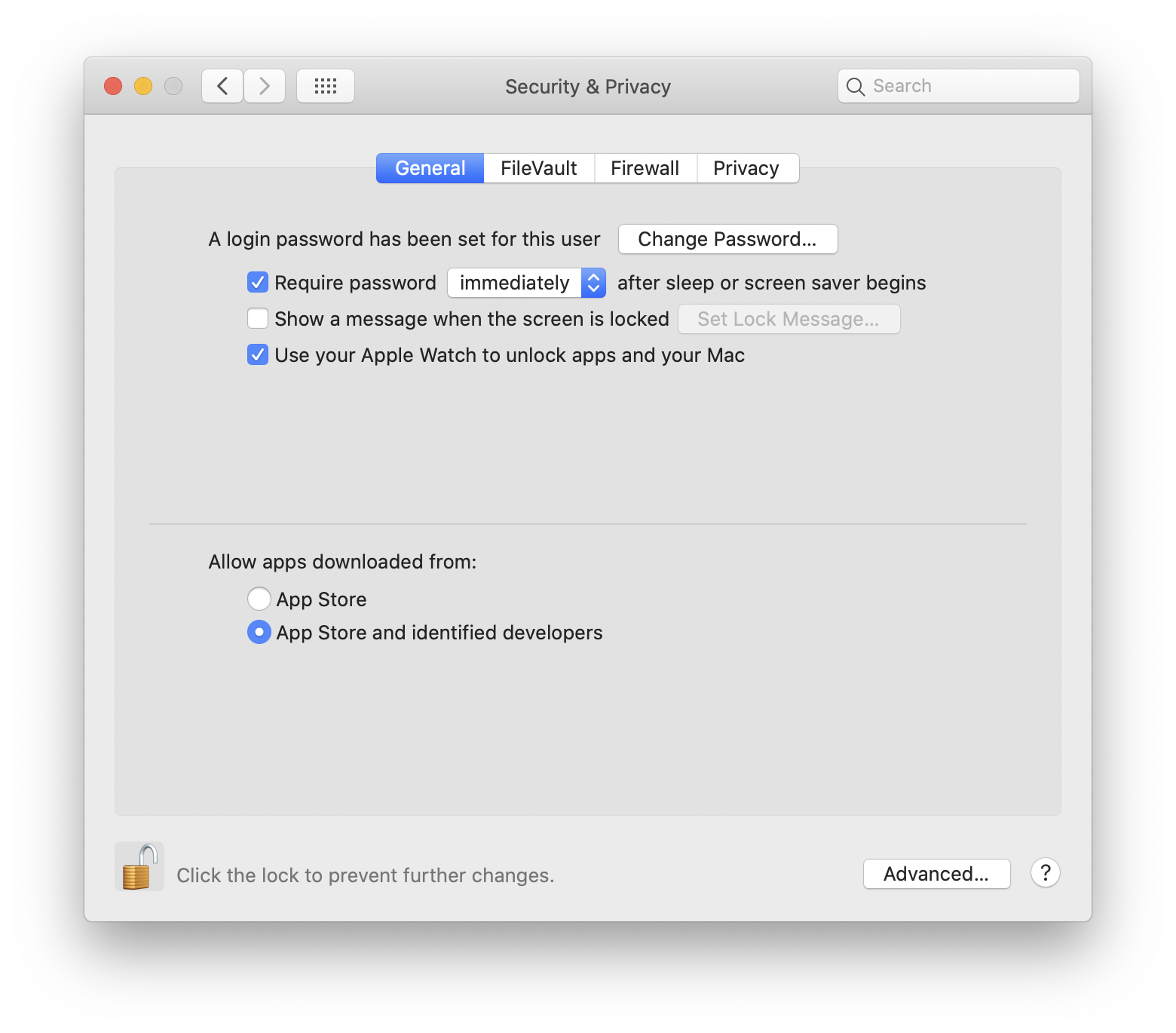
Security Policy Mac . A shared architecture for security. When i start to do it from bootable disk with macos. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). For compliance policy processing we need the company portal here. For an enterprise deployment of macos devices, you should: I want to install new os. By default, your mac uses the highest level of security, called full security. It says security setting do not allow this mac to use. According to the small print in apple’s platform security guide, when you set up a new m1 mac, or set one up after restoring it in. Devices with a t2 security processor. Before a legacy system extension (also known as a kernel. On your mac, use privacy & security settings to manage the information your mac makes available to others across the internet or on a.
