Crown Jewels Security . Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most. Identify, protect and defend your most critical business assets from harmful compromise. A crown jewel can be anything essential to an organization’s operations, reputation, and success.
from www.pwndefend.com
Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. Identify, protect and defend your most critical business assets from harmful compromise. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most. A crown jewel can be anything essential to an organization’s operations, reputation, and success.
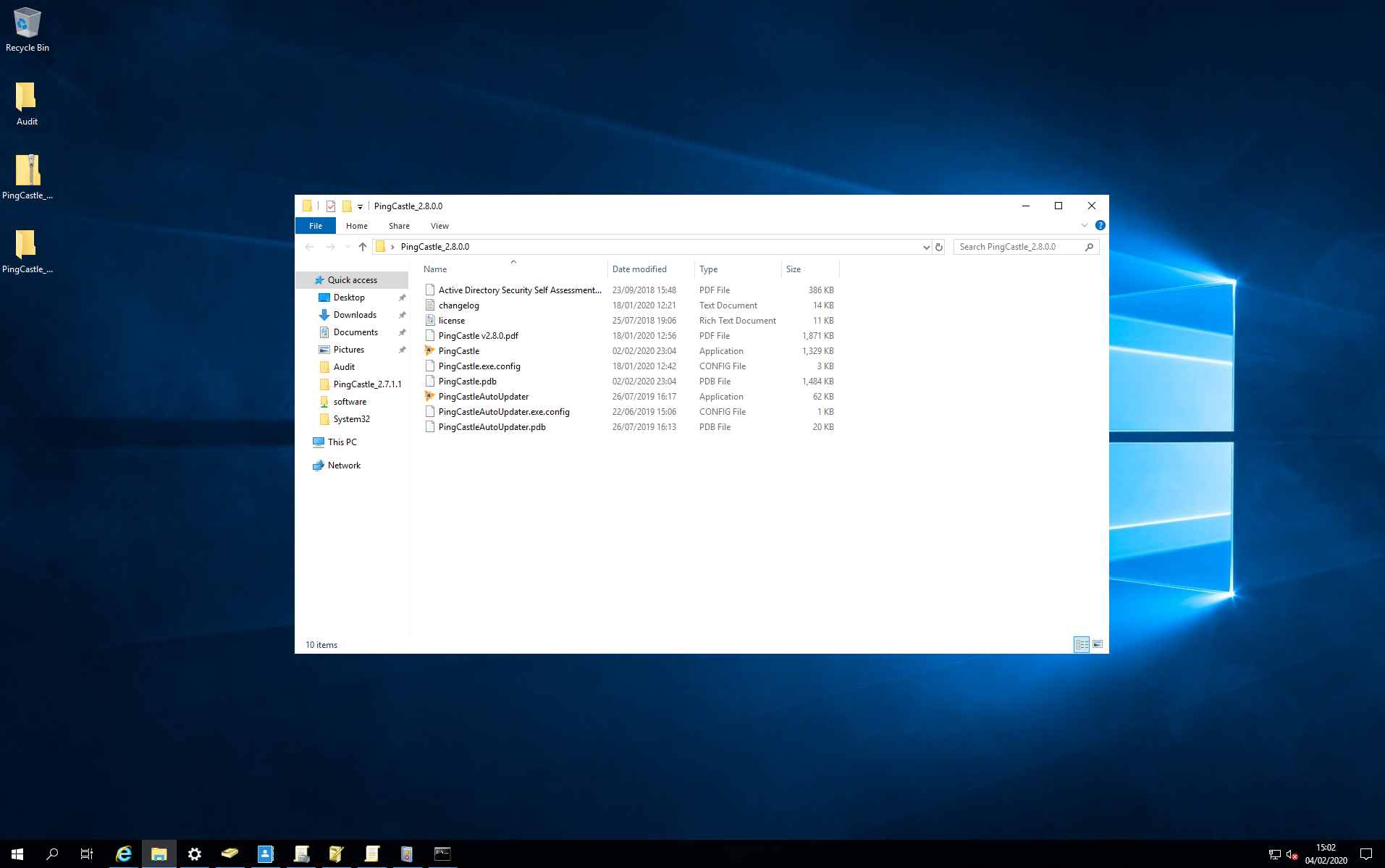
Active Directory Security Securing the crown jewels with PingCastle 2
Crown Jewels Security A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. A crown jewel can be anything essential to an organization’s operations, reputation, and success. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Identify, protect and defend your most critical business assets from harmful compromise. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most.
