What Does The Trojan Horse Look Like
Just like Zeus, it never seems to go away and instead keeps on coming back with more tricks up its sleeve. Thankfully, users of Malwarebytes are protected from this threat and many more like it. Gift horse, mouth, do not look Regardless of intention, turning your PC into an open access gateway for Trojan dolphins-er, horses.
If you do find yourself the victim of a Trojan attack, don't worry - there are a number of things you can do to remove the malware and protect your computer. First, run a diagnostic scan with your internet security software to identify and delete any malicious files. Then, run a full system scan to make sure that your computer is clean. By understanding how Trojans work, you can avoid.
I would like to know what a trojan looks like. There was a great example of a worm (although it is old) posted by Wired. Viruses embed themselves into an existing program, by changing the existing code (if I am not mistaken). On the other hand, I have no idea what trojans look like. Are they for example an executable file, which installs the desired software but also adds a backdoor?
Working with specialists, Secrets of the Dead: The Real Trojan Horse explores ideas of what the real Trojan Horse, used by the ancient Greeks to siege Troy, look like.
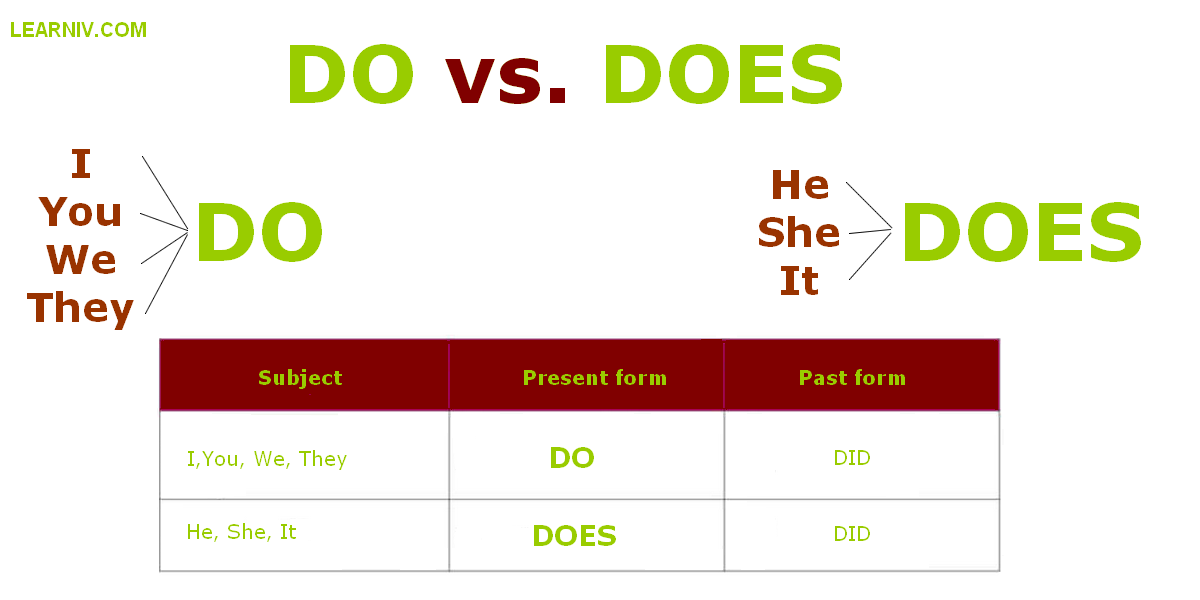
