Security Control Diagram . network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. security controls are parameters implemented to protect various forms of data and infrastructure important. the three types of security controls include administrative control, physical control, and technical control. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures.
from www.chemanager-online.com
we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. the three types of security controls include administrative control, physical control, and technical control. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. security controls are parameters implemented to protect various forms of data and infrastructure important. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s.
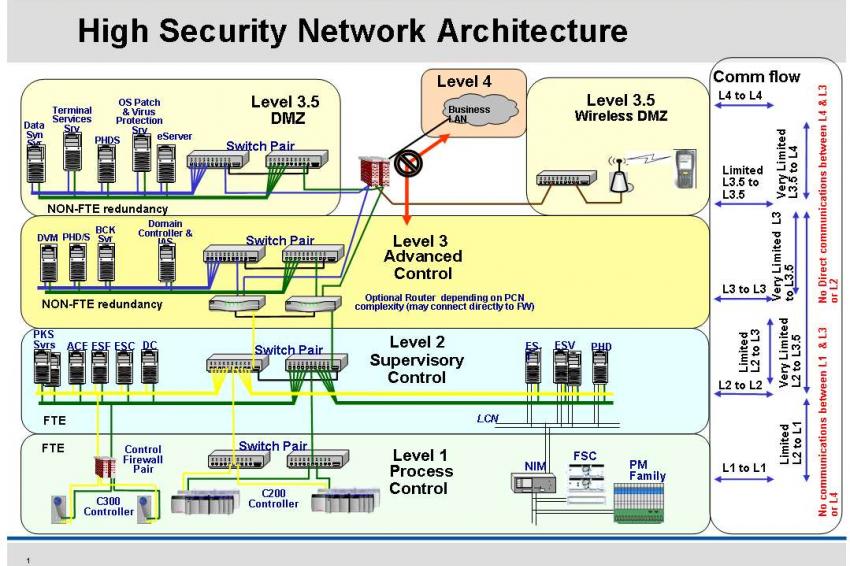
Cyber Security for Industrial Control Systems CHEManager
Security Control Diagram security controls are parameters implemented to protect various forms of data and infrastructure important. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. security controls are parameters implemented to protect various forms of data and infrastructure important. we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. the three types of security controls include administrative control, physical control, and technical control. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and.
From kintronics.com
Security Provided by Access Control Systems Kintronics Security Control Diagram security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. we have a number of visualizations of the nist cybersecurity framework. Security Control Diagram.
From www.lucidchart.com
Network Security Diagram Template Lucidchart Security Control Diagram we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. Cybersecurity controls are mechanisms used. Security Control Diagram.
From www.cipherspace.com
5 Steps for Implementing IT Security Controls What to do, and How to Security Control Diagram security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. the three types of security controls include administrative control, physical control,. Security Control Diagram.
From www.conceptdraw.com
Network Security Security Control Diagram security controls are parameters implemented to protect various forms of data and infrastructure important. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. the three types of security controls include administrative control, physical control, and technical control.. Security Control Diagram.
From wentzwu.com
Compensating Controls vs Defenseindepth Strategy by Wentz Wu, CISSP Security Control Diagram security controls are parameters implemented to protect various forms of data and infrastructure important. the three types of security controls include administrative control, physical control, and technical control. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s.. Security Control Diagram.
From www.conceptdraw.com
Network Security Diagrams Network Security Architecture Diagram Security Control Diagram we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. security controls are parameters implemented to protect various. Security Control Diagram.
From www.conceptdraw.com
Network Security Architecture Diagram Security Control Diagram network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. security controls are parameters implemented to protect various forms of data and infrastructure important. the three types of security controls include administrative control, physical control, and technical control. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and.. Security Control Diagram.
From www.alamy.com
Diagram of Security Stock Photo Alamy Security Control Diagram security controls are parameters implemented to protect various forms of data and infrastructure important. we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. Cybersecurity controls are mechanisms used to prevent,. Security Control Diagram.
From purplesec.us
Types Of Security Controls Explained Security Control Diagram Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. the three types of security controls include administrative. Security Control Diagram.
From www.linkedin.com
Security Control Functional Types Security Control Diagram security controls are parameters implemented to protect various forms of data and infrastructure important. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. Cybersecurity controls are mechanisms used to prevent, detect and mitigate. Security Control Diagram.
From www.chemanager-online.com
Cyber Security for Industrial Control Systems CHEManager Security Control Diagram security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. security controls are parameters implemented to protect various forms of data and infrastructure important. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. the three types of security controls include administrative control, physical control, and technical. Security Control Diagram.
From kentonbrothers.com
CPTED Part 2 Natural Surveillance and Natural Access Control Kenton Security Control Diagram network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. the three types of security controls include administrative control, physical control, and technical control. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. we have a number of visualizations of the nist. Security Control Diagram.
From wiringdbtrnavacti.z13.web.core.windows.net
Security Systems Wiring Diagrams Home Security Control Diagram network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. the three types of security controls include administrative control, physical control, and technical control. Cybersecurity controls are mechanisms used to prevent, detect. Security Control Diagram.
From www.conceptdraw.com
Network Security Diagrams Network Security Architecture Diagram Security Control Diagram security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. the three types of security controls include administrative control, physical control, and technical control. we have a number of visualizations of the nist. Security Control Diagram.
