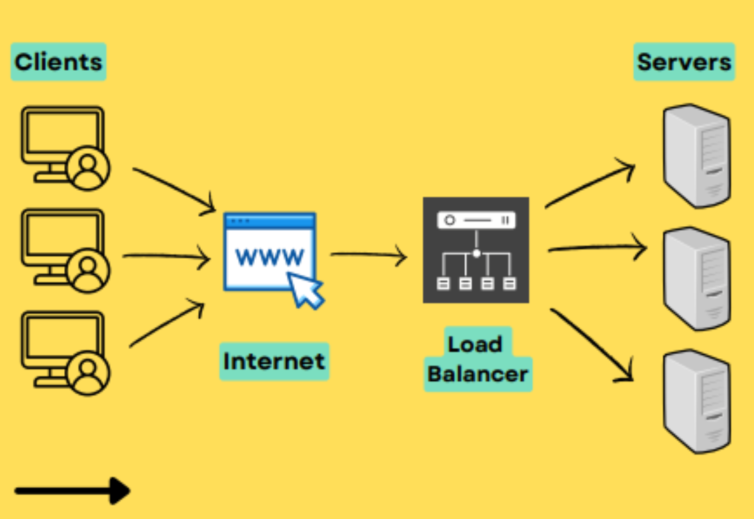
F5 Load Balancer Rules . This method differs from least connections (member), in that the least connections method measures connections. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. As depicted, the load balancer. With this common vocabulary established, let’s examine the basic load balancing transaction. It distributes load of incoming client requests based various. Let your applications help decide where to send your clients with the most. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via.
from techjunction.co
It distributes load of incoming client requests based various. This method differs from least connections (member), in that the least connections method measures connections. With this common vocabulary established, let’s examine the basic load balancing transaction. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. As depicted, the load balancer. Let your applications help decide where to send your clients with the most. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server.
F5 Load Balancer Training Tech Junction
F5 Load Balancer Rules It distributes load of incoming client requests based various. This method differs from least connections (member), in that the least connections method measures connections. Let your applications help decide where to send your clients with the most. As depicted, the load balancer. It distributes load of incoming client requests based various. With this common vocabulary established, let’s examine the basic load balancing transaction. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via.
From technotes.adelerhof.eu
Basic LoadBalancer Scenarios Explained Technotes F5 Load Balancer Rules Let your applications help decide where to send your clients with the most. It distributes load of incoming client requests based various. With this common vocabulary established, let’s examine the basic load balancing transaction. This method differs from least connections (member), in that the least connections method measures connections. Key network and application functions, such as load balancing, encryption, acceleration,. F5 Load Balancer Rules.
From www.f5.com
Load Balancing on AWS Know Your Options F5 F5 Load Balancer Rules With this common vocabulary established, let’s examine the basic load balancing transaction. As depicted, the load balancer. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. It distributes load of incoming client requests based various. This method differs from least connections (member), in that the least connections. F5 Load Balancer Rules.
From www.youtube.com
GCPcloud Google Cloud Platform Load Balancer Concepts Types of Load F5 Load Balancer Rules It distributes load of incoming client requests based various. This method differs from least connections (member), in that the least connections method measures connections. With this common vocabulary established, let’s examine the basic load balancing transaction. As depicted, the load balancer. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints. F5 Load Balancer Rules.
From www.f5.com.cn
F5 WAF Support for AWS Security Hub Empowering Centralized Security F5 Load Balancer Rules In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. As depicted, the load balancer. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. Let your applications help decide where to send your clients with the most. With this common. F5 Load Balancer Rules.
From blogs.vmware.com
Tanzu Grid MultiCloud and F5 BIGIP Series Load Balancer F5 Load Balancer Rules As depicted, the load balancer. Let your applications help decide where to send your clients with the most. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. It distributes load of incoming client requests based various. This method differs from least connections (member), in that the least connections method measures connections. In. F5 Load Balancer Rules.
From techjunction.co
F5 Load Balancer Training Tech Junction F5 Load Balancer Rules With this common vocabulary established, let’s examine the basic load balancing transaction. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. Let your applications help decide where to send your clients with the most. Key network and application functions, such as load balancing, encryption, acceleration, and security,. F5 Load Balancer Rules.
From mavink.com
F5 Load Balancer Configuration F5 Load Balancer Rules In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. With this common vocabulary established, let’s examine the basic load balancing transaction. As depicted, the load balancer. This method differs from. F5 Load Balancer Rules.