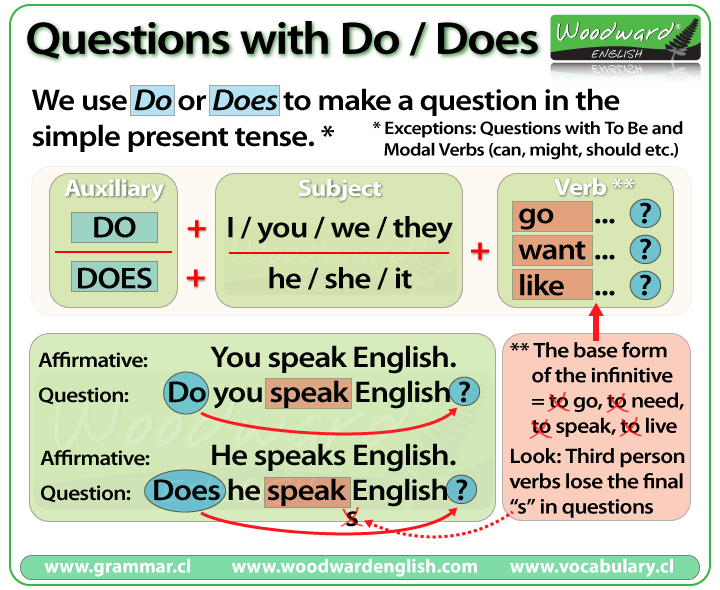
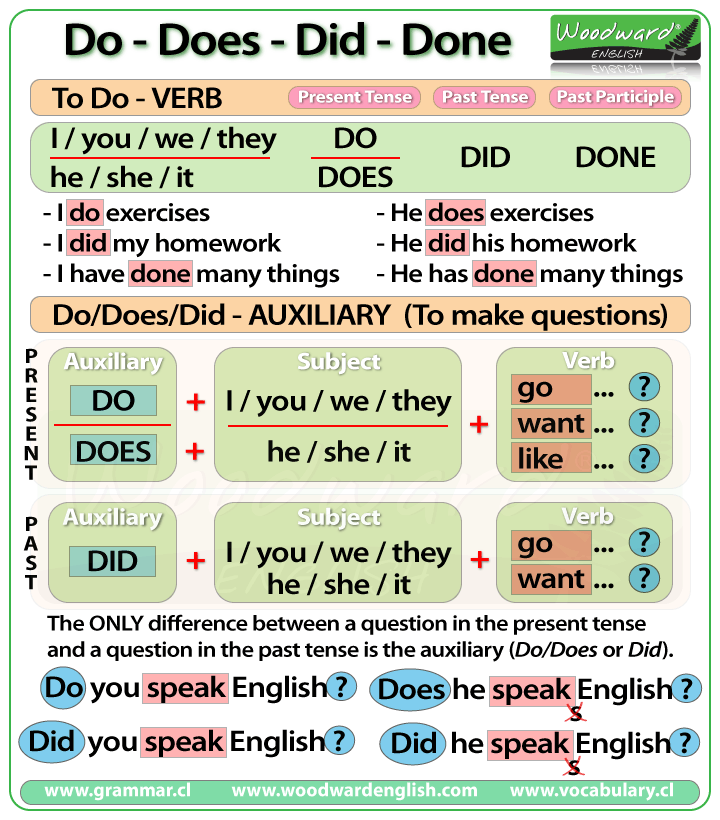
Do Does Did Rules - RebeccaminKaiser

A Trojan virus is like a wolf in sheep's clothing - or, like in the Homeric legend it's named for, offensive threats hiding in a massive wooden horse. Trojans mask themselves as legitimate files to sneak into an unsuspecting victim's device. about what Trojans do, the different types, and how you can help protect against these dangerous viruses.
The meaning of 'trojan horse' Think back to your Greek history for a second, and you might recall a famous story about the Greeks, who were at war with the Trojans, offering their enemies a gift of a giant wooden horse. The Trojans, suspecting nothing, gladly accepted the gift and wheeled it inside their city walls. This is exactly what the Greeks wanted because a cadre of Greek soldiers.
Understand Trojan Horse attacks, their types, detection, prevention methods, and how to respond effectively to these cybersecurity threats.
I would like to know what a trojan looks like. There was a great example of a worm (although it is old) posted by Wired. Viruses embed themselves into an existing program, by changing the existing code (if I am not mistaken). On the other hand, I have no idea what trojans look like. Are they for example an executable file, which installs the desired software but also adds a backdoor?
