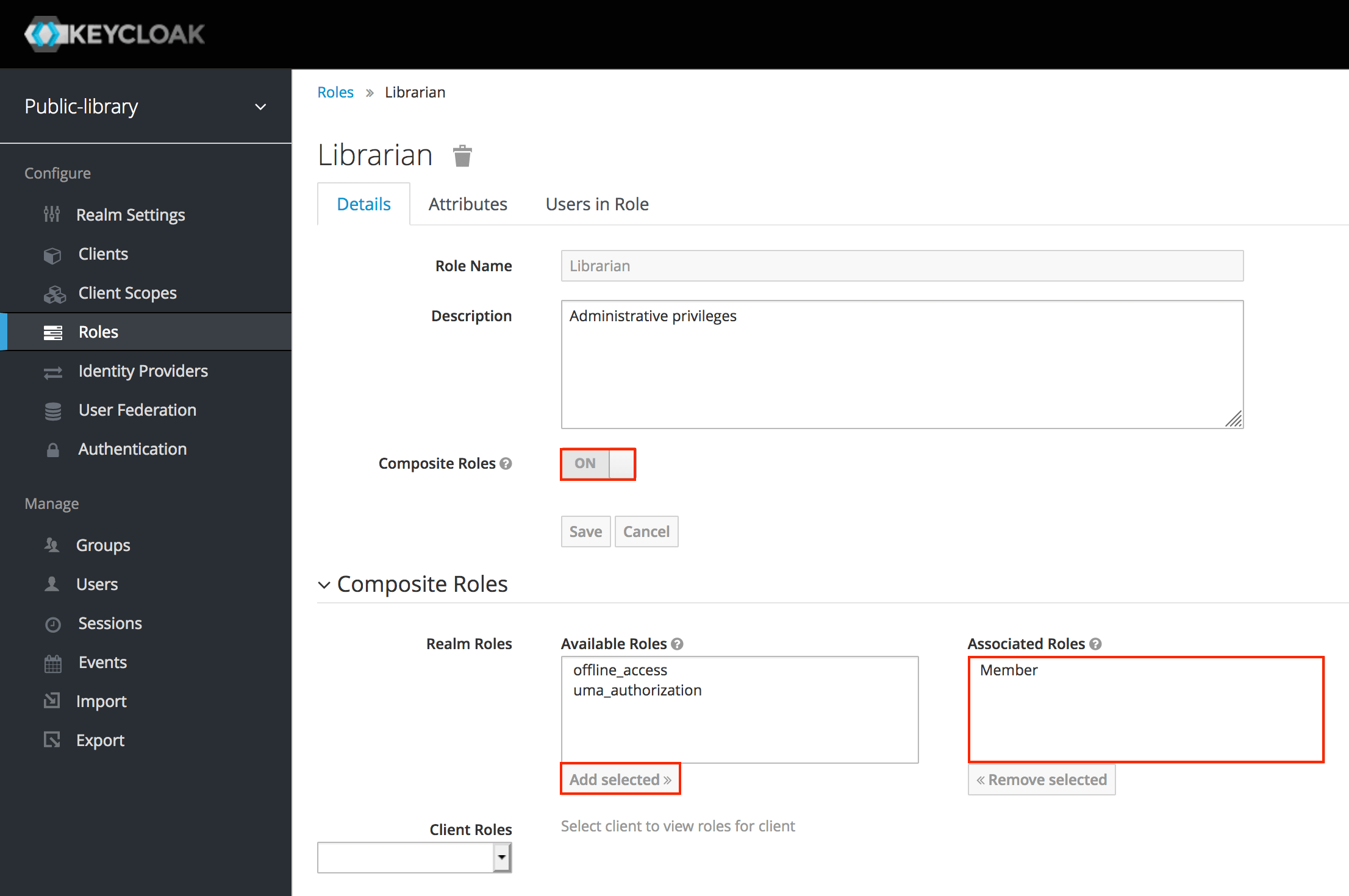
Keycloak User Authorization . Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Learn how to use keycloak rest api to enable authentication and authorization for a java application. Learn how to use the keycloak authz client to manage and check permissions for resource servers.
from www.thomasvitale.com
In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. Learn how to use the keycloak authz client to manage and check permissions for resource servers. Learn how to use keycloak rest api to enable authentication and authorization for a java application. In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to.
