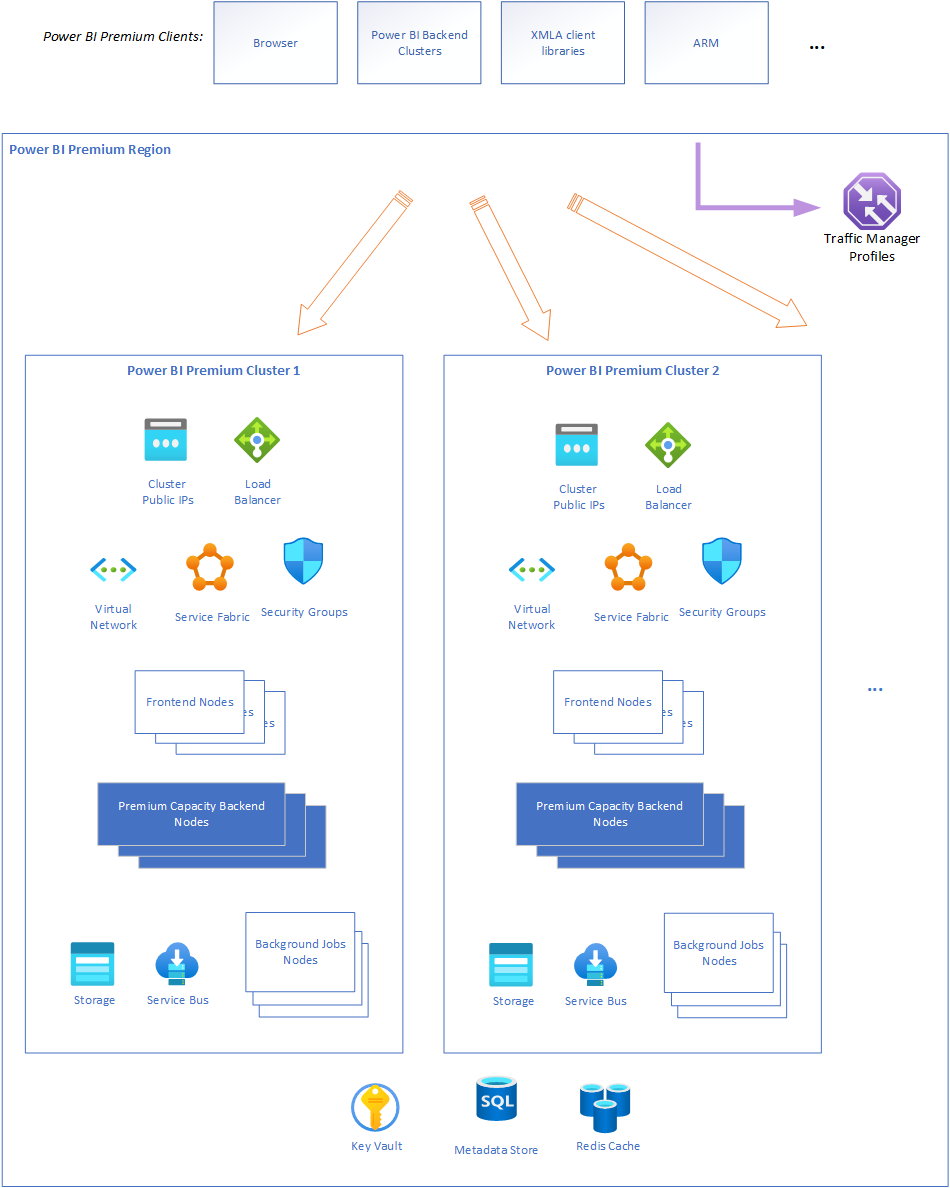
Azure Power Bi Security Best Practices . While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. The blog post also outlines 24 best practices for implementing power bi security, which are as follows: Große liste von anbieternrecovery von gpos The easiest way to limit access to the database is to select the “allow access to. How can you connect to azure sql database from the power bi service in a secure fashion? The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development cost. Power bi has robust encryption for both data at rest and data in transit. Microsoft power bi data and service security. A secure connection is established with the data. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal.
from learn.microsoft.com
The blog post also outlines 24 best practices for implementing power bi security, which are as follows: The easiest way to limit access to the database is to select the “allow access to. A secure connection is established with the data. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Microsoft power bi data and service security. Power bi has robust encryption for both data at rest and data in transit. Große liste von anbieternrecovery von gpos How can you connect to azure sql database from the power bi service in a secure fashion? While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development cost.
