Encryption In Transit Protocols . When data is being transferred between components, locations, or programs, it's in transit. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. A short overview of the various data encryption methods available today: This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. Encryption may be implemented at the source, where data is generated and stored at the origin. Encryption at rest refers to the encryption applied to the stored data.
from netlibsecurity.com
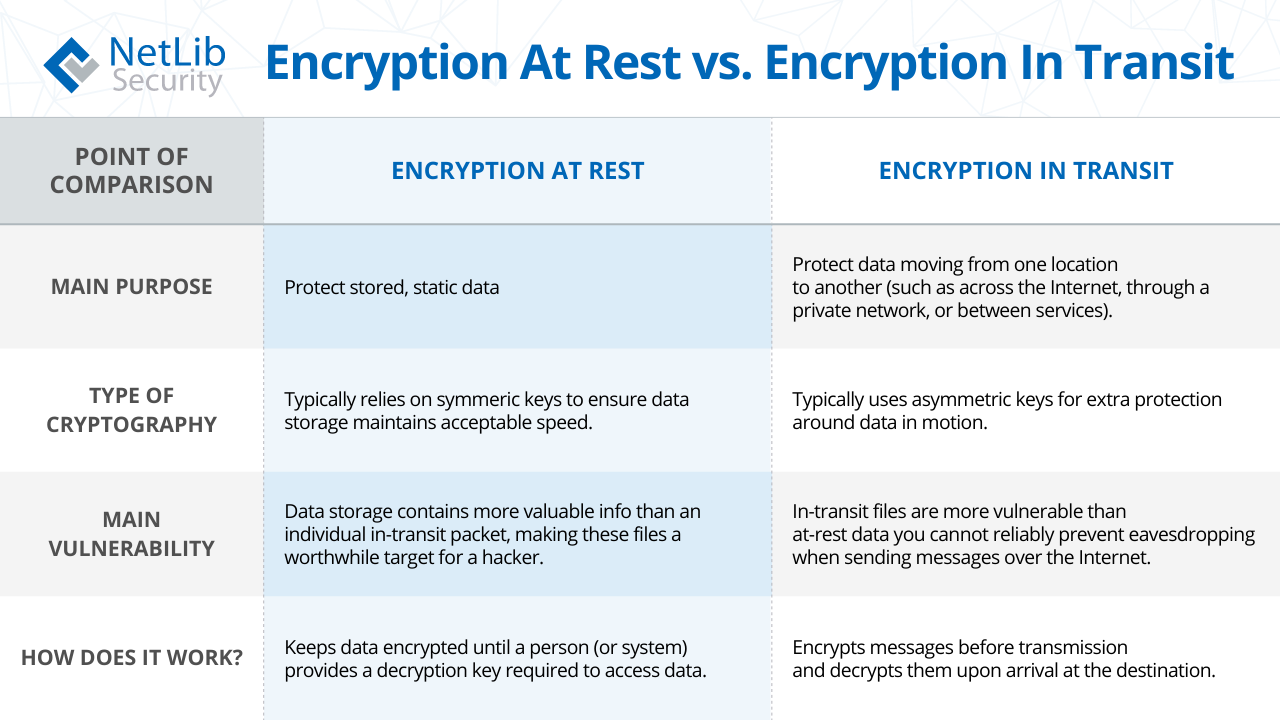
Encryption at rest refers to the encryption applied to the stored data. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. Encryption may be implemented at the source, where data is generated and stored at the origin. Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. When data is being transferred between components, locations, or programs, it's in transit. A short overview of the various data encryption methods available today:
Data at Rest vs Data in Transit
Encryption In Transit Protocols A short overview of the various data encryption methods available today: When data is being transferred between components, locations, or programs, it's in transit. A short overview of the various data encryption methods available today: This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. Encryption at rest refers to the encryption applied to the stored data. Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. Encryption may be implemented at the source, where data is generated and stored at the origin.
From netlibsecurity.com
Data at Rest vs Data in Transit Encryption In Transit Protocols Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. Encryption may be implemented at the source, where data is generated and stored at the origin. A short overview of the various data encryption methods available today: When data is being transferred between components, locations, or programs, it's in transit. In addition to. Encryption In Transit Protocols.
From www.exam-answer.com
How encrypting in transit worksTo enable encryption of data in transit Encryption In Transit Protocols A short overview of the various data encryption methods available today: Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. Encryption at rest refers to the encryption applied to the stored data. When data is being transferred between components, locations, or programs, it's in transit. Encryption may be implemented at the source,. Encryption In Transit Protocols.
From www.redswitches.com
Data At Rest Encryption 6 Best Practices For Data Security Encryption In Transit Protocols In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. A short overview of the various data encryption methods available today: When data is being transferred between components, locations, or programs, it's in transit. Encryption. Encryption In Transit Protocols.