From control.com
Designbased Fortifications Cybersecurity in Industrial Measurement Security Control Diagram the three types of security controls include administrative control, physical control, and technical control. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. security controls are parameters implemented to protect various forms of data and infrastructure important. security architecture diagram, also known as a security blueprint, is a visual representation of the security. Security Control Diagram.
From advancedatan.com
Physical Security Measures Advancedata NetworkAdvancedata Network Security Control Diagram we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. the three types of security controls include administrative control, physical control, and technical control. network security diagram examples provide an important graphical representation of the. Security Control Diagram.
From www.f5.com
What Are Security Controls? Security Control Diagram security controls are parameters implemented to protect various forms of data and infrastructure important. we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. the three types of security controls include administrative control, physical control, and technical control. Cybersecurity controls are mechanisms used to prevent, detect and mitigate. Security Control Diagram.
From www.conceptdraw.com
Network Security Diagram Security Control Diagram the three types of security controls include administrative control, physical control, and technical control. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. Cybersecurity controls are mechanisms used to prevent, detect and mitigate. Security Control Diagram.
From www.cipherspace.com
5 Steps for Implementing IT Security Controls What to do, and How to Security Control Diagram security controls are parameters implemented to protect various forms of data and infrastructure important. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. the three types of security controls include. Security Control Diagram.
From www.eescorporation.com
Types of Security Controls EES Corporation Security Control Diagram the three types of security controls include administrative control, physical control, and technical control. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. network security diagram examples provide an important graphical representation of the. Security Control Diagram.
From www.researchgate.net
Core security functions, principles and activities of NIST Risk Security Control Diagram we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. the three types of security controls include administrative control, physical control, and technical control. security architecture diagram, also known as a security blueprint, is a. Security Control Diagram.
From learndiagram.com
Network Security Diagram Learn Diagram Security Control Diagram Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. security controls are parameters implemented to protect various forms. Security Control Diagram.
From satoricyber.com
Chapter 3 Cybersecurity Frameworks Satori Security Control Diagram we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. security controls are parameters implemented to protect various forms of data and infrastructure important. Cybersecurity controls are mechanisms used to prevent, detect. Security Control Diagram.
From www.researchgate.net
Network information security control evaluation model. Download Security Control Diagram we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. the three types of security controls include administrative control,. Security Control Diagram.
From www.conceptdraw.com
Network Security Tips Security Control Diagram the three types of security controls include administrative control, physical control, and technical control. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. security controls are parameters implemented to protect various forms. Security Control Diagram.
From www.scrut.io
Security Control Types Scrut Automation Security Control Diagram Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. security controls are parameters implemented to protect various forms of data and infrastructure important. the three types of security controls include administrative control, physical control, and technical. Security Control Diagram.
From datanoesis.gr
Physical Security Systems Retail in a box Datanoesis Security Control Diagram the three types of security controls include administrative control, physical control, and technical control. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. security controls are parameters implemented to protect various forms. Security Control Diagram.
From huntsmansecurity.com
Measure the effectiveness of your Security Controls Huntsman Security Control Diagram security controls are parameters implemented to protect various forms of data and infrastructure important. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. the three types of security controls include administrative control, physical control, and technical control.. Security Control Diagram.
From www.dreamstime.com
Diagram of it Security stock illustration. Illustration of defence Security Control Diagram Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. security controls are parameters implemented to protect various forms of data and infrastructure important. security architecture diagram, also known as a security blueprint, is a. Security Control Diagram.
From www.slideteam.net
Technical Security Control Model With Isk Management Guide For Security Control Diagram security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. the three types of security controls include administrative control, physical control, and technical control. Cybersecurity controls are mechanisms used to prevent, detect and mitigate. Security Control Diagram.
From www.slideteam.net
Cyber Security Incident Response Process Flow Chart Deploying Computer Security Control Diagram security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. security controls are parameters implemented to protect various forms of data and infrastructure important. the three types of security controls include administrative control, physical control, and technical control. network security diagram examples provide an important graphical representation of the. Security Control Diagram.
From www.slideteam.net
Nist Framework Process For Security Control Selection PPT Sample Security Control Diagram Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. the three types of security controls include administrative control, physical control, and technical control. security controls are parameters implemented to protect various forms of data and infrastructure. Security Control Diagram.
From diy.stackexchange.com
electrical How Do I Plan for an Intrusion Detection System? Home Security Control Diagram security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. we have a number of visualizations of the nist cybersecurity framework and accompanying control families that will help you. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. security controls are parameters implemented to protect various. Security Control Diagram.
From www.gotyoursixcyber.com
Access Control Got Your Six Cybersecurity Security Control Diagram the three types of security controls include administrative control, physical control, and technical control. network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. Cybersecurity controls are mechanisms used to prevent, detect and mitigate cyber threats and. security architecture diagram, also known as a security blueprint, is a visual representation of. Security Control Diagram.
From learn.microsoft.com
Desain arsitektur keamanan Azure Architecture Center Microsoft Learn Security Control Diagram network security diagram examples provide an important graphical representation of the implementation of an it infrastructure’s. security architecture diagram, also known as a security blueprint, is a visual representation of the security measures. the three types of security controls include administrative control, physical control, and technical control. Cybersecurity controls are mechanisms used to prevent, detect and mitigate. Security Control Diagram.