Power BI security white paper Power BI Microsoft Learn
Azure Power Bi Security Best Practices How can you connect to azure sql database from the power bi service in a secure fashion? The blog post also outlines 24 best practices for implementing power bi security, which are as follows: Microsoft power bi data and service security. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Power bi has robust encryption for both data at rest and data in transit. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development cost. A secure connection is established with the data. The easiest way to limit access to the database is to select the “allow access to. Große liste von anbieternrecovery von gpos How can you connect to azure sql database from the power bi service in a secure fashion?
From quadexcel.com
Azure Security best practices Azure Tips and Tricks Azure Power Bi Security Best Practices Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. A secure connection is established with the data. The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development cost. The blog post also outlines 24 best practices for implementing power. Azure Power Bi Security Best Practices.
From learn.microsoft.com
Power BI security white paper Power BI Microsoft Learn Azure Power Bi Security Best Practices The blog post also outlines 24 best practices for implementing power bi security, which are as follows: Power bi has robust encryption for both data at rest and data in transit. Microsoft power bi data and service security. Große liste von anbieternrecovery von gpos The easiest way to limit access to the database is to select the “allow access to.. Azure Power Bi Security Best Practices.
From powerbigate.com
Power BI Security Best Practices Protecting Your Data and Reports Azure Power Bi Security Best Practices Große liste von anbieternrecovery von gpos Microsoft power bi data and service security. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Power bi has robust encryption for both data at rest and data in transit. The sdl helps developers build more secure software by reducing the number and severity. Azure Power Bi Security Best Practices.
From onlineappsdba.com
Data Security in Power BI How to Implement and Configure Azure Power Bi Security Best Practices A secure connection is established with the data. The blog post also outlines 24 best practices for implementing power bi security, which are as follows: Microsoft power bi data and service security. The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development cost. Große liste von anbieternrecovery von gpos. Azure Power Bi Security Best Practices.
From discover.opscompass.com
5 Best Practices for Securing Microsoft Azure Azure Power Bi Security Best Practices Microsoft power bi data and service security. Power bi has robust encryption for both data at rest and data in transit. How can you connect to azure sql database from the power bi service in a secure fashion? Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. The blog post. Azure Power Bi Security Best Practices.
From www.onpointserv.com
Protecting Your Business Insights Power BI Security Best Practices Azure Power Bi Security Best Practices How can you connect to azure sql database from the power bi service in a secure fashion? A secure connection is established with the data. Microsoft power bi data and service security. Große liste von anbieternrecovery von gpos The blog post also outlines 24 best practices for implementing power bi security, which are as follows: While the power bi security. Azure Power Bi Security Best Practices.
From hbservices.in
Introduction to Azure security 1 IT Training institute in chennai Azure Power Bi Security Best Practices Power bi has robust encryption for both data at rest and data in transit. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. The easiest way to limit access to the database is to select the “allow access to. The sdl helps developers build more secure software by reducing the. Azure Power Bi Security Best Practices.
From www.sparity.com
8 Best Power BI Security Practices Azure Power Bi Security Best Practices While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Microsoft power bi data and service security. A secure connection is established with the data. The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities. Azure Power Bi Security Best Practices.
From www.ilink-digital.com
Microsoft Power BI Security 6 Best Practices iLink Digital Azure Power Bi Security Best Practices The blog post also outlines 24 best practices for implementing power bi security, which are as follows: Power bi has robust encryption for both data at rest and data in transit. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. While the power bi security white paper focuses on key. Azure Power Bi Security Best Practices.