Keycloak Basic Configuration for Authentication and Authorization
Keycloak User Authorization Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. Learn how to use keycloak rest api to enable authentication and authorization for a java application. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Learn how to use the keycloak authz client to manage and check permissions for resource servers. In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,.
From medium.com
Keycloak for Identity and Access Management & High Availability Keycloak User Authorization Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. Learn how to use keycloak rest. Keycloak User Authorization.
From walkingtree.tech
Keycloak Identity Access Management Solutions WalkingTree Technologies Keycloak User Authorization In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. Learn how to use the keycloak authz client to manage and check permissions for resource servers. Keycloak is based on. Keycloak User Authorization.
From github.com
GitHub 5stones/keycloakemailotp A Keycloak Authentication step Keycloak User Authorization Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Learn how to use the keycloak authz client to manage and check permissions for resource servers. In this article, we'll dive into. Keycloak User Authorization.
From jpassing.com
Using a Google Cloud service account to authenticate to KeyCloak Keycloak User Authorization Learn how to use the keycloak authz client to manage and check permissions for resource servers. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for. Keycloak User Authorization.
From mailpiler.com
Keycloak Authentication Keycloak User Authorization In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create. Keycloak User Authorization.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak User Authorization In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. Learn how to use the keycloak authz client to manage and check permissions for resource servers. Learn how to use keycloak rest api to enable authentication and authorization for a java application. In this article, we'll. Keycloak User Authorization.
From www.keycloak.org
Authorization Services Guide Keycloak User Authorization Learn how to use the keycloak authz client to manage and check permissions for resource servers. In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. Learn how to use keycloak rest api to enable authentication and authorization for a java application. Therefore, the applications don't. Keycloak User Authorization.
From www.helikube.de
Part 1 Keycloak Setup for running Keycloak Authorization Sample Keycloak User Authorization Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for. Keycloak User Authorization.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak User Authorization In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. Keycloak is based on. Keycloak User Authorization.
From appsec-tmr.gitbook.io
Authorization Code Grant Demo Keycloak User Authorization Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Learn how to use keycloak rest api to enable authentication and authorization for a java application. In chapter 8, thorgersen and silva. Keycloak User Authorization.
From sciencegateways.org
sciencegateways Tech Blog Using Keycloak to Provide Authentication Keycloak User Authorization In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. Learn how to use the keycloak authz client to manage and check permissions for resource servers. Keycloak is based on a set of administrative uis and a restful. Keycloak User Authorization.
From www.helikube.de
Part 1 Keycloak Setup for running Keycloak Authorization Sample Keycloak User Authorization In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. Learn how to use keycloak rest api to enable authentication and authorization for a java application. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. Keycloak is based on. Keycloak User Authorization.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak User Authorization Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Learn how to use the keycloak authz client to manage and check permissions for resource servers. In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the. Keycloak User Authorization.
From community.ibm.com
Extending Keycloak's authentication capabilities by integrating with Keycloak User Authorization Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Learn how to use the keycloak authz client to manage and check permissions for resource servers. Learn how to use keycloak rest api to enable authentication and authorization for a java application. In chapter 8, thorgersen and silva. Keycloak User Authorization.
From www.janua.fr
understanding client Authenticator security with Keycloak JANUA Keycloak User Authorization In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. Learn how to use the keycloak authz client to manage and check permissions for resource servers. Keycloak is based on a set of administrative uis and a restful. Keycloak User Authorization.
From andrevianna-1662831931436.hashnode.dev
Understanding the Powerful Keycloak Tool Keycloak User Authorization Learn how to use keycloak rest api to enable authentication and authorization for a java application. In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Therefore, the applications don't. Keycloak User Authorization.
From www.puppeteers.net
Keycloak authorization services terminology Puppeteers Oy Keycloak User Authorization In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create. Keycloak User Authorization.
From suberi.pics
Authentication and authorization of users through Keycloak (2023) Keycloak User Authorization Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for. Keycloak User Authorization.
