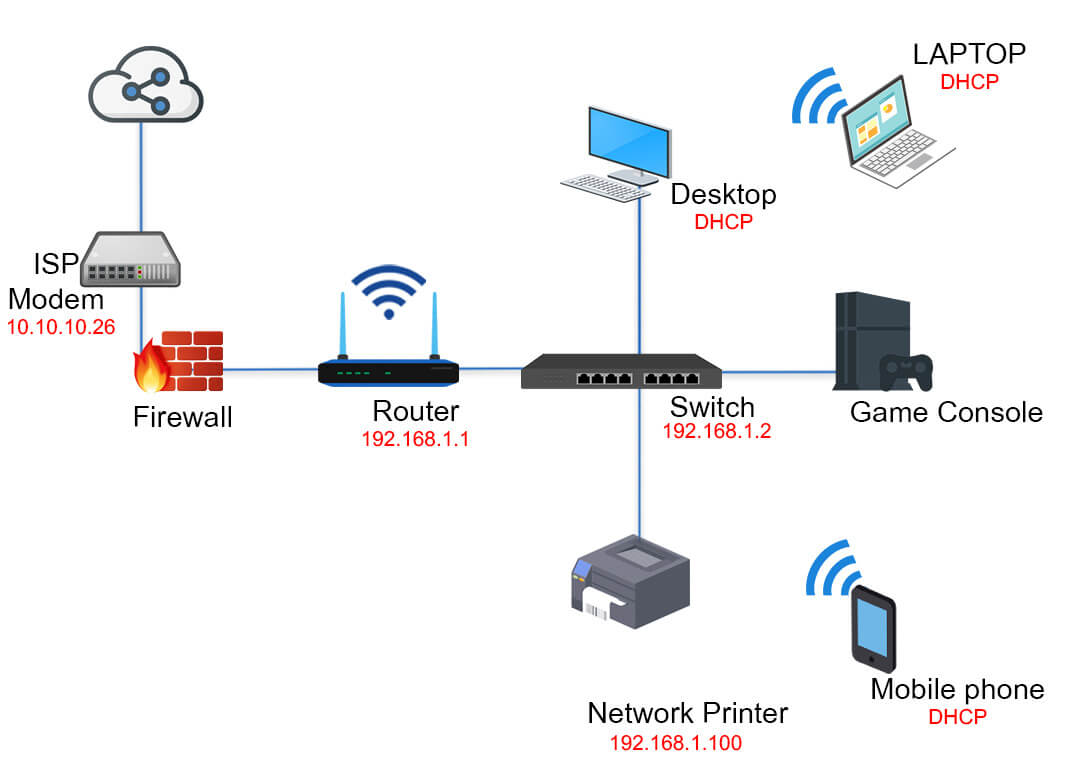
Data Link Firewall . The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros). We analyze the pros and cons of. To see if your firewall is blocking a website, app, or port on windows, go to windows firewall > advanced settings and check your outbound rules. The data link layer checks the fcs for errors, removes the mac addresses and passes the packet to the network layer. The firewalls in an ha pair use ha links to synchronize data and maintain state information. The network layer removes the ip addresses from the packet, turning it back. Some models of the firewall have dedicated ha. Read up on the advantages and disadvantages of five different types of firewalls, plus three firewall deployment models and firewall placement options. This article presentseight different types of firewalls that keep malicious traffic out of networks. The ha cluster peers synchronize sessions to protect against failure of the data center or a large security inspection point with horizontally.
from smartnetworkgeek.com
We analyze the pros and cons of. The ha cluster peers synchronize sessions to protect against failure of the data center or a large security inspection point with horizontally. The firewalls in an ha pair use ha links to synchronize data and maintain state information. The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros). The network layer removes the ip addresses from the packet, turning it back. Some models of the firewall have dedicated ha. To see if your firewall is blocking a website, app, or port on windows, go to windows firewall > advanced settings and check your outbound rules. This article presentseight different types of firewalls that keep malicious traffic out of networks. The data link layer checks the fcs for errors, removes the mac addresses and passes the packet to the network layer. Read up on the advantages and disadvantages of five different types of firewalls, plus three firewall deployment models and firewall placement options.
