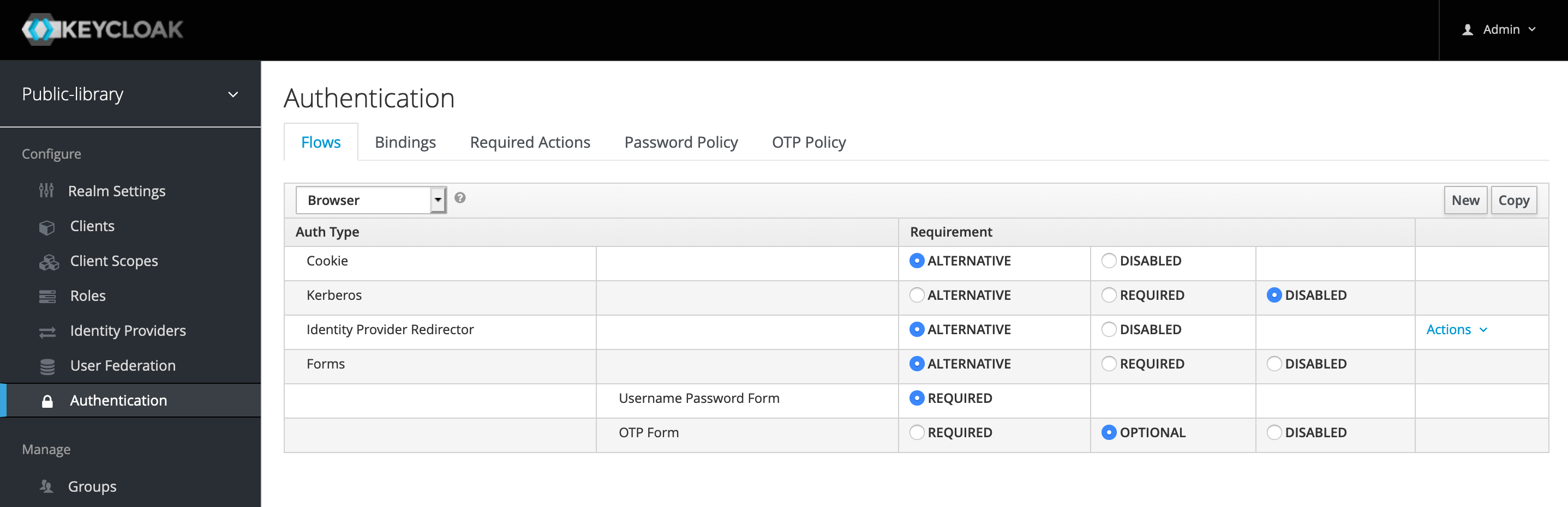
Keycloak Authentication Manager . No need to deal with storing users or authenticating users. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Add authentication to applications and secure services with minimum effort. The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate the user. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. How to configure keycloak to manage authentication and authorization for web applications or services. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Creating realms, security roles, users and passwords.
from www.thomasvitale.com
Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Creating realms, security roles, users and passwords. Add authentication to applications and secure services with minimum effort. The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate the user. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. How to configure keycloak to manage authentication and authorization for web applications or services. No need to deal with storing users or authenticating users. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything.
Keycloak Authentication Flows, SSO Protocols and Client Configuration
Keycloak Authentication Manager No need to deal with storing users or authenticating users. The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate the user. How to configure keycloak to manage authentication and authorization for web applications or services. No need to deal with storing users or authenticating users. Add authentication to applications and secure services with minimum effort. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Creating realms, security roles, users and passwords. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption.
From hasura.io
Keycloak Hasura Authentication Tutorial Keycloak Authentication Manager The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Creating realms, security roles, users and passwords. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Add authentication to applications and secure services with minimum effort. How to configure keycloak to manage authentication. Keycloak Authentication Manager.
From soundsessential.com
Setting Up A Keycloak Server For Authenticating To FileMaker Part 8 Keycloak Authentication Manager No need to deal with storing users or authenticating users. The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate the user. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Keycloak provides the flexibility to. Keycloak Authentication Manager.
From stackoverflow.com
rest Keycloak Oauth2 Authentication Flow Stack Overflow Keycloak Authentication Manager The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. How to configure keycloak to manage authentication and authorization for web applications or services. No need to deal with storing users or authenticating users. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for.. Keycloak Authentication Manager.