From www.auratechnology.com
Azure Security Best Practices for Your Cloud Infrastructure Aura Azure Power Bi Security Best Practices Power bi has robust encryption for both data at rest and data in transit. The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development cost. Große liste von anbieternrecovery von gpos How can you connect to azure sql database from the power bi service in a secure fashion? A. Azure Power Bi Security Best Practices.
From www.yittbox.com
Power BI Security Best Practices for Data Protection and Governance Azure Power Bi Security Best Practices The easiest way to limit access to the database is to select the “allow access to. How can you connect to azure sql database from the power bi service in a secure fashion? Power bi has robust encryption for both data at rest and data in transit. A secure connection is established with the data. Microsoft power bi data and. Azure Power Bi Security Best Practices.
From blog.hametbenoit.info
Azure The Azure Security team has developed a Power BI Dashboard Azure Power Bi Security Best Practices A secure connection is established with the data. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Microsoft power bi data and service security. How can you connect to azure sql database from the power bi service in a secure fashion? The blog post also outlines 24 best practices for. Azure Power Bi Security Best Practices.
From www.journeyteam.com
9 Power BI Security Best Practices Azure Power Bi Security Best Practices Power bi has robust encryption for both data at rest and data in transit. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. The blog post also outlines 24 best practices for implementing power bi security, which are as follows: A secure connection is established with the data. The sdl. Azure Power Bi Security Best Practices.
From www.threatshub.org
Best practices for adding layered security to Azure security with Check Azure Power Bi Security Best Practices Große liste von anbieternrecovery von gpos Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. The easiest way to limit access to the database is to select the “allow access to. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network. Azure Power Bi Security Best Practices.
From medium.com
Power BI Security Best Practices and Emerging Threats by Chirag Azure Power Bi Security Best Practices Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Große liste von anbieternrecovery von gpos Microsoft power bi data and service security. The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development cost. The blog post also outlines 24. Azure Power Bi Security Best Practices.
From qmetrix.com.au
Power BI Architecture And Security What You Need To Know Azure Power Bi Security Best Practices While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development cost. The blog post also outlines 24 best practices for. Azure Power Bi Security Best Practices.
From docs.microsoft.com
Azure and Power BI Power BI Microsoft Docs Azure Power Bi Security Best Practices Große liste von anbieternrecovery von gpos The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development cost. How can you connect to azure sql database from the power bi service in a secure fashion? The easiest way to limit access to the database is to select the “allow access. Azure Power Bi Security Best Practices.
From www.youtube.com
Explore Azure Security Center in Power BI YouTube Azure Power Bi Security Best Practices A secure connection is established with the data. The easiest way to limit access to the database is to select the “allow access to. Microsoft power bi data and service security. How can you connect to azure sql database from the power bi service in a secure fashion? While the power bi security white paper focuses on key technical topics. Azure Power Bi Security Best Practices.
From thecyphere.com
Microsoft Azure Security Best Practices Cyphere Azure Power Bi Security Best Practices While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. A secure connection is established with the data. Große liste von anbieternrecovery von gpos How can you connect to azure sql database from the power bi service in a secure fashion?. Azure Power Bi Security Best Practices.
From www.sparity.com
8 Best Power BI Security Practices Azure Power Bi Security Best Practices The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development cost. The blog post also outlines 24 best practices for implementing power bi security, which are as follows: Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. Power bi. Azure Power Bi Security Best Practices.
From deltanem.com
Best Practices to Enhance Your Security in Microsoft Azure Delta News Azure Power Bi Security Best Practices Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. The easiest way to limit access to the database is to select the “allow access to. Große liste von anbieternrecovery von gpos Power bi has robust encryption for both data at rest and data in transit. How can you connect to. Azure Power Bi Security Best Practices.
From www.opsramp.com
Azure Security Best Practices & Step By Step Instructions OpsRamp Azure Power Bi Security Best Practices Power bi has robust encryption for both data at rest and data in transit. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in. Azure Power Bi Security Best Practices.
From www.linkedin.com
Microsoft Azure WellArchitected Security Best Practices for Building Azure Power Bi Security Best Practices The easiest way to limit access to the database is to select the “allow access to. Microsoft power bi data and service security. The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development cost. While the power bi security white paper focuses on key technical topics such as authentication,. Azure Power Bi Security Best Practices.
