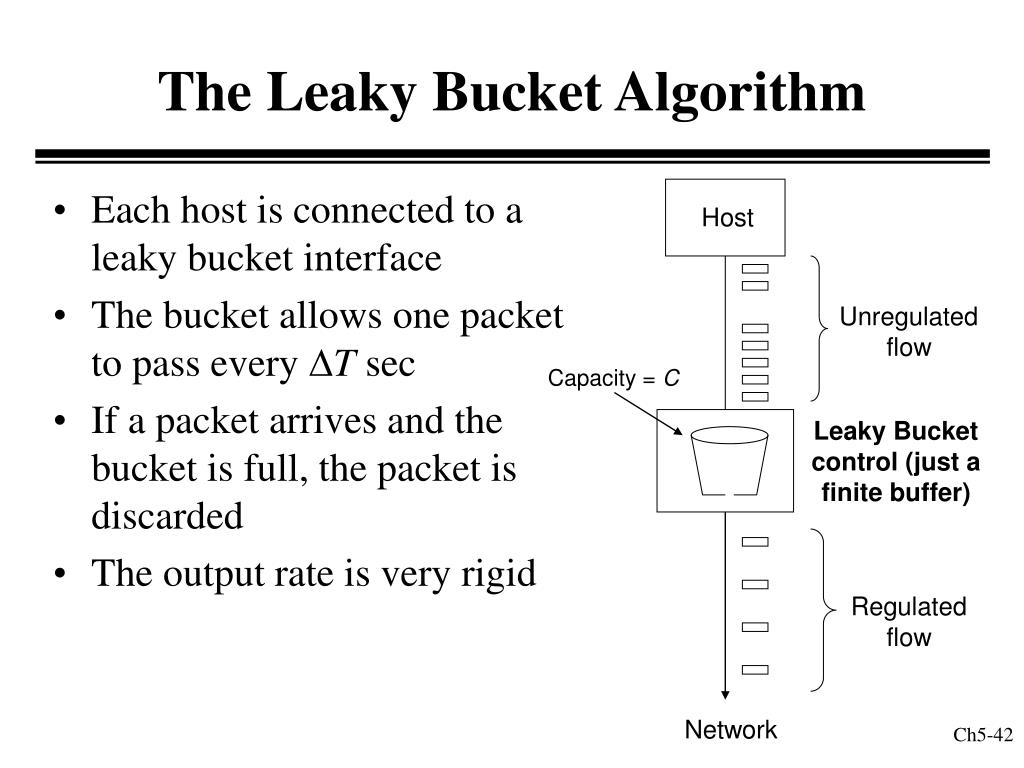
Leaky Bucket Algorithm Javatpoint . What is the leaky bucket algorithm? The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted over a network. The leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in computer networks. It is designed to smooth out bursts of traffic and ensure a steady, predictable data flow. These packets are sent to the. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown into the bucket, which leaks the data at a constant rate, i.e., high traffic is converted into constant traffic with the help of the leaky bucket. The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted.
from www.slideserve.com
What is the leaky bucket algorithm? These packets are sent to the. As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown into the bucket, which leaks the data at a constant rate, i.e., high traffic is converted into constant traffic with the help of the leaky bucket. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. It is designed to smooth out bursts of traffic and ensure a steady, predictable data flow. The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted over a network. The leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in computer networks.
PPT The Network Layer PowerPoint Presentation, free download ID5856654
Leaky Bucket Algorithm Javatpoint It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. What is the leaky bucket algorithm? These packets are sent to the. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted over a network. It is designed to smooth out bursts of traffic and ensure a steady, predictable data flow. As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown into the bucket, which leaks the data at a constant rate, i.e., high traffic is converted into constant traffic with the help of the leaky bucket. The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. The leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in computer networks. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate.
From github.com
GitHub HirenAmbekar/LeakyBucketAlgorithmDemonstration This is a Leaky Bucket Algorithm Javatpoint As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown into the bucket, which leaks the data at a constant rate, i.e., high traffic is converted into constant traffic with the help of the leaky bucket. It operates like a leaky bucket, where data is added at a variable rate,. Leaky Bucket Algorithm Javatpoint.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Javatpoint The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted over a network. It is designed to smooth out bursts of traffic and ensure a steady, predictable data flow. As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown. Leaky Bucket Algorithm Javatpoint.
