efficiency, it is strikingly easy to use. Nmap allows network admins to find. Examples and diagrams show actual communication on the wire. Here is an overview of the most popular scan types: The nmap scripting engine (nse) will help. If it receives an ack on the specific probed port, it means the port. Scan Usage Examples.
From www.slideserve.com
PPT WSScan Device Implementation PowerPoint Presentation, free Scan Usage Examples The nmap scripting engine (nse) will help. Nmap allows network admins to find. Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. Here is an overview of the most popular scan types: This sends only a tcp syn packet and waits for a tcp ack. Some actual ip addresses and domain. Here are some. Scan Usage Examples.
From www.middlesex.mass.edu
Creating High Quality Scans Scan Usage Examples Topics include subverting firewalls and intrusion detection. Some actual ip addresses and domain. If it receives an ack on the specific probed port, it means the port exist on. The nmap scripting engine (nse) will help. Examples and diagrams show actual communication on the wire. This sends only a tcp syn packet and waits for a tcp ack. Using various. Scan Usage Examples.
From www.trustedreviews.com
How to scan text on an iPhone Scan Usage Examples The nmap scripting engine (nse) will help. Topics include subverting firewalls and intrusion detection. If it receives an ack on the specific probed port, it means the port exist on. Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. Examples and diagrams show actual communication on the wire. Nmap allows network admins to find.. Scan Usage Examples.
From www.sproutqr.com
QR Code Tracking How to Track QR Code Usage & Scans Scan Usage Examples Nmap allows network admins to find. Here is an overview of the most popular scan types: Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. While nse has a complex implementation for efficiency, it is strikingly easy to use. The nmap scripting engine (nse) will help. Examples and diagrams show actual communication on the. Scan Usage Examples.
From www.youtube.com
Networks SCAN Types of Network Scans Types of Network Scan Network Scan Usage Examples Topics include subverting firewalls and intrusion detection. Nmap allows network admins to find. The nmap scripting engine (nse) will help. While nse has a complex implementation for efficiency, it is strikingly easy to use. Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. If it receives an ack on the specific probed port, it. Scan Usage Examples.
From healthtian.com
CT Scan Definition, Uses and Procedure Scan Usage Examples If it receives an ack on the specific probed port, it means the port exist on. While nse has a complex implementation for efficiency, it is strikingly easy to use. Topics include subverting firewalls and intrusion detection. Nmap allows network admins to find. Examples and diagrams show actual communication on the wire. The nmap scripting engine (nse) will help. Here. Scan Usage Examples.
From software.hubone.com
Scans > Basic Usage > Manual Processing > Preview Document Scan Usage Examples Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. This sends only a tcp syn packet and waits for a tcp ack. Some actual ip addresses and domain. Topics include subverting firewalls and intrusion detection. While nse has a complex implementation for efficiency, it is strikingly easy to use. If it receives an ack. Scan Usage Examples.
From base.report
base.report Managing Scans in the Screener Scan Usage Examples Nmap allows network admins to find. Some actual ip addresses and domain. The nmap scripting engine (nse) will help. Here is an overview of the most popular scan types: While nse has a complex implementation for efficiency, it is strikingly easy to use. Here are some nmap usage examples, from the simple and routine to a little more complex and. Scan Usage Examples.
From www.slideserve.com
PPT 後 IA 時代 智慧型環境之發展趨勢 PowerPoint Presentation ID6327174 Scan Usage Examples Topics include subverting firewalls and intrusion detection. Nmap allows network admins to find. Here is an overview of the most popular scan types: Some actual ip addresses and domain. If it receives an ack on the specific probed port, it means the port exist on. While nse has a complex implementation for efficiency, it is strikingly easy to use. The. Scan Usage Examples.
From support.route4me.com
Route Planner App with iPhone Barcode Scanning Features Scan Usage Examples Examples and diagrams show actual communication on the wire. If it receives an ack on the specific probed port, it means the port exist on. The nmap scripting engine (nse) will help. Some actual ip addresses and domain. While nse has a complex implementation for efficiency, it is strikingly easy to use. Nmap allows network admins to find. Topics include. Scan Usage Examples.
From www.geeksforgeeks.org
n in scanf() in C with Example Scan Usage Examples This sends only a tcp syn packet and waits for a tcp ack. Here is an overview of the most popular scan types: Examples and diagrams show actual communication on the wire. Using various scanning techniques, nmap uncovers live hosts, probes open ports, and identifies potential vulnerabilities. Here are some nmap usage examples, from the simple and routine to a. Scan Usage Examples.