From docs.aws.amazon.com
AWS DataSync encryption in transit AWS DataSync Encryption In Transit Protocols Encryption may be implemented at the source, where data is generated and stored at the origin. Encryption at rest refers to the encryption applied to the stored data. When data is being transferred between components, locations, or programs, it's in transit. A short overview of the various data encryption methods available today: This article aims to provide a comprehensive guide. Encryption In Transit Protocols.
From trailhead.salesforce.com
Encrypt Data at Rest Salesforce Trailhead Encryption In Transit Protocols Encryption may be implemented at the source, where data is generated and stored at the origin. Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. Encryption at rest refers to the encryption applied to the stored data. A short overview of the various data encryption methods available today: When data is being. Encryption In Transit Protocols.
From www.proofpoint.com
What is Encryption? Definition, Types & More Proofpoint US Encryption In Transit Protocols A short overview of the various data encryption methods available today: When data is being transferred between components, locations, or programs, it's in transit. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. Encryption. Encryption In Transit Protocols.
From phoenixnap.com
Data in Transit Encryption Explained phoenixNAP Blog Encryption In Transit Protocols Encryption may be implemented at the source, where data is generated and stored at the origin. When data is being transferred between components, locations, or programs, it's in transit. This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. A short overview of the. Encryption In Transit Protocols.
From us.norton.com
What is encryption? How it works + types of encryption Norton Encryption In Transit Protocols This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. Encryption may be implemented at the source, where data is generated and stored at the origin. When data is being transferred between components, locations, or programs, it's in transit. Employ reputable encryption protocols like. Encryption In Transit Protocols.
From www.newsoftwares.net
Decoding Data Encryption In Transit An Overview Of Popular Protocols Encryption In Transit Protocols A short overview of the various data encryption methods available today: Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. When data is being transferred between. Encryption In Transit Protocols.
From www.comparitech.com
Common Encryption Types, Protocols and Algorithms Explained Encryption In Transit Protocols Encryption may be implemented at the source, where data is generated and stored at the origin. Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. When data is being transferred between components, locations, or programs, it's in transit. A short overview of the various data encryption methods available today: In addition to. Encryption In Transit Protocols.
From www.comparitech.com
Common Encryption Types, Protocols and Algorithms Explained Encryption In Transit Protocols A short overview of the various data encryption methods available today: Encryption at rest refers to the encryption applied to the stored data. When data is being transferred between components, locations, or programs, it's in transit. Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. Encryption may be implemented at the source,. Encryption In Transit Protocols.
From www.slideteam.net
Overview Of Encryption For Securing Data In Transit Encryption Encryption In Transit Protocols When data is being transferred between components, locations, or programs, it's in transit. Encryption may be implemented at the source, where data is generated and stored at the origin. Encryption at rest refers to the encryption applied to the stored data. This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues,. Encryption In Transit Protocols.
From flo.net
Encryption How to protect data in transit Flō Networks Encryption In Transit Protocols Encryption may be implemented at the source, where data is generated and stored at the origin. This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. A short overview of the various data encryption methods available today: In addition to protecting customer data at. Encryption In Transit Protocols.
From www.encryptionconsulting.com
What is the difference between Encryption and Tokenization? Which is Encryption In Transit Protocols Encryption at rest refers to the encryption applied to the stored data. Encryption may be implemented at the source, where data is generated and stored at the origin. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. This article aims to provide a comprehensive guide to secure data transit, including best. Encryption In Transit Protocols.
From docs.pinecone.io
Security Pinecone Docs Encryption In Transit Protocols Encryption at rest refers to the encryption applied to the stored data. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. When data is being. Encryption In Transit Protocols.
From www.youtube.com
What does encryption of dataintransit and data at rest mean? YouTube Encryption In Transit Protocols Encryption at rest refers to the encryption applied to the stored data. This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. Encryption may be implemented. Encryption In Transit Protocols.
From blog.documatic.com
Data Encryption Securing Data at Rest and in Transit with Encryption Encryption In Transit Protocols Encryption at rest refers to the encryption applied to the stored data. Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. This article aims to provide a comprehensive guide to secure data transit, including. Encryption In Transit Protocols.
From www.youtube.com
The Definitive Guide to Understanding AtRest and InTransit Encryption Encryption In Transit Protocols In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. When data is being transferred between components, locations, or programs, it's in transit. A short overview of the various data encryption methods available today: Encryption may be implemented at the source, where data is generated and stored at the origin. Employ reputable. Encryption In Transit Protocols.
From www.slideserve.com
PPT Data Encryption in Transit PowerPoint Presentation, free download Encryption In Transit Protocols This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. A short overview of the various data encryption methods available today: Encryption at rest refers to. Encryption In Transit Protocols.