From www.youtube.com
12. Leaky Bucket Algorithm Program VTU 5th Sem Computer Network Lab Leaky Bucket Algorithm Javatpoint As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown into the bucket, which leaks the data at a constant rate, i.e., high traffic is converted into constant traffic with the help of the leaky bucket. It operates like a leaky bucket, where data is added at a variable rate,. Leaky Bucket Algorithm Javatpoint.
From www.youtube.com
Leaky bucket algorithm in congestion control algorithm YouTube Leaky Bucket Algorithm Javatpoint The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. These packets are sent to the. As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown into the bucket, which leaks the data at a constant rate, i.e.,. Leaky Bucket Algorithm Javatpoint.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation ID3653615 Leaky Bucket Algorithm Javatpoint The leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in computer networks. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. These packets are sent to the. The leaky bucket. Leaky Bucket Algorithm Javatpoint.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID4138688 Leaky Bucket Algorithm Javatpoint What is the leaky bucket algorithm? It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. The leaky bucket algorithm is a traffic shaping mechanism. Leaky Bucket Algorithm Javatpoint.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID5856654 Leaky Bucket Algorithm Javatpoint The leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in computer networks. What is the leaky bucket algorithm? These packets are sent to the. It is designed to smooth out bursts of traffic and ensure a steady, predictable data flow. The leaky bucket algorithm is a network traffic management mechanism. Leaky Bucket Algorithm Javatpoint.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm Javatpoint It is designed to smooth out bursts of traffic and ensure a steady, predictable data flow. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. The leaky bucket algorithm is a method of congestion control where multiple packets are stored. Leaky Bucket Algorithm Javatpoint.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID1753059 Leaky Bucket Algorithm Javatpoint It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control. Leaky Bucket Algorithm Javatpoint.
From www.slideserve.com
PPT Leaky Bucket Algorithm PowerPoint Presentation, free download Leaky Bucket Algorithm Javatpoint It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. It is designed to smooth out bursts of traffic and ensure a steady, predictable data flow. As per leaky bucket algorithm, whatever the speed of the data packet from the source. Leaky Bucket Algorithm Javatpoint.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket Algorithm Javatpoint What is the leaky bucket algorithm? The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted over a network. These packets are sent to the. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow. Leaky Bucket Algorithm Javatpoint.
From www.youtube.com
CN LabLeaky Bucket Algorithm YouTube Leaky Bucket Algorithm Javatpoint The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. These packets are sent to the. What is the leaky bucket algorithm? The leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in computer networks. As per leaky bucket. Leaky Bucket Algorithm Javatpoint.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID569119 Leaky Bucket Algorithm Javatpoint What is the leaky bucket algorithm? The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. The leaky bucket algorithm is a traffic shaping and policing technique used to control the rate. Leaky Bucket Algorithm Javatpoint.
From www.geeksforgeeks.org
Rate Limiting Algorithms System Design Leaky Bucket Algorithm Javatpoint The leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in computer networks. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. These packets are sent to the. The leaky bucket algorithm is a method of congestion control. Leaky Bucket Algorithm Javatpoint.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID5320728 Leaky Bucket Algorithm Javatpoint What is the leaky bucket algorithm? The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. The leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in computer networks. As per leaky bucket algorithm, whatever the speed of the. Leaky Bucket Algorithm Javatpoint.
From www.researchgate.net
Leaky bucket approach. Download Scientific Diagram Leaky Bucket Algorithm Javatpoint It is designed to smooth out bursts of traffic and ensure a steady, predictable data flow. The leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in computer networks. These packets are sent to the. As per leaky bucket algorithm, whatever the speed of the data packet from the source host,. Leaky Bucket Algorithm Javatpoint.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Algorithm Javatpoint The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data. Leaky Bucket Algorithm Javatpoint.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm Javatpoint The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted over a network. The leaky bucket algorithm is a method of congestion control where multiple packets are. Leaky Bucket Algorithm Javatpoint.
From www.youtube.com
Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm Javatpoint As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown into the bucket, which leaks the data at a constant rate, i.e., high traffic is converted into constant traffic with the help of the leaky bucket. It operates like a leaky bucket, where data is added at a variable rate,. Leaky Bucket Algorithm Javatpoint.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and Leaky Bucket Algorithm Javatpoint What is the leaky bucket algorithm? It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. The leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in computer networks. The leaky bucket. Leaky Bucket Algorithm Javatpoint.
From www.researchgate.net
Intelligent leaky bucket algorithm. Download Scientific Diagram Leaky Bucket Algorithm Javatpoint The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted over a network. It is designed to smooth out bursts of traffic and ensure a steady, predictable data flow. As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown. Leaky Bucket Algorithm Javatpoint.