From www.netapp.com
NetApp IT Perspective StorageGRID F5 Load Balancer Design F5 Load Balancer Rules In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. With this common vocabulary established, let’s examine the basic load balancing transaction. This method differs from least connections (member), in that the least connections method measures connections. Key network and application functions, such as load balancing, encryption, acceleration,. F5 Load Balancer Rules.
From www.youtube.com
How to secure AWS Load Balancer with Listener Rules YouTube F5 Load Balancer Rules With this common vocabulary established, let’s examine the basic load balancing transaction. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. Let your applications help decide where to send your clients with the most. This method differs from least connections (member), in that the least connections method measures connections. In mesh, a. F5 Load Balancer Rules.
From www.imperva.com
Without session persistence, the web application would have to maintain F5 Load Balancer Rules This method differs from least connections (member), in that the least connections method measures connections. Let your applications help decide where to send your clients with the most. It distributes load of incoming client requests based various. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. As depicted, the load balancer. In. F5 Load Balancer Rules.
From clouddocs.f5.com
5.4.1. Apply F5 Networks WAF Rules to an AWS Application Load Balancer F5 Load Balancer Rules With this common vocabulary established, let’s examine the basic load balancing transaction. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. As depicted, the load balancer. It distributes load of. F5 Load Balancer Rules.
From www.f5.com.cn
负载均衡入门:具体细节 F5 F5 Load Balancer Rules As depicted, the load balancer. Let your applications help decide where to send your clients with the most. It distributes load of incoming client requests based various. This method differs from least connections (member), in that the least connections method measures connections. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. With. F5 Load Balancer Rules.
From www.ssltrust.co.uk
Setup SSL/TLS with F5 BigIP SSLTrust F5 Load Balancer Rules Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. It distributes load of incoming client requests based various. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. As depicted, the load balancer. This method differs from least connections (member),. F5 Load Balancer Rules.
From mavink.com
F5 Load Balancer Architecture Diagram F5 Load Balancer Rules With this common vocabulary established, let’s examine the basic load balancing transaction. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. This method differs from least connections (member), in that the least connections method measures connections. Let your applications help decide where to send your clients with. F5 Load Balancer Rules.
From careerkafe.blogspot.com
Study Material Explaining SSL on F5 BIGIP LTM Load Balancer F5 Load Balancer Rules With this common vocabulary established, let’s examine the basic load balancing transaction. As depicted, the load balancer. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. This method differs from least connections (member), in that the least connections method measures connections. Let your applications help decide where. F5 Load Balancer Rules.
From www.youtube.com
DAY8 F5 Training What is Ratio based Load Balancing Method TMOS F5 Load Balancer Rules With this common vocabulary established, let’s examine the basic load balancing transaction. It distributes load of incoming client requests based various. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via.. F5 Load Balancer Rules.
From www.f5.com
Migrating Tier 1 Application Workloads to AWS with F5 F5 F5 Load Balancer Rules It distributes load of incoming client requests based various. As depicted, the load balancer. This method differs from least connections (member), in that the least connections method measures connections. Let your applications help decide where to send your clients with the most. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. In. F5 Load Balancer Rules.
From www.thenetworkdna.com
F5 Load Balancer Upgrade the SSL Certificate The Network DNA F5 Load Balancer Rules This method differs from least connections (member), in that the least connections method measures connections. As depicted, the load balancer. It distributes load of incoming client requests based various. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. In mesh, a load balancer is the same as a reverse proxy and is. F5 Load Balancer Rules.
From www.networkingsignal.com
How To Deploy F5 Load Balancer In Azure Cloud? F5 Load Balancer Rules Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. This method differs from least connections (member), in that the least connections method measures connections. Let your applications help decide where to send your clients with the most. As depicted, the load balancer. With this common vocabulary established, let’s examine the basic load. F5 Load Balancer Rules.
From aws.amazon.com
Adding F5 BIGIP Virtual Edition Load Balancing for Container Network F5 Load Balancer Rules Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. With this common vocabulary established, let’s examine the basic load balancing transaction. As depicted, the load balancer. It distributes load of incoming client requests based various. In mesh, a load balancer is the same as a reverse proxy and is configured to have. F5 Load Balancer Rules.
From ipwithease.com
F5 Load Balancing Methods in 2020 IP With Ease F5 Load Balancer Rules Let your applications help decide where to send your clients with the most. It distributes load of incoming client requests based various. With this common vocabulary established, let’s examine the basic load balancing transaction. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. In mesh, a load balancer is the same as. F5 Load Balancer Rules.
