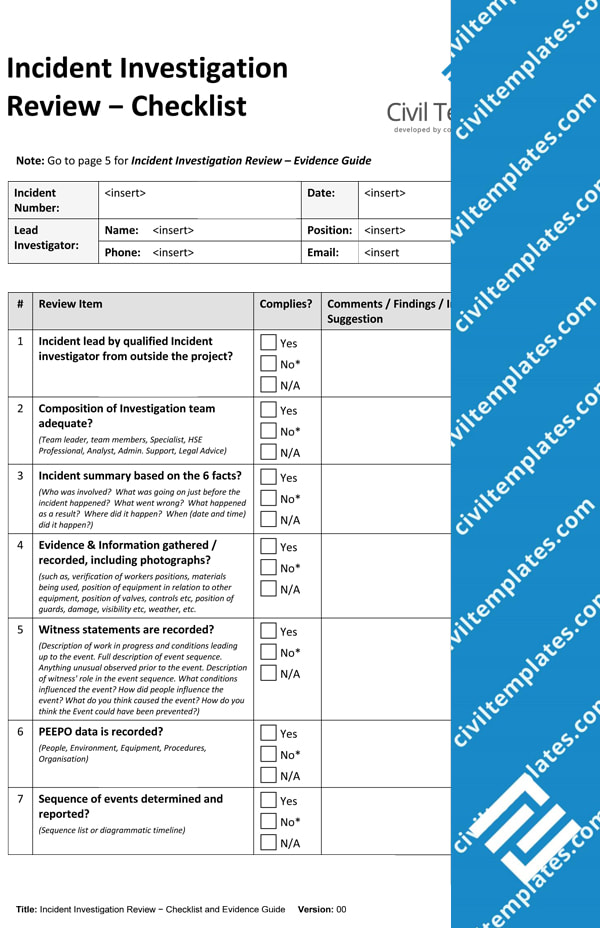
Incident Response Audit Checklist . A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. Before you move on, make sure you can explain the four stages of the incident response process: It covers incident identification, containment and eradication, recovery and lessons.
from template.mapadapalavra.ba.gov.br
A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. It covers incident identification, containment and eradication, recovery and lessons. Before you move on, make sure you can explain the four stages of the incident response process: This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the.
Incident Response Checklist Templates
Incident Response Audit Checklist This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. Before you move on, make sure you can explain the four stages of the incident response process: This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. It covers incident identification, containment and eradication, recovery and lessons.
From studylib.net
Emergency Response Checklist Incident Recognition and Reporting Workplace Incident Response Audit Checklist This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. It covers incident identification, containment and eradication, recovery and lessons. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. Before you move on, make sure you can explain the four stages of the incident. Incident Response Audit Checklist.
From www.giva.uk.com
ITIL Incident Management Best Practises Giva Incident Response Audit Checklist This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. It covers incident identification, containment and eradication, recovery and lessons. Before you move on, make sure you can explain the four stages of the incident response process: This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently. Incident Response Audit Checklist.
From www.scribd.com
Emergency Response Planning Checklist Incident Response Audit Checklist This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. It covers incident identification, containment and eradication, recovery and. Incident Response Audit Checklist.
From www.checklist.templateral.com
√ Free Printable Incident Response Checklist Template Checklist Templates Incident Response Audit Checklist This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. Before you move on, make sure you can explain the four stages of the incident response process: It covers incident identification, containment and eradication, recovery and. Incident Response Audit Checklist.
From templates.rjuuc.edu.np
Incident Response Checklist Templates Incident Response Audit Checklist Before you move on, make sure you can explain the four stages of the incident response process: It covers incident identification, containment and eradication, recovery and lessons. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and.. Incident Response Audit Checklist.
From old.sermitsiaq.ag
Incident Response Checklist Templates Incident Response Audit Checklist It covers incident identification, containment and eradication, recovery and lessons. This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. Before you move on, make sure you can explain the four stages of the incident. Incident Response Audit Checklist.