From songhayoung.github.io
[System Design] Leaky bucket / token bucket SUMFIのBlog Leaky Bucket Algorithm Javatpoint As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown into the bucket, which leaks the data at a constant rate, i.e., high traffic is converted into constant traffic with the help of the leaky bucket. What is the leaky bucket algorithm? The leaky bucket algorithm is a traffic shaping. Leaky Bucket Algorithm Javatpoint.
From www.youtube.com
Token and Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm Javatpoint As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown into the bucket, which leaks the data at a constant rate, i.e., high traffic is converted into constant traffic with the help of the leaky bucket. The leaky bucket algorithm is a method of congestion control where multiple packets are. Leaky Bucket Algorithm Javatpoint.
From www.youtube.com
Leaky Bucket vs Token Bucket Algorithm Leaky Bucket and Token Bucket Leaky Bucket Algorithm Javatpoint The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It is designed to smooth out bursts of traffic and ensure a steady, predictable data flow. As per leaky bucket algorithm, whatever. Leaky Bucket Algorithm Javatpoint.
From in.pinterest.com
Leaky Bucket Algorithm educlick Algorithm, Computer network Leaky Bucket Algorithm Javatpoint As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown into the bucket, which leaks the data at a constant rate, i.e., high traffic is converted into constant traffic with the help of the leaky bucket. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to. Leaky Bucket Algorithm Javatpoint.
From www.linqz.io
Leaky/Token bucket algorithm for flow control Learn INQuiZitively Leaky Bucket Algorithm Javatpoint It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown into the bucket, which leaks the data at a constant rate,. Leaky Bucket Algorithm Javatpoint.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket Algorithm Javatpoint These packets are sent to the. What is the leaky bucket algorithm? The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted over a network. As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown into the bucket, which. Leaky Bucket Algorithm Javatpoint.
From www.youtube.com
leaky bucket algorithm traffic shaping in computer networks 2021 Leaky Bucket Algorithm Javatpoint These packets are sent to the. What is the leaky bucket algorithm? The leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in computer networks. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted over a network. The leaky. Leaky Bucket Algorithm Javatpoint.
From www.youtube.com
Leaky bucket and Token bucket with GATE PYQs. Clear Explanation YouTube Leaky Bucket Algorithm Javatpoint The leaky bucket algorithm is a traffic shaping and policing technique used to control the rate of data transmission in computer networks. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. The leaky bucket algorithm is a method of congestion. Leaky Bucket Algorithm Javatpoint.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Javatpoint As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown into the bucket, which leaks the data at a constant rate, i.e., high traffic is converted into constant traffic with the help of the leaky bucket. It is designed to smooth out bursts of traffic and ensure a steady, predictable. Leaky Bucket Algorithm Javatpoint.
From www.youtube.com
Congestion Control using Traffic Shaping in TCP, Leaky Bucket Algorithm Leaky Bucket Algorithm Javatpoint It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. These packets are sent to the. It is designed to smooth out bursts of traffic and ensure a steady, predictable data flow. The leaky bucket algorithm is a traffic shaping and. Leaky Bucket Algorithm Javatpoint.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID4138688 Leaky Bucket Algorithm Javatpoint It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data to flow out at a steady rate. The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted over a network. As per leaky bucket algorithm, whatever the. Leaky Bucket Algorithm Javatpoint.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Algorithm Javatpoint The leaky bucket algorithm is a method of congestion control where multiple packets are stored temporarily. The leaky bucket algorithm is a traffic shaping mechanism used in computer networks to control the rate at which data is transmitted. It operates like a leaky bucket, where data is added at a variable rate, and there is a constant leak, allowing data. Leaky Bucket Algorithm Javatpoint.
From www.rdiachenko.com
Exploring and Implementing the Leaky Bucket Rate Limiting Algorithm Leaky Bucket Algorithm Javatpoint What is the leaky bucket algorithm? The leaky bucket algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted over a network. It is designed to smooth out bursts of traffic and ensure a steady, predictable data flow. These packets are sent to the. The leaky bucket algorithm is a method of. Leaky Bucket Algorithm Javatpoint.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Algorithm Javatpoint These packets are sent to the. It is designed to smooth out bursts of traffic and ensure a steady, predictable data flow. As per leaky bucket algorithm, whatever the speed of the data packet from the source host, the packets are thrown into the bucket, which leaks the data at a constant rate, i.e., high traffic is converted into constant. Leaky Bucket Algorithm Javatpoint.