From www.valuesec.in
Cyber Risk Assessment Services ValueSec Crown Jewels Security Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most. Identify, protect and defend your most critical business assets from harmful. Crown Jewels Security.
From www.pwndefend.com
Active Directory Security Securing the crown jewels with PingCastle 2 Crown Jewels Security Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most. A crown jewel can be anything essential to an organization’s operations, reputation, and success. Identify, protect and defend your most critical business assets from harmful compromise. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify. Crown Jewels Security.
From www.ifsecglobal.com
Securing the world’s most valuable artefacts Crown Jewels Security A crown jewel can be anything essential to an organization’s operations, reputation, and success. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. Identify, protect and defend your most critical business assets from harmful compromise. A crown jewels assessment. Crown Jewels Security.
From www.cliffnyangau.co.ke
Shielding Your Crown Jewels A Cybersecurity Framework for Protecting Crown Jewels Security A crown jewel can be anything essential to an organization’s operations, reputation, and success. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are. Crown Jewels Security.
From www.socinvestigation.com
What is Crown Jewels Analysis ? Part01 Security Investigation Crown Jewels Security Identify, protect and defend your most critical business assets from harmful compromise. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. A crown jewel can be anything essential to an organization’s operations, reputation, and success. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection. Crown Jewels Security.
From the-siu.org.uk
Westminster Abbey to be turned into fortress to protect Crown Jewels Crown Jewels Security Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most. A crown jewel can be anything essential to an organization’s operations, reputation, and success. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Crown jewel analysis (cja) is a risk management methodology used in cyber. Crown Jewels Security.
From nypost.com
Top secret Crown Jewels security operation revealed Crown Jewels Security A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. A crown jewel can be anything essential to an organization’s operations, reputation, and success. Identify, protect and defend your most critical business assets from harmful compromise. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection. Crown Jewels Security.
From www.slideserve.com
PPT cyber security services PowerPoint Presentation, free download Crown Jewels Security Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most. A crown jewel can be anything essential to an organization’s operations,. Crown Jewels Security.
From www.gdatasoftware.com
Establishing Security Protecting the crown jewels of your company Crown Jewels Security A crown jewel can be anything essential to an organization’s operations, reputation, and success. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most. Identify, protect and defend your most critical business assets from harmful compromise.. Crown Jewels Security.
From www.securityforum.org
Protecting the Crown Jewels How to Secure MissionCritical Assets Crown Jewels Security A crown jewel can be anything essential to an organization’s operations, reputation, and success. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Mitre's. Crown Jewels Security.
From securityintelligence.com
Guarding the Crown Jewels The Importance of Intellectual Property Crown Jewels Security Identify, protect and defend your most critical business assets from harmful compromise. A crown jewel can be anything essential to an organization’s operations, reputation, and success. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. Mitre's crown jewels analysis. Crown Jewels Security.
From www.dragos.com
Crown Jewel Analysis Infographic Building Automation Systems Crown Jewels Security A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Identify, protect and defend your most critical business assets from harmful compromise. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most. Crown jewel analysis (cja) is a risk management methodology used in cyber security to. Crown Jewels Security.
From nypost.com
Top secret Crown Jewels security operation revealed Crown Jewels Security Identify, protect and defend your most critical business assets from harmful compromise. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. A crown jewel can be anything essential to an organization’s operations, reputation, and success. A crown jewels assessment. Crown Jewels Security.
From www.scotsman.com
Operation Tower of London crown jewel security plans revealed Crown Jewels Security A crown jewel can be anything essential to an organization’s operations, reputation, and success. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Identify, protect and defend your most critical business assets from harmful compromise. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection. Crown Jewels Security.
From www.socinvestigation.com
What is Crown Jewels Analysis ? Part01 Security Investigation Crown Jewels Security Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. Identify, protect and defend your most critical business assets from harmful compromise. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are. Crown Jewels Security.
From www.mandiant.com
Crown Jewels Security Assessment Critical Information Assets Crown Jewels Security A crown jewel can be anything essential to an organization’s operations, reputation, and success. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most. Identify, protect and defend your most critical business assets from harmful compromise. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets.. Crown Jewels Security.
From www.blackfog.com
Data Security Protecting the Crown Jewels BlackFog Crown Jewels Security Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. A crown jewel can be anything essential to an organization’s operations, reputation, and success. Crown jewel analysis (cja) is a risk management methodology used in cyber. Crown Jewels Security.
From www.pwndefend.com
Active Directory Security Securing the crown jewels with PingCastle 2 Crown Jewels Security A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. Identify, protect and defend your most critical business assets from harmful compromise. A crown jewel. Crown Jewels Security.
