An Example Of A Keylogger Avoidance Strategy . To protect yourself, it’s important to know what keyloggers are, how to prevent an attack and how to remove a keylogger if you are attacked. Keyloggers are malicious tools that record keystrokes to capture sensitive information. Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying. You’re typing away, pouring your heart out in a personal email or entering your bank details. To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to think about where threats start and how they can. In my experience, here are tips that can help you better detect, prevent, and respond to keylogging threats: Little do you know, there’s an invisible stowaway capturing every. It blocks any unauthorized access to a user’s keystrokes by encrypting or. Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware.
from www.scaler.com
To protect yourself, it’s important to know what keyloggers are, how to prevent an attack and how to remove a keylogger if you are attacked. Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying. Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. You’re typing away, pouring your heart out in a personal email or entering your bank details. It blocks any unauthorized access to a user’s keystrokes by encrypting or. Little do you know, there’s an invisible stowaway capturing every. Keyloggers are malicious tools that record keystrokes to capture sensitive information. In my experience, here are tips that can help you better detect, prevent, and respond to keylogging threats: To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to think about where threats start and how they can.
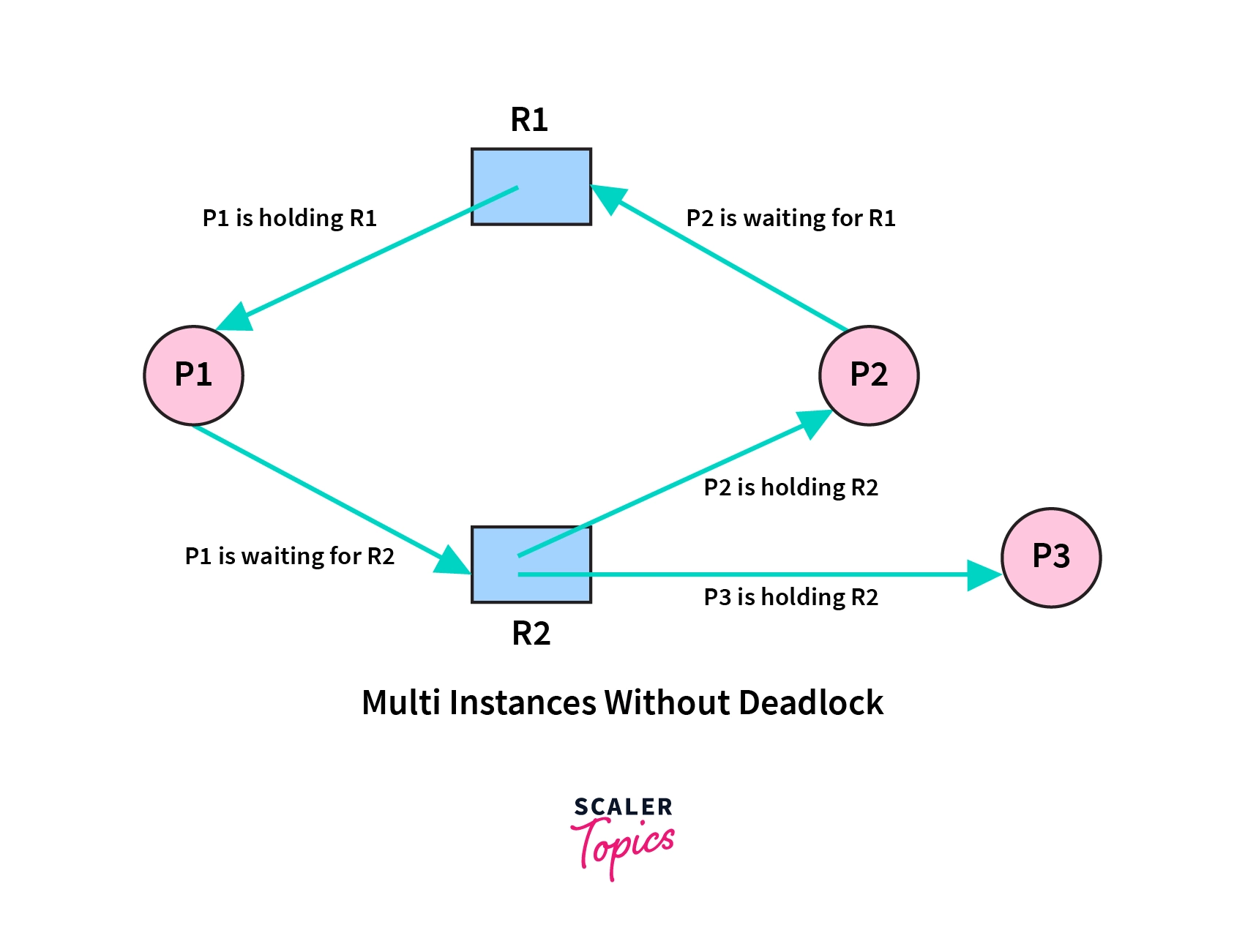
Deadlock Avoidance in OS Scaler Topics
An Example Of A Keylogger Avoidance Strategy Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. It blocks any unauthorized access to a user’s keystrokes by encrypting or. Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying. You’re typing away, pouring your heart out in a personal email or entering your bank details. Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. Keyloggers are malicious tools that record keystrokes to capture sensitive information. To protect yourself, it’s important to know what keyloggers are, how to prevent an attack and how to remove a keylogger if you are attacked. To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to think about where threats start and how they can. Little do you know, there’s an invisible stowaway capturing every. In my experience, here are tips that can help you better detect, prevent, and respond to keylogging threats:
From www.monitask.com
Is Stealth Monitoring Ethical? Difference Between Stealth and Regular An Example Of A Keylogger Avoidance Strategy Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. To protect yourself, it’s important to know what keyloggers are, how to prevent an attack and how to remove a keylogger if you are attacked. It blocks any unauthorized access to a user’s keystrokes by encrypting or. Little. An Example Of A Keylogger Avoidance Strategy.