From template.mapadapalavra.ba.gov.br
Incident Response Checklist Templates Incident Response Audit Checklist This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. It covers incident identification, containment and eradication, recovery and. Incident Response Audit Checklist.
From www.cm-alliance.com
Cyber Incident Response Checklist, Data Breach Cyber Management Alliance Incident Response Audit Checklist Before you move on, make sure you can explain the four stages of the incident response process: This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. A cyber security audit checklist includes components such as. Incident Response Audit Checklist.
From www.scribd.com
Sample Investigation Improvement Checklist Incident Investigation Guideline Incident Response Audit Checklist Before you move on, make sure you can explain the four stages of the incident response process: This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. It covers incident identification, containment and eradication, recovery and lessons. A cyber security audit checklist includes components such as network security assessments, incident response plans,. Incident Response Audit Checklist.
From studylib.net
HSEF1201.1 Emergency Preparedness Audit Checklist Incident Response Audit Checklist This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. It covers incident identification, containment and eradication, recovery and lessons. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. A cyber security audit checklist includes components such as network security assessments, incident response plans, access. Incident Response Audit Checklist.
From www.cisecurity.org
Cyber Incident Checklist Incident Response Audit Checklist This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. It covers incident identification, containment and eradication, recovery and lessons. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. Before you move on, make sure you can explain the four stages of the incident. Incident Response Audit Checklist.
From templates.rjuuc.edu.np
Incident Response Checklist Templates Incident Response Audit Checklist This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. It covers incident identification, containment and eradication, recovery and lessons. Before you move on, make sure you can explain the four stages of the incident response process: A cyber security audit checklist includes components such as network security assessments, incident response plans,. Incident Response Audit Checklist.
From www.slideteam.net
Cyber Security Incident Response Plan Checklist PPT Presentation Incident Response Audit Checklist This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. Before you move on, make sure you can explain the four stages of the incident response process: A cyber security audit checklist includes components such as. Incident Response Audit Checklist.
From www.etsy.com
Incident Response Checklist Cyber Event Form Editable Word Docx Instant Incident Response Audit Checklist Before you move on, make sure you can explain the four stages of the incident response process: It covers incident identification, containment and eradication, recovery and lessons. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and.. Incident Response Audit Checklist.
From 1streporting.com
The Incident Management Checklist (With 12 Tips For Best Use) Incident Response Audit Checklist A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. Before you move on, make sure you can explain the four stages of the incident response process: This incident response checklist is structured around the ipdrr (identify,. Incident Response Audit Checklist.
From frsecure.com
Incident Response Plan Template FRSecure Incident Response Audit Checklist This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. It covers incident identification, containment and eradication, recovery and. Incident Response Audit Checklist.
From studylib.net
Department Incident Response Checklist Incident Response Audit Checklist This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. It covers incident identification, containment and eradication, recovery and lessons. This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by. Incident Response Audit Checklist.
From www.yumpu.com
Inspection Checklist for Incident Response Select Agent Program Incident Response Audit Checklist This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. It covers incident identification, containment and eradication, recovery and lessons. A cyber security audit checklist includes components such as network security assessments, incident response plans, access. Incident Response Audit Checklist.
From template.mapadapalavra.ba.gov.br
Incident Response Checklist Templates Incident Response Audit Checklist Before you move on, make sure you can explain the four stages of the incident response process: It covers incident identification, containment and eradication, recovery and lessons. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control.. Incident Response Audit Checklist.
From templateroad.com
Notion Incident Report First Response Checklist Template Template Incident Response Audit Checklist A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. It covers incident identification, containment and eradication, recovery and lessons. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently. Incident Response Audit Checklist.
From clearinfosec.com
NIST for Computer Security Incident Handling Clear Incident Response Audit Checklist It covers incident identification, containment and eradication, recovery and lessons. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. Before you move on, make sure you can explain the four stages of the incident response process:. Incident Response Audit Checklist.