From developers.redhat.com
Authentication and authorization using the Keycloak REST API Red Hat Keycloak User Authorization In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Learn how to use the keycloak authz client to manage and check permissions for resource servers. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. In chapter 8, thorgersen and silva. Keycloak User Authorization.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak User Authorization In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Learn how to use the keycloak authz client to manage and check permissions for resource servers. Learn how to use keycloak rest api to enable authentication and authorization for a java application. Keycloak is based on a set of administrative uis and a restful. Keycloak User Authorization.
From suberi.pics
Authentication and authorization of users through Keycloak (2023) Keycloak User Authorization In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate. Keycloak User Authorization.
From www.redhat.com
How to architect OAuth 2.0 authorization using Keycloak Enable Architect Keycloak User Authorization Learn how to use keycloak rest api to enable authentication and authorization for a java application. In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. Learn how to use the keycloak authz client to manage and check. Keycloak User Authorization.
From www.youtube.com
MySQL Keycloak User federation using existing MySQL database for Keycloak User Authorization Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. Learn how to use keycloak rest api to enable authentication and authorization for a java application. In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. Learn how to use. Keycloak User Authorization.
From witekio.com
Authentication Management Focus On Keycloak Witekio Keycloak User Authorization Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Learn how to use keycloak rest api to enable authentication and authorization for a java application. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. Learn how to use the keycloak. Keycloak User Authorization.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak User Authorization Learn how to use the keycloak authz client to manage and check permissions for resource servers. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. In chapter 8, thorgersen and silva. Keycloak User Authorization.
From scalac.io
User Authentication with Keycloak Part 1 React frontend Keycloak User Authorization In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Learn how to use keycloak rest api to enable authentication and authorization for a. Keycloak User Authorization.
From www.helikube.de
Part 1 Keycloak Setup for running Keycloak Authorization Sample Keycloak User Authorization Learn how to use the keycloak authz client to manage and check permissions for resource servers. In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. Therefore, the applications don't. Keycloak User Authorization.
From www.springcloud.io
Unified authentication authorization platform keycloak Introduction Keycloak User Authorization Learn how to use the keycloak authz client to manage and check permissions for resource servers. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Learn how to use keycloak rest api to enable authentication and authorization for a java application. In this article, we'll dive into. Keycloak User Authorization.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak User Authorization In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Learn how to use keycloak rest api to enable authentication and authorization for a. Keycloak User Authorization.
From docs.geoserver.org
Authentication with Keycloak — GeoServer 2.26.x User Manual Keycloak User Authorization Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. In chapter 8, thorgersen and silva explained keycloak authorization strategies, covering the basics of iam authorization and how to use keycloak for rbac, gbac,. Learn how to use keycloak rest api to enable authentication and authorization for a. Keycloak User Authorization.
From www.kloia.com
Simplifying Authentication and Authorization with Keycloak on AWS EKS Keycloak User Authorization Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Learn how to use keycloak rest api to enable authentication and authorization for a java application. Learn how to use the keycloak authz client to manage and check. Keycloak User Authorization.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak User Authorization In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Learn how to use keycloak rest. Keycloak User Authorization.
From www.redpill-linpro.com
Get started with OpenID Connect and Keycloak /techblog Keycloak User Authorization Learn how to use keycloak rest api to enable authentication and authorization for a java application. In this article, we'll dive into keycloak's authorization entities, how they're interconnected, and demonstrate how to. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. In chapter 8, thorgersen and silva. Keycloak User Authorization.
From suberi.pics
Authentication and authorization of users through Keycloak (2023) Keycloak User Authorization Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. Learn how to use the keycloak authz client to manage and check permissions for resource servers. Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. In this article, we'll dive into. Keycloak User Authorization.
From www.linkedin.com
Simplify User Authentication and Authorization with Keycloak Keycloak User Authorization Therefore, the applications don't have to deal with login forms, user authentication, and user account storage. Learn how to use the keycloak authz client to manage and check permissions for resource servers. Keycloak is based on a set of administrative uis and a restful api, and provides the necessary means to create permissions for. In this article, we'll dive into. Keycloak User Authorization.