What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users . learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. security value of vpn traffic monitoring. learn how to select and harden remote access vpns to protect your network from adversaries. Ensure that you have signed certificates in. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. Integrating network monitoring with cybersecurity activities. any local user on the vpn appliance should be monitored for access. stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of.
from middleware.io
learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. Ensure that you have signed certificates in. learn how to select and harden remote access vpns to protect your network from adversaries. Integrating network monitoring with cybersecurity activities. any local user on the vpn appliance should be monitored for access. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of. security value of vpn traffic monitoring.
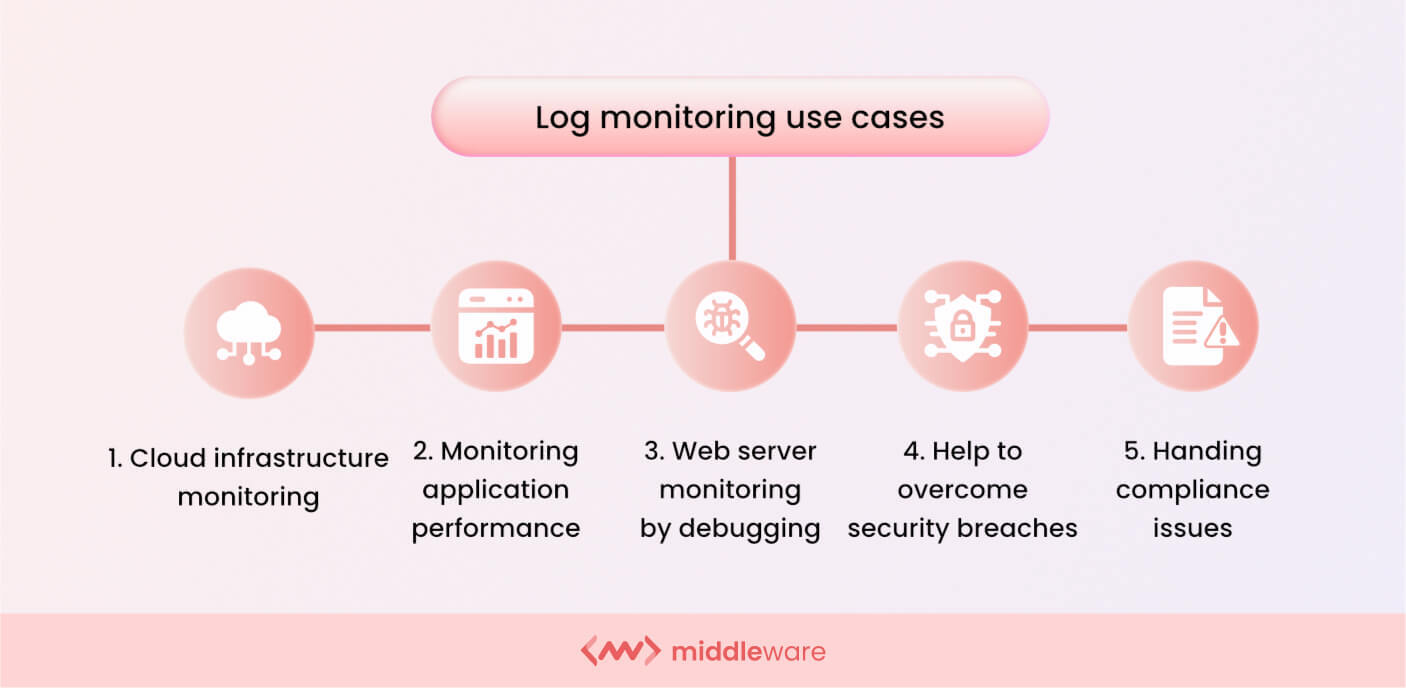
What Is Log Monitoring? A Detailed Guide (Updated) Middleware
What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users any local user on the vpn appliance should be monitored for access. any local user on the vpn appliance should be monitored for access. security value of vpn traffic monitoring. Ensure that you have signed certificates in. Integrating network monitoring with cybersecurity activities. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of. learn how to select and harden remote access vpns to protect your network from adversaries.