Captcha - WEDOS Global Protection
I would like to know what a trojan looks like. There was a great example of a worm (although it is old) posted by Wired. Viruses embed themselves into an existing program, by changing the existing code (if I am not mistaken). On the other hand, I have no idea what trojans look like. Are they for example an executable file, which installs the desired software but also adds a backdoor?
If you do find yourself the victim of a Trojan attack, don't worry - there are a number of things you can do to remove the malware and protect your computer. First, run a diagnostic scan with your internet security software to identify and delete any malicious files. Then, run a full system scan to make sure that your computer is clean. By understanding how Trojans work, you can avoid.
Understand Trojan Horse attacks, their types, detection, prevention methods, and how to respond effectively to these cybersecurity threats.
Working with specialists, Secrets of the Dead: The Real Trojan Horse explores ideas of what the real Trojan Horse, used by the ancient Greeks to siege Troy, look like.
Oraciones Con Do Y Does En Inglés - YouTube

In Greek mythology, the Trojan Horse (Greek: δούρειος ίππος, romanized: doureios hippos, lit. 'wooden horse') was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's Iliad, with the poem ending before the war is concluded, and it is only briefly mentioned in the Odyssey.
Working with specialists, Secrets of the Dead: The Real Trojan Horse explores ideas of what the real Trojan Horse, used by the ancient Greeks to siege Troy, look like.
The name "Trojan Horse" is taken from a classical story of the Trojan War. It is a code that is malicious and has the capacity to take control of the computer. It is designed to steal, damage, or do some harmful actions on the computer. It tries to deceive the user to load and execute the files on the device. After it executes, this allows attackers to perform actions on the user's computer.
The meaning of 'trojan horse' Think back to your Greek history for a second, and you might recall a famous story about the Greeks, who were at war with the Trojans, offering their enemies a gift of a giant wooden horse. The Trojans, suspecting nothing, gladly accepted the gift and wheeled it inside their city walls. This is exactly what the Greeks wanted because a cadre of Greek soldiers.
Using Do And Does - English Grammar

In Greek mythology, the Trojan Horse (Greek: δούρειος ίππος, romanized: doureios hippos, lit. 'wooden horse') was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's Iliad, with the poem ending before the war is concluded, and it is only briefly mentioned in the Odyssey.
I would like to know what a trojan looks like. There was a great example of a worm (although it is old) posted by Wired. Viruses embed themselves into an existing program, by changing the existing code (if I am not mistaken). On the other hand, I have no idea what trojans look like. Are they for example an executable file, which installs the desired software but also adds a backdoor?
A Closer Look At Trojans A Trojan horse, Trojan malware, or simply a Trojan is a type of malware. It makes up approximately 51.45 percent of all malware, 1 which comes as no surprise, given the unique traits of a Trojan.
Just like Zeus, it never seems to go away and instead keeps on coming back with more tricks up its sleeve. Thankfully, users of Malwarebytes are protected from this threat and many more like it. Gift horse, mouth, do not look Regardless of intention, turning your PC into an open access gateway for Trojan dolphins-er, horses.
DO Vs. DOES | English Exercises | Learn English DO Vs DOES | ESOL ...

Understand Trojan Horse attacks, their types, detection, prevention methods, and how to respond effectively to these cybersecurity threats.
I would like to know what a trojan looks like. There was a great example of a worm (although it is old) posted by Wired. Viruses embed themselves into an existing program, by changing the existing code (if I am not mistaken). On the other hand, I have no idea what trojans look like. Are they for example an executable file, which installs the desired software but also adds a backdoor?
In Greek mythology, the Trojan Horse (Greek: δούρειος ίππος, romanized: doureios hippos, lit. 'wooden horse') was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's Iliad, with the poem ending before the war is concluded, and it is only briefly mentioned in the Odyssey.
The meaning of 'trojan horse' Think back to your Greek history for a second, and you might recall a famous story about the Greeks, who were at war with the Trojans, offering their enemies a gift of a giant wooden horse. The Trojans, suspecting nothing, gladly accepted the gift and wheeled it inside their city walls. This is exactly what the Greeks wanted because a cadre of Greek soldiers.