From medium.com
Authentication in Angular using Keycloak by Damilare A. Adedoyin Medium Keycloak Authentication Manager The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Creating realms, security roles, users and passwords. How to configure keycloak to manage authentication and authorization for web applications or services. No need to deal with storing users or authenticating users. Keycloak provides the flexibility to export and import configurations easily, using a single view to. Keycloak Authentication Manager.
From blog.tharinduhasthika.com
Authenticating Jitsi Meetings using Keycloak Keycloak Authentication Manager Creating realms, security roles, users and passwords. Add authentication to applications and secure services with minimum effort. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate. Keycloak Authentication Manager.
From blog.bioinformaticalabs.com
Understanding the Powerful Keycloak Tool Keycloak Authentication Manager Add authentication to applications and secure services with minimum effort. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. How to configure keycloak to manage authentication and authorization for web applications or services. Creating realms, security roles, users and passwords. The starting point in our process to. Keycloak Authentication Manager.
From scalac.io
User Authentication with Keycloak Part 1 React frontend Keycloak Authentication Manager Creating realms, security roles, users and passwords. How to configure keycloak to manage authentication and authorization for web applications or services. Add authentication to applications and secure services with minimum effort. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Keycloak provides the flexibility to export and. Keycloak Authentication Manager.
From www.janua.fr
understanding client Authenticator security with Keycloak JANUA Keycloak Authentication Manager The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate the user. Creating realms, security roles, users and passwords. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Add authentication to applications and secure services with. Keycloak Authentication Manager.
From walkingtree.tech
Keycloak Identity Access Management Solutions WalkingTree Technologies Keycloak Authentication Manager How to configure keycloak to manage authentication and authorization for web applications or services. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. No need to deal with storing users or authenticating users. The starting point in our process to secure an application or a web service. Keycloak Authentication Manager.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Authentication Manager How to configure keycloak to manage authentication and authorization for web applications or services. The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate the user. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Creating. Keycloak Authentication Manager.
From github.com
GitHub akshatsachdeva/keycloakotpwebhook Keycloak authentication Keycloak Authentication Manager No need to deal with storing users or authenticating users. How to configure keycloak to manage authentication and authorization for web applications or services. The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate the user. Keycloak provides the flexibility to export and import configurations easily, using a single. Keycloak Authentication Manager.
From refactorfirst.com
FIDO2 Passwordless Authentication With Keycloak Part 2 RefactorFirst Keycloak Authentication Manager How to configure keycloak to manage authentication and authorization for web applications or services. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Creating realms, security roles, users and passwords.. Keycloak Authentication Manager.
From developers.redhat.com
Authentication and authorization using the Keycloak REST API Red Hat Keycloak Authentication Manager Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. No need to deal with storing users. Keycloak Authentication Manager.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Authentication Manager The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. No need to deal with storing users or authenticating users. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Add authentication to applications and secure services with minimum effort. How to configure keycloak. Keycloak Authentication Manager.
From www.thomasvitale.com
Introducing Keycloak for Identity and Access Management Keycloak Authentication Manager Creating realms, security roles, users and passwords. How to configure keycloak to manage authentication and authorization for web applications or services. No need to deal with storing users or authenticating users. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. Add authentication to applications and secure services with minimum effort. The authentication. Keycloak Authentication Manager.
From pm4ml.github.io
Managing user access in Keycloak Payment Manager OSS Documentation Keycloak Authentication Manager The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. How to configure keycloak to manage authentication and authorization for web applications or services. Add authentication to applications and secure services with minimum effort. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for.. Keycloak Authentication Manager.
From www.typingdna.com
Add twofactor authentication to your web app using Keycloak & Node.js Keycloak Authentication Manager Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate. Keycloak Authentication Manager.
From pm4ml.github.io
Managing user access in Keycloak Payment Manager OSS Documentation Keycloak Authentication Manager No need to deal with storing users or authenticating users. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. How to configure keycloak to manage authentication and authorization for web applications or services. Creating realms, security roles, users and passwords. The starting point in our process to. Keycloak Authentication Manager.