From www.pwndefend.com
Active Directory Security Securing the crown jewels with PingCastle 2 Crown Jewels Security A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. Identify, protect and defend your most critical business assets from harmful compromise. Mitre's crown jewels. Crown Jewels Security.
From securityintelligence.com
Security Safeguard Data Protection & Your Crown Jewels Crown Jewels Security A crown jewel can be anything essential to an organization’s operations, reputation, and success. Identify, protect and defend your most critical business assets from harmful compromise. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection. Crown Jewels Security.
From www.pwndefend.com
Active Directory Security Securing the crown jewels with PingCastle 2 Crown Jewels Security A crown jewel can be anything essential to an organization’s operations, reputation, and success. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. Mitre's. Crown Jewels Security.
From www.pwndefend.com
Active Directory Security Securing the crown jewels with PingCastle 2 Crown Jewels Security Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. A crown jewel can be anything essential to an organization’s operations, reputation, and success. Mitre's. Crown Jewels Security.
From www.adnovum.com
Cybersecurity Protect your Crown Jewels Crown Jewels Security Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. Identify, protect and defend your most critical business assets from harmful compromise. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are. Crown Jewels Security.
From www.linkedin.com
Protecting the Crown Jewels Securing Critical Assets Crown Jewels Security Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. A crown jewel can be anything essential to an organization’s operations, reputation, and success. Identify, protect and defend your most critical business assets from harmful compromise. A crown jewels assessment. Crown Jewels Security.
From colortokens.com
Crown Jewels Security for Hybrid Environments ColorTokens Crown Jewels Security A crown jewel can be anything essential to an organization’s operations, reputation, and success. Identify, protect and defend your most critical business assets from harmful compromise. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. A crown jewels assessment. Crown Jewels Security.
From www.linkedin.com
Shielding Your Crown Jewels A Cybersecurity Framework for Protecting Crown Jewels Security A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Identify, protect and defend your most critical business assets from harmful compromise. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. Mitre's crown jewels. Crown Jewels Security.
From www.pwndefend.com
Active Directory Security Securing the crown jewels with PingCastle 2 Crown Jewels Security A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most. A crown jewel can be anything essential to an organization’s operations, reputation, and success. Crown jewel analysis (cja) is a risk management methodology used in cyber. Crown Jewels Security.
From www.pwndefend.com
Active Directory Security Securing the crown jewels with PingCastle 2 Crown Jewels Security A crown jewel can be anything essential to an organization’s operations, reputation, and success. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. Identify, protect and defend your most critical business assets from harmful compromise. A crown jewels assessment. Crown Jewels Security.
From www.youtube.com
Crown Jewels Risk Assessment CostEffective Risk Identification YouTube Crown Jewels Security A crown jewel can be anything essential to an organization’s operations, reputation, and success. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. Identify, protect and defend your most critical business assets from harmful compromise. A crown jewels assessment. Crown Jewels Security.
From www.pwndefend.com
Active Directory Security Securing the crown jewels with PingCastle 2 Crown Jewels Security Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Identify, protect and defend your most critical business assets from harmful compromise. Mitre's crown jewels. Crown Jewels Security.
From kravensecurity.com
Crown Jewel Analysis How To Figure Out What To Protect Kraven Security Crown Jewels Security A crown jewel can be anything essential to an organization’s operations, reputation, and success. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Identify, protect and defend your most critical business assets from harmful compromise. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most.. Crown Jewels Security.
From www.syseleven.de
Protecting The Crown Jewels Managing And Securing Secrets Crown Jewels Security Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which. Crown Jewels Security.
From am1.news
NY Post Top secret Crown Jewels security operation for King Charles Crown Jewels Security A crown jewel can be anything essential to an organization’s operations, reputation, and success. Identify, protect and defend your most critical business assets from harmful compromise. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection. Crown Jewels Security.
From popculturely.com
Top secret Crown Jewels security operation revealed Pop Culturely Crown Jewels Security Crown jewel analysis (cja) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber. Crown Jewels Security.
From layerxsecurity.com
Protecting Your Company's Data Crown Jewels How to Solve ChatGPT Crown Jewels Security Identify, protect and defend your most critical business assets from harmful compromise. Mitre's crown jewels analysis (cja) is a process and corresponding toolset for identifying those cyber assets that are most. A crown jewel can be anything essential to an organization’s operations, reputation, and success. A crown jewels assessment (cja) is a process that identifies, prioritizes, and protects these assets.. Crown Jewels Security.