from www.intego.com
For compliance policy processing we need the company portal here. By default, your mac uses the highest level of security, called full security. According to the small print in apple’s platform security guide, when you set up a new m1 mac, or set one up after restoring it in. Devices with a t2 security processor. It says security setting do not allow this mac to use. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). For an enterprise deployment of macos devices, you should: When i start to do it from bootable disk with macos. Before a legacy system extension (also known as a kernel. A shared architecture for security.
8 Mac security and privacy features to set up right away The Mac
Security Policy Mac By default, your mac uses the highest level of security, called full security. On your mac, use privacy & security settings to manage the information your mac makes available to others across the internet or on a. It says security setting do not allow this mac to use. Devices with a t2 security processor. For an enterprise deployment of macos devices, you should: For compliance policy processing we need the company portal here. A shared architecture for security. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). By default, your mac uses the highest level of security, called full security. Before a legacy system extension (also known as a kernel. According to the small print in apple’s platform security guide, when you set up a new m1 mac, or set one up after restoring it in. When i start to do it from bootable disk with macos. I want to install new os.
From vastcor.weebly.com
Mac security settings vastcor Security Policy Mac These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). Devices with a t2 security processor. On your mac, use privacy & security settings to manage the information your mac makes available to others across the internet or on a. It says security setting do not allow this mac to use. For compliance. Security Policy Mac.
From www.macworld.com
How Secure Is A Mac? Best Mac Security Settings Macworld Security Policy Mac These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). When i start to do it from bootable disk with macos. For an enterprise deployment of macos devices, you should: On your mac, use privacy & security settings to manage the information your mac makes available to others across the internet or on. Security Policy Mac.
From informationq.com
What is the Macintosh Operating System History of Mac OS Security Policy Mac For an enterprise deployment of macos devices, you should: Devices with a t2 security processor. When i start to do it from bootable disk with macos. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). For compliance policy processing we need the company portal here. On your mac, use privacy & security. Security Policy Mac.
From support.apple.com
Startup Disk security policy control for a Mac with Apple silicon Security Policy Mac By default, your mac uses the highest level of security, called full security. For compliance policy processing we need the company portal here. A shared architecture for security. When i start to do it from bootable disk with macos. According to the small print in apple’s platform security guide, when you set up a new m1 mac, or set one. Security Policy Mac.
From mongeit.consulting
Mac Security Settings ‣ Monge IT Consulting, Inc. Security Policy Mac On your mac, use privacy & security settings to manage the information your mac makes available to others across the internet or on a. When i start to do it from bootable disk with macos. For compliance policy processing we need the company portal here. I want to install new os. According to the small print in apple’s platform security. Security Policy Mac.
From templatelab.com
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab Security Policy Mac According to the small print in apple’s platform security guide, when you set up a new m1 mac, or set one up after restoring it in. For compliance policy processing we need the company portal here. When i start to do it from bootable disk with macos. On your mac, use privacy & security settings to manage the information your. Security Policy Mac.
From www.interactcard.com.au
Using Teamviewer on MAC Security Policy Mac These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). On your mac, use privacy & security settings to manage the information your mac makes available to others across the internet or on a. By default, your mac uses the highest level of security, called full security. Devices with a t2 security processor.. Security Policy Mac.
From www.1kosmos.com
What Is Mandatory Access Control (MAC)? 1Kosmos Security Policy Mac It says security setting do not allow this mac to use. Before a legacy system extension (also known as a kernel. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). According to the small print in apple’s platform security guide, when you set up a new m1 mac, or set one up. Security Policy Mac.
From www.alamy.com
Six Types of Security Policy Stock Photo Alamy Security Policy Mac Before a legacy system extension (also known as a kernel. According to the small print in apple’s platform security guide, when you set up a new m1 mac, or set one up after restoring it in. When i start to do it from bootable disk with macos. I want to install new os. These are typically security configurations as well. Security Policy Mac.
