Threat Modeling Tool Mac . Learn how to get started using the threat modeling tool. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Create a diagram, identify threats, mitigate threats, and validate each. Threat dragon follows the values and principles of the threat. Use it to draw threat modeling. It is used both as a web application and as a desktop application installed for macos, windows and linux. It allows software architects to. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. An open source threat modeling tool from owasp.
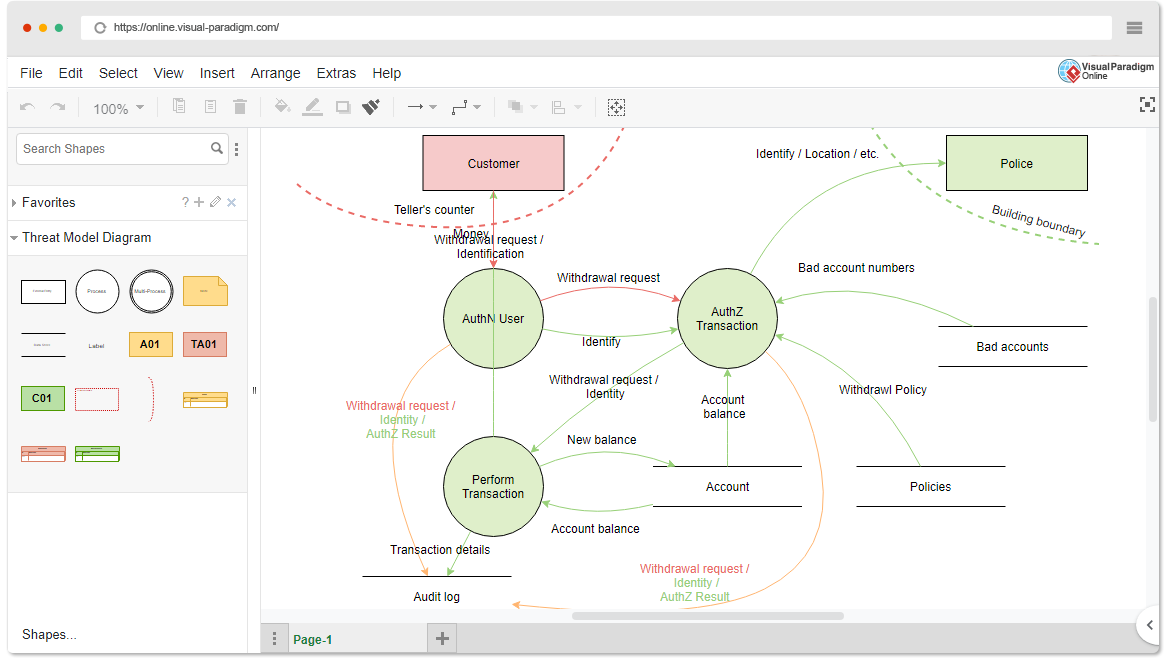
from online.visual-paradigm.com
Learn how to get started using the threat modeling tool. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. It allows software architects to. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). An open source threat modeling tool from owasp. Use it to draw threat modeling. Threat dragon follows the values and principles of the threat. Create a diagram, identify threats, mitigate threats, and validate each. It is used both as a web application and as a desktop application installed for macos, windows and linux.
Free Threat Modeling Tool
Threat Modeling Tool Mac The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Use it to draw threat modeling. An open source threat modeling tool from owasp. It allows software architects to. It is used both as a web application and as a desktop application installed for macos, windows and linux. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Threat dragon follows the values and principles of the threat. Learn how to get started using the threat modeling tool. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. Create a diagram, identify threats, mitigate threats, and validate each.
From mouseprice.weebly.com
Sdl threat modeling tool v3 mouseprice Threat Modeling Tool Mac Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. It allows software architects to. Learn how to get started using the threat modeling tool. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Threat dragon follows the values and principles of the threat.. Threat Modeling Tool Mac.