From mstajbakhsh.ir
Onion Balance v2 Beautiful Load Balancer in TOR Mir Saman Tajbakhsh F5 Load Balancer Rules As depicted, the load balancer. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. With this common vocabulary established, let’s examine the basic load balancing transaction. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. It distributes load of. F5 Load Balancer Rules.
From www.zippyops.com
Adding load balancer to F5 Load Balancer Rules In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. This method differs from least connections (member), in that the least connections method measures connections. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. It distributes load of incoming client. F5 Load Balancer Rules.
From docs.solace.com
Using F5 BigIP as a Load Balancer for External Connectivity F5 Load Balancer Rules As depicted, the load balancer. Let your applications help decide where to send your clients with the most. With this common vocabulary established, let’s examine the basic load balancing transaction. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. It distributes load of incoming client requests based. F5 Load Balancer Rules.
From learn.microsoft.com
Administración de reglas para Azure Load Balancer Azure Portal F5 Load Balancer Rules This method differs from least connections (member), in that the least connections method measures connections. With this common vocabulary established, let’s examine the basic load balancing transaction. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. Key network and application functions, such as load balancing, encryption, acceleration,. F5 Load Balancer Rules.
From mavink.com
F5 Load Balancer Architecture Diagram F5 Load Balancer Rules It distributes load of incoming client requests based various. As depicted, the load balancer. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. With this common vocabulary established, let’s examine the basic load balancing transaction. Key network and application functions, such as load balancing, encryption, acceleration, and. F5 Load Balancer Rules.
From easycloudsupport.zendesk.com
Atlassian Load Balancer configuration options Easy Cloud F5 Load Balancer Rules Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. With this common vocabulary established, let’s examine the basic load balancing transaction. As depicted, the load balancer. Let your applications help decide where to send your clients with the most. It distributes load of incoming client requests based various. In mesh, a load. F5 Load Balancer Rules.
From www.kareemccie.com
F5 Load Balancing Methods Part 2 Network & Security Consultant F5 Load Balancer Rules This method differs from least connections (member), in that the least connections method measures connections. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. With this common vocabulary established, let’s examine the basic load balancing transaction. It distributes load of incoming client requests based various. Let your. F5 Load Balancer Rules.
From support.rackspace.com
Using dedicated load balancers with RackConnect v2.0 F5 Load Balancer Rules With this common vocabulary established, let’s examine the basic load balancing transaction. This method differs from least connections (member), in that the least connections method measures connections. Let your applications help decide where to send your clients with the most. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for. F5 Load Balancer Rules.
From www.thenetworkdna.com
High Availability Through Intelligent Load Balancing Strategies The F5 Load Balancer Rules With this common vocabulary established, let’s examine the basic load balancing transaction. It distributes load of incoming client requests based various. As depicted, the load balancer. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. Key network and application functions, such as load balancing, encryption, acceleration, and. F5 Load Balancer Rules.
From learn.microsoft.com
Gateway load balancer Azure Load Balancer Microsoft Learn F5 Load Balancer Rules In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. This method differs from least connections (member), in that the least connections method measures connections. It distributes load of incoming client requests based various. Let your applications help decide where to send your clients with the most. Key. F5 Load Balancer Rules.
From clouddocs.f5.com
5.4.1. Apply F5 Networks WAF Rules to an AWS Application Load Balancer F5 Load Balancer Rules Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. This method differs from least connections (member), in that the least connections method measures connections. Let your applications help decide where. F5 Load Balancer Rules.
From www.vrogue.co
Azure Internal Load Balancer Overview Microsoft Docs vrogue.co F5 Load Balancer Rules As depicted, the load balancer. This method differs from least connections (member), in that the least connections method measures connections. Key network and application functions, such as load balancing, encryption, acceleration, and security, can be provided via. It distributes load of incoming client requests based various. In mesh, a load balancer is the same as a reverse proxy and is. F5 Load Balancer Rules.
From www.linkedin.com
Demystifying F5 Load Balancer F5 Load Balancer Rules Let your applications help decide where to send your clients with the most. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. It distributes load of incoming client requests based various. This method differs from least connections (member), in that the least connections method measures connections. With. F5 Load Balancer Rules.
From www.youtube.com
Lecture 1 F5 Load Balancer Deployment Basics F5 LTM Training YouTube F5 Load Balancer Rules Let your applications help decide where to send your clients with the most. It distributes load of incoming client requests based various. As depicted, the load balancer. In mesh, a load balancer is the same as a reverse proxy and is configured to have multiple endpoints for a server. Key network and application functions, such as load balancing, encryption, acceleration,. F5 Load Balancer Rules.