From ded9.com
Endtoend encryption; A way to secure communication? Encryption In Transit Protocols Encryption may be implemented at the source, where data is generated and stored at the origin. A short overview of the various data encryption methods available today: In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. This article aims to provide a comprehensive guide to secure data transit, including best practices,. Encryption In Transit Protocols.
From docs.cloudera.com
Encryption Encryption In Transit Protocols In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. Encryption at rest refers to the encryption applied to the stored data. Encryption may be implemented at the source, where data is generated and stored at the origin. Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport. Encryption In Transit Protocols.
From www.newsoftwares.net
Decoding Data Encryption In Transit An Overview Of Popular Protocols Encryption In Transit Protocols Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. When data is being transferred between components, locations, or programs, it's in transit. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. Encryption may be implemented at the source, where data is generated and. Encryption In Transit Protocols.
From www.youtube.com
Protecting Data in Transit (CISSP Free by YouTube Encryption In Transit Protocols Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. When data is being transferred between components, locations, or programs, it's in transit. This article aims to provide a comprehensive guide to secure data transit,. Encryption In Transit Protocols.
From android-full-encryption.blogspot.com
Asymmetric vs symmetric encryption graphic illustrates the asymmetric Encryption In Transit Protocols A short overview of the various data encryption methods available today: When data is being transferred between components, locations, or programs, it's in transit. Encryption may be implemented at the source, where data is generated and stored at the origin. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. This article. Encryption In Transit Protocols.
From ico.org.uk
Types of encryption ICO Encryption In Transit Protocols Encryption at rest refers to the encryption applied to the stored data. This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. Employ reputable encryption protocols. Encryption In Transit Protocols.
From www.codeproject.com
Data Encryption in Azure CodeProject Encryption In Transit Protocols Encryption may be implemented at the source, where data is generated and stored at the origin. This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. When data is being transferred between components, locations, or programs, it's in transit. In addition to protecting customer. Encryption In Transit Protocols.
From maturitymodel.security.aws.dev
Encryption in transit AWS Security Maturity Model Encryption In Transit Protocols A short overview of the various data encryption methods available today: This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. Encryption at rest refers to the encryption applied to the stored data. In addition to protecting customer data at rest, microsoft uses encryption. Encryption In Transit Protocols.
From www.securenetconsulting.co.uk
Data in Transit Encryption Encryption In Transit Protocols Encryption at rest refers to the encryption applied to the stored data. Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. Encryption may be implemented at the source, where data is generated and stored at the origin. A short overview of the various data encryption methods available today: This article aims to. Encryption In Transit Protocols.
From www.cisco.com
What Is Encryption? Explanation and Types Cisco Encryption In Transit Protocols This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. Encryption may be implemented at the source, where data is generated and stored at the origin. A. Encryption In Transit Protocols.
From www.sealpath.com
The Three States of Data Guide Description and How to Secure them Encryption In Transit Protocols A short overview of the various data encryption methods available today: Encryption at rest refers to the encryption applied to the stored data. Employ reputable encryption protocols like ssl (secure sockets layer) or its successor tls (transport layer security) for. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. When data. Encryption In Transit Protocols.
From pushbuildtestdeploy.com
Encryption in Transit and Rest Push Build Test Deploy Encryption In Transit Protocols When data is being transferred between components, locations, or programs, it's in transit. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. Encryption at rest refers to the encryption applied to the stored data. A short overview of the various data encryption methods available today: Encryption may be implemented at the. Encryption In Transit Protocols.
From www.pandasecurity.com
PGP Encryption The Email Security Standard Panda Security Encryption In Transit Protocols A short overview of the various data encryption methods available today: Encryption at rest refers to the encryption applied to the stored data. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. Encryption may be implemented at the source, where data is generated and stored at the origin. Employ reputable encryption. Encryption In Transit Protocols.
From www.newsoftwares.net
Securing Data In Transit Best Practices For Proper Encryption Encryption In Transit Protocols This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. Encryption at rest refers to the encryption applied to the stored data. When data is being. Encryption In Transit Protocols.
From www.newsoftwares.net
Decoding Data Encryption In Transit An Overview Of Popular Protocols Encryption In Transit Protocols This article aims to provide a comprehensive guide to secure data transit, including best practices, encryption techniques/protocols, common issues, compliance, and methods to securely transfer files. Encryption at rest refers to the encryption applied to the stored data. In addition to protecting customer data at rest, microsoft uses encryption technologies to protect customer data in transit. Employ reputable encryption protocols. Encryption In Transit Protocols.
From blog.documatic.com
Data Encryption Securing Data at Rest and in Transit with Encryption Encryption In Transit Protocols Encryption may be implemented at the source, where data is generated and stored at the origin. A short overview of the various data encryption methods available today: When data is being transferred between components, locations, or programs, it's in transit. Encryption at rest refers to the encryption applied to the stored data. This article aims to provide a comprehensive guide. Encryption In Transit Protocols.