From www.ionos.ca
What is a Keylogger and how can you protect yourself? IONOS CA An Example Of A Keylogger Avoidance Strategy You’re typing away, pouring your heart out in a personal email or entering your bank details. Little do you know, there’s an invisible stowaway capturing every. Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying. In my experience, here are tips that can help you better detect, prevent, and respond to keylogging threats:. An Example Of A Keylogger Avoidance Strategy.
From www.tarlogic.com
How to make a keylogger in PowerShell Tarlogic BlackArrow An Example Of A Keylogger Avoidance Strategy It blocks any unauthorized access to a user’s keystrokes by encrypting or. You’re typing away, pouring your heart out in a personal email or entering your bank details. To protect yourself, it’s important to know what keyloggers are, how to prevent an attack and how to remove a keylogger if you are attacked. Little do you know, there’s an invisible. An Example Of A Keylogger Avoidance Strategy.
From docslib.org
KEYLOGGERS Comparison of Detection Techniques & Its DocsLib An Example Of A Keylogger Avoidance Strategy Keyloggers are malicious tools that record keystrokes to capture sensitive information. Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. Little do you know, there’s an invisible stowaway capturing every. It blocks any unauthorized access to a user’s keystrokes by encrypting or. In my experience, here are. An Example Of A Keylogger Avoidance Strategy.
From www.integrasources.com
A USB keylogger to record keystrokes Integra Sources An Example Of A Keylogger Avoidance Strategy Keyloggers are malicious tools that record keystrokes to capture sensitive information. To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to think about where threats start and how they can. Little do you know, there’s an invisible stowaway capturing every. To protect yourself, it’s important to know what keyloggers. An Example Of A Keylogger Avoidance Strategy.
From www.slideshare.net
Keyloggers An Example Of A Keylogger Avoidance Strategy To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to think about where threats start and how they can. To protect yourself, it’s important to know what keyloggers are, how to prevent an attack and how to remove a keylogger if you are attacked. It blocks any unauthorized access. An Example Of A Keylogger Avoidance Strategy.
From www.researchgate.net
Sample Hardware Keylogger Menu (KeyGhost) Download Scientific Diagram An Example Of A Keylogger Avoidance Strategy Keyloggers are malicious tools that record keystrokes to capture sensitive information. Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying. To protect yourself, it’s important to know what keyloggers are, how to prevent an attack and how to remove a keylogger if you are attacked. Essentially, keyloggers are sneaky bits of code that. An Example Of A Keylogger Avoidance Strategy.
From cybr.com
How I made an advanced Python Keylogger that sends emails Cybr An Example Of A Keylogger Avoidance Strategy Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to think about where threats start and how they can. You’re typing away, pouring your heart out in. An Example Of A Keylogger Avoidance Strategy.
From us.norton.com
What Is a keylogger and how to detect keystroke logging Norton An Example Of A Keylogger Avoidance Strategy To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to think about where threats start and how they can. You’re typing away, pouring your heart out in a personal email or entering your bank details. Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke. An Example Of A Keylogger Avoidance Strategy.
From helpfulprofessor.com
Avoidance Learning Definition and 10 Examples (2024) An Example Of A Keylogger Avoidance Strategy Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to think about where threats start and how they can. Companies should take various steps to prevent keylogger. An Example Of A Keylogger Avoidance Strategy.
From www.sangfor.com
What Is A Keylogger Software, How Does It Work Glossary An Example Of A Keylogger Avoidance Strategy To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to think about where threats start and how they can. Little do you know, there’s an invisible stowaway capturing every. Keyloggers are malicious tools that record keystrokes to capture sensitive information. Companies should take various steps to prevent keylogger attacks,. An Example Of A Keylogger Avoidance Strategy.