Do And Does Sentences Examples | Sentence Examples, English Vocabulary ...

In Greek mythology, the Trojan Horse (Greek: δούρειος ίππος, romanized: doureios hippos, lit. 'wooden horse') was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's Iliad, with the poem ending before the war is concluded, and it is only briefly mentioned in the Odyssey.
The meaning of 'trojan horse' Think back to your Greek history for a second, and you might recall a famous story about the Greeks, who were at war with the Trojans, offering their enemies a gift of a giant wooden horse. The Trojans, suspecting nothing, gladly accepted the gift and wheeled it inside their city walls. This is exactly what the Greeks wanted because a cadre of Greek soldiers.
Working with specialists, Secrets of the Dead: The Real Trojan Horse explores ideas of what the real Trojan Horse, used by the ancient Greeks to siege Troy, look like.
Understand Trojan Horse attacks, their types, detection, prevention methods, and how to respond effectively to these cybersecurity threats.
Do Vs Does Questions In The Present Simple Tense | Learn English ...
Understand Trojan Horse attacks, their types, detection, prevention methods, and how to respond effectively to these cybersecurity threats.
In Greek mythology, the Trojan Horse (Greek: δούρειος ίππος, romanized: doureios hippos, lit. 'wooden horse') was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's Iliad, with the poem ending before the war is concluded, and it is only briefly mentioned in the Odyssey.
A Closer Look At Trojans A Trojan horse, Trojan malware, or simply a Trojan is a type of malware. It makes up approximately 51.45 percent of all malware, 1 which comes as no surprise, given the unique traits of a Trojan.
The meaning of 'trojan horse' Think back to your Greek history for a second, and you might recall a famous story about the Greeks, who were at war with the Trojans, offering their enemies a gift of a giant wooden horse. The Trojans, suspecting nothing, gladly accepted the gift and wheeled it inside their city walls. This is exactly what the Greeks wanted because a cadre of Greek soldiers.
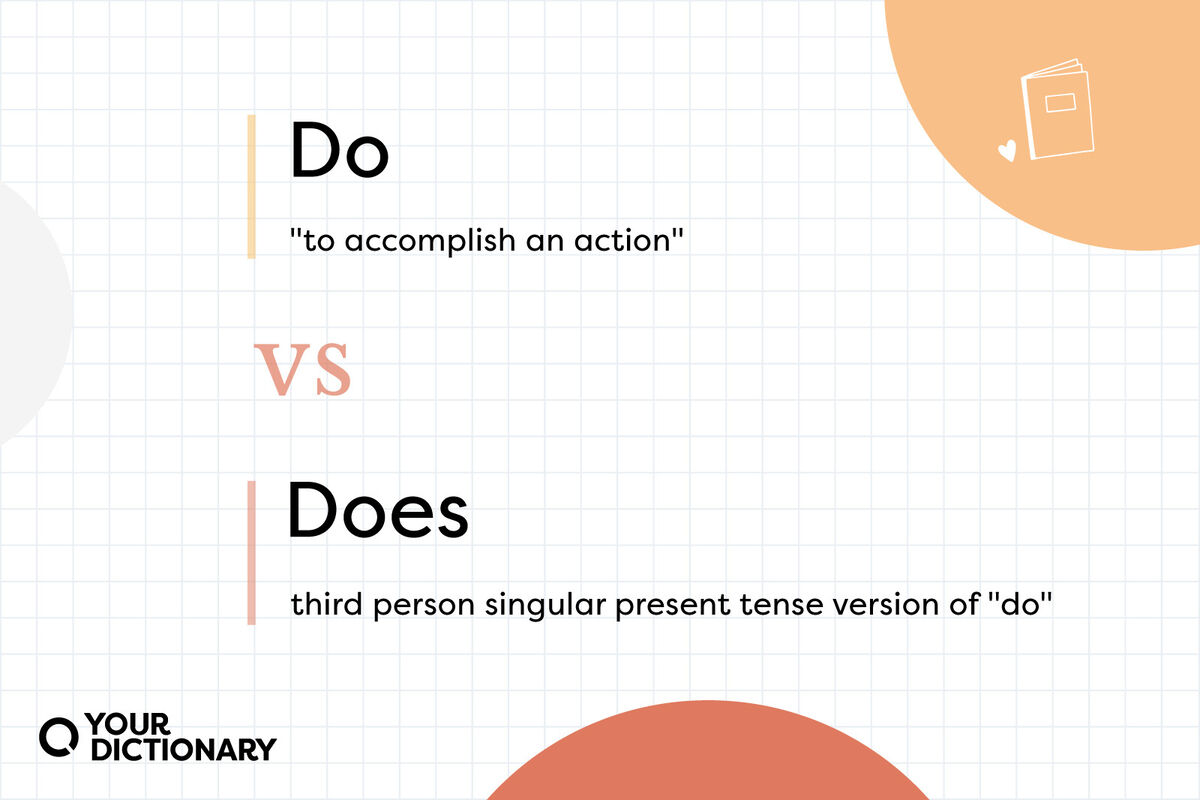
Do Vs. Does: How To Use Does Vs Do In Sentences - Confused Words

Just like Zeus, it never seems to go away and instead keeps on coming back with more tricks up its sleeve. Thankfully, users of Malwarebytes are protected from this threat and many more like it. Gift horse, mouth, do not look Regardless of intention, turning your PC into an open access gateway for Trojan dolphins-er, horses.
A Closer Look At Trojans A Trojan horse, Trojan malware, or simply a Trojan is a type of malware. It makes up approximately 51.45 percent of all malware, 1 which comes as no surprise, given the unique traits of a Trojan.