From 1streporting.com
The Cyber Security Incident Response Plan Checklist For Business 1st Incident Response Audit Checklist It covers incident identification, containment and eradication, recovery and lessons. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. Before you move on, make sure you can explain the four stages of the incident response process: A cyber security audit checklist includes components such as network security assessments, incident response plans, access control.. Incident Response Audit Checklist.
From www.rapid7.com
Incident Response Plan Templates Incident Response Audit Checklist Before you move on, make sure you can explain the four stages of the incident response process: A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. This incident response checklist is structured around the ipdrr (identify,. Incident Response Audit Checklist.
From clickup.com
10 Free Incident Report Templates in ClickUp Docs, Word, and Excel Incident Response Audit Checklist It covers incident identification, containment and eradication, recovery and lessons. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. Before you move on, make sure you can explain the four stages of the incident response process: A cyber security audit checklist includes components such as network security assessments, incident response plans, access control.. Incident Response Audit Checklist.
From checklist.gg
Incident response plan checklist Incident Response Audit Checklist It covers incident identification, containment and eradication, recovery and lessons. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. Before you move on, make sure you can explain the four stages of the incident response process: This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by. Incident Response Audit Checklist.
From mavink.com
Incident Response Checklist Templates Incident Response Audit Checklist This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. It covers incident identification, containment and eradication, recovery and lessons. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. Before you move on, make sure you can explain the four stages of the incident response process:. Incident Response Audit Checklist.
From www.template.net
IT Incident Response Checklist Template in Word, PDF, Google Docs Incident Response Audit Checklist This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. Before you move on, make sure you can explain the four stages of the incident response process: This incident response checklist is structured around the ipdrr (identify,. Incident Response Audit Checklist.
From shawnetuma.com
Cyber Incident Response Checklist Business Cyber Risk Incident Response Audit Checklist Before you move on, make sure you can explain the four stages of the incident response process: This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. It covers incident identification, containment and eradication, recovery and lessons. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control.. Incident Response Audit Checklist.
From www.scribd.com
Audit Checklist for Incident Investigation Report Incident Response Audit Checklist This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. Before you move on, make sure you can explain the four stages of the incident response process: A cyber security audit checklist includes components such as. Incident Response Audit Checklist.
From martellotech.com
Best Practices for Incident Management Martello Incident Response Audit Checklist It covers incident identification, containment and eradication, recovery and lessons. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. Before you move on, make sure you can explain the four stages of the incident response process:. Incident Response Audit Checklist.
From cashier.mijndomein.nl
Incident Response Checklist Templates Incident Response Audit Checklist A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. It covers incident identification, containment and eradication, recovery and lessons. Before you move on, make sure you can explain the four stages of the incident response process: This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed. Incident Response Audit Checklist.
From www.slideteam.net
Incident Management Process Audit Checklist Ppt Powerpoint Background Incident Response Audit Checklist This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control. Before you move on, make sure you can explain the four stages of the incident response process: This incident response checklist is structured around the ipdrr (identify,. Incident Response Audit Checklist.
From blueteamresources.in
2023 Cyber Security Audit Checklist Strengthen Your Defense Incident Response Audit Checklist Before you move on, make sure you can explain the four stages of the incident response process: It covers incident identification, containment and eradication, recovery and lessons. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. A cyber security audit checklist includes components such as network security assessments, incident response plans, access control.. Incident Response Audit Checklist.
From old.sermitsiaq.ag
Incident Response Flow Chart Template Incident Response Audit Checklist This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. Before you move on, make sure you can explain the four stages of the incident response process: This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. A cyber security audit checklist includes components such as. Incident Response Audit Checklist.
From duffycompliance.com
Incident Response Checklist Duffy Compliance Services Incident Response Audit Checklist It covers incident identification, containment and eradication, recovery and lessons. This incident response checklist is structured around the ipdrr (identify, protect, detect, response, recover) framework developed by the. This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and. Before you move on, make sure you can explain the four stages of the incident response. Incident Response Audit Checklist.