From www.keycloak.org
How to Integrate Keycloak for Authentication with Apache APISIX Keycloak Keycloak Authentication Manager Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Creating realms, security roles, users and passwords. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. The starting point in our process to secure an application or a web service. Keycloak Authentication Manager.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Authentication Manager No need to deal with storing users or authenticating users. The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate the user. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. The authentication protocols that are. Keycloak Authentication Manager.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Authentication Manager Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. No need to deal with storing users or authenticating users. Creating realms, security roles, users and passwords. The authentication protocols that. Keycloak Authentication Manager.
From walkingtree.tech
Keycloak and MultiFactor Authentication (MFA) Strengthening Security Keycloak Authentication Manager The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Add authentication to applications and secure services with minimum effort. How to configure keycloak to manage authentication and authorization for web applications or services. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for.. Keycloak Authentication Manager.
From www.olivercoding.com
at home Part 5 Keycloak for authentication Oliver Coding Keycloak Authentication Manager Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Creating realms, security roles, users and passwords. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. Add authentication to applications and secure services with minimum effort. No need to deal. Keycloak Authentication Manager.
From www.olivercoding.com
at home Part 6 Keycloak authentication and Azure Active Keycloak Authentication Manager How to configure keycloak to manage authentication and authorization for web applications or services. Add authentication to applications and secure services with minimum effort. Creating realms, security roles, users and passwords. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. The starting point in our process to. Keycloak Authentication Manager.
From github.com
GitHub 5stones/keycloakemailotp A Keycloak Authentication step Keycloak Authentication Manager Add authentication to applications and secure services with minimum effort. How to configure keycloak to manage authentication and authorization for web applications or services. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. Creating realms, security roles, users. Keycloak Authentication Manager.
From apim.docs.wso2.com
Configure Keycloak as a Key Manager WSO2 API Manager Documentation 4.1.0 Keycloak Authentication Manager No need to deal with storing users or authenticating users. Add authentication to applications and secure services with minimum effort. Creating realms, security roles, users and passwords. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. Keycloak is based on a set of administrative uis and a restful api, and provides the. Keycloak Authentication Manager.
From apisix.apache.org
Accessing APISIXDashboard from Everywhere with Keycloak Authentication Keycloak Authentication Manager Creating realms, security roles, users and passwords. No need to deal with storing users or authenticating users. Add authentication to applications and secure services with minimum effort. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Keycloak provides the flexibility to export and import configurations easily, using. Keycloak Authentication Manager.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Authentication Manager The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate the user. No need to deal with storing users or authenticating users. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. How to configure keycloak to manage authentication and authorization for. Keycloak Authentication Manager.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Authentication Manager The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. Add authentication to applications and secure services with minimum effort. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. No need to deal with storing users or authenticating users. How to configure keycloak. Keycloak Authentication Manager.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Authentication Manager Creating realms, security roles, users and passwords. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate the. Keycloak Authentication Manager.
From witekio.com
Authentication Management Focus On Keycloak Witekio Keycloak Authentication Manager Creating realms, security roles, users and passwords. The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate the user. No need to deal with storing users or authenticating users. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. How to configure. Keycloak Authentication Manager.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Authentication Manager Creating realms, security roles, users and passwords. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Keycloak provides the flexibility to export and import configurations easily, using a single view to manage everything. The starting point in our process to secure an application or a web service. Keycloak Authentication Manager.
From pm4ml.github.io
Managing user access in Keycloak Payment Manager OSS Documentation Keycloak Authentication Manager Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Add authentication to applications and secure services with minimum effort. The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate the user. The authentication protocols that are. Keycloak Authentication Manager.
From pm4ml.github.io
Managing user access in Keycloak Payment Manager OSS Documentation Keycloak Authentication Manager How to configure keycloak to manage authentication and authorization for web applications or services. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. No need to deal with storing users or authenticating users. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption.. Keycloak Authentication Manager.
From sciencegateways.org
sciencegateways Tech Blog Using Keycloak to Provide Authentication Keycloak Authentication Manager The starting point in our process to secure an application or a web service with keycloak is to identify and authenticate the user. The authentication protocols that are used by keycloak require cryptographic signatures and sometimes encryption. No need to deal with storing users or authenticating users. Keycloak provides the flexibility to export and import configurations easily, using a single. Keycloak Authentication Manager.