Working with specialists, Secrets of the Dead: The Real Trojan Horse explores ideas of what the real Trojan Horse, used by the ancient Greeks to siege Troy, look like.
In Greek mythology, the Trojan Horse (Greek: δούρειος ίππος, romanized: doureios hippos, lit. 'wooden horse') was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's Iliad, with the poem ending before the war is concluded, and it is only briefly mentioned in the Odyssey.
Present Simple Questions - Interactive Worksheet

I would like to know what a trojan looks like. There was a great example of a worm (although it is old) posted by Wired. Viruses embed themselves into an existing program, by changing the existing code (if I am not mistaken). On the other hand, I have no idea what trojans look like. Are they for example an executable file, which installs the desired software but also adds a backdoor?
The meaning of 'trojan horse' Think back to your Greek history for a second, and you might recall a famous story about the Greeks, who were at war with the Trojans, offering their enemies a gift of a giant wooden horse. The Trojans, suspecting nothing, gladly accepted the gift and wheeled it inside their city walls. This is exactly what the Greeks wanted because a cadre of Greek soldiers.
A Closer Look At Trojans A Trojan horse, Trojan malware, or simply a Trojan is a type of malware. It makes up approximately 51.45 percent of all malware, 1 which comes as no surprise, given the unique traits of a Trojan.
In Greek mythology, the Trojan Horse (Greek: δούρειος ίππος, romanized: doureios hippos, lit. 'wooden horse') was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's Iliad, with the poem ending before the war is concluded, and it is only briefly mentioned in the Odyssey.
Do Or Does Interactive And Downloadable Worksheet. You Can Do The ...

In Greek mythology, the Trojan Horse (Greek: δούρειος ίππος, romanized: doureios hippos, lit. 'wooden horse') was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's Iliad, with the poem ending before the war is concluded, and it is only briefly mentioned in the Odyssey.
A Closer Look At Trojans A Trojan horse, Trojan malware, or simply a Trojan is a type of malware. It makes up approximately 51.45 percent of all malware, 1 which comes as no surprise, given the unique traits of a Trojan.
I would like to know what a trojan looks like. There was a great example of a worm (although it is old) posted by Wired. Viruses embed themselves into an existing program, by changing the existing code (if I am not mistaken). On the other hand, I have no idea what trojans look like. Are they for example an executable file, which installs the desired software but also adds a backdoor?