8 Effective Home Network Setup Diagram For Your House In 2023 Smart
Data Link Firewall The network layer removes the ip addresses from the packet, turning it back. To see if your firewall is blocking a website, app, or port on windows, go to windows firewall > advanced settings and check your outbound rules. The data link layer checks the fcs for errors, removes the mac addresses and passes the packet to the network layer. The firewalls in an ha pair use ha links to synchronize data and maintain state information. This article presentseight different types of firewalls that keep malicious traffic out of networks. The network layer removes the ip addresses from the packet, turning it back. We analyze the pros and cons of. Some models of the firewall have dedicated ha. Read up on the advantages and disadvantages of five different types of firewalls, plus three firewall deployment models and firewall placement options. The ha cluster peers synchronize sessions to protect against failure of the data center or a large security inspection point with horizontally. The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros).
From www.difference101.com
Firewall vs. VPN Key Differences, Pros & Cons, Similarities Data Link Firewall The firewalls in an ha pair use ha links to synchronize data and maintain state information. The network layer removes the ip addresses from the packet, turning it back. To see if your firewall is blocking a website, app, or port on windows, go to windows firewall > advanced settings and check your outbound rules. Some models of the firewall. Data Link Firewall.
From www.routexp.com
PaloAlto PA7000 Series Firewall Next Generation Firewalls Route XP Data Link Firewall The firewalls in an ha pair use ha links to synchronize data and maintain state information. The data link layer checks the fcs for errors, removes the mac addresses and passes the packet to the network layer. Some models of the firewall have dedicated ha. We analyze the pros and cons of. This article presentseight different types of firewalls that. Data Link Firewall.
From www.indiamart.com
DLink LAN Capable D'Link Firewall, 15W at Rs 6500 in Noida ID Data Link Firewall The network layer removes the ip addresses from the packet, turning it back. The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros). Some models of the firewall have dedicated ha. The ha cluster peers synchronize sessions to protect against failure of the data. Data Link Firewall.
From 5gstore.com
Understanding Firewalls The Key to Network Security To The Data Link Firewall The firewalls in an ha pair use ha links to synchronize data and maintain state information. We analyze the pros and cons of. Read up on the advantages and disadvantages of five different types of firewalls, plus three firewall deployment models and firewall placement options. To see if your firewall is blocking a website, app, or port on windows, go. Data Link Firewall.
From www.youtube.com
Next Generation Firewalls How to select, plan and deploy a modern Data Link Firewall We analyze the pros and cons of. Some models of the firewall have dedicated ha. The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros). The firewalls in an ha pair use ha links to synchronize data and maintain state information. This article presentseight. Data Link Firewall.
From www.informaticashop.com.br
mais imagens do produto Data Link Firewall To see if your firewall is blocking a website, app, or port on windows, go to windows firewall > advanced settings and check your outbound rules. The firewalls in an ha pair use ha links to synchronize data and maintain state information. The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer. Data Link Firewall.
From www.redeszone.net
Cómo configurar el firewall y el IDS IPS del DLink DBG2000 Data Link Firewall The ha cluster peers synchronize sessions to protect against failure of the data center or a large security inspection point with horizontally. The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros). This article presentseight different types of firewalls that keep malicious traffic out. Data Link Firewall.
From www.bhphotovideo.com
DLink NetDefend DFL260E Unified Threat Management DFL260ENB Data Link Firewall The network layer removes the ip addresses from the packet, turning it back. The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros). Some models of the firewall have dedicated ha. To see if your firewall is blocking a website, app, or port on. Data Link Firewall.
From www.conceptdraw.com
Network Security Diagrams Solution Data Link Firewall The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros). The ha cluster peers synchronize sessions to protect against failure of the data center or a large security inspection point with horizontally. Some models of the firewall have dedicated ha. The data link layer. Data Link Firewall.
From vesselautomation.com
Firewall in networking onboard Vessel Automation Data Link Firewall The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros). Some models of the firewall have dedicated ha. The firewalls in an ha pair use ha links to synchronize data and maintain state information. We analyze the pros and cons of. The ha cluster. Data Link Firewall.
From www.visme.co
Firewall Office Network Diagram Template Visme Data Link Firewall The network layer removes the ip addresses from the packet, turning it back. To see if your firewall is blocking a website, app, or port on windows, go to windows firewall > advanced settings and check your outbound rules. Read up on the advantages and disadvantages of five different types of firewalls, plus three firewall deployment models and firewall placement. Data Link Firewall.