From animalia-life.club
Approach Avoidance Conflict Clipart An Example Of A Keylogger Avoidance Strategy Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying. Keyloggers are malicious tools that record keystrokes to capture sensitive information. You’re typing away, pouring your heart out in a personal email. An Example Of A Keylogger Avoidance Strategy.
From www.scaler.com
Deadlock Avoidance in OS Scaler Topics An Example Of A Keylogger Avoidance Strategy To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to think about where threats start and how they can. Keyloggers are malicious tools that record keystrokes to capture sensitive information. In my experience, here are tips that can help you better detect, prevent, and respond to keylogging threats: Little. An Example Of A Keylogger Avoidance Strategy.
From us.norton.com
What Is a keylogger and how to detect keystroke logging Norton An Example Of A Keylogger Avoidance Strategy It blocks any unauthorized access to a user’s keystrokes by encrypting or. Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. Keyloggers are malicious tools that record keystrokes to capture sensitive information. To protect yourself, it’s important to know what keyloggers are, how to prevent an attack. An Example Of A Keylogger Avoidance Strategy.
From www.semanticscholar.org
Figure 3 from Detecting keyloggers based on traffic analysis with An Example Of A Keylogger Avoidance Strategy Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying. It blocks any unauthorized access to a user’s keystrokes by encrypting or. Keyloggers are malicious tools that record keystrokes to capture sensitive information. To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to. An Example Of A Keylogger Avoidance Strategy.
From www.slideserve.com
PPT Threats and Vulnerabilities PowerPoint Presentation, free An Example Of A Keylogger Avoidance Strategy Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying. You’re typing away, pouring your heart out in a personal email or entering your bank details. Keyloggers are malicious tools that record. An Example Of A Keylogger Avoidance Strategy.
From www.resmo.com
What is a Keylogger? Keystroke Logging & How to Prevent It Resmo An Example Of A Keylogger Avoidance Strategy It blocks any unauthorized access to a user’s keystrokes by encrypting or. You’re typing away, pouring your heart out in a personal email or entering your bank details. In my experience, here are tips that can help you better detect, prevent, and respond to keylogging threats: To protect yourself, it’s important to know what keyloggers are, how to prevent an. An Example Of A Keylogger Avoidance Strategy.
From www.ringcentral.com
The Definitive Guide to Call Avoidance What is Call Avoidance An Example Of A Keylogger Avoidance Strategy You’re typing away, pouring your heart out in a personal email or entering your bank details. Little do you know, there’s an invisible stowaway capturing every. In my experience, here are tips that can help you better detect, prevent, and respond to keylogging threats: Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying.. An Example Of A Keylogger Avoidance Strategy.
From us.norton.com
Keylogger What is keylogging? Norton An Example Of A Keylogger Avoidance Strategy Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. Keyloggers are malicious tools that record keystrokes to capture sensitive information. In my experience, here are tips that can help you better detect, prevent, and respond to keylogging threats: To plan a security strategy that will protect today’s. An Example Of A Keylogger Avoidance Strategy.
From www.askpython.com
Implementing a KeyLogger in Python AskPython An Example Of A Keylogger Avoidance Strategy Little do you know, there’s an invisible stowaway capturing every. To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to think about where threats start and how they can. In my experience, here are tips that can help you better detect, prevent, and respond to keylogging threats: To protect. An Example Of A Keylogger Avoidance Strategy.
From www.softactivity.com
Keylogger Software Guide. What is a Keylogger? SoftActivity An Example Of A Keylogger Avoidance Strategy It blocks any unauthorized access to a user’s keystrokes by encrypting or. To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to think about where threats start and how they can. Keyloggers are malicious tools that record keystrokes to capture sensitive information. To protect yourself, it’s important to know. An Example Of A Keylogger Avoidance Strategy.
From www.softactivity.com
Keylogger Software Guide. What is a Keylogger? SoftActivity An Example Of A Keylogger Avoidance Strategy You’re typing away, pouring your heart out in a personal email or entering your bank details. Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying. Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. Keyloggers are malicious tools that record. An Example Of A Keylogger Avoidance Strategy.
From www.hackingloops.com
HACKING CLASS 13 Password Cracking (Using Keyloggers) An Example Of A Keylogger Avoidance Strategy Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying. You’re typing away, pouring your heart out in a personal email or entering your bank details. Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. Little do you know, there’s an. An Example Of A Keylogger Avoidance Strategy.
From hes-extraordinary.com
15 Effective Parenting Strategies for Pathological Demand Avoidance An Example Of A Keylogger Avoidance Strategy To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to think about where threats start and how they can. Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. Companies should take various steps to prevent keylogger. An Example Of A Keylogger Avoidance Strategy.