The meaning of 'trojan horse' Think back to your Greek history for a second, and you might recall a famous story about the Greeks, who were at war with the Trojans, offering their enemies a gift of a giant wooden horse. The Trojans, suspecting nothing, gladly accepted the gift and wheeled it inside their city walls. This is exactly what the Greeks wanted because a cadre of Greek soldiers.
A Printable For Learning 'do And Does' | English Language Learning ...

A Trojan virus is like a wolf in sheep's clothing - or, like in the Homeric legend it's named for, offensive threats hiding in a massive wooden horse. Trojans mask themselves as legitimate files to sneak into an unsuspecting victim's device. about what Trojans do, the different types, and how you can help protect against these dangerous viruses.
In Greek mythology, the Trojan Horse (Greek: δούρειος ίππος, romanized: doureios hippos, lit. 'wooden horse') was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's Iliad, with the poem ending before the war is concluded, and it is only briefly mentioned in the Odyssey.
I would like to know what a trojan looks like. There was a great example of a worm (although it is old) posted by Wired. Viruses embed themselves into an existing program, by changing the existing code (if I am not mistaken). On the other hand, I have no idea what trojans look like. Are they for example an executable file, which installs the desired software but also adds a backdoor?
If you do find yourself the victim of a Trojan attack, don't worry - there are a number of things you can do to remove the malware and protect your computer. First, run a diagnostic scan with your internet security software to identify and delete any malicious files. Then, run a full system scan to make sure that your computer is clean. By understanding how Trojans work, you can avoid.

In Greek mythology, the Trojan Horse (Greek: δούρειος ίππος, romanized: doureios hippos, lit. 'wooden horse') was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's Iliad, with the poem ending before the war is concluded, and it is only briefly mentioned in the Odyssey.
Just like Zeus, it never seems to go away and instead keeps on coming back with more tricks up its sleeve. Thankfully, users of Malwarebytes are protected from this threat and many more like it. Gift horse, mouth, do not look Regardless of intention, turning your PC into an open access gateway for Trojan dolphins-er, horses.
Working with specialists, Secrets of the Dead: The Real Trojan Horse explores ideas of what the real Trojan Horse, used by the ancient Greeks to siege Troy, look like.
Understand Trojan Horse attacks, their types, detection, prevention methods, and how to respond effectively to these cybersecurity threats.
What Does Playwright - Crafting Stories For The Stage
A Closer Look At Trojans A Trojan horse, Trojan malware, or simply a Trojan is a type of malware. It makes up approximately 51.45 percent of all malware, 1 which comes as no surprise, given the unique traits of a Trojan.
The meaning of 'trojan horse' Think back to your Greek history for a second, and you might recall a famous story about the Greeks, who were at war with the Trojans, offering their enemies a gift of a giant wooden horse. The Trojans, suspecting nothing, gladly accepted the gift and wheeled it inside their city walls. This is exactly what the Greeks wanted because a cadre of Greek soldiers.
Just like Zeus, it never seems to go away and instead keeps on coming back with more tricks up its sleeve. Thankfully, users of Malwarebytes are protected from this threat and many more like it. Gift horse, mouth, do not look Regardless of intention, turning your PC into an open access gateway for Trojan dolphins-er, horses.
Understand Trojan Horse attacks, their types, detection, prevention methods, and how to respond effectively to these cybersecurity threats.
Using Do Vs. Does Properly In Questions And Sentences | YourDictionary
The meaning of 'trojan horse' Think back to your Greek history for a second, and you might recall a famous story about the Greeks, who were at war with the Trojans, offering their enemies a gift of a giant wooden horse. The Trojans, suspecting nothing, gladly accepted the gift and wheeled it inside their city walls. This is exactly what the Greeks wanted because a cadre of Greek soldiers.
A Closer Look At Trojans A Trojan horse, Trojan malware, or simply a Trojan is a type of malware. It makes up approximately 51.45 percent of all malware, 1 which comes as no surprise, given the unique traits of a Trojan.