From www.youtube.com
Security Logging and Monitoring Failures YouTube What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users security value of vpn traffic monitoring. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. Ensure that you have signed certificates in. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. stay informed, adapt to new. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From dxoybyqqi.blob.core.windows.net
How To Get Access Key For Outline Vpn at Marcia Brown blog What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users Integrating network monitoring with cybersecurity activities. any local user on the vpn appliance should be monitored for access. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. Ensure. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.networkworld.com
Chapter 10 Designing and Building SSL Remote Access VPNs (VPN What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of. security value of vpn traffic monitoring. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. Integrating network monitoring with cybersecurity activities. Ensure that you. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From servpac.com
6 Benefits of Remote Access VPNs SERVPAC What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. security value of vpn traffic monitoring. any local user on the vpn appliance should be monitored for access. learn how to select and harden remote access vpns to protect your network from adversaries. stay informed,. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From superuser.com
Allow Remote Access Users to remote VPN site trought HQ Office GW Check What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. learn how to select and harden remote access vpns to protect your network from adversaries. stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of.. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.remote-accesss.com
Remote Access Vpn With Two Factor Authentication What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users Integrating network monitoring with cybersecurity activities. security value of vpn traffic monitoring. any local user on the vpn appliance should be monitored for access. Ensure that you have signed certificates in. stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of. learn how vpns. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.bitlyft.com
What is Security Logging and Monitoring? BitLyft Cybersecurity What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. any local user on the vpn appliance should be monitored for access. Integrating network monitoring with cybersecurity activities. learn how to select and harden remote access vpns to protect your network from adversaries. security value of vpn traffic. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From ar.inspiredpencil.com
Cisco Vpn Remote Access What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users Integrating network monitoring with cybersecurity activities. security value of vpn traffic monitoring. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. Ensure that you have signed certificates in. stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From tiptopsecurity.com
All About VPNs « TipTopSecurity What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users any local user on the vpn appliance should be monitored for access. Integrating network monitoring with cybersecurity activities. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.greyson.com
Remote Access VPN Guide Greyson Technologies Florida What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users Integrating network monitoring with cybersecurity activities. stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of. Ensure that you have signed certificates in. any local user on the vpn appliance should be monitored for access. learn how to use vpn load balancing function to distribute. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.sdxcentral.com
Virtual Private Network (VPN) Best Practices SDxCentral What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users Integrating network monitoring with cybersecurity activities. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. Ensure that you have signed certificates in. learn how to select and harden remote access vpns to protect your network from adversaries. stay informed, adapt to new trends, and prioritize security to embrace. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.genians.com
Securing Remote Access Users and Devices Genians What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users security value of vpn traffic monitoring. Ensure that you have signed certificates in. stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of. learn how to select and harden remote access vpns to protect your network from adversaries. learn how vpns use encryption to. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From middleware.io
What Is Log Monitoring? A Detailed Guide (Updated) Middleware What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users any local user on the vpn appliance should be monitored for access. Integrating network monitoring with cybersecurity activities. stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of. learn how vpns use encryption to protect data and access control over the internet, and what are. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From networkwalks.com
Firewalls and VPNs Networkwalks Academy What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. Ensure that you have signed certificates in. security value of vpn traffic monitoring. any local user on the. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.vaultnetworks.com
How VPNs Give Employees Remote Network Access Without Sacrificing What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of. Ensure that you have signed certificates in. security value of vpn traffic monitoring. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. learn how vpns. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From techtiptrick.com
VPN The Best Solution for Remote Access and Teleworking What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users learn how to select and harden remote access vpns to protect your network from adversaries. Integrating network monitoring with cybersecurity activities. security value of vpn traffic monitoring. stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of. any local user on the vpn appliance. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From blog.isa.org
How to Implement Secure, Remote Access to an Industrial Automation System What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users Ensure that you have signed certificates in. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. security value of vpn traffic monitoring. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. any local user on the. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From info.pivitglobal.com
Remote Access Clientless VPN What You Need To Know What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users learn how to select and harden remote access vpns to protect your network from adversaries. stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. security. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.codiga.io