From reverasite.com
Analyze Your Azure Security Center Data With Power Bi Power Bi Power Azure Power Bi Security Best Practices The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development cost. The easiest way to limit access to the database is to select the “allow access to. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary. Azure Power Bi Security Best Practices.
From www.checkyourlogs.net
Using Azure Blueprints Implementation best practices to put security Azure Power Bi Security Best Practices Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development cost. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network. Azure Power Bi Security Best Practices.
From www.uniquenewsonline.com
Azure Security Best Practices You Need To Implement Azure Power Bi Security Best Practices While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Identify and analyze risky behavior patterns with oversight capabilities in power bi and the microsoft cloud app security portal. The sdl helps developers build more secure software by reducing the number. Azure Power Bi Security Best Practices.
From skypointcloud.com
How Do We Improve Power BI Security? SkyPoint Cloud Azure Power Bi Security Best Practices The easiest way to limit access to the database is to select the “allow access to. How can you connect to azure sql database from the power bi service in a secure fashion? The blog post also outlines 24 best practices for implementing power bi security, which are as follows: Microsoft power bi data and service security. Große liste von. Azure Power Bi Security Best Practices.
From docs.microsoft.com
Security Overview Azure SQL Database & Azure SQL Managed Instance Azure Power Bi Security Best Practices The blog post also outlines 24 best practices for implementing power bi security, which are as follows: Power bi has robust encryption for both data at rest and data in transit. While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide.. Azure Power Bi Security Best Practices.
From www.codingninjas.com
Azure Security Baseline for Power BI Coding Ninjas CodeStudio Azure Power Bi Security Best Practices How can you connect to azure sql database from the power bi service in a secure fashion? Power bi has robust encryption for both data at rest and data in transit. The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development cost. Große liste von anbieternrecovery von gpos The. Azure Power Bi Security Best Practices.
From powerbigate.com
Power BI Security Best Practices Protecting Your Data and Reports Azure Power Bi Security Best Practices Microsoft power bi data and service security. Power bi has robust encryption for both data at rest and data in transit. A secure connection is established with the data. The blog post also outlines 24 best practices for implementing power bi security, which are as follows: While the power bi security white paper focuses on key technical topics such as. Azure Power Bi Security Best Practices.
From www.onpointserv.com
Enhance Your Power BI Security Best Practices Unveiled Azure Power Bi Security Best Practices Power bi has robust encryption for both data at rest and data in transit. The blog post also outlines 24 best practices for implementing power bi security, which are as follows: While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide.. Azure Power Bi Security Best Practices.
From www.theproche.com
Power BI Security Best Practices Safeguarding Your Data Proche Azure Power Bi Security Best Practices The blog post also outlines 24 best practices for implementing power bi security, which are as follows: Große liste von anbieternrecovery von gpos The easiest way to limit access to the database is to select the “allow access to. The sdl helps developers build more secure software by reducing the number and severity of vulnerabilities in software, while reducing development. Azure Power Bi Security Best Practices.
From www.onpointserv.com
Enhance Your Power BI Security Best Practices Unveiled Azure Power Bi Security Best Practices How can you connect to azure sql database from the power bi service in a secure fashion? A secure connection is established with the data. Microsoft power bi data and service security. Große liste von anbieternrecovery von gpos While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary. Azure Power Bi Security Best Practices.
From www.youtube.com
Power BI Security Best Practices YouTube Azure Power Bi Security Best Practices While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. The easiest way to limit access to the database is to select the “allow access to. A secure connection is established with the data. Identify and analyze risky behavior patterns with. Azure Power Bi Security Best Practices.
From www.softude.com
24 Essential Practices to Ensure Power BI Security Azure Power Bi Security Best Practices The blog post also outlines 24 best practices for implementing power bi security, which are as follows: Große liste von anbieternrecovery von gpos While the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of the series is to provide. Identify and analyze risky behavior patterns with oversight. Azure Power Bi Security Best Practices.