From www.vrogue.co
What Are Next Generation Firewalls How The Cloud And vrogue.co Data Link Firewall Some models of the firewall have dedicated ha. The data link layer checks the fcs for errors, removes the mac addresses and passes the packet to the network layer. We analyze the pros and cons of. Read up on the advantages and disadvantages of five different types of firewalls, plus three firewall deployment models and firewall placement options. The network. Data Link Firewall.
From www.youtube.com
DLink DSR Series Firewall Introduction YouTube Data Link Firewall Some models of the firewall have dedicated ha. Read up on the advantages and disadvantages of five different types of firewalls, plus three firewall deployment models and firewall placement options. To see if your firewall is blocking a website, app, or port on windows, go to windows firewall > advanced settings and check your outbound rules. The ha cluster peers. Data Link Firewall.
From www.difference101.com
Firewall vs. Router Key Differences, Pros & Cons, Similarities Data Link Firewall This article presentseight different types of firewalls that keep malicious traffic out of networks. We analyze the pros and cons of. The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros). The network layer removes the ip addresses from the packet, turning it back.. Data Link Firewall.
From www.conceptdraw.com
Network Security Firewall between LAN and WAN Network Security Data Link Firewall The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros). The firewalls in an ha pair use ha links to synchronize data and maintain state information. The network layer removes the ip addresses from the packet, turning it back. The ha cluster peers synchronize. Data Link Firewall.
From tutorialslink.com
What is Edge Firewall and NSX Logical Firewall? Tutorials Link Data Link Firewall The firewalls in an ha pair use ha links to synchronize data and maintain state information. The network layer removes the ip addresses from the packet, turning it back. This article presentseight different types of firewalls that keep malicious traffic out of networks. The data link layer checks the fcs for errors, removes the mac addresses and passes the packet. Data Link Firewall.
From www.gns3network.com
The Complete Guide to Network Firewall 2023 GNS3 Network Data Link Firewall Some models of the firewall have dedicated ha. The network layer removes the ip addresses from the packet, turning it back. The data link layer checks the fcs for errors, removes the mac addresses and passes the packet to the network layer. Read up on the advantages and disadvantages of five different types of firewalls, plus three firewall deployment models. Data Link Firewall.
From blog.ipspace.net
Distributed Firewalls a Ticking Bomb « blog Data Link Firewall Read up on the advantages and disadvantages of five different types of firewalls, plus three firewall deployment models and firewall placement options. The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros). We analyze the pros and cons of. The ha cluster peers synchronize. Data Link Firewall.
From www.cisco-supplier.com
What role does a switch, router, firewall, and wireless AP play in the Data Link Firewall Some models of the firewall have dedicated ha. We analyze the pros and cons of. The data link layer checks the fcs for errors, removes the mac addresses and passes the packet to the network layer. The ha cluster peers synchronize sessions to protect against failure of the data center or a large security inspection point with horizontally. To see. Data Link Firewall.
From www.f5.com
Data Center Firewall (BIGIP v11 LTM) Data Link Firewall This article presentseight different types of firewalls that keep malicious traffic out of networks. Some models of the firewall have dedicated ha. The data link layer checks the fcs for errors, removes the mac addresses and passes the packet to the network layer. We analyze the pros and cons of. To see if your firewall is blocking a website, app,. Data Link Firewall.
From www.youtube.com
D Link Firewall SD WAN VPN DBG 2000 Cloud Managed YouTube Data Link Firewall Read up on the advantages and disadvantages of five different types of firewalls, plus three firewall deployment models and firewall placement options. The network layer removes the ip addresses from the packet, turning it back. This article presentseight different types of firewalls that keep malicious traffic out of networks. We analyze the pros and cons of. The ha cluster peers. Data Link Firewall.
From www.bullfrag.com
Configure The DLink DSR1000AC Router Firewall With Advanced ACLs Data Link Firewall To see if your firewall is blocking a website, app, or port on windows, go to windows firewall > advanced settings and check your outbound rules. The network layer removes the ip addresses from the packet, turning it back. This article presentseight different types of firewalls that keep malicious traffic out of networks. The firewalls in an ha pair use. Data Link Firewall.
From www.packetswitch.co.uk
A simple guide to Palo Alto Active/Passive Failover Data Link Firewall The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros). The network layer removes the ip addresses from the packet, turning it back. The ha cluster peers synchronize sessions to protect against failure of the data center or a large security inspection point with. Data Link Firewall.