From www.youtube.com
What is keylogger? Keylogger / keystroke logger spyware explained YouTube An Example Of A Keylogger Avoidance Strategy In my experience, here are tips that can help you better detect, prevent, and respond to keylogging threats: Little do you know, there’s an invisible stowaway capturing every. You’re typing away, pouring your heart out in a personal email or entering your bank details. Keyloggers are malicious tools that record keystrokes to capture sensitive information. Essentially, keyloggers are sneaky bits. An Example Of A Keylogger Avoidance Strategy.
From pofetrend.weebly.com
How to code a keylogger in notepad pofetrend An Example Of A Keylogger Avoidance Strategy Keyloggers are malicious tools that record keystrokes to capture sensitive information. Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. Little do you know, there’s an invisible stowaway capturing every. You’re typing away, pouring your heart out in a personal email or entering your bank details. It. An Example Of A Keylogger Avoidance Strategy.
From www.proofpoint.com
What Are Keyloggers? Definition, Removal & More Proofpoint US An Example Of A Keylogger Avoidance Strategy To protect yourself, it’s important to know what keyloggers are, how to prevent an attack and how to remove a keylogger if you are attacked. It blocks any unauthorized access to a user’s keystrokes by encrypting or. Little do you know, there’s an invisible stowaway capturing every. Companies should take various steps to prevent keylogger attacks, including educating employees, using. An Example Of A Keylogger Avoidance Strategy.
From educatorkiwi.blogspot.com
Edu_KIWI What is a Keylogger An Example Of A Keylogger Avoidance Strategy Little do you know, there’s an invisible stowaway capturing every. To protect yourself, it’s important to know what keyloggers are, how to prevent an attack and how to remove a keylogger if you are attacked. It blocks any unauthorized access to a user’s keystrokes by encrypting or. Keyloggers are malicious tools that record keystrokes to capture sensitive information. To plan. An Example Of A Keylogger Avoidance Strategy.
From privacysavvy.com
What is a keylogger? How to detect, remove and further avoid it An Example Of A Keylogger Avoidance Strategy Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying. To protect yourself, it’s important to know what keyloggers are, how to prevent an attack and how to remove a keylogger if you are attacked. In my experience, here are tips that can help you better detect, prevent, and respond to keylogging threats: To. An Example Of A Keylogger Avoidance Strategy.
From us.norton.com
What Is a keylogger and how to detect keystroke logging Norton An Example Of A Keylogger Avoidance Strategy Little do you know, there’s an invisible stowaway capturing every. In my experience, here are tips that can help you better detect, prevent, and respond to keylogging threats: Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. Keyloggers are malicious tools that record keystrokes to capture sensitive. An Example Of A Keylogger Avoidance Strategy.
From www.resmo.com
What is a Keylogger? Keystroke Logging & How to Prevent It Resmo An Example Of A Keylogger Avoidance Strategy Little do you know, there’s an invisible stowaway capturing every. Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. You’re typing away, pouring your heart out in a personal email or entering your bank details. Keyloggers are malicious tools that record keystrokes to capture sensitive information. To. An Example Of A Keylogger Avoidance Strategy.
From toolbox.iskysoft.com
Keylogger and Best 6 Free AntiKeyloggers for Windows An Example Of A Keylogger Avoidance Strategy It blocks any unauthorized access to a user’s keystrokes by encrypting or. Essentially, keyloggers are sneaky bits of code that meticulously track and record every keystroke you make, often without you even being aware. Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying. You’re typing away, pouring your heart out in a personal. An Example Of A Keylogger Avoidance Strategy.
From www.wallarm.com
What is a Keylogger? Definition, Detection and Prevention An Example Of A Keylogger Avoidance Strategy Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying. It blocks any unauthorized access to a user’s keystrokes by encrypting or. In my experience, here are tips that can help you better detect, prevent, and respond to keylogging threats: You’re typing away, pouring your heart out in a personal email or entering your. An Example Of A Keylogger Avoidance Strategy.
From www2.deloitte.com
¿Qué es un keylogger y cómo protegernos? An Example Of A Keylogger Avoidance Strategy To plan a security strategy that will protect today’s newly distributed workforce and the companies they work for, it’s important to think about where threats start and how they can. You’re typing away, pouring your heart out in a personal email or entering your bank details. Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus. An Example Of A Keylogger Avoidance Strategy.
From medium.com
What is Keylogger? How to protect against keyloggers? by She is An Example Of A Keylogger Avoidance Strategy To protect yourself, it’s important to know what keyloggers are, how to prevent an attack and how to remove a keylogger if you are attacked. Companies should take various steps to prevent keylogger attacks, including educating employees, using antivirus software, deploying. It blocks any unauthorized access to a user’s keystrokes by encrypting or. Essentially, keyloggers are sneaky bits of code. An Example Of A Keylogger Avoidance Strategy.