From www.acte.in
What is Threat Modeling? All you need to know [OverView] Threat Modeling Tool Mac It allows software architects to. Create a diagram, identify threats, mitigate threats, and validate each. Threat dragon follows the values and principles of the threat. It is used both as a web application and as a desktop application installed for macos, windows and linux. Use it to draw threat modeling. Learn how to get started using the threat modeling tool.. Threat Modeling Tool Mac.
From binmile.com
Implementing Threat Modeling with DevOps Threat Modeling Tool Mac Threat dragon follows the values and principles of the threat. It is used both as a web application and as a desktop application installed for macos, windows and linux. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. Learn how to get started using the threat modeling tool. An. Threat Modeling Tool Mac.
From threat-modeling.com
Threat Modeling Tool Threat Modeling Tool Mac Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. It allows software architects to. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Threat dragon follows the values and principles of the threat. An open source threat modeling tool from owasp. Learn how. Threat Modeling Tool Mac.
From www.formacionprofesional.info
Guía rápida Microsoft Threat Modeling Tool Buscar Tutorial Threat Modeling Tool Mac It allows software architects to. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. Learn how to get started using the threat modeling tool. Use it to draw threat modeling. It is used both as a web application and as a desktop application installed for macos, windows and linux.. Threat Modeling Tool Mac.
From www.linkedin.com
Threat modelling for API's is better in Shift Left Security and Zero Threat Modeling Tool Mac It allows software architects to. Create a diagram, identify threats, mitigate threats, and validate each. Threat dragon follows the values and principles of the threat. Learn how to get started using the threat modeling tool. Use it to draw threat modeling. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). It is used both. Threat Modeling Tool Mac.
From www.heise.de
Microsoft Threat Modeling Tool in Version 3 verfügbar heise online Threat Modeling Tool Mac Use it to draw threat modeling. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. It is used both as a web application and as a desktop application installed for macos, windows and linux. Create a diagram, identify threats, mitigate threats, and validate each. Threat dragon follows the values. Threat Modeling Tool Mac.
From www.spiceworks.com
What Is Threat Modeling? Definition, Process, Examples, and Best Threat Modeling Tool Mac Create a diagram, identify threats, mitigate threats, and validate each. Learn how to get started using the threat modeling tool. An open source threat modeling tool from owasp. Use it to draw threat modeling. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). It is used both as a web application and as a. Threat Modeling Tool Mac.
From www.geeksforgeeks.org
Microsoft Threat modelling tool 2016 Set 2 Threat Modeling Tool Mac An open source threat modeling tool from owasp. It is used both as a web application and as a desktop application installed for macos, windows and linux. Threat dragon follows the values and principles of the threat. Create a diagram, identify threats, mitigate threats, and validate each. Use it to draw threat modeling. The threat modeling tool is a core. Threat Modeling Tool Mac.
From threat-modeling.com
Threat Modeling Tool Threat Modeling Tool Mac It allows software architects to. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Use it to draw threat modeling. An open source threat modeling tool from owasp. Create a diagram, identify threats, mitigate threats, and validate each. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of. Threat Modeling Tool Mac.
From github.com
GitHub rusakovichma/awsthreatmodelingtooltemplate Amazon Threat Modeling Tool Mac An open source threat modeling tool from owasp. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). It allows software architects to. Learn how to get started using the threat modeling tool. Create a diagram, identify threats, mitigate threats, and validate each. Use it to draw threat modeling. Owasp threat dragon is a modeling. Threat Modeling Tool Mac.
From securityxp.com
The Microsoft Threat Modeling Tool (TMT) SecurityXP Threat Modeling Tool Mac Learn how to get started using the threat modeling tool. Threat dragon follows the values and principles of the threat. Create a diagram, identify threats, mitigate threats, and validate each. Use it to draw threat modeling. It allows software architects to. It is used both as a web application and as a desktop application installed for macos, windows and linux.. Threat Modeling Tool Mac.