From www.pcmag.com
Avast Security for Mac Review PCMag Security Policy Mac A shared architecture for security. Devices with a t2 security processor. For compliance policy processing we need the company portal here. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). Before a legacy system extension (also known as a kernel. When i start to do it from bootable disk with macos. It. Security Policy Mac.
From www.intego.com
Get to know the System Settings app on macOS Ventura The Mac Security Security Policy Mac It says security setting do not allow this mac to use. For an enterprise deployment of macos devices, you should: By default, your mac uses the highest level of security, called full security. A shared architecture for security. When i start to do it from bootable disk with macos. I want to install new os. According to the small print. Security Policy Mac.
From macpaw.com
The ultimate guide to macOS Security Security Policy Mac I want to install new os. Devices with a t2 security processor. By default, your mac uses the highest level of security, called full security. Before a legacy system extension (also known as a kernel. A shared architecture for security. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). For compliance policy. Security Policy Mac.
From mongeit.consulting
Mac Security Settings ‣ Monge IT Consulting, Inc. Security Policy Mac For compliance policy processing we need the company portal here. According to the small print in apple’s platform security guide, when you set up a new m1 mac, or set one up after restoring it in. I want to install new os. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). Devices. Security Policy Mac.
From transportintensive.weebly.com
Change App Security Preferences Mac transportintensive Security Policy Mac It says security setting do not allow this mac to use. When i start to do it from bootable disk with macos. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). I want to install new os. Devices with a t2 security processor. According to the small print in apple’s platform security. Security Policy Mac.
From sclubvast.weebly.com
Mac security settings for apps Security Policy Mac These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). By default, your mac uses the highest level of security, called full security. It says security setting do not allow this mac to use. For compliance policy processing we need the company portal here. When i start to do it from bootable disk. Security Policy Mac.
From www.intego.com
8 Mac security and privacy features to set up right away The Mac Security Policy Mac Before a legacy system extension (also known as a kernel. Devices with a t2 security processor. A shared architecture for security. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). By default, your mac uses the highest level of security, called full security. When i start to do it from bootable disk. Security Policy Mac.
From www.securemac.com
macOS Ventura Security and Privacy Guide SecureMac Security Policy Mac For compliance policy processing we need the company portal here. I want to install new os. It says security setting do not allow this mac to use. By default, your mac uses the highest level of security, called full security. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). When i start. Security Policy Mac.
From www.datamation.com
IT Security Policy Definition, Types & How to Create One Security Policy Mac These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). According to the small print in apple’s platform security guide, when you set up a new m1 mac, or set one up after restoring it in. I want to install new os. Before a legacy system extension (also known as a kernel. A. Security Policy Mac.
From greyreaders.com
How to set Mac security preferences for installation Grey Readers Security Policy Mac These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). On your mac, use privacy & security settings to manage the information your mac makes available to others across the internet or on a. I want to install new os. By default, your mac uses the highest level of security, called full security.. Security Policy Mac.
From www.lifewire.com
Using the Mac Security Preference Pane Security Policy Mac For an enterprise deployment of macos devices, you should: According to the small print in apple’s platform security guide, when you set up a new m1 mac, or set one up after restoring it in. It says security setting do not allow this mac to use. By default, your mac uses the highest level of security, called full security. Before. Security Policy Mac.
From www.thesslstore.com
What Is a Message Authentication Code (MAC)? Hashed Out by The SSL Store™ Security Policy Mac For compliance policy processing we need the company portal here. For an enterprise deployment of macos devices, you should: It says security setting do not allow this mac to use. Before a legacy system extension (also known as a kernel. Devices with a t2 security processor. These are typically security configurations as well as configurations for usability or look and. Security Policy Mac.
From techlapse.com
How to Remove Apple Security Alert Scam [iPhone & Mac] TechLapse Security Policy Mac These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). For an enterprise deployment of macos devices, you should: When i start to do it from bootable disk with macos. It says security setting do not allow this mac to use. Before a legacy system extension (also known as a kernel. I want. Security Policy Mac.