OWASP 10 The Most Critical Security Risks To Applications What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users learn how to select and harden remote access vpns to protect your network from adversaries. security value of vpn traffic monitoring. Integrating network monitoring with cybersecurity activities. any local user on the vpn appliance should be monitored for access. learn how vpns use encryption to protect data and access control over the internet, and what are. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.youtube.com
Step by Step SSL VPN ( Mode) Remote Access VPN on FortiGate What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users Integrating network monitoring with cybersecurity activities. learn how to select and harden remote access vpns to protect your network from adversaries. Ensure that you have signed certificates in. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. any local user on the vpn appliance should be. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From middleware.io
What Is Log Monitoring? A Detailed Guide (Updated) Middleware What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. any local user on the vpn appliance should be monitored for access. security value of vpn traffic monitoring. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and.. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From duo.com
Smarter Security Logs & ContextAware Access Controls Duo Security What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. Integrating network monitoring with cybersecurity activities. Ensure that you have signed certificates in. stay informed, adapt to new trends,. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.grandmetric.com
VPN Remote Access with Multi Factor Authentication Experience Case What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users any local user on the vpn appliance should be monitored for access. learn how to select and harden remote access vpns to protect your network from adversaries. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. security value of vpn traffic monitoring. Integrating network monitoring. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From secureframe.com
6 Benefits of Continuous Monitoring for Cybersecurity What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. learn how to select and harden remote access vpns to protect your network from adversaries. stay informed, adapt. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.pinterest.com
Remote Access VPN The office network. It provides your team the What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users security value of vpn traffic monitoring. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of. learn how to use vpn load balancing function. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From atonce.com
50 Proven Ways VPNs Can Shield You from ISP Tracking 2024 What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users Integrating network monitoring with cybersecurity activities. security value of vpn traffic monitoring. any local user on the vpn appliance should be monitored for access. learn how to select and harden remote access vpns to protect your network from adversaries. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From xmcyber.com
Continuous Controls Monitoring Automatically Identifying Gaps in What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users learn how to select and harden remote access vpns to protect your network from adversaries. Integrating network monitoring with cybersecurity activities. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. Ensure that you have signed certificates in. stay informed, adapt to new trends, and prioritize security to embrace. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From inbound.usisecurity.com
What Are The Benefits Of Remote Surveillance Monitoring? What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. learn how to select and harden remote access vpns to protect your network from adversaries. Integrating network monitoring with. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.urtech.ca
Comparing SitetoSite VPN vs. Remote Access VPN Which One is Right What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users Ensure that you have signed certificates in. security value of vpn traffic monitoring. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of. Integrating network. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From intecit.com
Managed Services Remote Monitoring & Management CybersecurityIT What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users any local user on the vpn appliance should be monitored for access. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. Ensure that you have signed certificates in.. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.dnsstuff.com
Security Log Best Practices for Logging and Management DNSstuff What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users Ensure that you have signed certificates in. any local user on the vpn appliance should be monitored for access. Integrating network monitoring with cybersecurity activities. learn how to select and harden remote access vpns to protect your network from adversaries. security value of vpn traffic monitoring. stay informed, adapt to new trends, and prioritize security to. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.reddit.com
Security logging and Monitoring Failure is a critical vulnerability What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. any local user on the vpn appliance should be monitored for access. Ensure that you have signed certificates in. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance.. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.glocomp.com
Cisco Remote Access VPN architecture for Amazon Services (AWS What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users security value of vpn traffic monitoring. learn how to select and harden remote access vpns to protect your network from adversaries. learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. Integrating network monitoring with cybersecurity activities. any local user on the vpn appliance should be. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From www.softether.org
10.11 Exploit SecureNAT for Remote Access into Firewall without Any What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users learn how vpns use encryption to protect data and access control over the internet, and what are the drawbacks and. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. Integrating network monitoring with cybersecurity activities. Ensure that you have signed certificates in. stay informed, adapt to new trends,. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.
From atlasprecon.com
Top 3 Reasons to Use Remote Monitoring Atlas Precision Consulting What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users stay informed, adapt to new trends, and prioritize security to embrace a future where remote vpn access is an integral part of. Ensure that you have signed certificates in. learn how to use vpn load balancing function to distribute vpn sessions across multiple asas and improve performance. security value of vpn traffic monitoring. learn how vpns. What Security Controls Monitoring And Logging Should Be Enabled For Remote Vpn Access And Users.