From engexecutive.weebly.com
Microsoft Threat Modeling Tool For Mac engexecutive Threat Modeling Tool Mac Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. Create a diagram, identify threats, mitigate threats, and validate each. Learn how to get started using the threat modeling tool. It allows software architects to. Use it to draw threat modeling. The threat modeling tool is a core element of. Threat Modeling Tool Mac.
From threat-modeling.com
Threat Modeling with STRIDE using a Threat Modeling Tool Threat Threat Modeling Tool Mac Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. It allows software architects to. Create a diagram, identify threats, mitigate threats, and validate each. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Threat dragon follows the values and principles of the threat.. Threat Modeling Tool Mac.
From online.visual-paradigm.com
Free Threat Modeling Tool Threat Modeling Tool Mac The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). An open source threat modeling tool from owasp. Use it to draw threat modeling. It allows software architects to. Threat dragon follows the values and principles of the threat. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of. Threat Modeling Tool Mac.
From threat-modeling.com
Threat Modeling Tool Threat Modeling Tool Mac It allows software architects to. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Use it to draw threat modeling. It is used both as a web application and as a desktop application installed for macos, windows and linux. Learn how to get started using the threat modeling tool. Create a diagram, identify threats,. Threat Modeling Tool Mac.
From www.formacionprofesional.info
Guía rápida Microsoft Threat Modeling Tool Buscar Tutorial Threat Modeling Tool Mac It allows software architects to. Use it to draw threat modeling. It is used both as a web application and as a desktop application installed for macos, windows and linux. Threat dragon follows the values and principles of the threat. Create a diagram, identify threats, mitigate threats, and validate each. Owasp threat dragon is a modeling tool used to create. Threat Modeling Tool Mac.
From blogs.microsoft.com
Introducing Microsoft Threat Modeling Tool 2014 Microsoft Secure Blog Threat Modeling Tool Mac Threat dragon follows the values and principles of the threat. It is used both as a web application and as a desktop application installed for macos, windows and linux. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. Use it to draw threat modeling. The threat modeling tool is. Threat Modeling Tool Mac.
From fasrrv477.weebly.com
Microsoft Threat Modeling Tool For Mac fasrrv Threat Modeling Tool Mac Threat dragon follows the values and principles of the threat. Learn how to get started using the threat modeling tool. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). It allows software architects to. An open source threat modeling tool from owasp. Use it to draw threat modeling. Create a diagram, identify threats, mitigate. Threat Modeling Tool Mac.
From securityxp.com
The Microsoft Threat Modeling Tool (TMT) SecurityXP Threat Modeling Tool Mac It allows software architects to. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. Use it to draw threat modeling. Learn how to get started using the threat modeling tool. An open source threat modeling tool from owasp. It is used both as a web application and as a. Threat Modeling Tool Mac.
From embracethered.com
Threat modeling a machine learning system · Embrace The Red Threat Modeling Tool Mac Threat dragon follows the values and principles of the threat. It allows software architects to. It is used both as a web application and as a desktop application installed for macos, windows and linux. Create a diagram, identify threats, mitigate threats, and validate each. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of. Threat Modeling Tool Mac.
From www.spiceworks.com
Top 10 Threat Modeling Tools in 2021 Spiceworks Threat Modeling Tool Mac An open source threat modeling tool from owasp. Learn how to get started using the threat modeling tool. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). It is used both as a web application and as a desktop application installed for macos, windows and linux. It allows software architects to. Owasp threat dragon. Threat Modeling Tool Mac.
From www.geeksforgeeks.org
Microsoft Threat modelling tool 2016 Set 1 Threat Modeling Tool Mac Learn how to get started using the threat modeling tool. An open source threat modeling tool from owasp. It is used both as a web application and as a desktop application installed for macos, windows and linux. Threat dragon follows the values and principles of the threat. Owasp threat dragon is a modeling tool used to create threat model diagrams. Threat Modeling Tool Mac.