From likosplex.weebly.com
Mac security settings for apps likosplex Security Policy Mac For an enterprise deployment of macos devices, you should: A shared architecture for security. Before a legacy system extension (also known as a kernel. When i start to do it from bootable disk with macos. I want to install new os. Devices with a t2 security processor. For compliance policy processing we need the company portal here. On your mac,. Security Policy Mac.
From www.youtube.com
How to Adjust the Security and Privacy Settings on macOS YouTube Security Policy Mac A shared architecture for security. For an enterprise deployment of macos devices, you should: On your mac, use privacy & security settings to manage the information your mac makes available to others across the internet or on a. For compliance policy processing we need the company portal here. According to the small print in apple’s platform security guide, when you. Security Policy Mac.
From imore.com
Mac Help Master Yosemite's Privacy settings iMore Security Policy Mac Before a legacy system extension (also known as a kernel. When i start to do it from bootable disk with macos. Devices with a t2 security processor. For compliance policy processing we need the company portal here. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). By default, your mac uses the. Security Policy Mac.
From www.macupdate.com
How to Encrypt Files and Folders on Mac [Updated 2020] Security Policy Mac It says security setting do not allow this mac to use. I want to install new os. A shared architecture for security. When i start to do it from bootable disk with macos. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). On your mac, use privacy & security settings to manage. Security Policy Mac.
From www.educba.com
Security Policies List of 6 Most Useful Security Policies Security Policy Mac According to the small print in apple’s platform security guide, when you set up a new m1 mac, or set one up after restoring it in. For compliance policy processing we need the company portal here. A shared architecture for security. Before a legacy system extension (also known as a kernel. It says security setting do not allow this mac. Security Policy Mac.
From macpaw.com
Here’s how to change security preferences on your Mac Security Policy Mac On your mac, use privacy & security settings to manage the information your mac makes available to others across the internet or on a. When i start to do it from bootable disk with macos. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). For compliance policy processing we need the company. Security Policy Mac.
From iboysoft.com
Access & Change Settings of Startup Security Utility (M1 Mac Included) Security Policy Mac A shared architecture for security. According to the small print in apple’s platform security guide, when you set up a new m1 mac, or set one up after restoring it in. By default, your mac uses the highest level of security, called full security. For compliance policy processing we need the company portal here. When i start to do it. Security Policy Mac.
From architect.salesforce.com
Security Policy Template Salesforce Architects Security Policy Mac According to the small print in apple’s platform security guide, when you set up a new m1 mac, or set one up after restoring it in. On your mac, use privacy & security settings to manage the information your mac makes available to others across the internet or on a. Devices with a t2 security processor. When i start to. Security Policy Mac.
From boofare.weebly.com
boofare Blog Security Policy Mac Devices with a t2 security processor. By default, your mac uses the highest level of security, called full security. Before a legacy system extension (also known as a kernel. I want to install new os. A shared architecture for security. For compliance policy processing we need the company portal here. For an enterprise deployment of macos devices, you should: It. Security Policy Mac.
From macpaw.com
Here’s how to change security preferences on your Mac Security Policy Mac It says security setting do not allow this mac to use. Devices with a t2 security processor. A shared architecture for security. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). Before a legacy system extension (also known as a kernel. By default, your mac uses the highest level of security, called. Security Policy Mac.
From www.etsy.com
Easy Network Security Policy Template Cybersecurity for Your Business Security Policy Mac Devices with a t2 security processor. These are typically security configurations as well as configurations for usability or look and feel (wallpaper etc.). On your mac, use privacy & security settings to manage the information your mac makes available to others across the internet or on a. It says security setting do not allow this mac to use. For an. Security Policy Mac.
From www.examples.com
Security Policy 16+ Examples, Format, Pdf Security Policy Mac On your mac, use privacy & security settings to manage the information your mac makes available to others across the internet or on a. When i start to do it from bootable disk with macos. By default, your mac uses the highest level of security, called full security. A shared architecture for security. According to the small print in apple’s. Security Policy Mac.
From www.examples.com
Security Policy 16+ Examples, Format, Pdf Security Policy Mac For an enterprise deployment of macos devices, you should: It says security setting do not allow this mac to use. On your mac, use privacy & security settings to manage the information your mac makes available to others across the internet or on a. Devices with a t2 security processor. A shared architecture for security. By default, your mac uses. Security Policy Mac.