A Trojan virus is like a wolf in sheep's clothing - or, like in the Homeric legend it's named for, offensive threats hiding in a massive wooden horse. Trojans mask themselves as legitimate files to sneak into an unsuspecting victim's device. about what Trojans do, the different types, and how you can help protect against these dangerous viruses.
The name "Trojan Horse" is taken from a classical story of the Trojan War. It is a code that is malicious and has the capacity to take control of the computer. It is designed to steal, damage, or do some harmful actions on the computer. It tries to deceive the user to load and execute the files on the device. After it executes, this allows attackers to perform actions on the user's computer.
Understand Trojan Horse attacks, their types, detection, prevention methods, and how to respond effectively to these cybersecurity threats.
The meaning of 'trojan horse' Think back to your Greek history for a second, and you might recall a famous story about the Greeks, who were at war with the Trojans, offering their enemies a gift of a giant wooden horse. The Trojans, suspecting nothing, gladly accepted the gift and wheeled it inside their city walls. This is exactly what the Greeks wanted because a cadre of Greek soldiers.
A Trojan virus is like a wolf in sheep's clothing - or, like in the Homeric legend it's named for, offensive threats hiding in a massive wooden horse. Trojans mask themselves as legitimate files to sneak into an unsuspecting victim's device. about what Trojans do, the different types, and how you can help protect against these dangerous viruses.
If you do find yourself the victim of a Trojan attack, don't worry - there are a number of things you can do to remove the malware and protect your computer. First, run a diagnostic scan with your internet security software to identify and delete any malicious files. Then, run a full system scan to make sure that your computer is clean. By understanding how Trojans work, you can avoid.
A Trojan virus is like a wolf in sheep's clothing - or, like in the Homeric legend it's named for, offensive threats hiding in a massive wooden horse. Trojans mask themselves as legitimate files to sneak into an unsuspecting victim's device. about what Trojans do, the different types, and how you can help protect against these dangerous viruses.
I would like to know what a trojan looks like. There was a great example of a worm (although it is old) posted by Wired. Viruses embed themselves into an existing program, by changing the existing code (if I am not mistaken). On the other hand, I have no idea what trojans look like. Are they for example an executable file, which installs the desired software but also adds a backdoor?
Working with specialists, Secrets of the Dead: The Real Trojan Horse explores ideas of what the real Trojan Horse, used by the ancient Greeks to siege Troy, look like.
Just like Zeus, it never seems to go away and instead keeps on coming back with more tricks up its sleeve. Thankfully, users of Malwarebytes are protected from this threat and many more like it. Gift horse, mouth, do not look Regardless of intention, turning your PC into an open access gateway for Trojan dolphins-er, horses.
A Closer Look At Trojans A Trojan horse, Trojan malware, or simply a Trojan is a type of malware. It makes up approximately 51.45 percent of all malware, 1 which comes as no surprise, given the unique traits of a Trojan.
The name "Trojan Horse" is taken from a classical story of the Trojan War. It is a code that is malicious and has the capacity to take control of the computer. It is designed to steal, damage, or do some harmful actions on the computer. It tries to deceive the user to load and execute the files on the device. After it executes, this allows attackers to perform actions on the user's computer.
The meaning of 'trojan horse' Think back to your Greek history for a second, and you might recall a famous story about the Greeks, who were at war with the Trojans, offering their enemies a gift of a giant wooden horse. The Trojans, suspecting nothing, gladly accepted the gift and wheeled it inside their city walls. This is exactly what the Greeks wanted because a cadre of Greek soldiers.
If you do find yourself the victim of a Trojan attack, don't worry - there are a number of things you can do to remove the malware and protect your computer. First, run a diagnostic scan with your internet security software to identify and delete any malicious files. Then, run a full system scan to make sure that your computer is clean. By understanding how Trojans work, you can avoid.
Understand Trojan Horse attacks, their types, detection, prevention methods, and how to respond effectively to these cybersecurity threats.
In Greek mythology, the Trojan Horse (Greek: δούρειος ίππος, romanized: doureios hippos, lit. 'wooden horse') was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's Iliad, with the poem ending before the war is concluded, and it is only briefly mentioned in the Odyssey.