From dzone.com
Threat Modelling Tools Analysis 101 DZone Threat Modeling Tool Mac Use it to draw threat modeling. Create a diagram, identify threats, mitigate threats, and validate each. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). An open source threat modeling tool from owasp. Threat dragon follows the values and principles of the threat. It allows software architects to. It is used both as a. Threat Modeling Tool Mac.
From flowerspdf.weebly.com
How To Download Threat Modeling Tool For Mac flowerspdf Threat Modeling Tool Mac Learn how to get started using the threat modeling tool. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). An open source threat modeling tool from owasp. Threat dragon follows the values and principles of the threat. It allows software architects to. Create a diagram, identify threats, mitigate threats, and validate each. Use it. Threat Modeling Tool Mac.
From leocontent.umgc.edu
Using the Microsoft Threat Modeling Tool Threat Modeling Tool Mac Learn how to get started using the threat modeling tool. It is used both as a web application and as a desktop application installed for macos, windows and linux. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. An open source threat modeling tool from owasp. It allows software. Threat Modeling Tool Mac.
From bartwullems.blogspot.com
Microsoft Threat Modeling Tool Threat Modeling Tool Mac Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. Create a diagram, identify threats, mitigate threats, and validate each. Threat dragon follows the values and principles of the threat. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). It is used both as. Threat Modeling Tool Mac.
From binmile.com
Implementing Threat Modeling with DevOps Threat Modeling Tool Mac It allows software architects to. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). An open source threat modeling tool from owasp. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. Use it to draw threat modeling. Create a diagram, identify threats, mitigate. Threat Modeling Tool Mac.
From learn.microsoft.com
概要 Microsoft Threat Modeling Tool Azure Microsoft Learn Threat Modeling Tool Mac The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. An open source threat modeling tool from owasp. Use it to draw threat modeling. Create a diagram, identify threats, mitigate threats, and validate each. It. Threat Modeling Tool Mac.
From owasp.org
Threat Modeling Process OWASP Foundation Threat Modeling Tool Mac Learn how to get started using the threat modeling tool. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). It is used both as a web application and as a desktop application installed for macos, windows and linux. It allows software architects to. Threat dragon follows the values and principles of the threat. Create. Threat Modeling Tool Mac.
From blog.johner-institute.com
Threat modeling An introduction Threat Modeling Tool Mac Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. It allows software architects to. Learn how to get started using the threat modeling tool. Create a diagram, identify threats, mitigate threats, and validate each. It is used both as a web application and as a desktop application installed for. Threat Modeling Tool Mac.
From holisticinfosec.blogspot.dk
HolisticInfoSec™ toolsmith Microsoft Threat Modeling Tool 2014 Threat Modeling Tool Mac It allows software architects to. An open source threat modeling tool from owasp. It is used both as a web application and as a desktop application installed for macos, windows and linux. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. Use it to draw threat modeling. Create a. Threat Modeling Tool Mac.
From takeoffcu.hatenablog.com
Sdl Threat Modeling Tool For Mac takeoffcu’s blog Threat Modeling Tool Mac Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. Learn how to get started using the threat modeling tool. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). It is used both as a web application and as a desktop application installed for. Threat Modeling Tool Mac.
From takeoffcu.hatenablog.com
Sdl Threat Modeling Tool For Mac takeoffcu’s blog Threat Modeling Tool Mac Learn how to get started using the threat modeling tool. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Threat dragon follows the values and principles of the threat. It allows software architects to. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle.. Threat Modeling Tool Mac.
From www.geeksforgeeks.org
Microsoft Threat modelling tool 2016 Set 2 Threat Modeling Tool Mac Create a diagram, identify threats, mitigate threats, and validate each. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Threat dragon follows the values and principles of the threat. Owasp threat dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. It allows software architects to.. Threat Modeling Tool Mac.