From www.slideserve.com
PPT Firewall Configuration Strategies PowerPoint Presentation, free Data Link Firewall To see if your firewall is blocking a website, app, or port on windows, go to windows firewall > advanced settings and check your outbound rules. Read up on the advantages and disadvantages of five different types of firewalls, plus three firewall deployment models and firewall placement options. The data link layer facilitates data transfer between devices on the same. Data Link Firewall.
From www.amazon.com
DLink NetDefend DFL210 VPN/Firewall 4 x 10/100BaseTX Data Link Firewall The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros). To see if your firewall is blocking a website, app, or port on windows, go to windows firewall > advanced settings and check your outbound rules. This article presentseight different types of firewalls that. Data Link Firewall.
From www.triella.com
Firewall Port Security How Network Access is Protected Data Link Firewall The firewalls in an ha pair use ha links to synchronize data and maintain state information. Read up on the advantages and disadvantages of five different types of firewalls, plus three firewall deployment models and firewall placement options. The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine. Data Link Firewall.
From www.broadbandsearch.net
How an Firewall Protects Your Online Privacy BroadbandSearch Data Link Firewall The data link layer checks the fcs for errors, removes the mac addresses and passes the packet to the network layer. To see if your firewall is blocking a website, app, or port on windows, go to windows firewall > advanced settings and check your outbound rules. The network layer removes the ip addresses from the packet, turning it back.. Data Link Firewall.
From www.datalinknetworks.net
Top 3 Firewalls for Your Business in 2023 Data Link Firewall The ha cluster peers synchronize sessions to protect against failure of the data center or a large security inspection point with horizontally. The firewalls in an ha pair use ha links to synchronize data and maintain state information. This article presentseight different types of firewalls that keep malicious traffic out of networks. The data link layer facilitates data transfer between. Data Link Firewall.
From www.redeszone.net
Configura el firewall del router DLink DSR1000AC con ACL avanzadas Data Link Firewall Some models of the firewall have dedicated ha. This article presentseight different types of firewalls that keep malicious traffic out of networks. The data link layer checks the fcs for errors, removes the mac addresses and passes the packet to the network layer. Read up on the advantages and disadvantages of five different types of firewalls, plus three firewall deployment. Data Link Firewall.
From lightyear.ai
Where Does a Network Firewall Go? Network Perimeter Security Data Link Firewall Some models of the firewall have dedicated ha. To see if your firewall is blocking a website, app, or port on windows, go to windows firewall > advanced settings and check your outbound rules. The ha cluster peers synchronize sessions to protect against failure of the data center or a large security inspection point with horizontally. The data link layer. Data Link Firewall.
From kirelos.com
What is Firewall? An Introduction Guide Kirelos Blog Data Link Firewall We analyze the pros and cons of. The data link layer checks the fcs for errors, removes the mac addresses and passes the packet to the network layer. This article presentseight different types of firewalls that keep malicious traffic out of networks. The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer. Data Link Firewall.
From www.numerade.com
SOLVED firewalls are designed to operate at the media access control Data Link Firewall The firewalls in an ha pair use ha links to synchronize data and maintain state information. Some models of the firewall have dedicated ha. We analyze the pros and cons of. The network layer removes the ip addresses from the packet, turning it back. The data link layer facilitates data transfer between devices on the same network, and, finally, the. Data Link Firewall.
From smartnetworkgeek.com
8 Effective Home Network Setup Diagram For Your House In 2023 Smart Data Link Firewall The data link layer facilitates data transfer between devices on the same network, and, finally, the physical layer transfers data in machine language (ones and zeros). The ha cluster peers synchronize sessions to protect against failure of the data center or a large security inspection point with horizontally. The data link layer checks the fcs for errors, removes the mac. Data Link Firewall.
From www.slideserve.com
PPT Exploring Firewall Types and Technologies for Network Security Data Link Firewall We analyze the pros and cons of. Some models of the firewall have dedicated ha. This article presentseight different types of firewalls that keep malicious traffic out of networks. The firewalls in an ha pair use ha links to synchronize data and maintain state information. The data link layer facilitates data transfer between devices on the same network, and, finally,. Data Link Firewall.
From www.techmey.com
Where is Firewall Placed in a Network to Get Best Security? Techmey Data Link Firewall We analyze the pros and cons of. Some models of the firewall have dedicated ha. The ha cluster peers synchronize sessions to protect against failure of the data center or a large security inspection point with horizontally. The network layer removes the ip addresses from the packet, turning it back. This article presentseight different types of firewalls that keep malicious. Data Link Firewall.